Method for security encryption and signing based on identity file
A security encryption and file technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as low safety factor, inconvenience in life, study and work, modification and theft by others, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
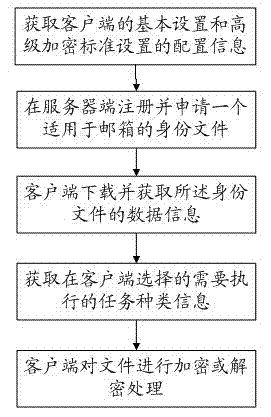
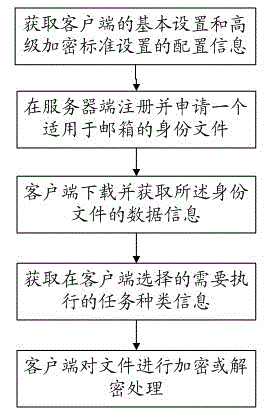
[0036] refer to figure 1 , figure 1 It is a structural diagram of a preferred embodiment of the security encryption and signature method based on the identity file of the present invention.
[0037] A secure encryption and signature method based on an identity file, the steps of which include: obtaining the configuration information of the basic settings of the client and the configuration information of the Advanced Encryption Standard setting; registering and applying for an identity file suitable for a mailbox at the server; downloading the And obtain the data information of the identity file; obtain the type information of the task selected ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com