Method of bidirectional authentication during subscriber switch in digital cellular mobile communication system
A technology for cellular mobile communication and mobile users, which is applied in the field of automatic two-way authentication of user and base station identities, which can solve problems such as user fake base station attacks, network security loopholes, and one-way authentication mechanism, and achieve the effect of guaranteeing benefits.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
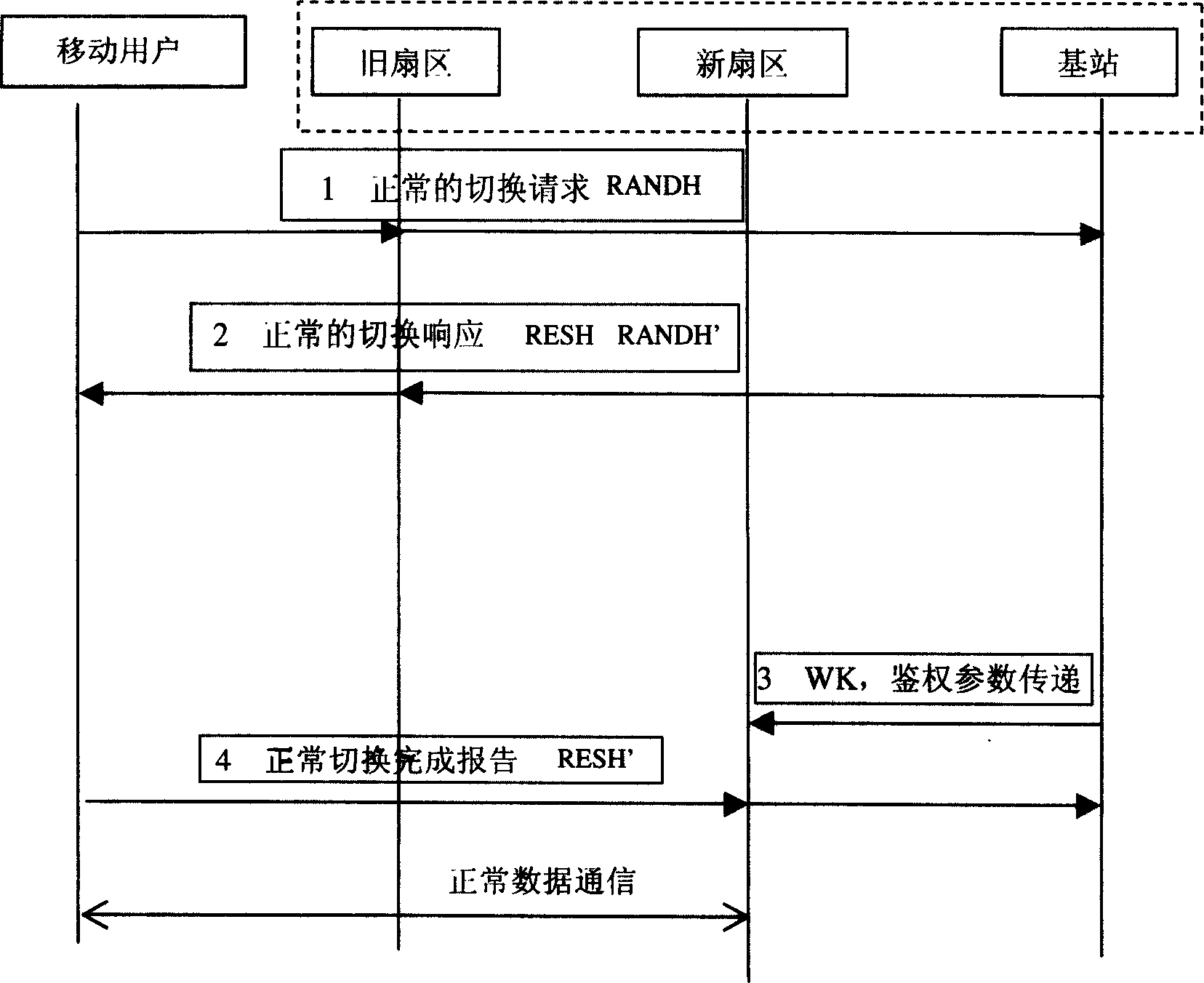
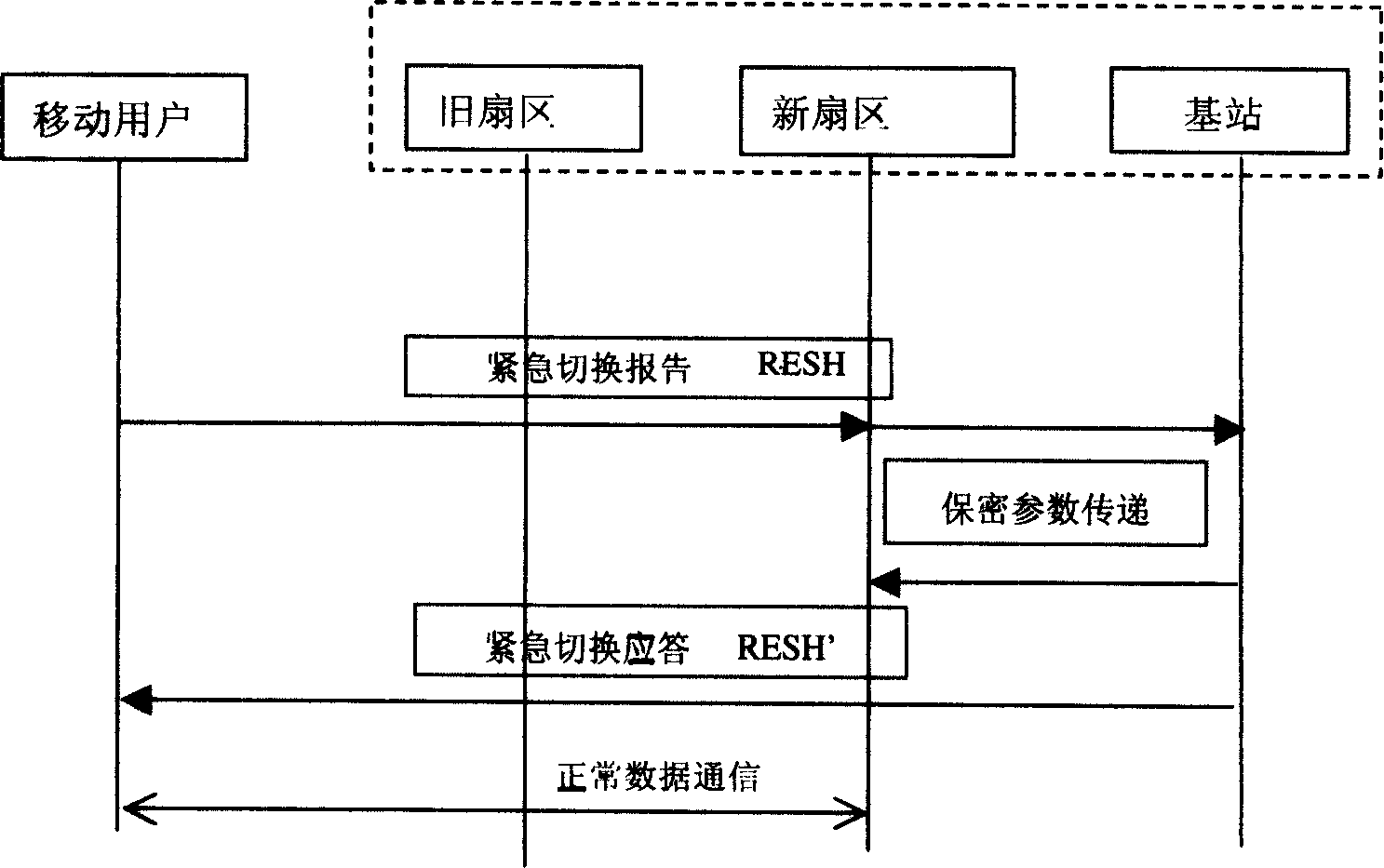
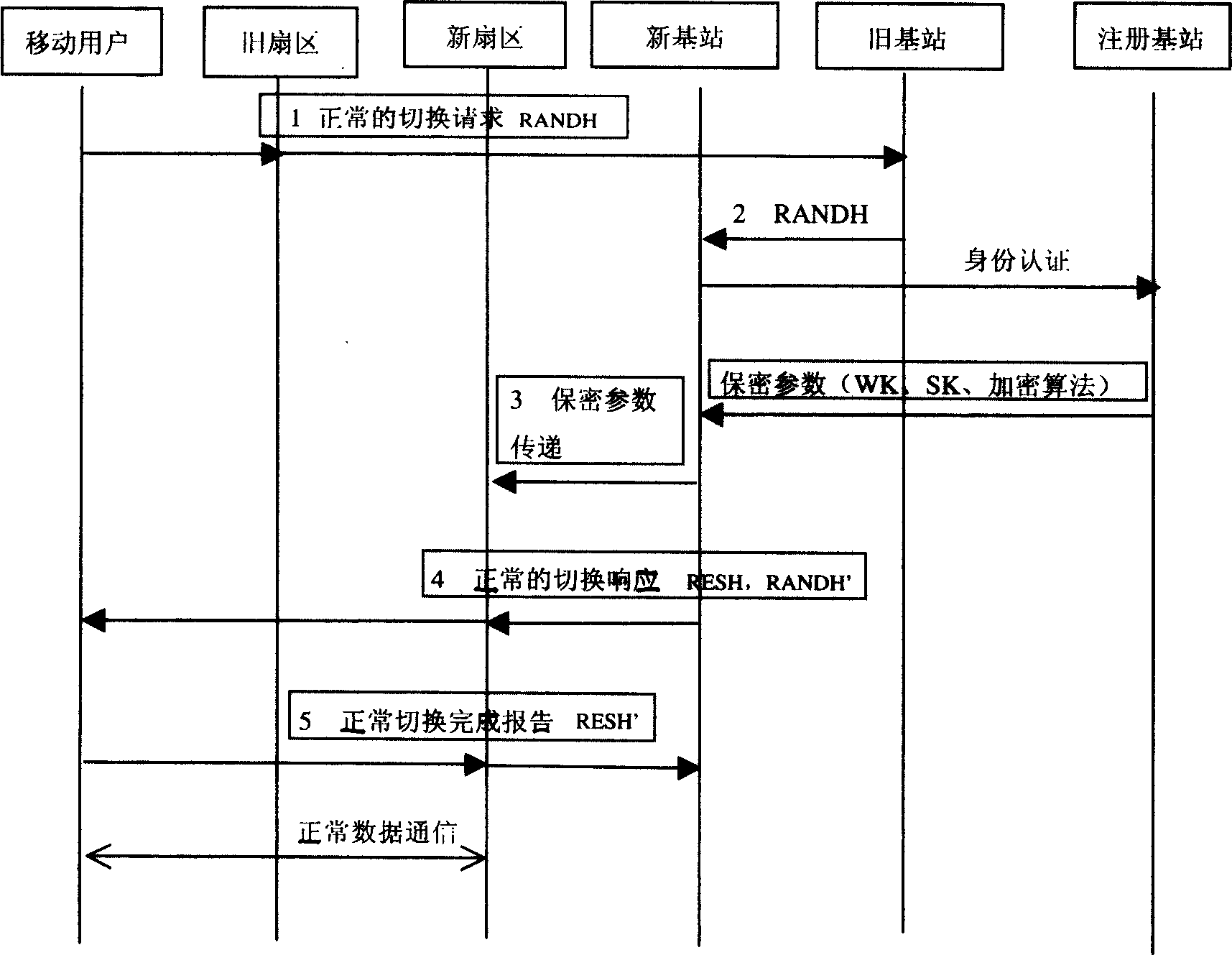
[0021] The two-way identification method when the user of the digital cellular mobile communication system switches is realized by the execution of the identification software. The identification software is respectively stored at both ends of the communication. The specific physical storage location is; mobile users such as mobile phones are stored in the SIM card Inside, the identification software at the base station is stored in the base station controller. Any one of the two parties can initiate a two-way authentication request, and the two-way authentication process during switching is quickly and automatically completed between the mobile phone, the base station controller and the AAA server.
[0022] If the user and the mobile phone move from one working sector of the same base station to another sector, the two-way identification software of the present invention in the SIM card of the mobile phone and the two-way identification software of the present invention in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com