Patents
Literature
397 results about "Inside information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
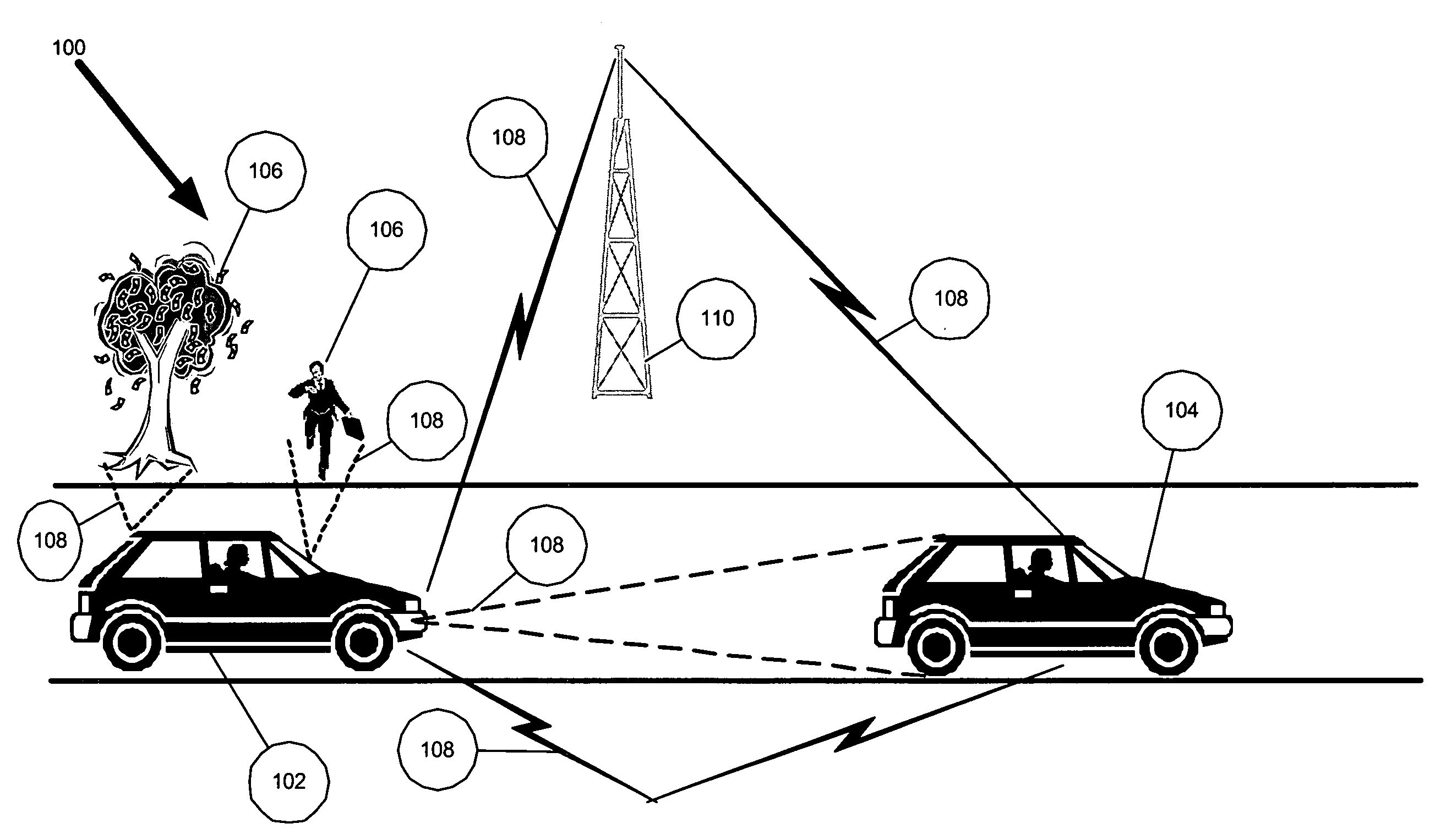
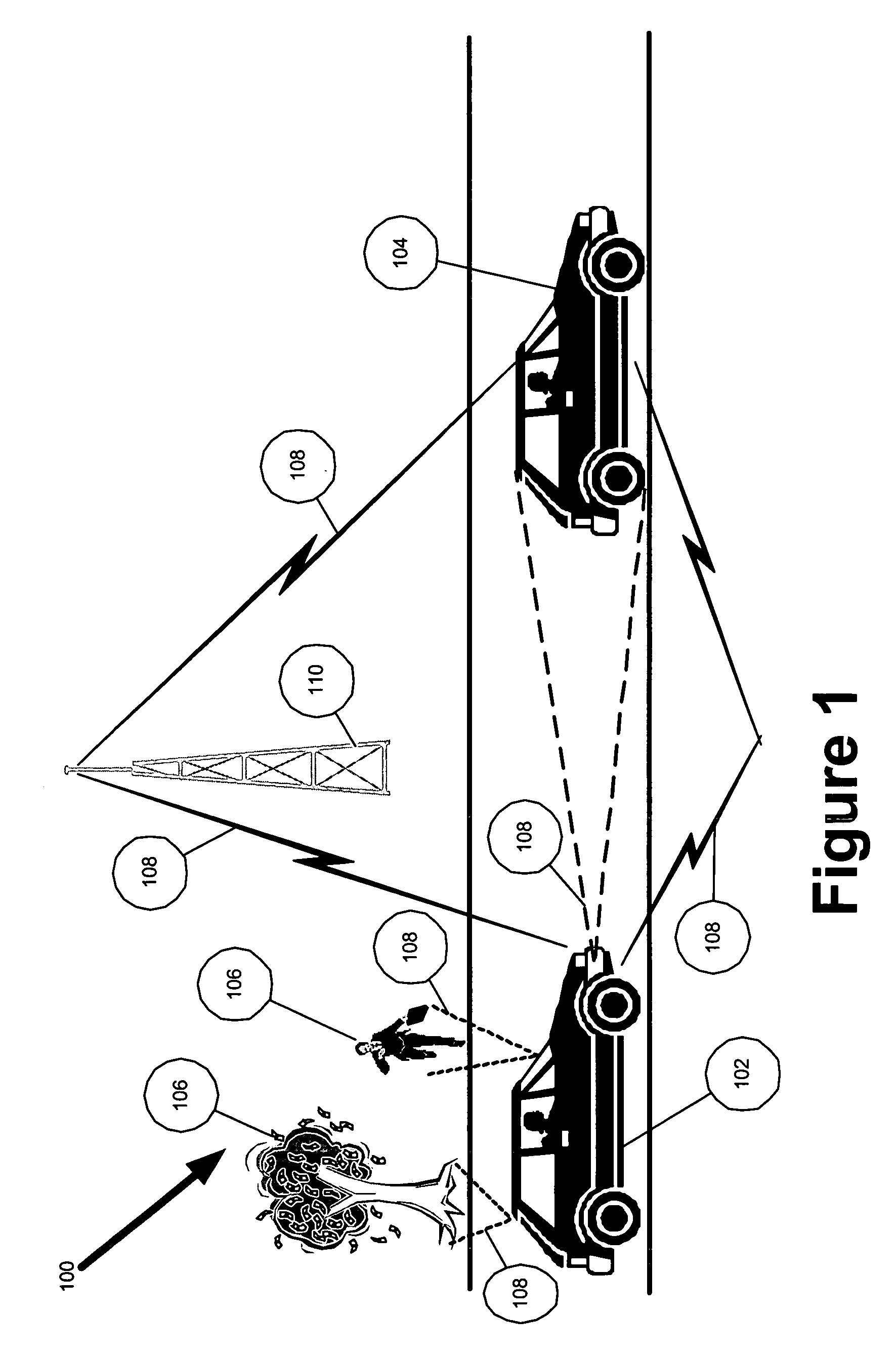
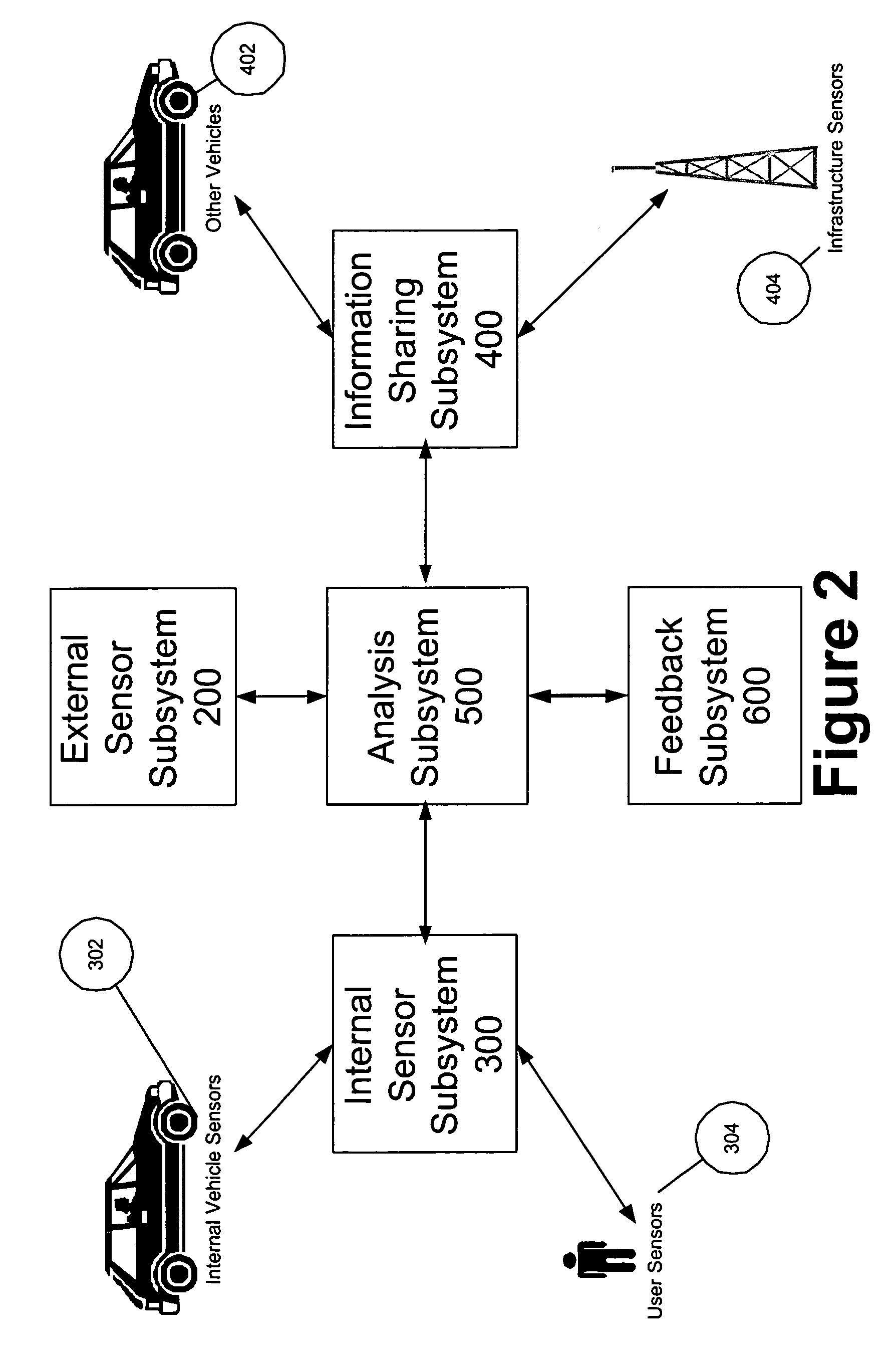
Multi-sensor integration for a vehicle
A sensor system for use in a vehicle that integrates sensor data from more than one sensor in an effort to facilitate collision avoidance and other types of sensor-related processing. The system include external sensors for capturing sensor data external to the vehicle. External sensors can include sensors of a wide variety of different sensor types, including radar, image processing, ultrasonic, infrared, and other sensor types. Each external sensor can be configured to focus on a particular sensor zone external to the vehicle. Each external sensor can also be configured to focus primarily on particular types of potential obstacles and obstructions based on the particular characteristics of the sensor zone and sensor type. All sensor data can be integrated in a comprehensive manner by a threat assessment subsystem within the sensor system. The system is not limited to sensor data from external sensors. Internal sensors can be used to capture internal sensor data, such a vehicle characteristics, user attributes, and other types of interior information. Moreover, the sensor system can also include an information sharing subsystem of exchanging information with other vehicle sensor systems or for exchanging information with non-vehicle systems such as a non-movable highway sensor system configured to transmit and receive information relating to traffic, weather, construction, and other conditions. The sensor system can potentially integrate data from all different sources in a comprehensive and integrated manner. The system can integrate information by assigning particular weights to particular determinations by particular sensors.
Owner:YAZAKI NORTH AMERICA
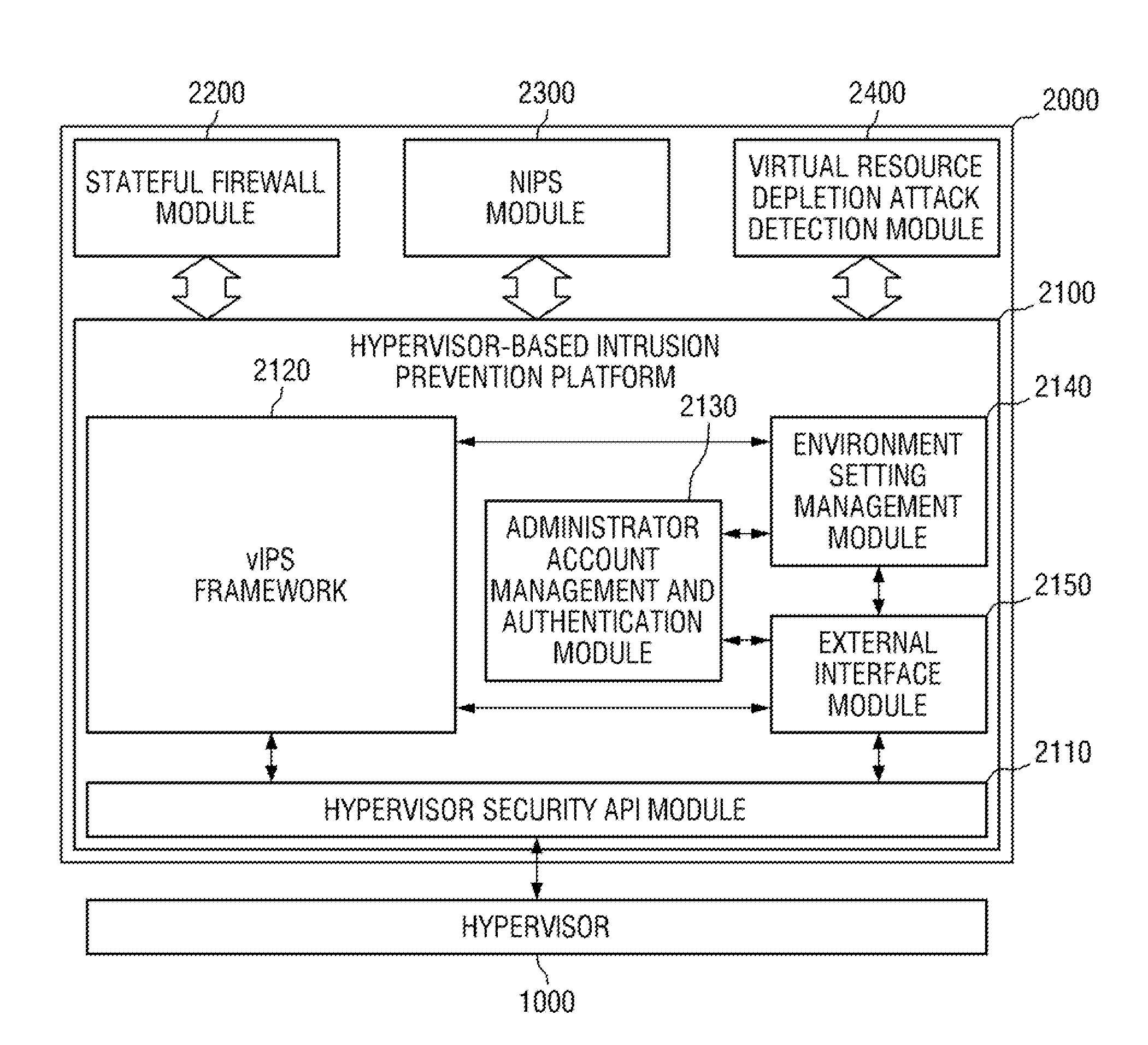
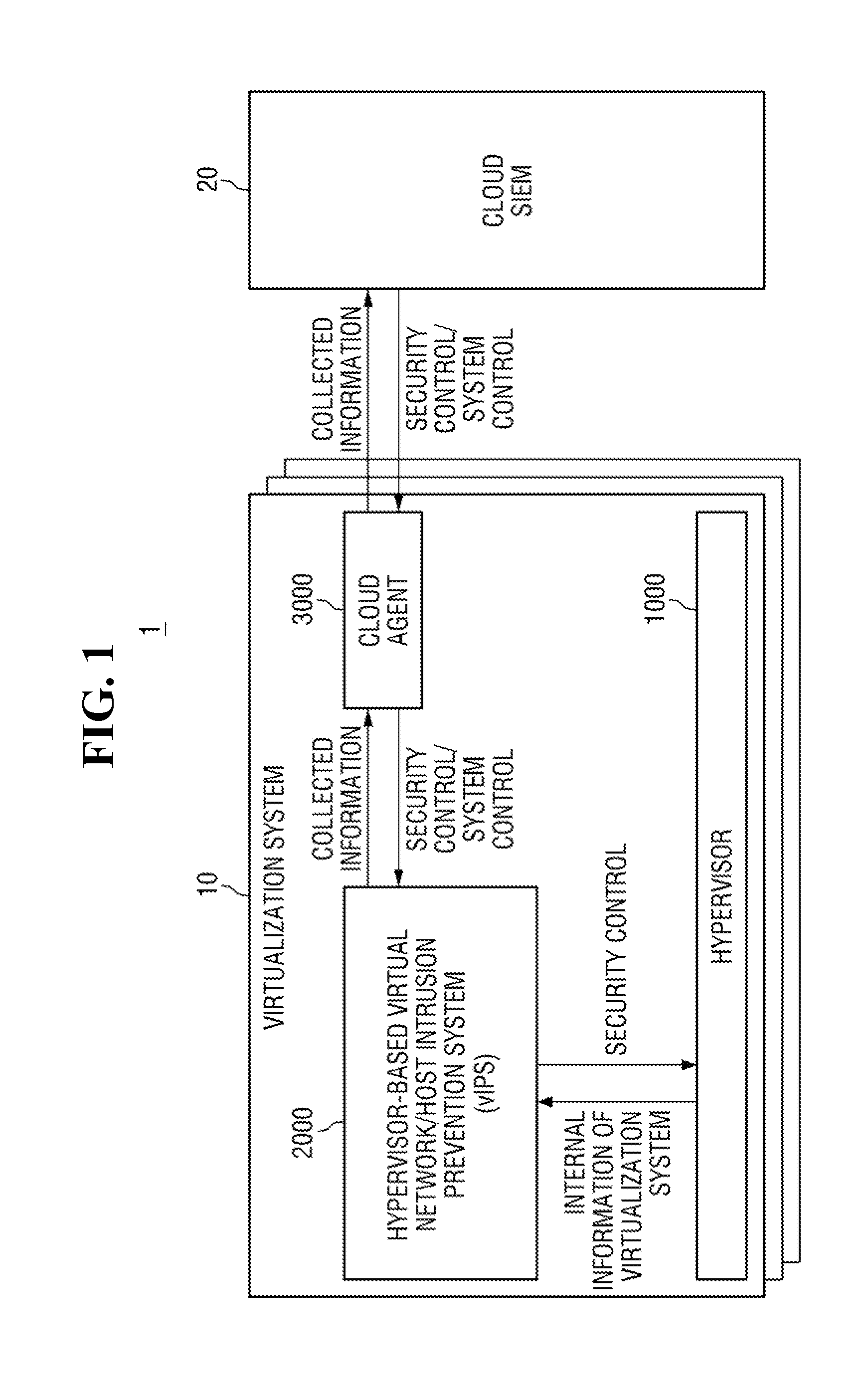
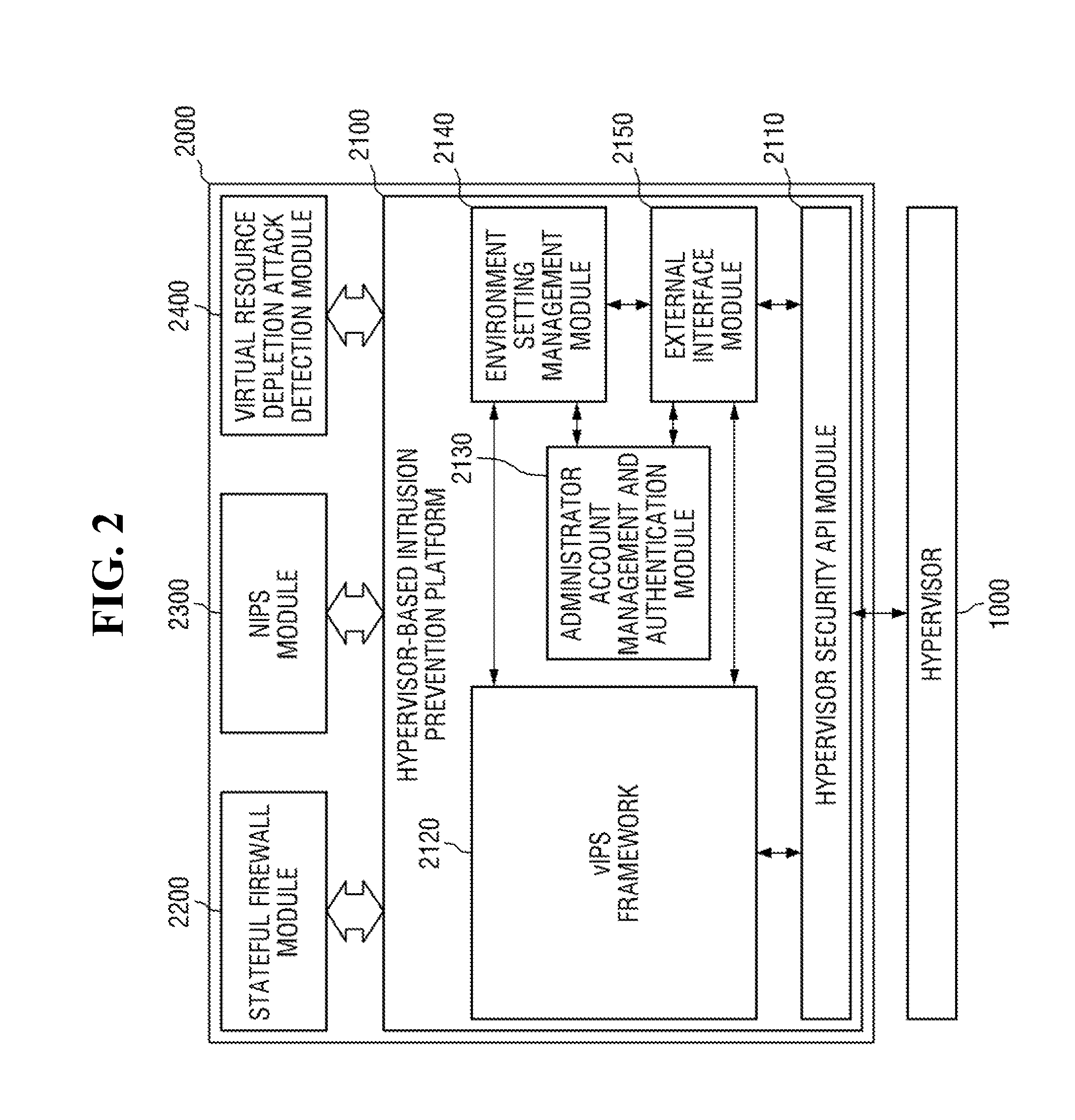
Hypervisor-based intrusion prevention platform and virtual network intrusion prevention system
InactiveUS20140317737A1Memory loss protectionData taking preventionApplication programming interfaceIntrusion prevention system
Hypervisor-based intrusion prevention platform is provided. The hypervisor-based intrusion prevention platform comprises a virtual network intrusion prevention system (vIPS) framework which obtains internal information of a virtualization system from a hypervisor and performs security control on the hypervisor in response to the result of intrusion detection carried out by using the internal information of the virtualization system, a hypervisor security application programming interface (API) module which provides an API used by the vIPS framework to access the hypervisor, an administrator account management and authentication module which manages an administrator account of a vIPS and authenticates the administrator account, an environment setting management module which manages environment setting values of modules within the vIPS, and an external interface module which provides an interface for system control and security control.
Owner:KOREA INTERNET & SECURITY AGENCY
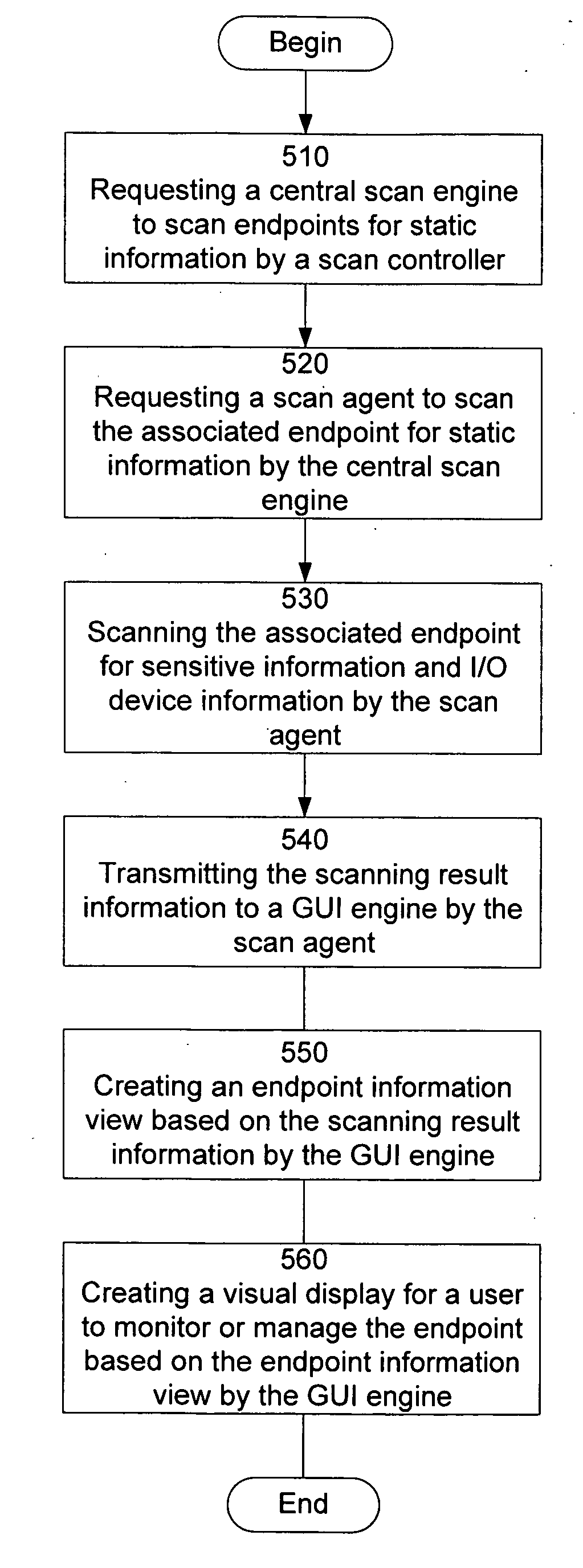
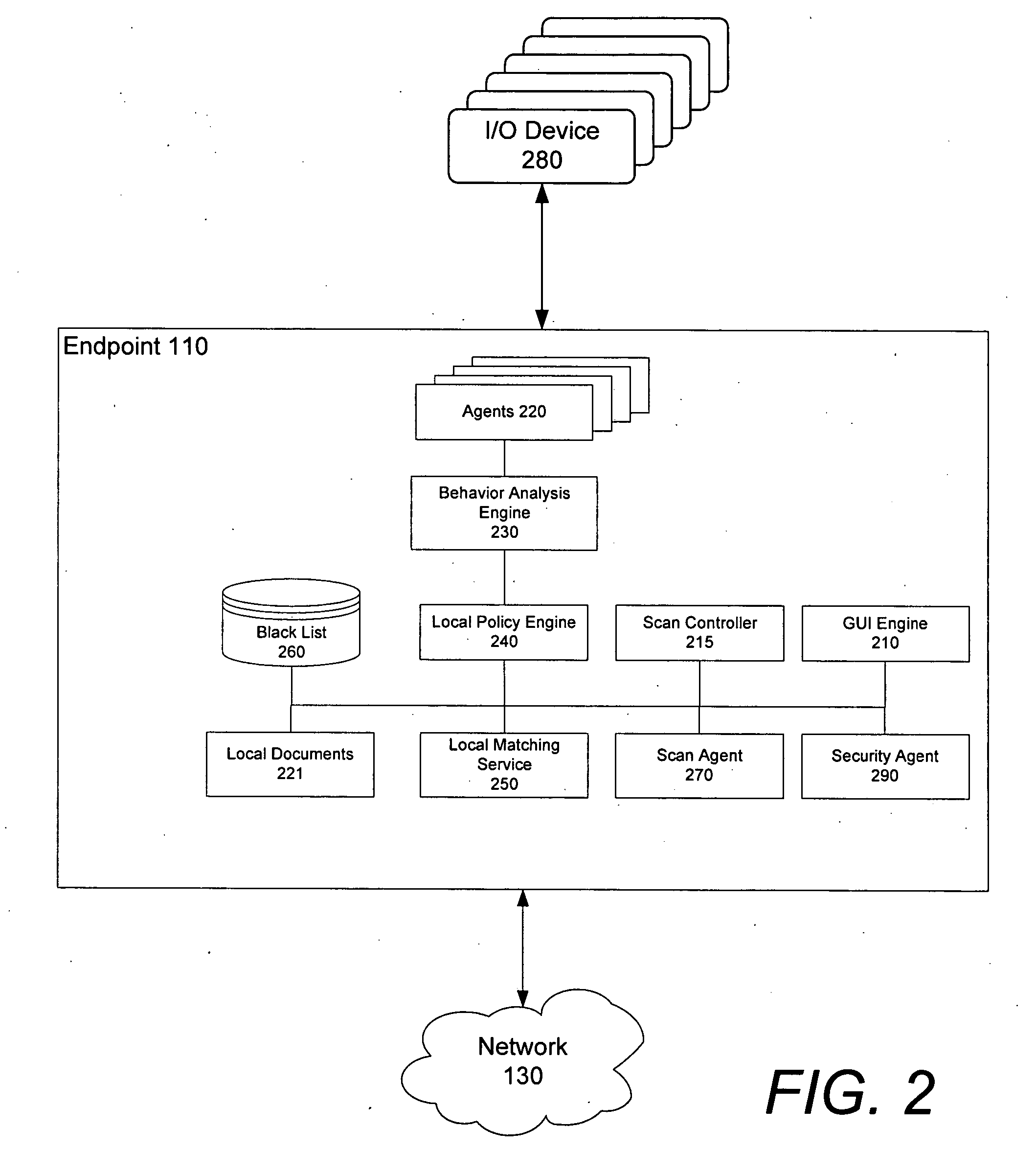
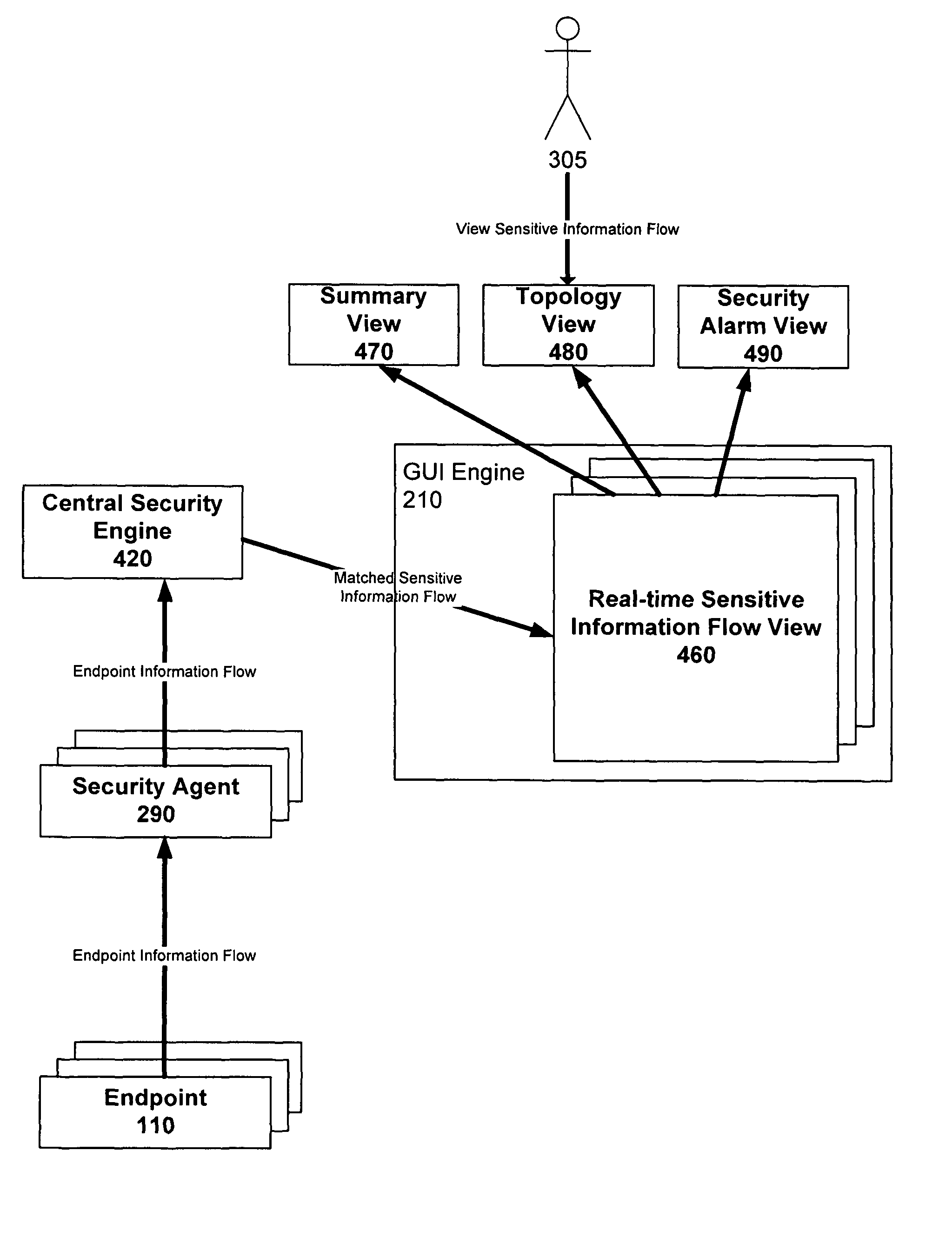
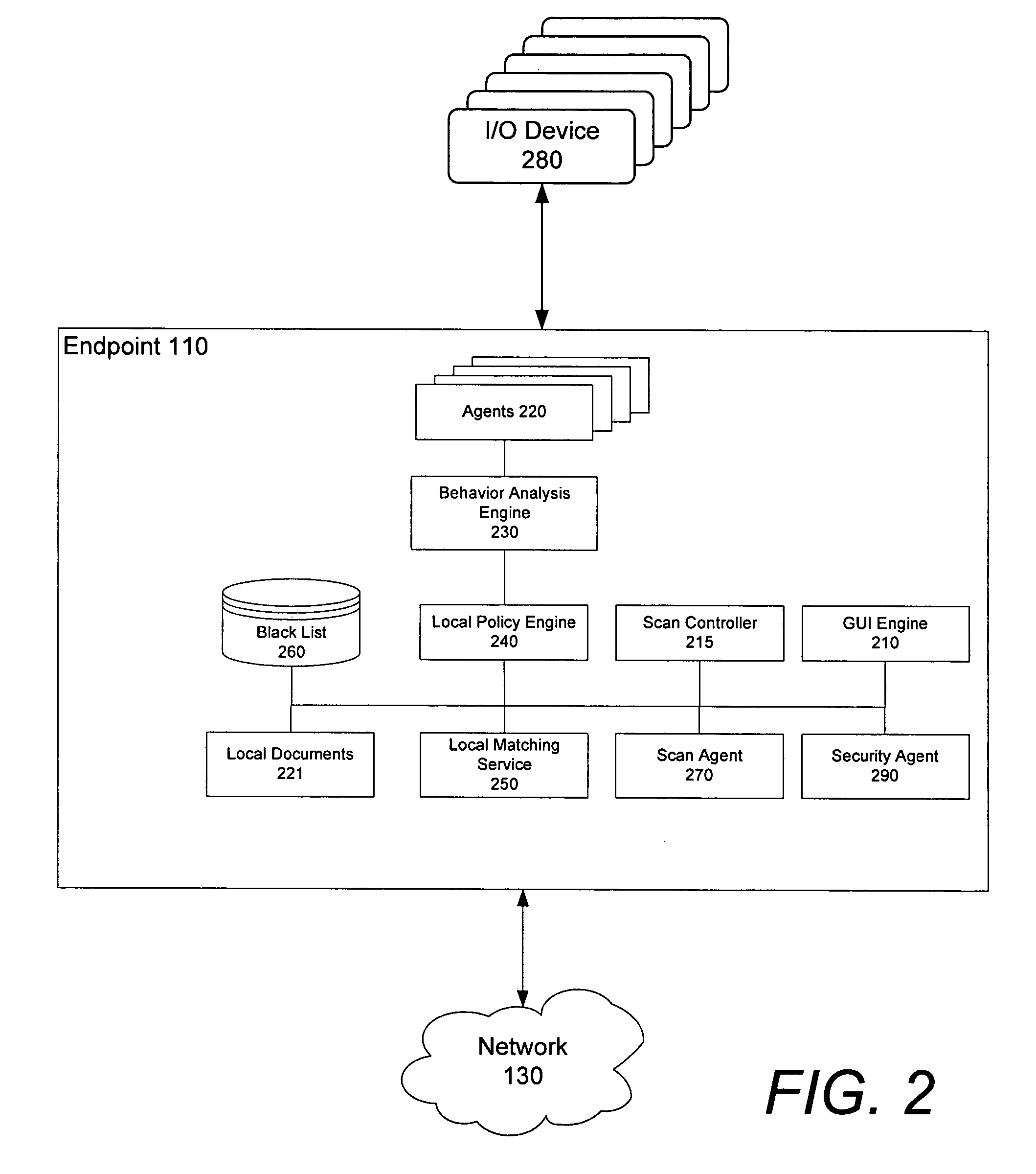
Graphical user interface based sensitive information and internal information vulnerability management system
ActiveUS20060272024A1Rapid assessmentEasy to identifyMemory loss protectionDigital data processing detailsTime informationGraphical user interface testing
A system and method provides a graphical user interface (GUI) for users to monitor and manage sensitive information within an enterprise network. The GUI can provide users with information, such as the presence of input / output devices (I / O device), the location of documents containing sensitive information (sensitive documents), and the status of local security policy. The GUI can also provide users with real-time information, such as the occurrence of local security policy violations, the life-cycle of sensitive documents, and the sensitive information dynamic flow within the enterprise network.
Owner:TREND MICRO INC
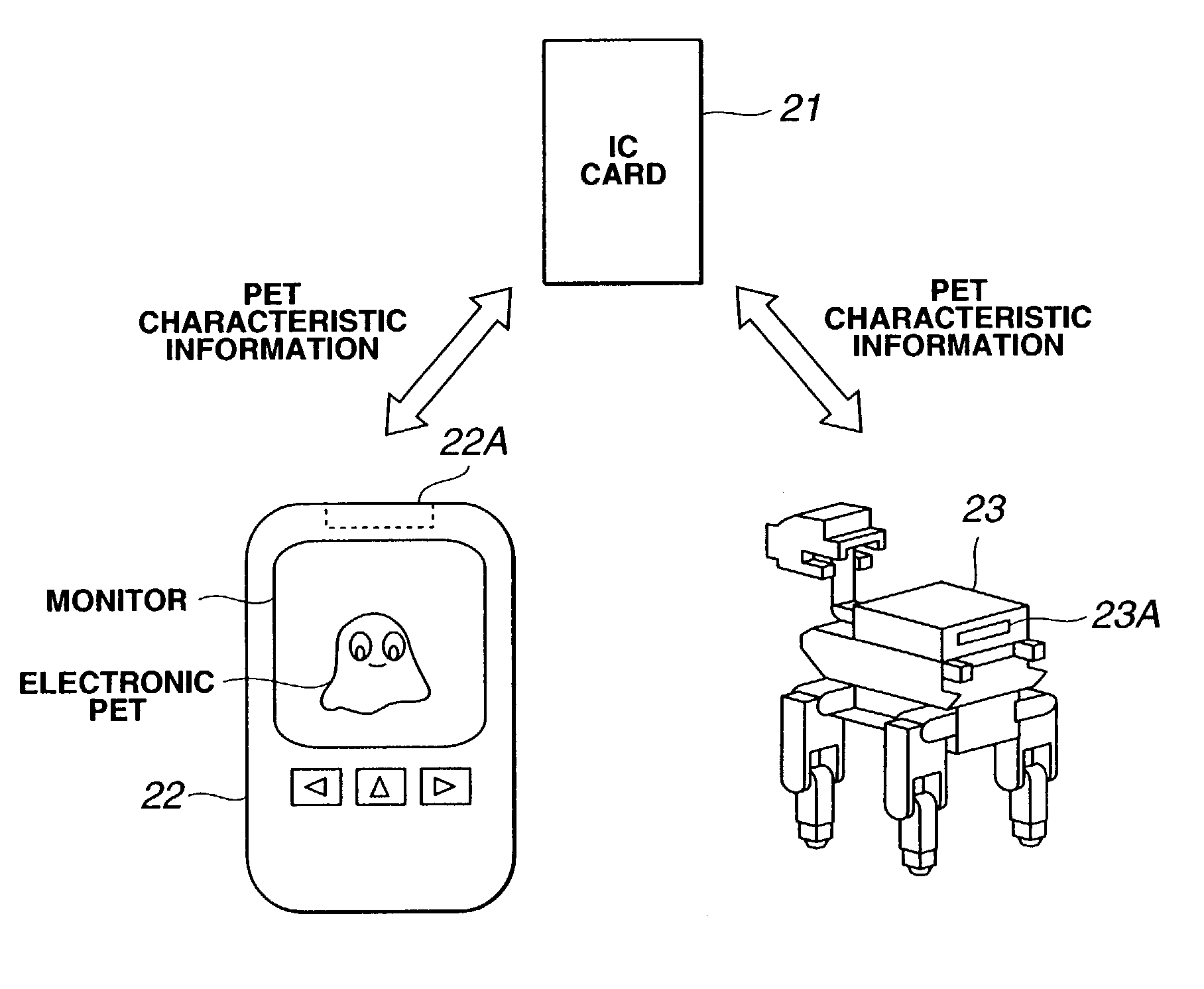
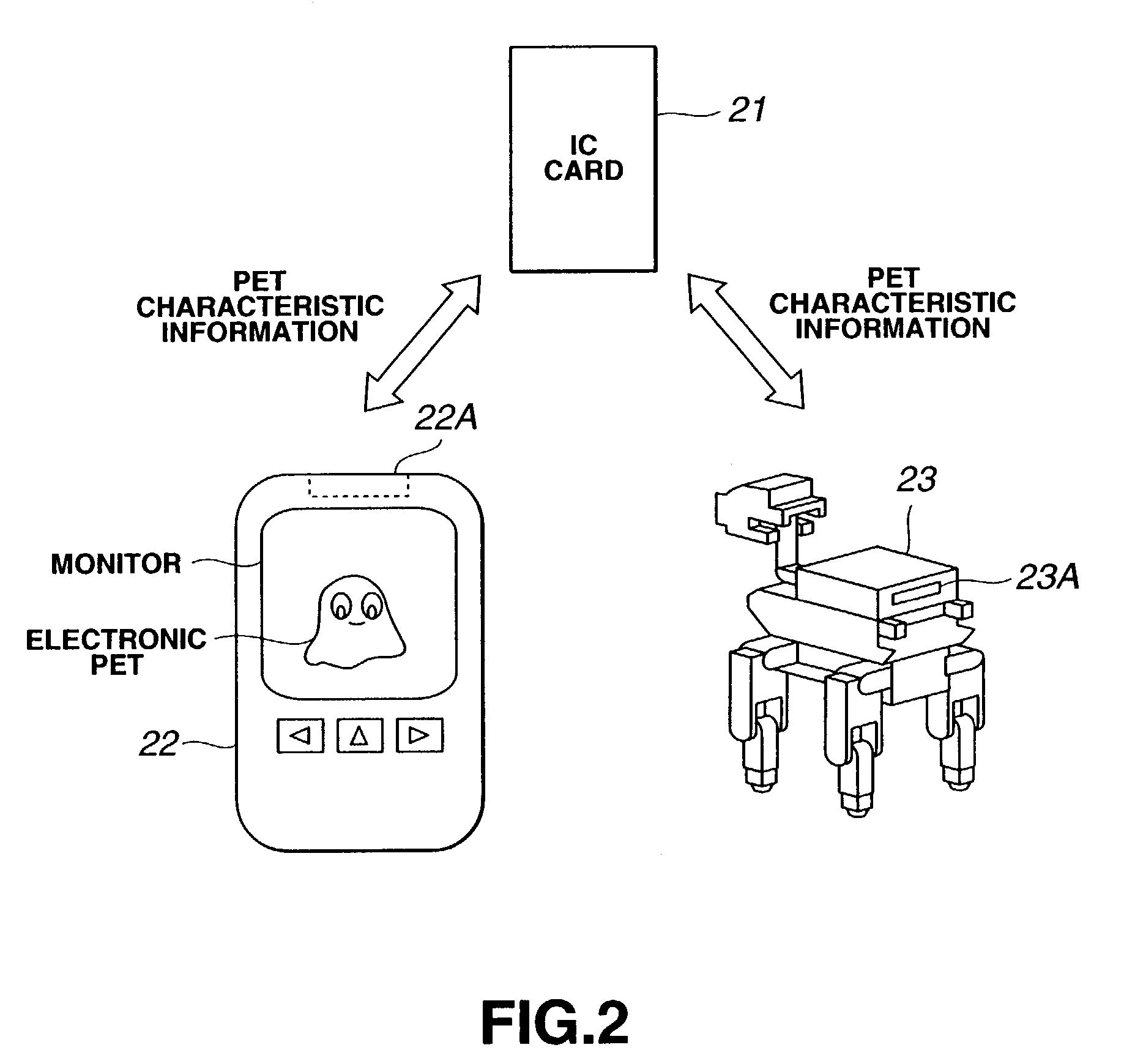
Electronic pet system, network system, robot, and storage medium
InactiveUS7089083B2Accurate loading positionProgramme-controlled manipulatorComputerized toysNetworked systemPersonal computer
Owner:SONY CORP
Information processing apparatus
InactiveUS20110030056A1Reduce loadMemory loss protectionError detection/correctionInformation processingInside information
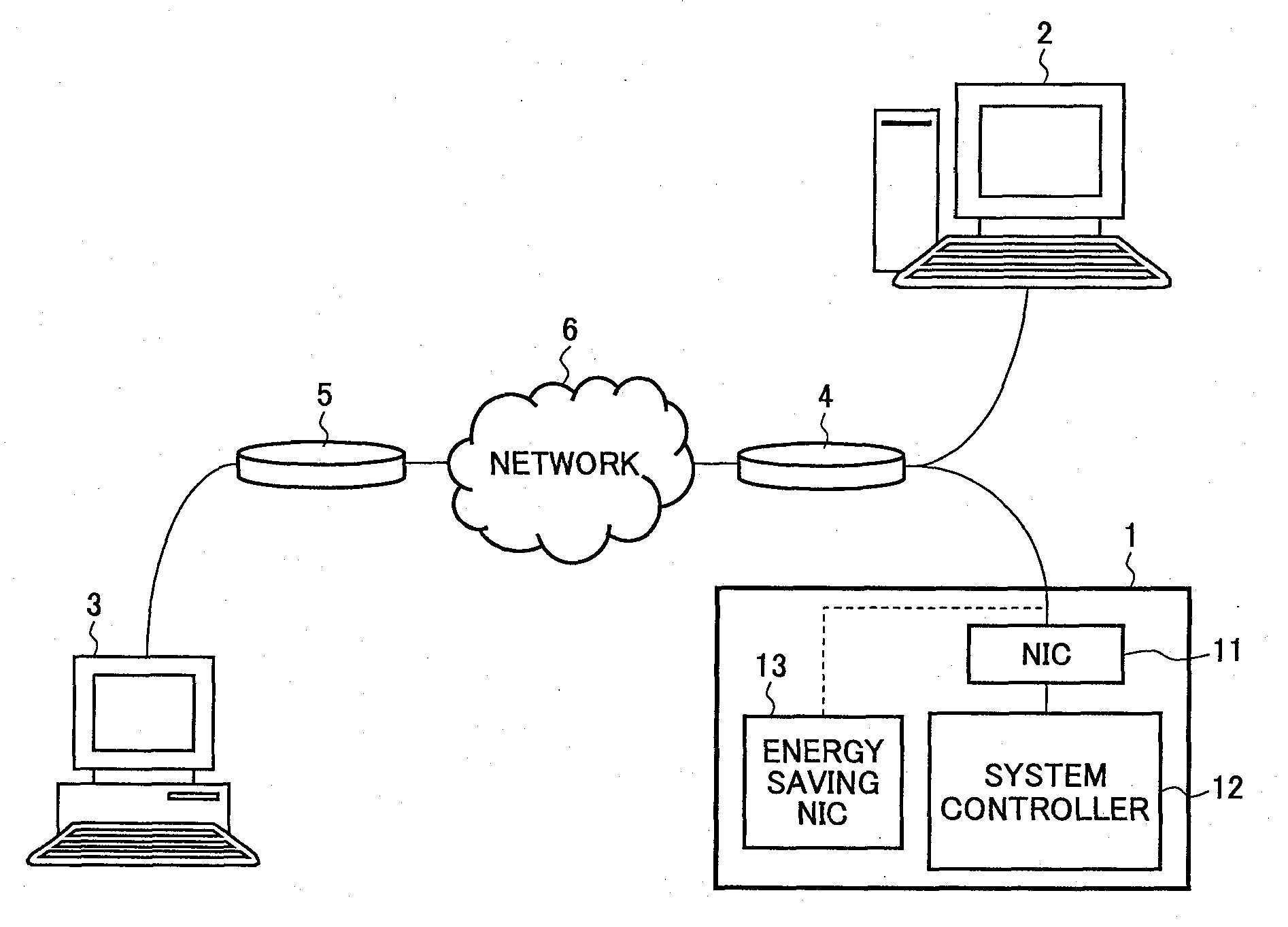
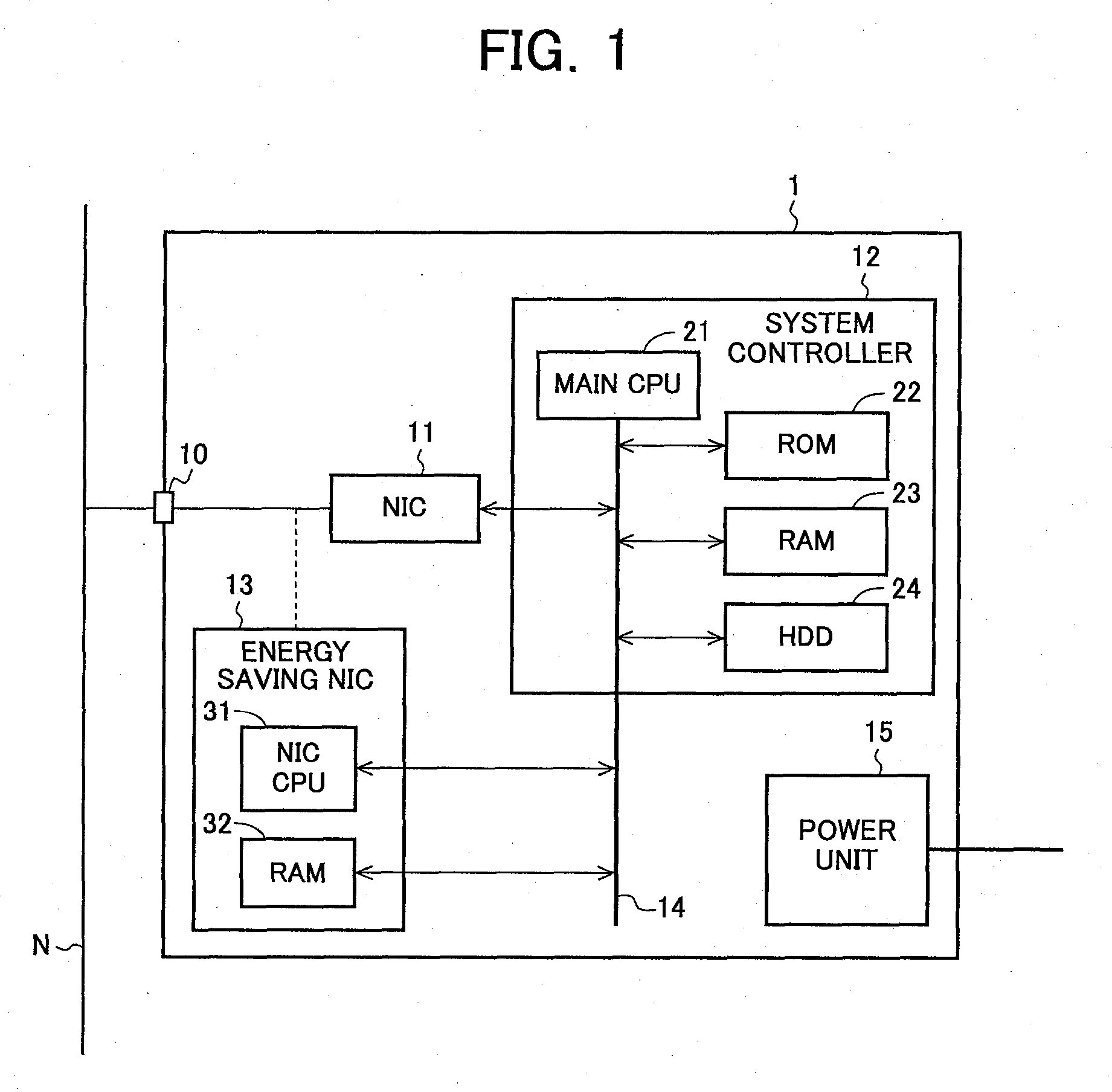
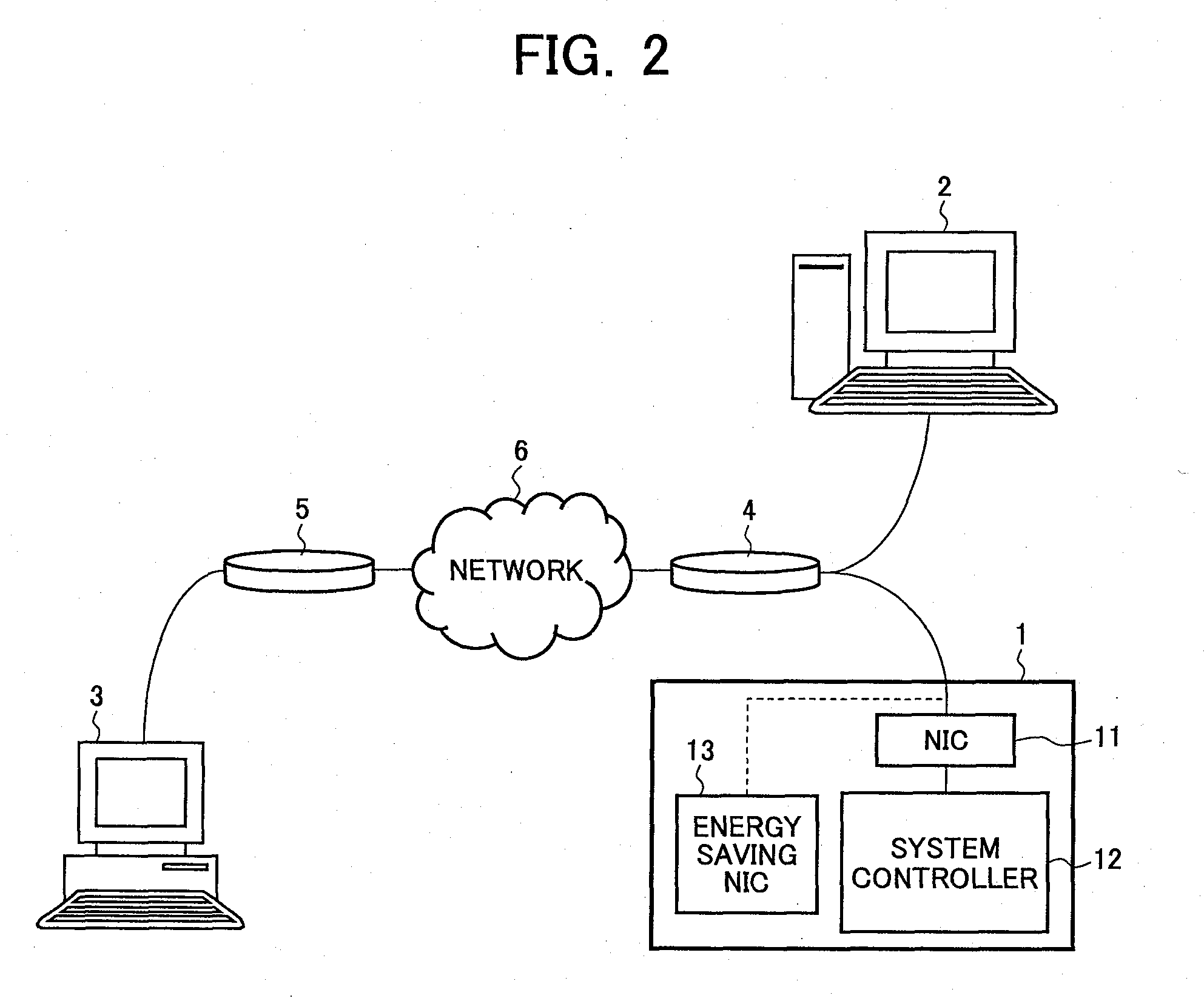
Provided is an information processing apparatus capable of protecting against an unauthorized access from outside without increasing load of packet analysis and also capable of performing protection from a device inside a network. The information processing apparatus has a first network interface (illustrated using an NIC as an example) and is communicable with other information processing apparatus via the NIC. The information processing apparatus further has a second network interface (illustrated using an energy saving NIC as an example) for performing communication with other information processing apparatus in place of the NIC. The information processing apparatus executes switching processing for switching a network interface to be operated from the NIC to the energy saving NIC when an unauthorized access from outside is detected. At the time of the switching processing, internal information of the information processing apparatus is saved in the energy saving NIC.
Owner:SHARP KK
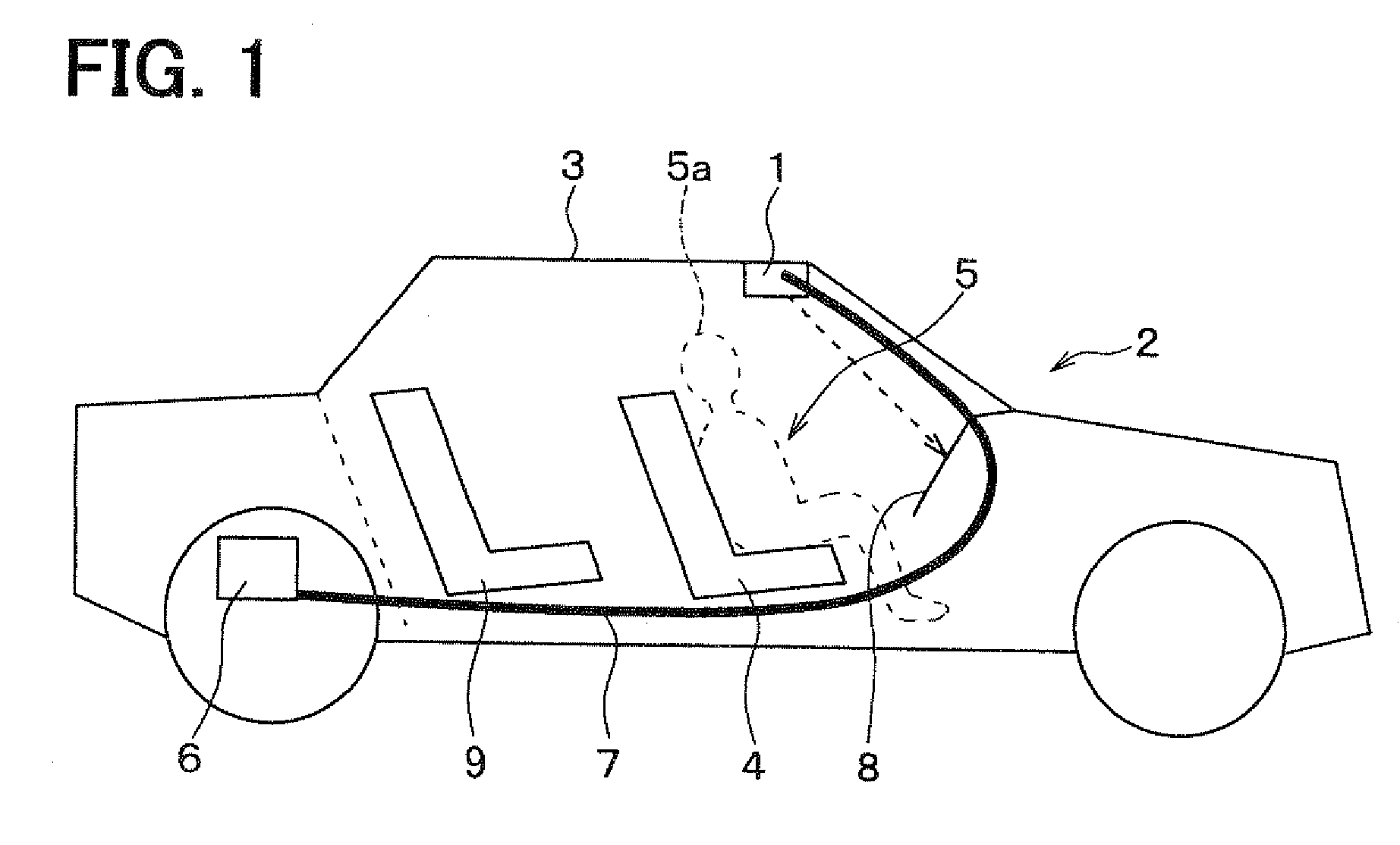
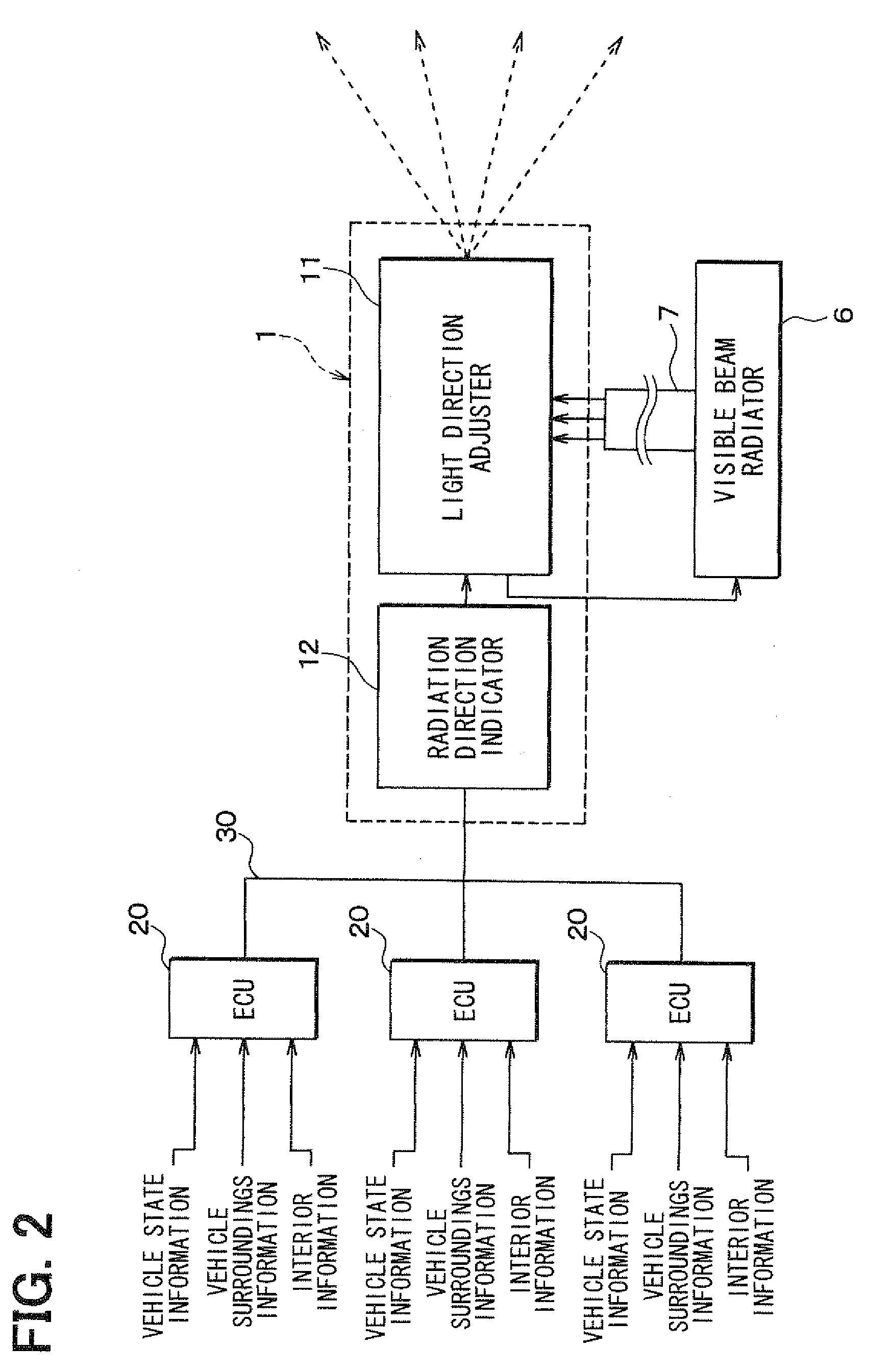
Interior information display apparatus and light irradiation apparatus used for the same
ActiveUS20100295670A1Raise the possibilityEffective displaySteering partsDashboard lighting devicesLight irradiationEngineering
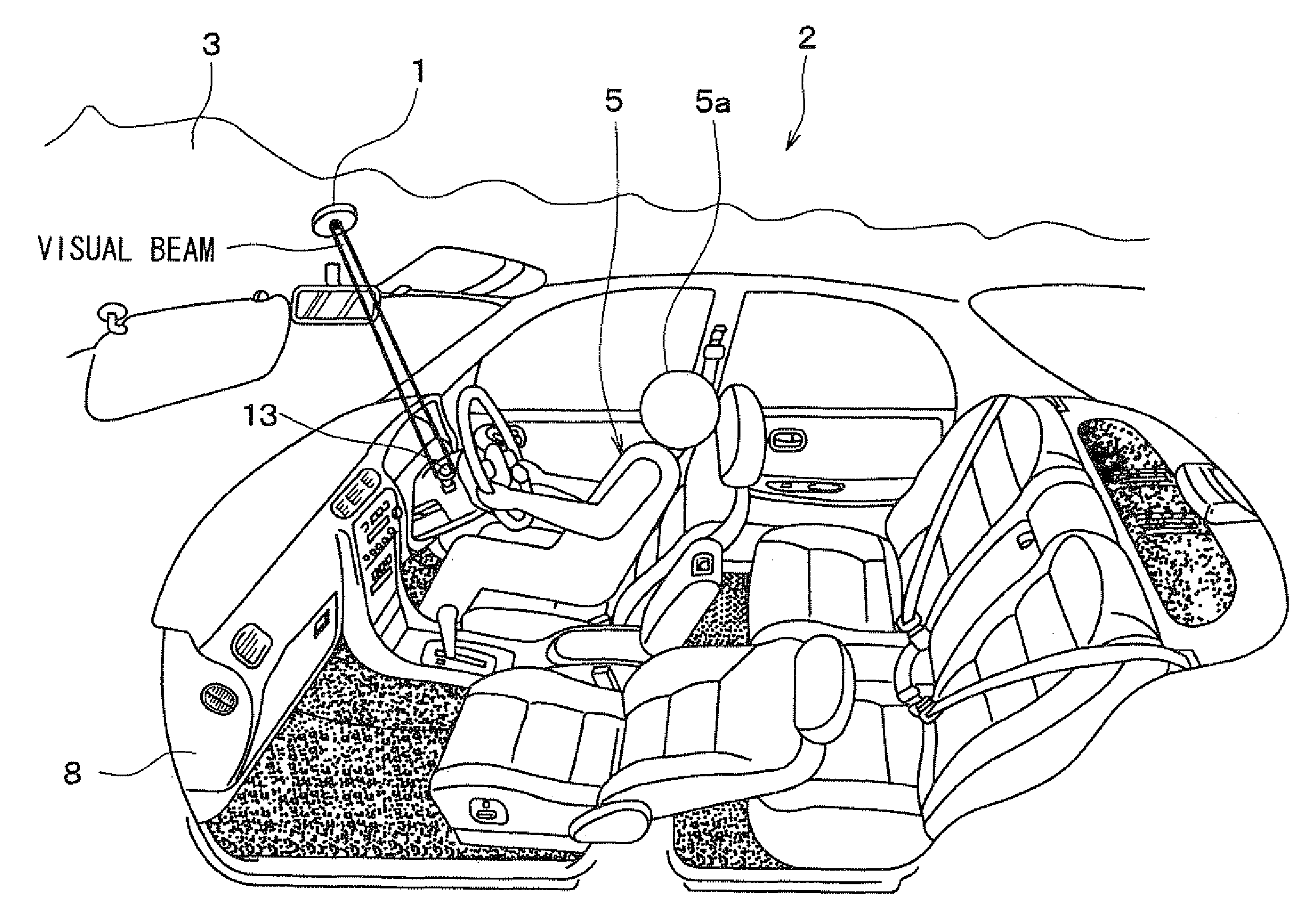
Information is displayed by irradiating a visible light on a specific position based on at least one of vehicle state information, vehicle surrounding information, and vehicle interior information. For example, the visible light is irradiated on a target switch based on signals indicating an on / off state of a headlamp operation switch and an on / off state of a key switch. A user 5 can easily confirm the target switch and unerringly operate the target switch. A visible light irradiator 6 is arranged in a vehicle compartment and irradiates the visible light to display information in the vehicle compartment. The information can be provided for the user 5 in a novel manner.
Owner:DENSO CORP
System for establishing a cryptographic key depending on a physical system
ActiveUS20120072737A1Reduction of informationReduce decreaseKey distribution for secure communicationDigital data processing detailsComputer hardwareCryptographic nonce
In systems for establishing a cryptographic key depending on a physical uncloneable function (PUF) it may be a problem that internal information correlated with the cryptographic key is leaked to the outside of the system via a side-channel. To mitigate this problem a cryptographic system for reproducibly establishing a cryptographic key is presented. The system comprises a physical system comprising a physical, at least partially random, configuration of components from which an initial bit-string is derived. An error corrector corrects deviations occurring in the initial bit-string. Through the use of randomization the error corrector operates on a randomized data. Information leaking through a side channel is thereby reduced. After error correction a cryptographic key may be derived from the initial bit-string.
Owner:INTRINSIC ID
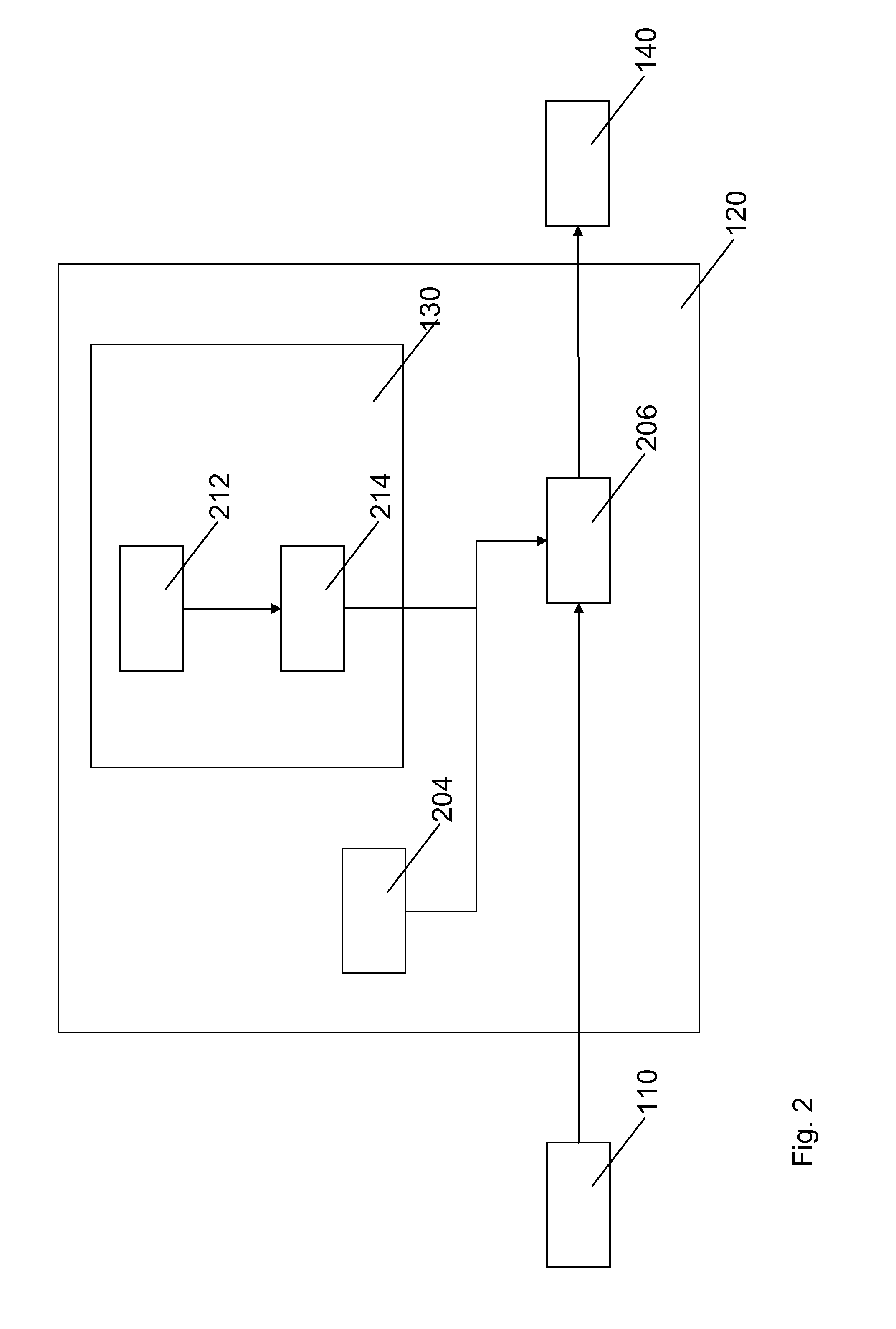
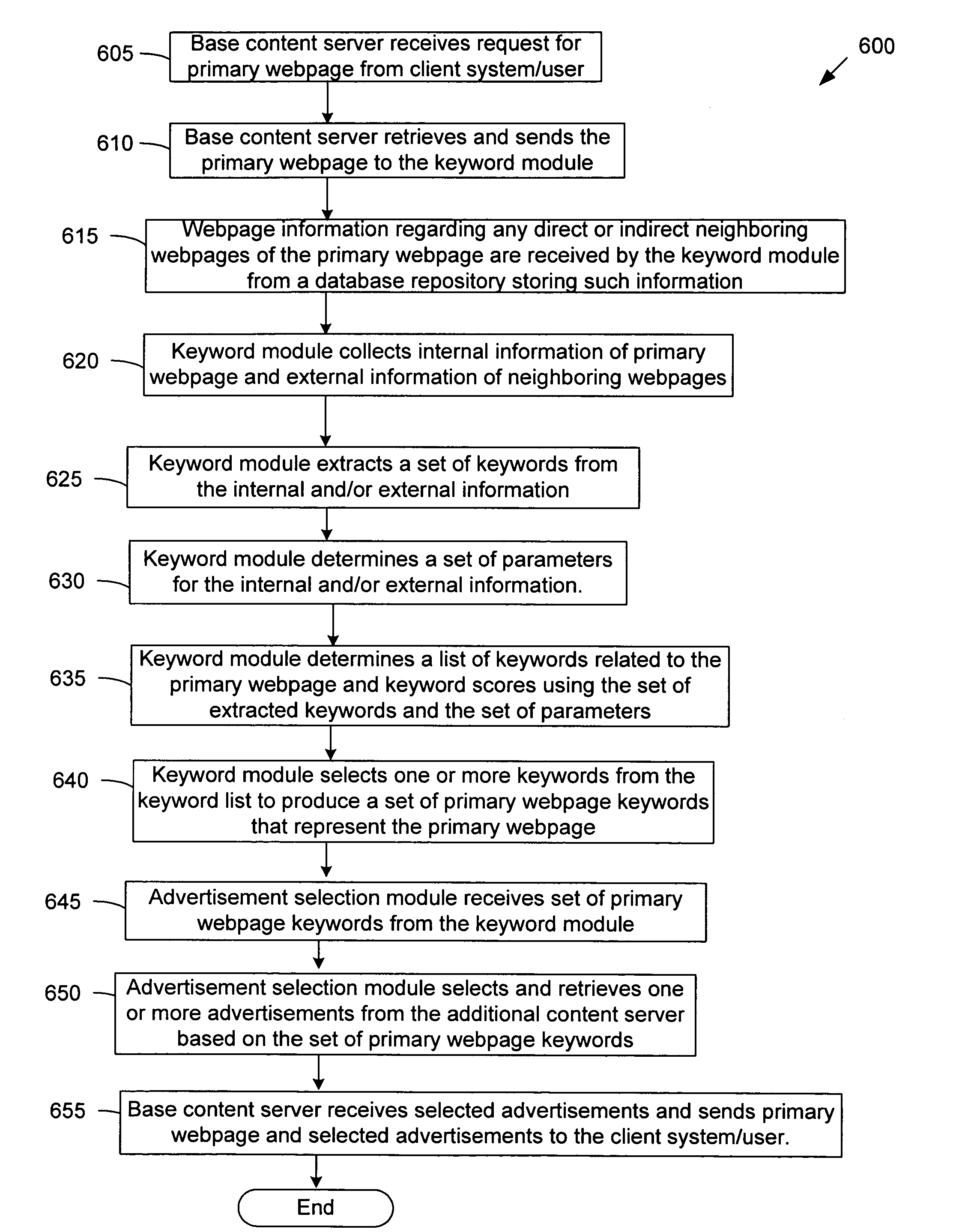
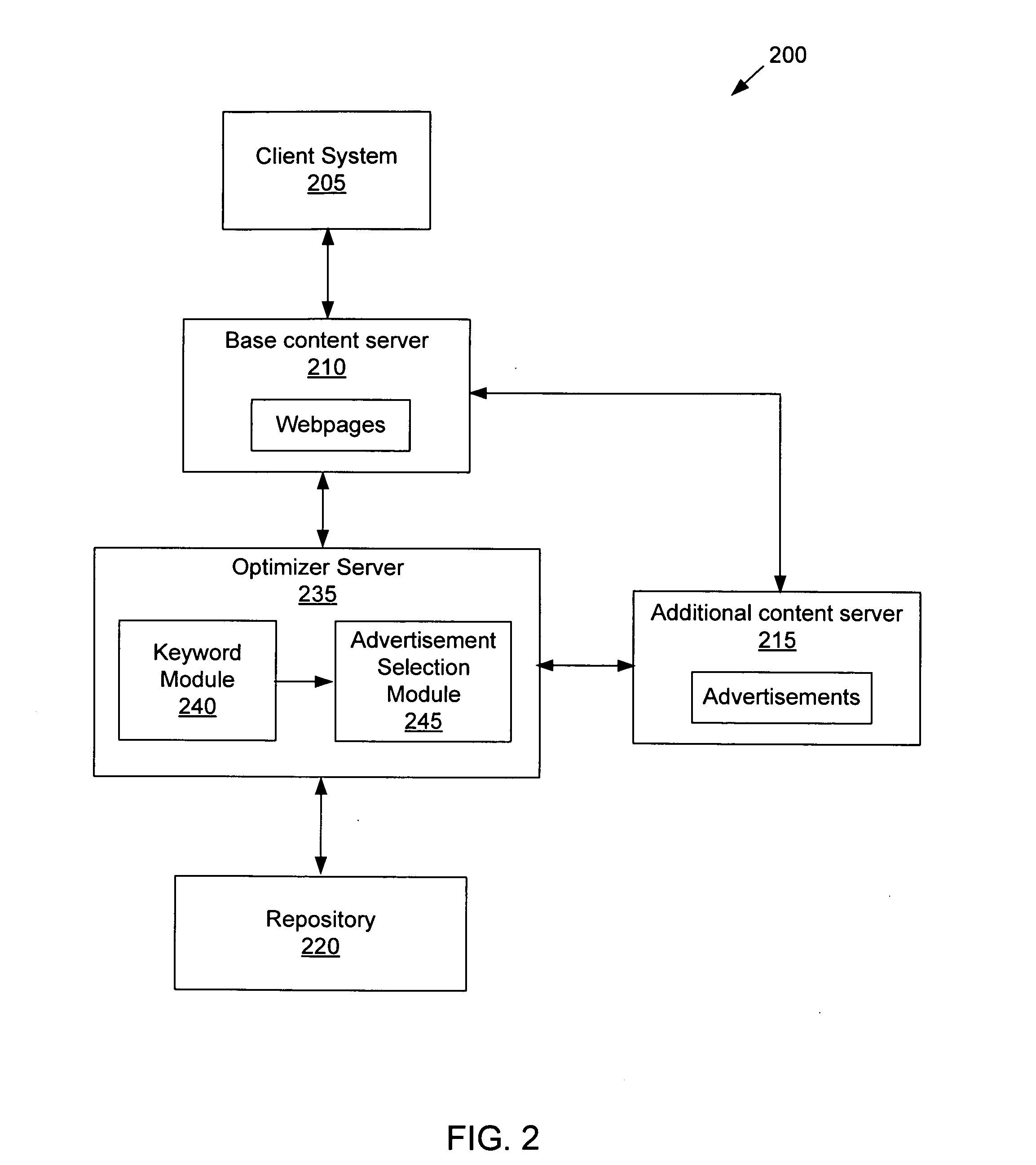
Serving advertisements based on keywords related to a webpage determined using external metadata
InactiveUS20080027798A1Improve accuracyMaximize advertiser revenueAdvertisementsHyperlinkInside information
Methods and apparatus for selecting advertisements to display to a user requesting a primary webpage is provided. Keywords related to the primary webpage are determined using internal information of the primary webpage and / or external information provided in neighboring webpages. The external information may include anchor text metadata of hyperlinks on neighboring webpages that link to the primary webpage or include the number of such hyperlinks having a same particular anchor text. Other internal and / or external information may be used to determine a list of keywords related to the primary webpage. One or more of keywords on the list are selected to represent the primary webpage according to one or more objectives. One or more advertisements are selected to be served to the user using the selected keywords. Machine learning techniques may be used to develop a model that automatedly determines keywords representing a webpage.
Owner:YAHOO INC
System and method for sensing local driving environment in front
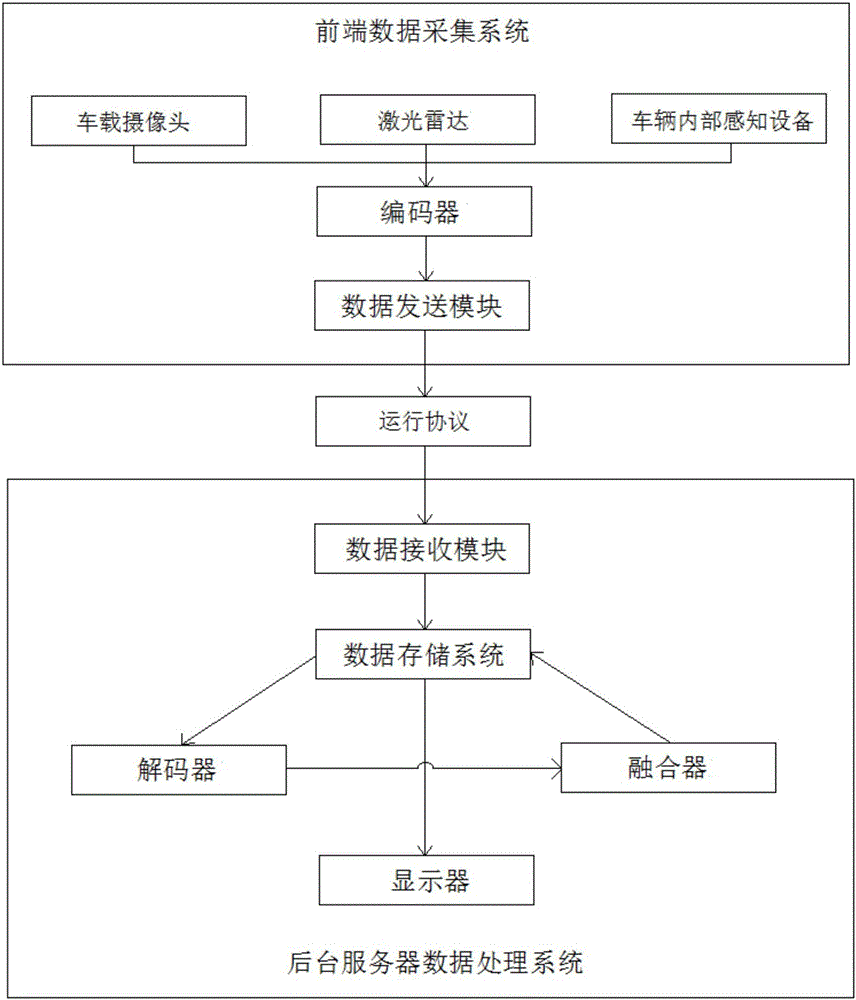
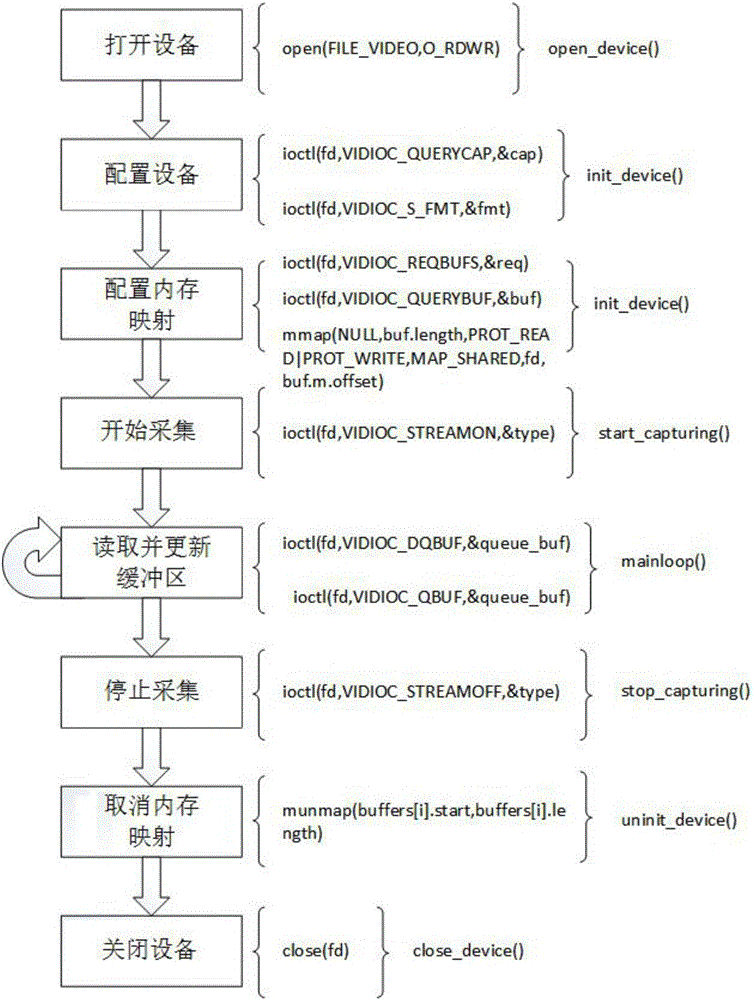
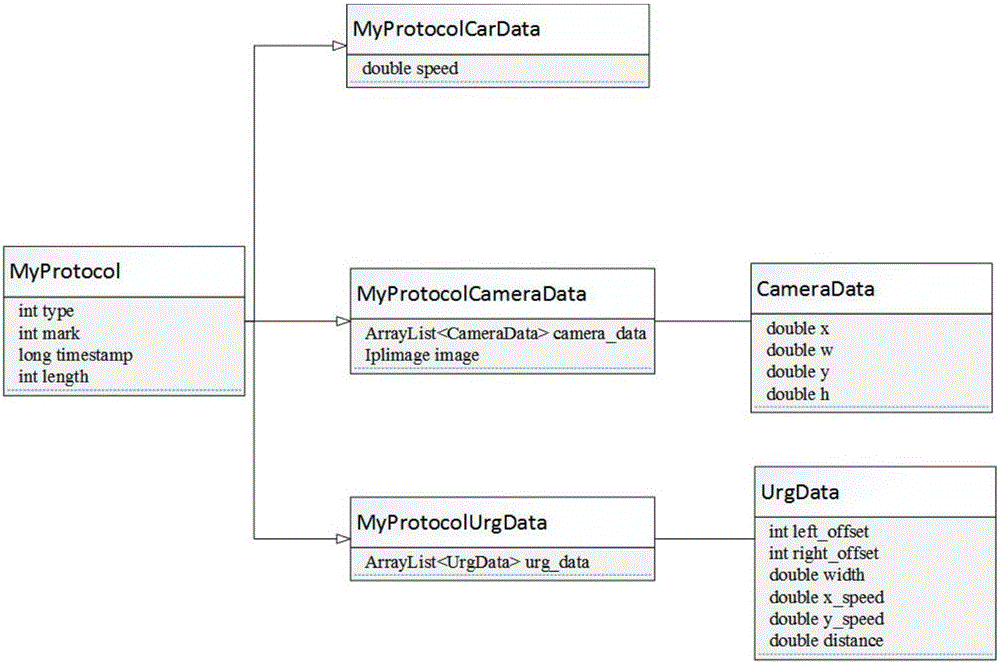
The invention provides a system and a method for sensing a local driving environment in the front. The system comprises a front-end data acquisition system and a background server data processing system, wherein the front-end data acquisition system comprises a vehicle-mounted camera, a laser radar and vehicle interior sensing equipment, wherein the camera is used for sensing pedestrians and lane lines in front of a running vehicle; the laser radar is used for sensing and extracting information of obstacles such as a vehicle in the front; the vehicle interior sensing equipment is used for acquiring running state parameters of the vehicle. Three data transmission types of MyProtocolCarData, MyProtocolCameraData and MyProtocolUrgData are defined, a data format is unified for encoding, and then camera information data, laser radar information data and vehicle interior information data are transmitted to a background server for decoding to integrate three kinds of sensor data into a frame of complete local traffic environment information which is saved into a data storage system, and a function for analyzing and visualizing data of the local driving environment in the front is provided. By real-time and efficient sensing of the local driving environment in the front, rear-end collision accidents are reduced, and the traffic safety is improved.
Owner:潍柴(扬州)特种车有限公司
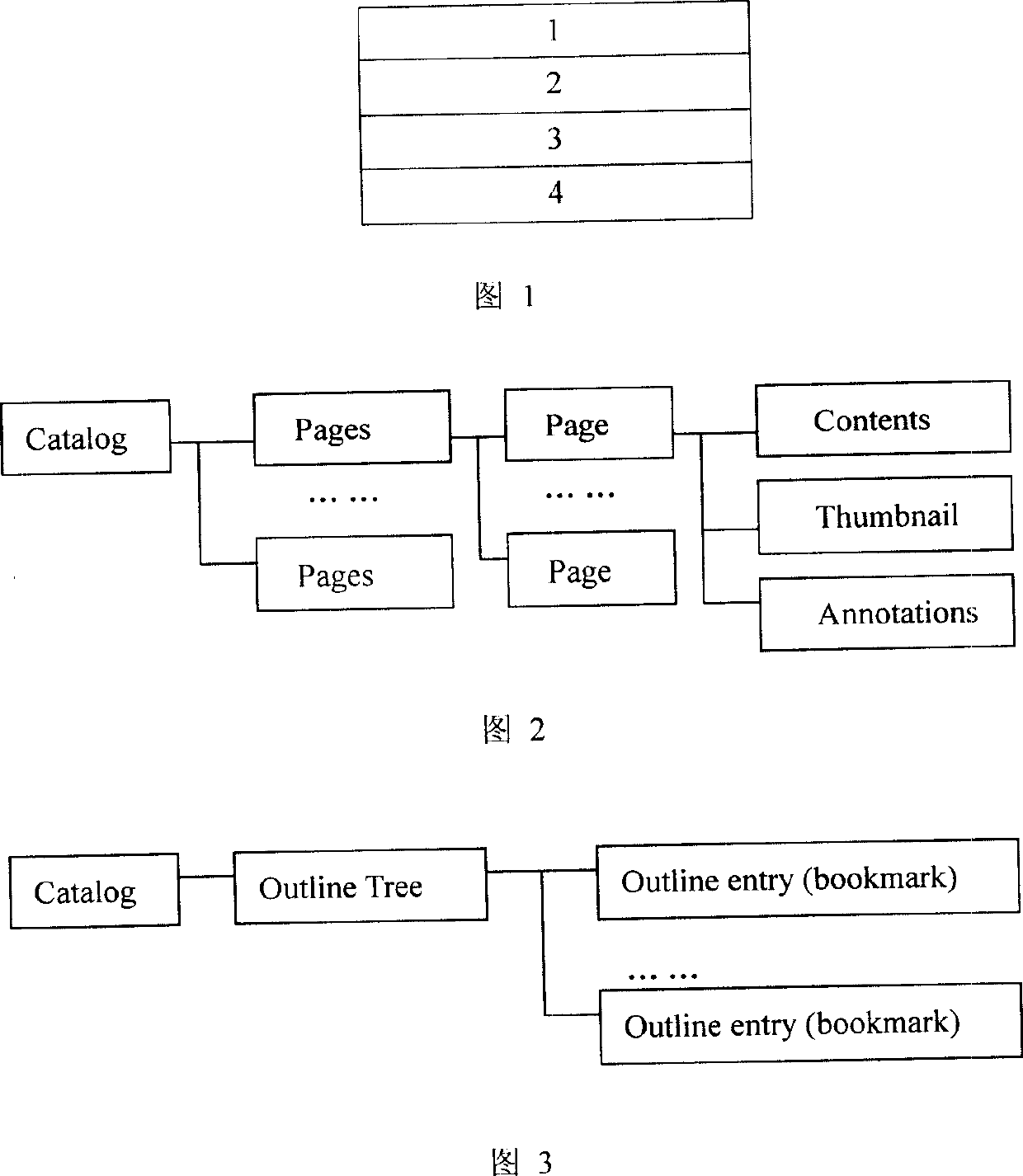
Method of PDF file information extraction system based on XML
InactiveCN1687926AImprove automatic classificationImprove retrieval efficiencySpecial data processing applicationsDocumentationXML
The invention discloses a method for XML-based PDF document information drawing system, an information converting method, belonging to the class of information technique and including the steps: (1) designing DTD, i.e. firstly analyzing and selecting external information cell data and internal information cell data; (2) drawing the semantic information of the PDF document, i.e. firstly drawing the content flow of each page stored in the PDF document for decoding, and then converting the physical structure of the PDF document to a logic structure, and finally drawing the external information cell data and internal information cell data; (3) generating a XML document. The invention can further process the XML document, thus raising the efficiencies of automatically classifying documents and searching user information.
Owner:FUZHOU UNIV
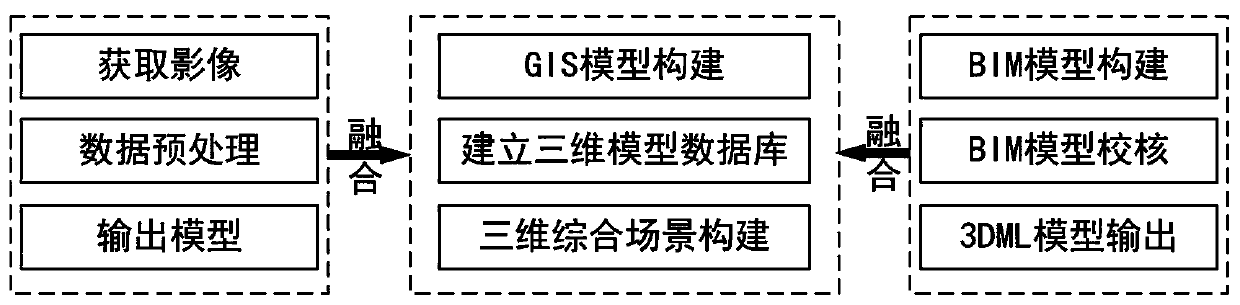
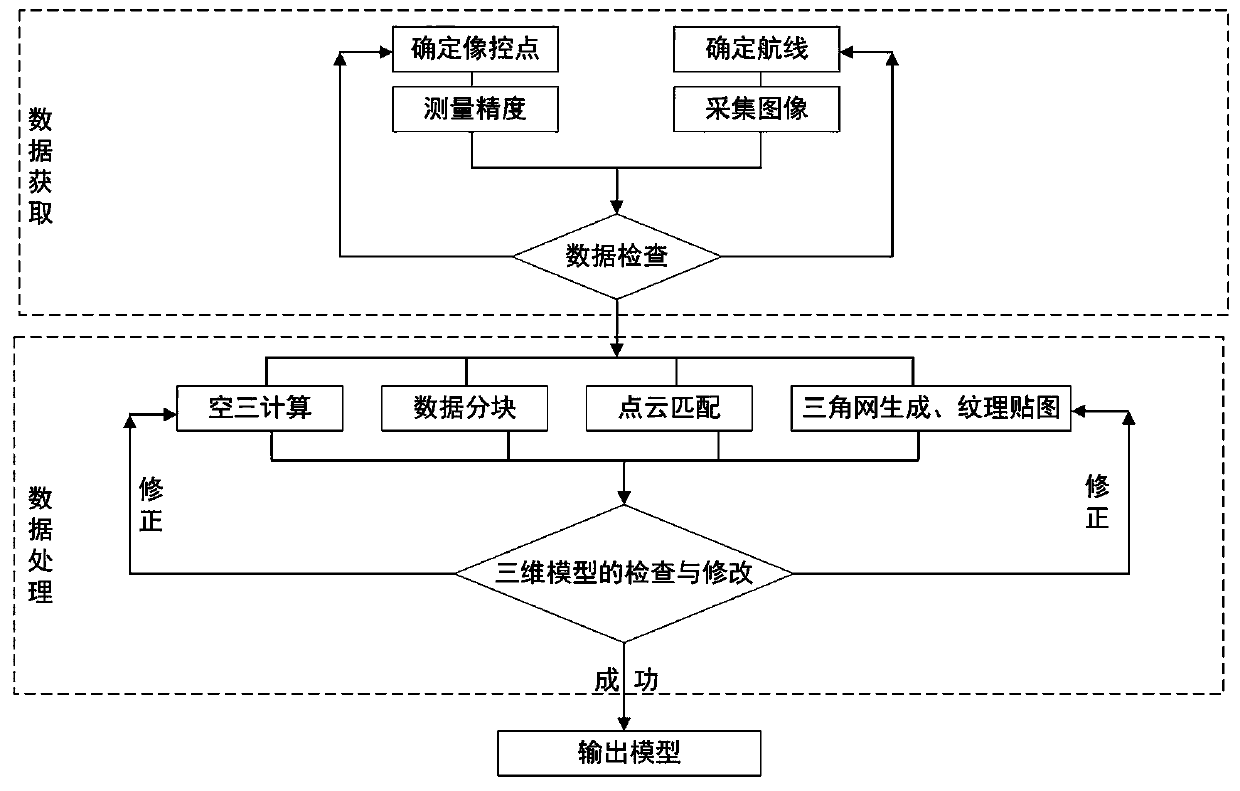
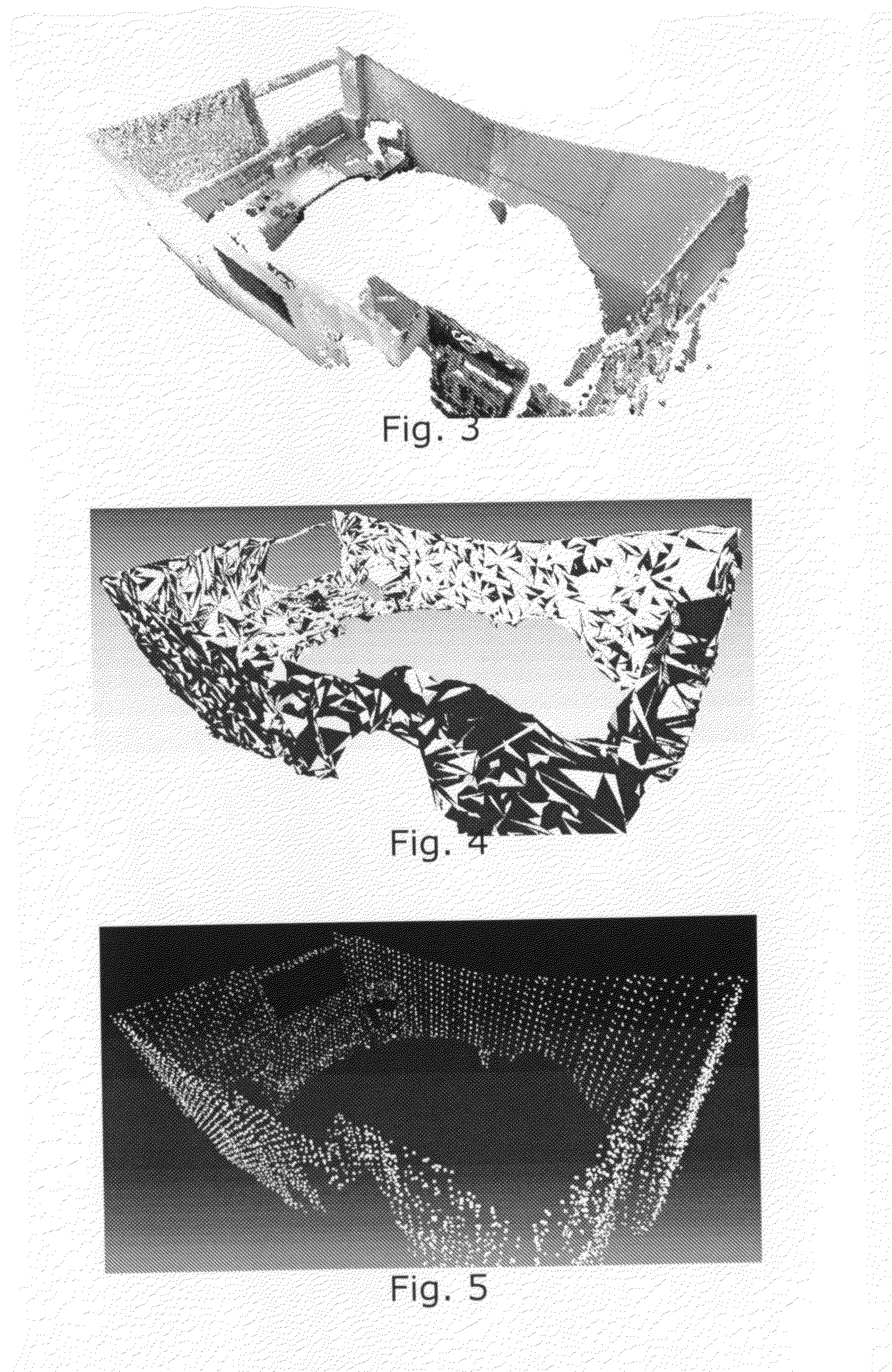
Three-dimensional modeling technology based on oblique photography assisted BIM and GIS
InactiveCN110136259AHigh precisionIncrease authenticity3D modellingDimensional modelingHigh resolution image
Owner:TANGSHAN IND VOCATIONAL TECHN COLLEGE
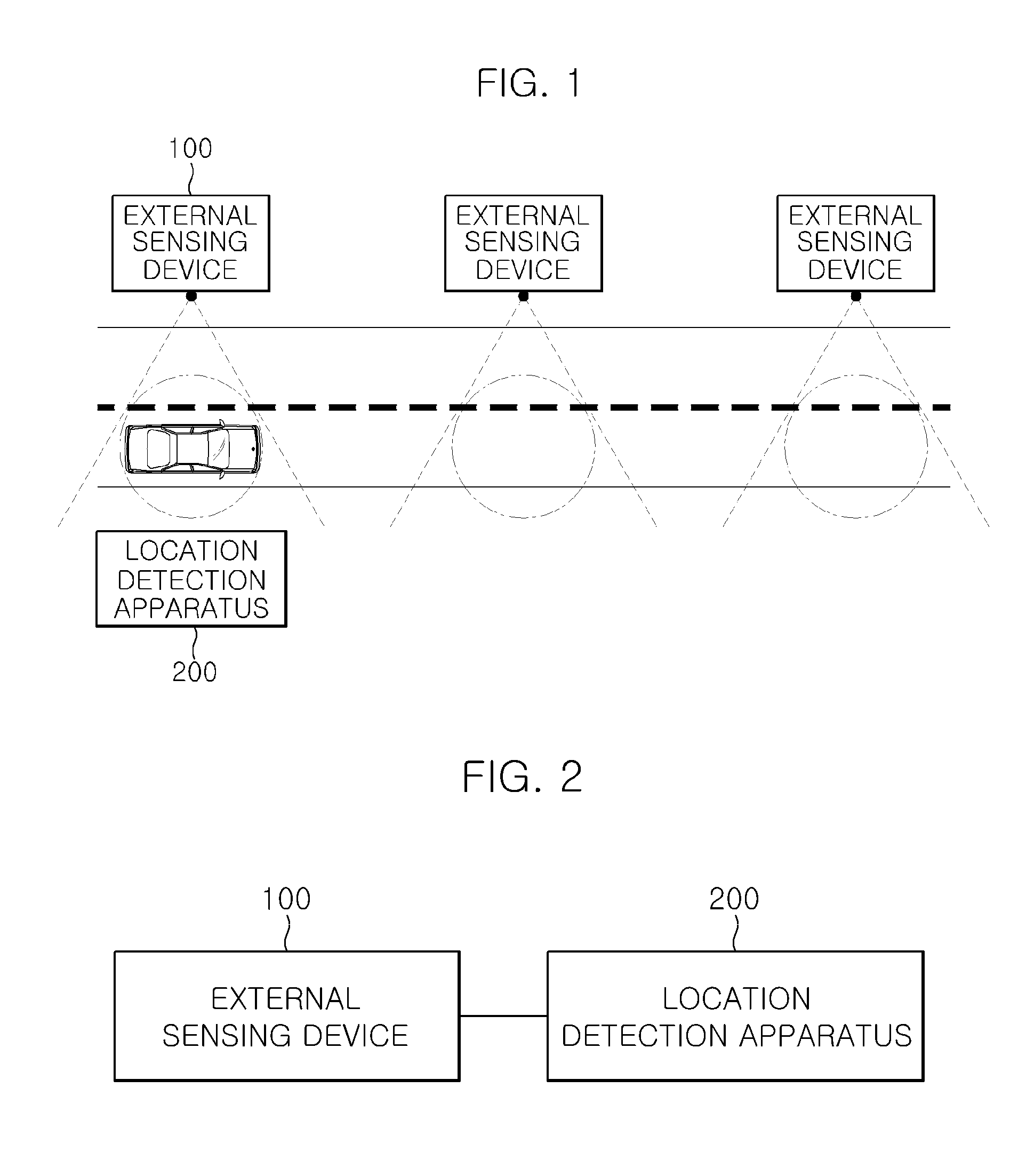
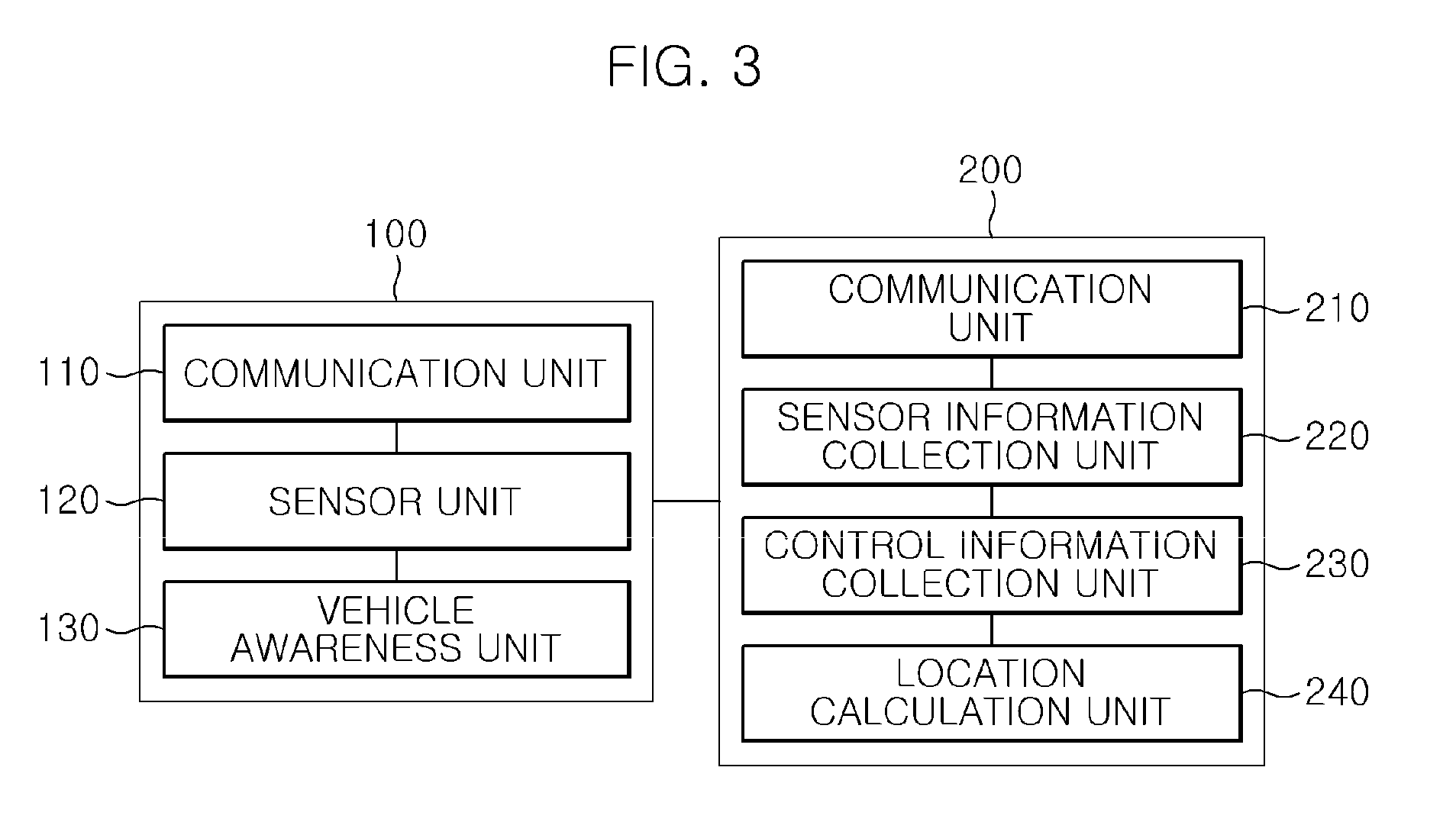
Apparatus and method for detecting location of vehicle
InactiveUS20120185112A1Intensity of signal is weakImprove errorRoad vehicles traffic controlDigital data processing detailsLocation detectionEngineering
Disclosed herein is an apparatus and method for detecting the location of a vehicle using results sensed by sensing devices installed outside the vehicle and the internal information of the vehicle without obtaining the current location information of the vehicle using signals transmitted from a Global Positioning System (GPS) satellite. The apparatus for detecting the location of a vehicle includes a location information reception unit for receiving location information that is generated by sensing a vehicle passing by a sensing point and that corresponds to the sensing point. A location detection unit estimates a current location of the vehicle based on information sensed by internal sensors of the vehicle and control information for a vehicle manipulation part while the location information is not received, and corrects the estimated current location of the vehicle using received location information when the location information is received.
Owner:ELECTRONICS & TELECOMM RES INST
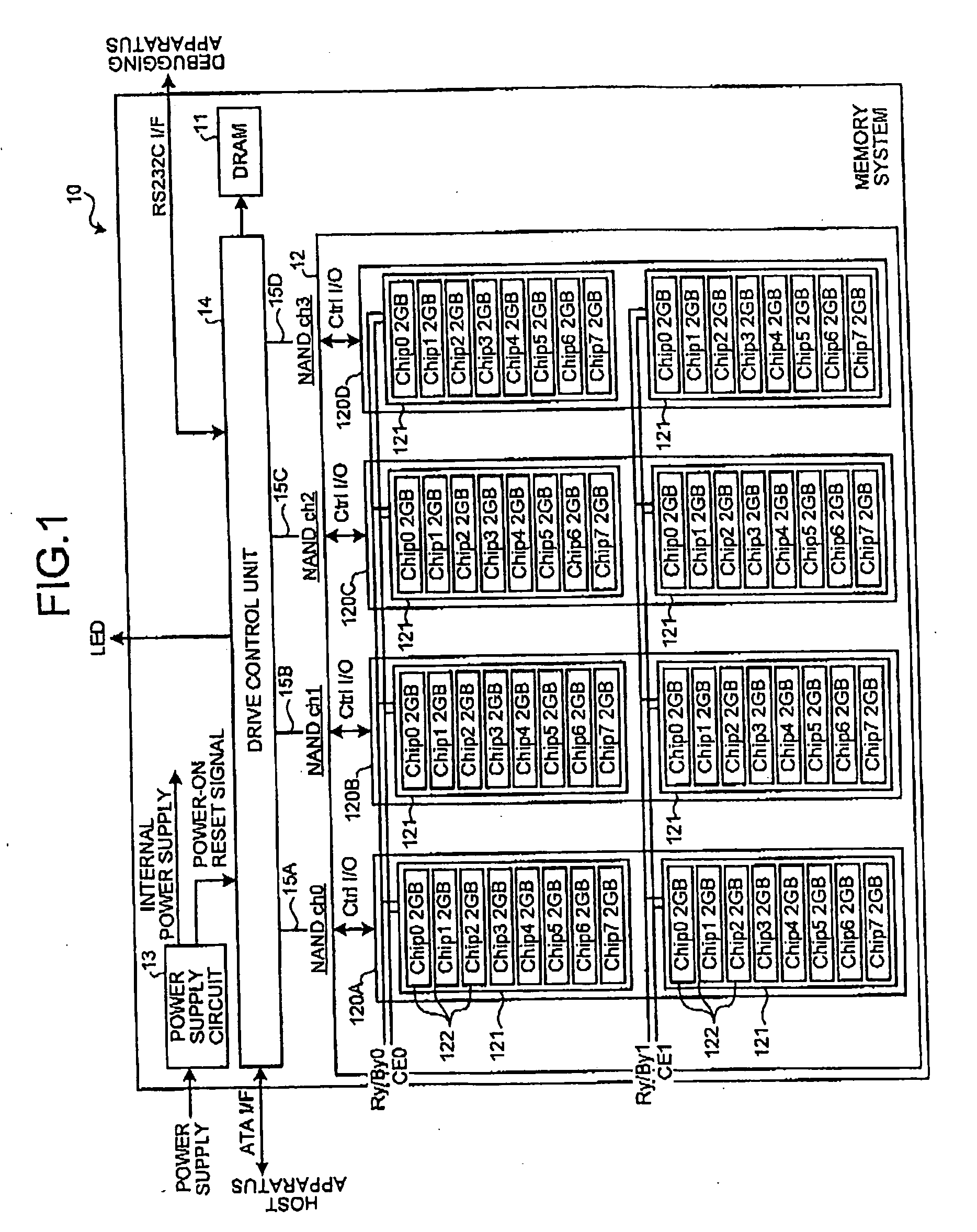
Data storing apparatus
InactiveUS20050036372A1Overcome problemsThe implementation process is simpleInput/output to record carriersMemory adressing/allocation/relocationInitData storing
A removable memory card (1) detachably mounted to a host device (2). The memory card (1) includes a non-volatile semiconductor memory in which data recorded in the memory is erased batch-wise in terms of a block of a predetermined data volume as a unit, a system information storage unit in which there is stored the inner information of the data storage device, and a controller for managing control for the semiconductor memory, based on a command supplied from the host device (2). The memory card (1) is able to accept a command for initialization. When supplied with the initializing command from the host device (2), the memory card (1) is responsive to the parameters stored in the system information storage unit to effect logical formatting of a recording area on a semiconductor memory.
Owner:SONY CORP
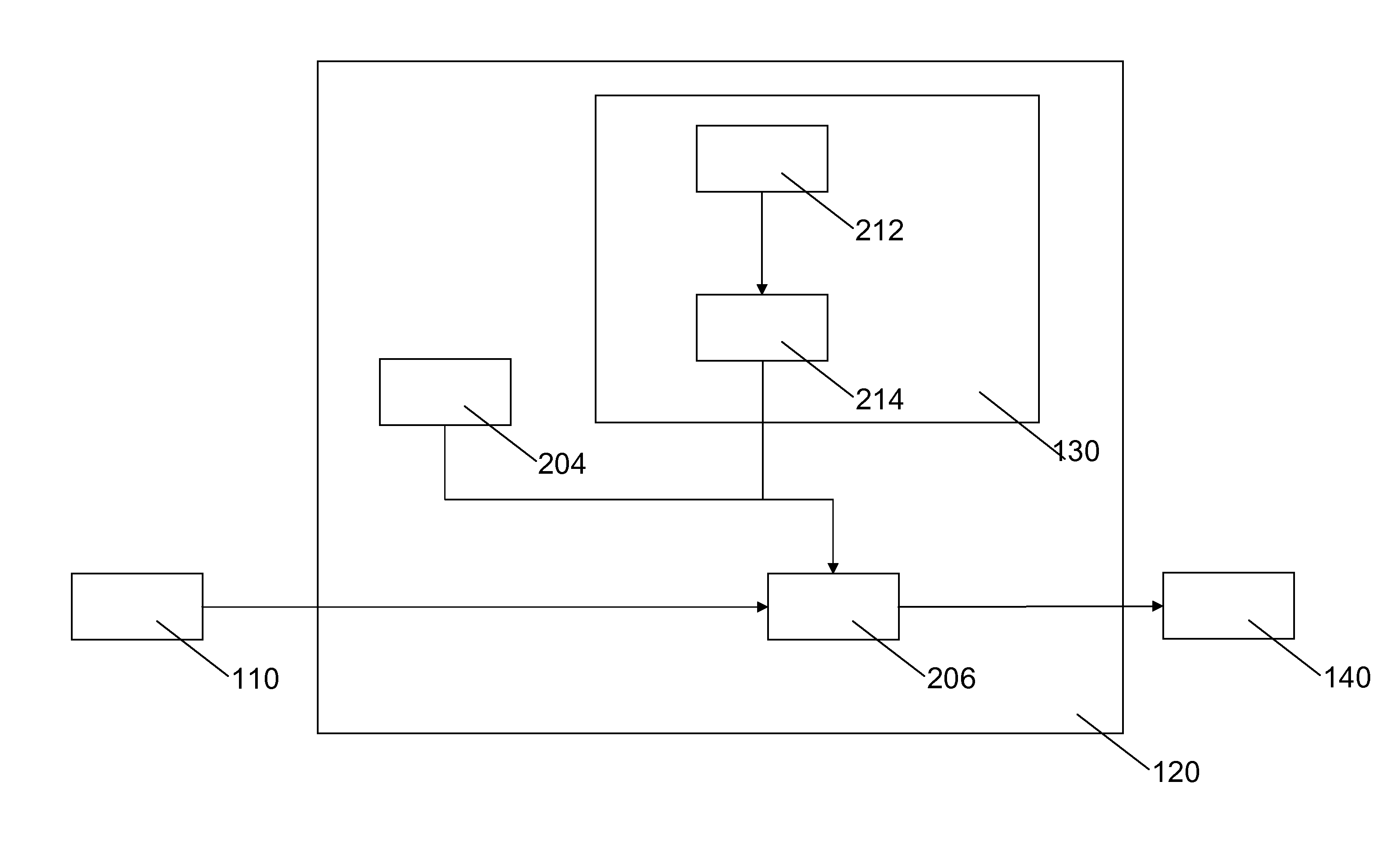
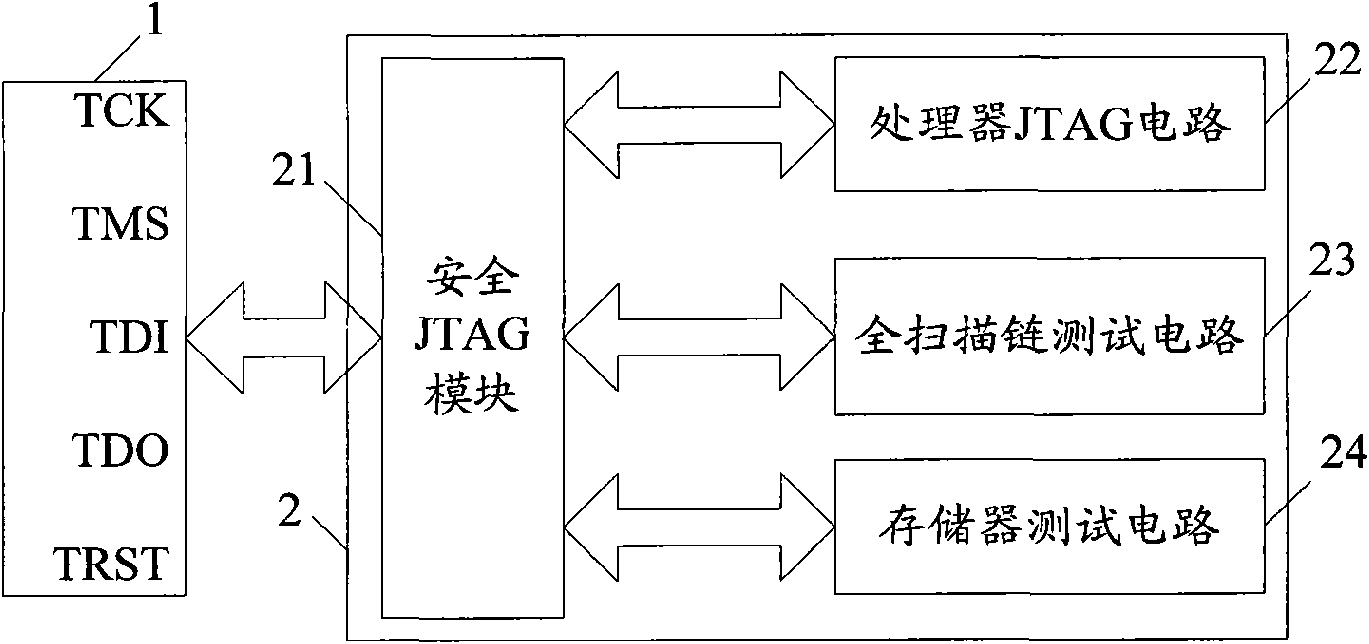
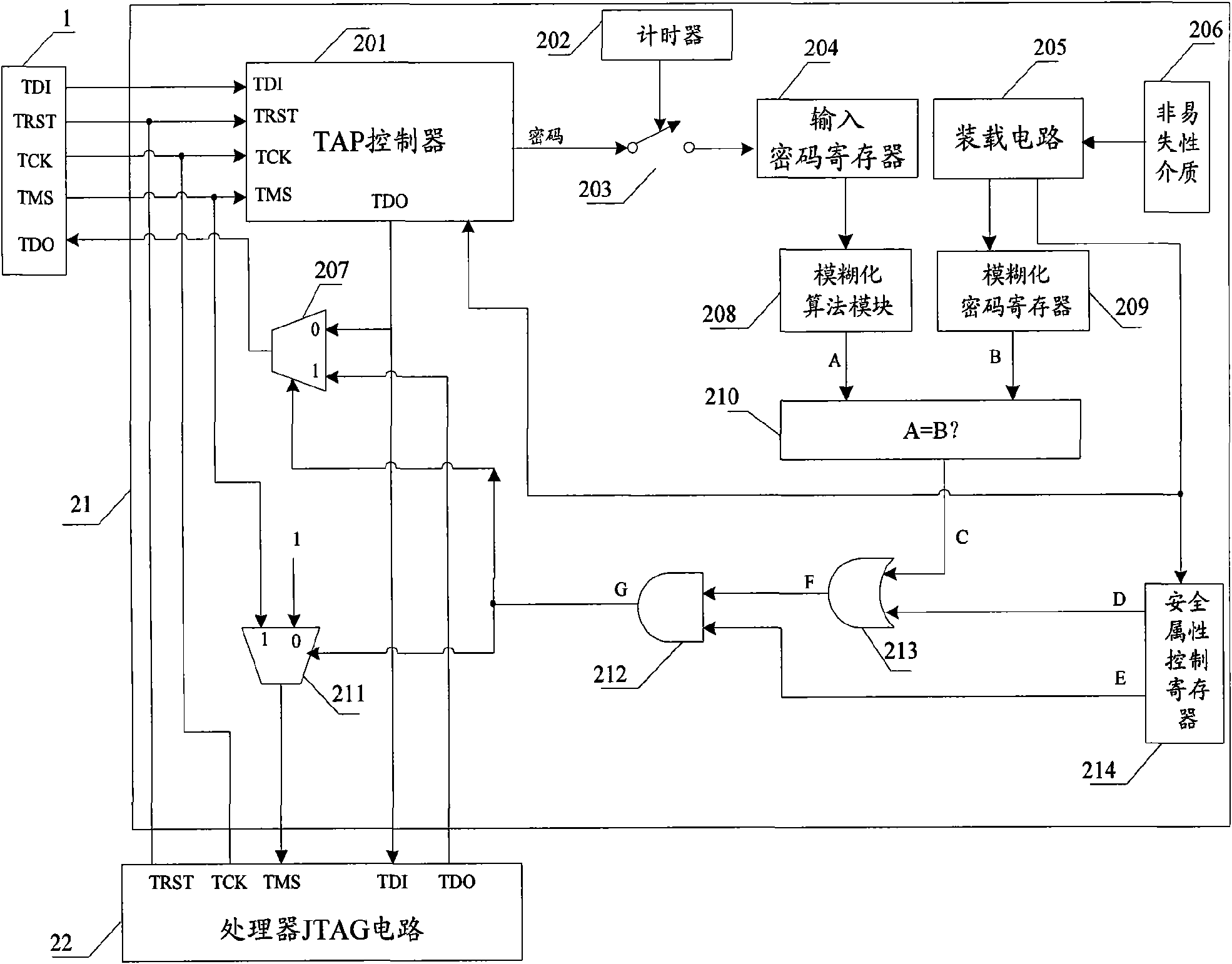
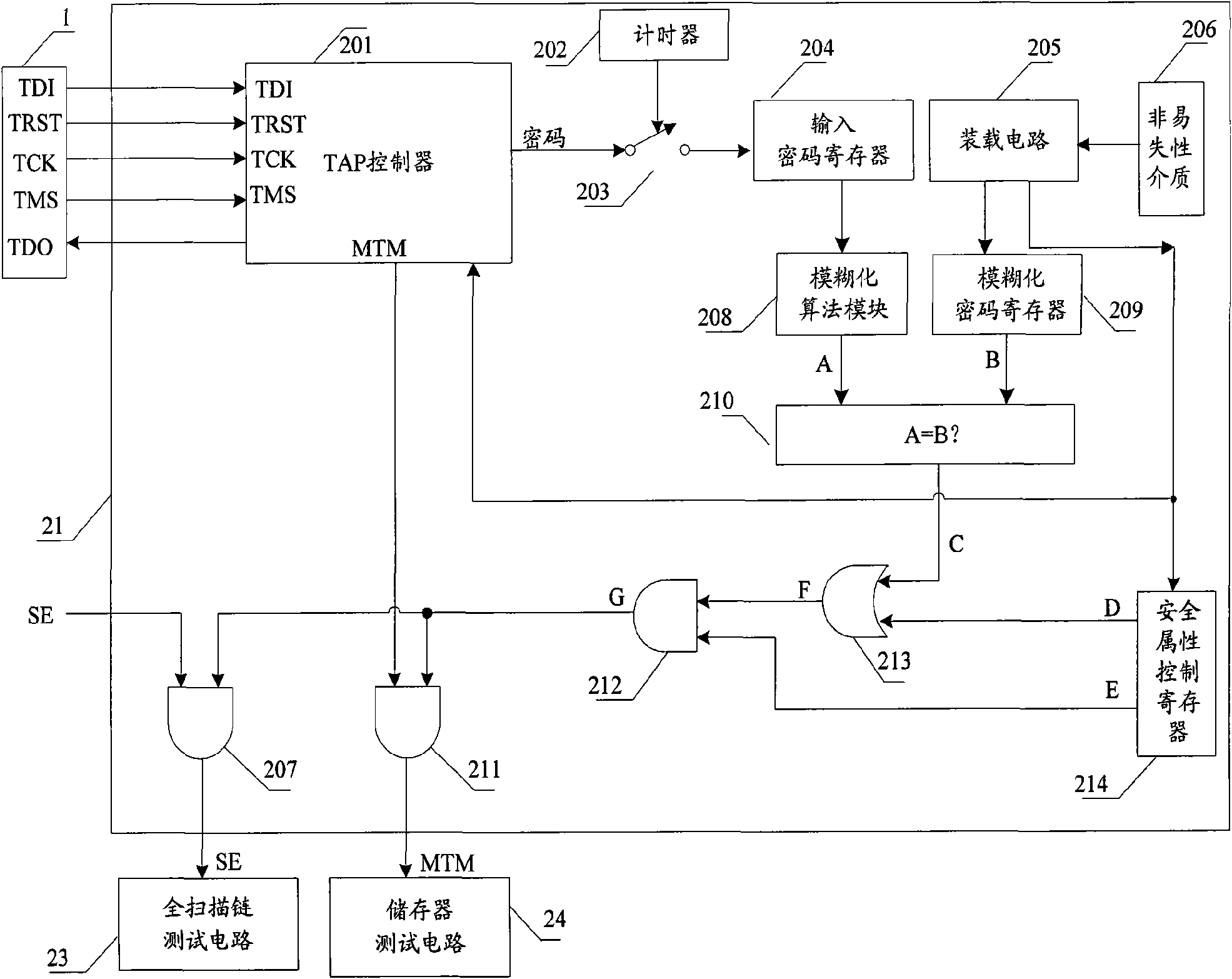
Safety JTAG module and method for protecting safety of information inside chip
InactiveCN101620656AReduce security risksImprove data security featuresInternal/peripheral component protectionProcessor registerPassword
The invention relates to a safety JTAG module and a method for protecting security of information inside a chip, wherein the safety JTAG module comprises a nonvolatile medium (206), a loading circuit (205), a security attribute control register (214), a TAP controller (201), two selectors (207 and 211), a switch (203), a password authentication module and a logic processing module; the TAP controller (201) and the two selectors (207 and 211) are connected between a JTAG port (1) and a protected object inside the chip; the switch (203) is switched by the control of a timer (202); the password authentication module is used for authenticating whether a clear-text password input by a user is accordant with a fuzzification password or not; and the logic processing module is used for logically processing an authentication result output by the password authentication module and an indication signal output by the security attribute control register (214) and outputting an enable signal to the two selectors (207 and 211) so as to control whether the JTAG port (1) is allowed to be connected with the protected object inside the chip through the TAP controller (201) or not. The invention ensures the security and the convenience of an SOC chip in testing and debugging processes, thereby protecting the security of data inside the chip.
Owner:SHENZHEN STATE MICRO TECH CO LTD
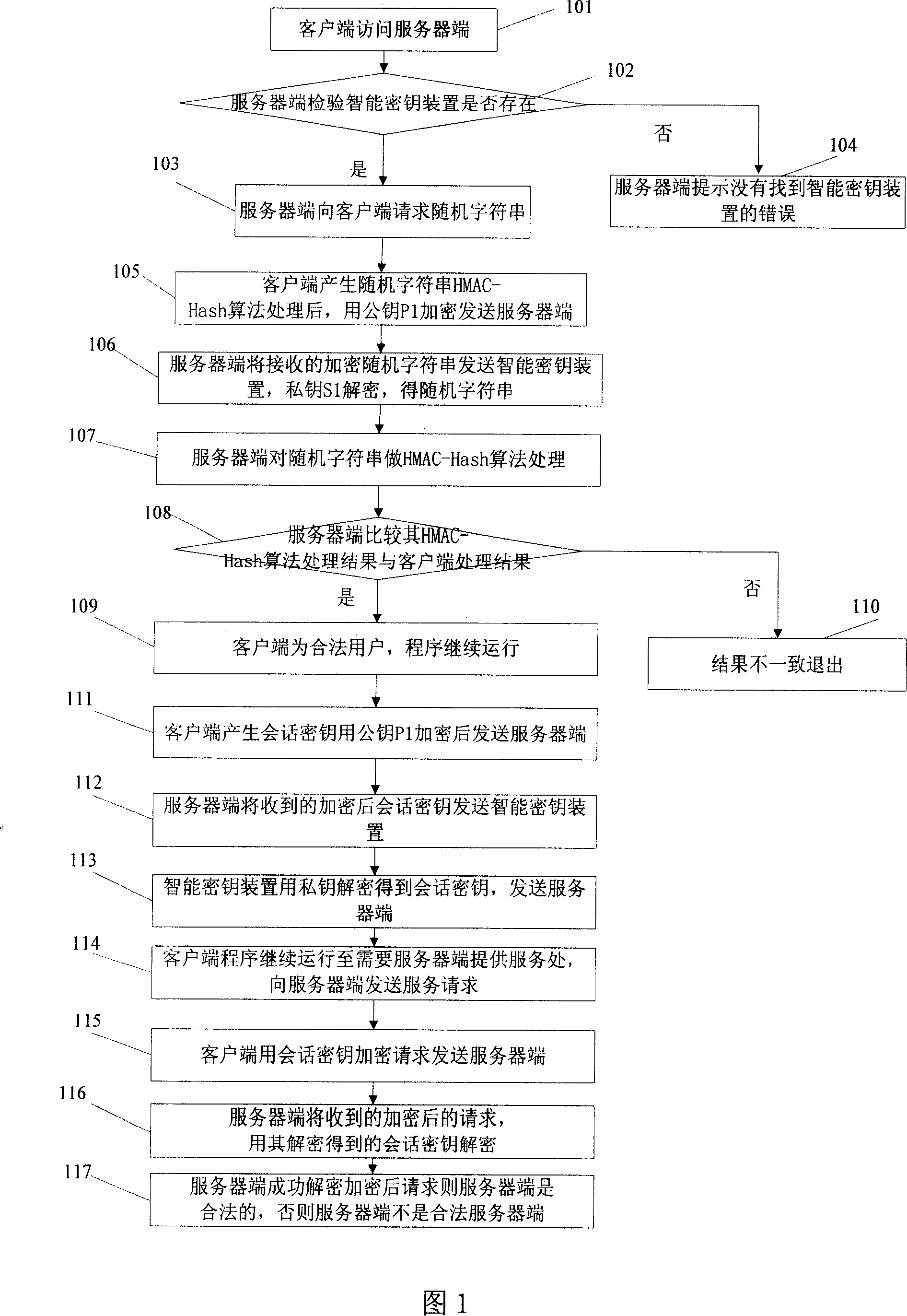
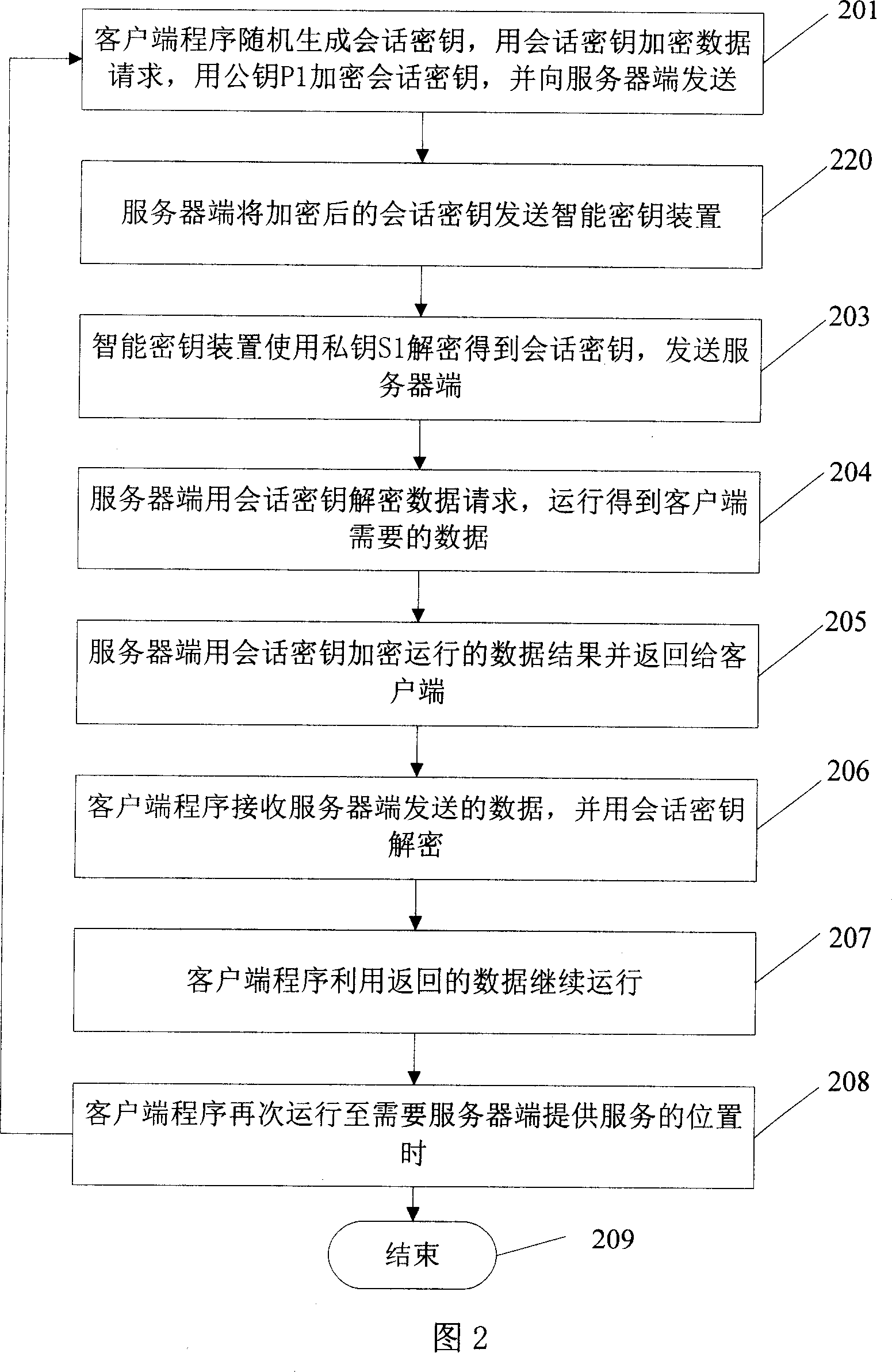
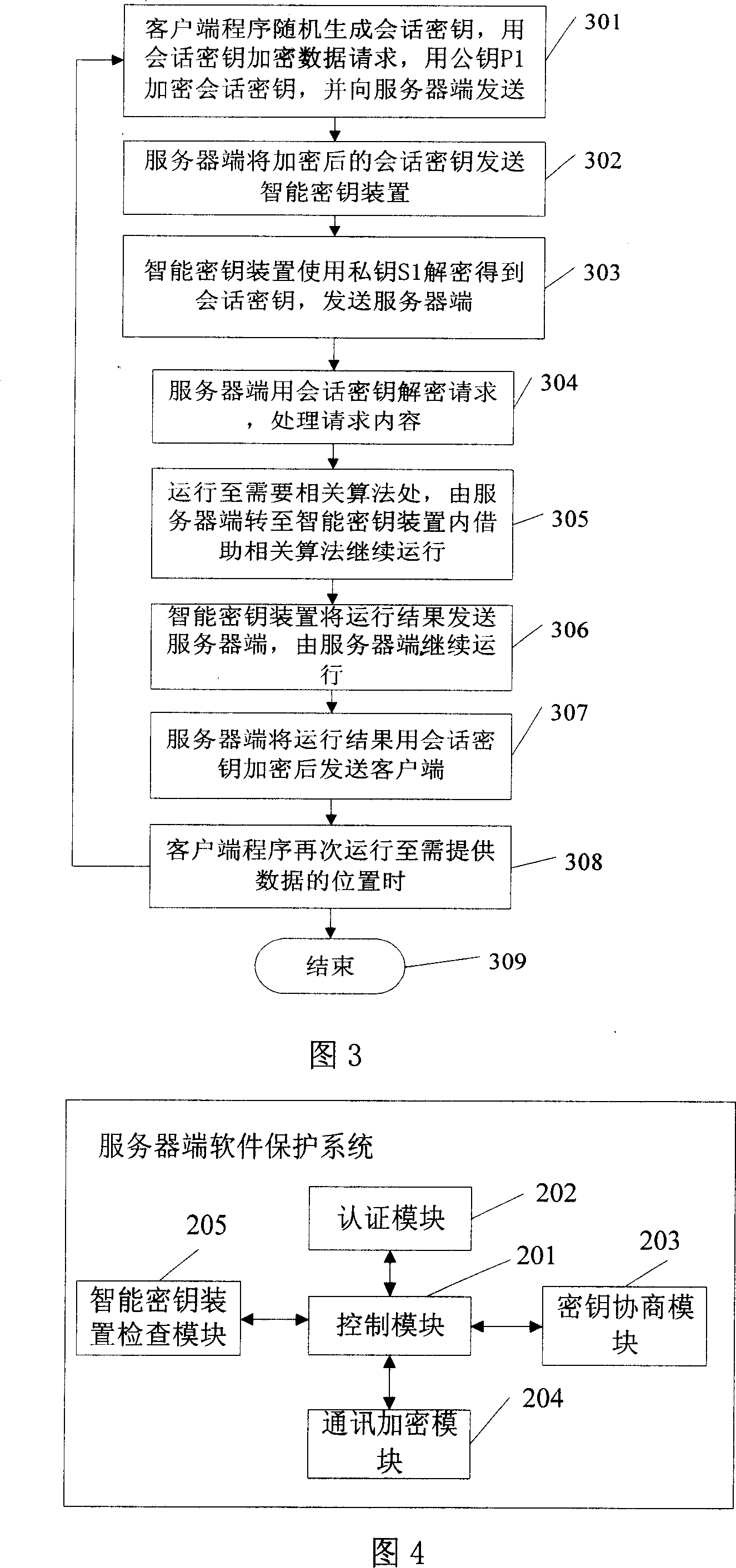
Server and software protection method and system
ActiveCN101005361AImprove securityEnsure safetyUser identity/authority verificationProgram/content distribution protectionNetwork communicationClient-side
The method combines server end with intelligent cipher key device. Network communication is carried out between server end and client end under C / S or B / S structure. ID of client end is authenticated by server end. Program at client end runs and generates session key. Client end sends service request encrypted by session key to server end, and sends session key encrypted by public key. After receiving encrypted service request, server end runs service corresponding to client end, and returns session key encrypted run result to the client end. The server end is bound to the intelligent cipher key device, which is safety carrier capable of preventing interpolating and embezzling internal information. Intelligent cipher key device allows private key used inside equipment. The private key cannot be reproduced and attacked to enhance security of software at server end.
Owner:FEITIAN TECHNOLOGIES
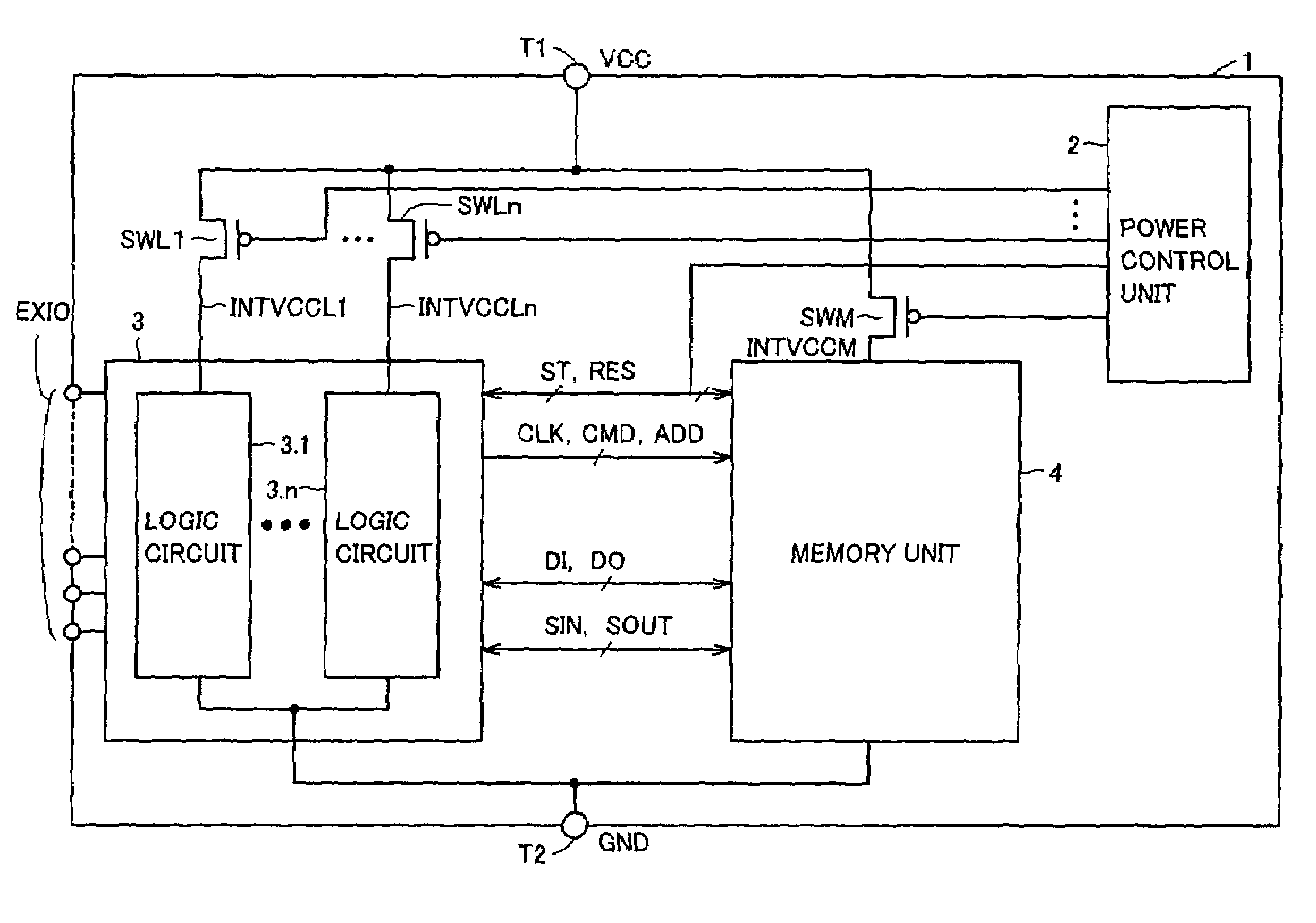
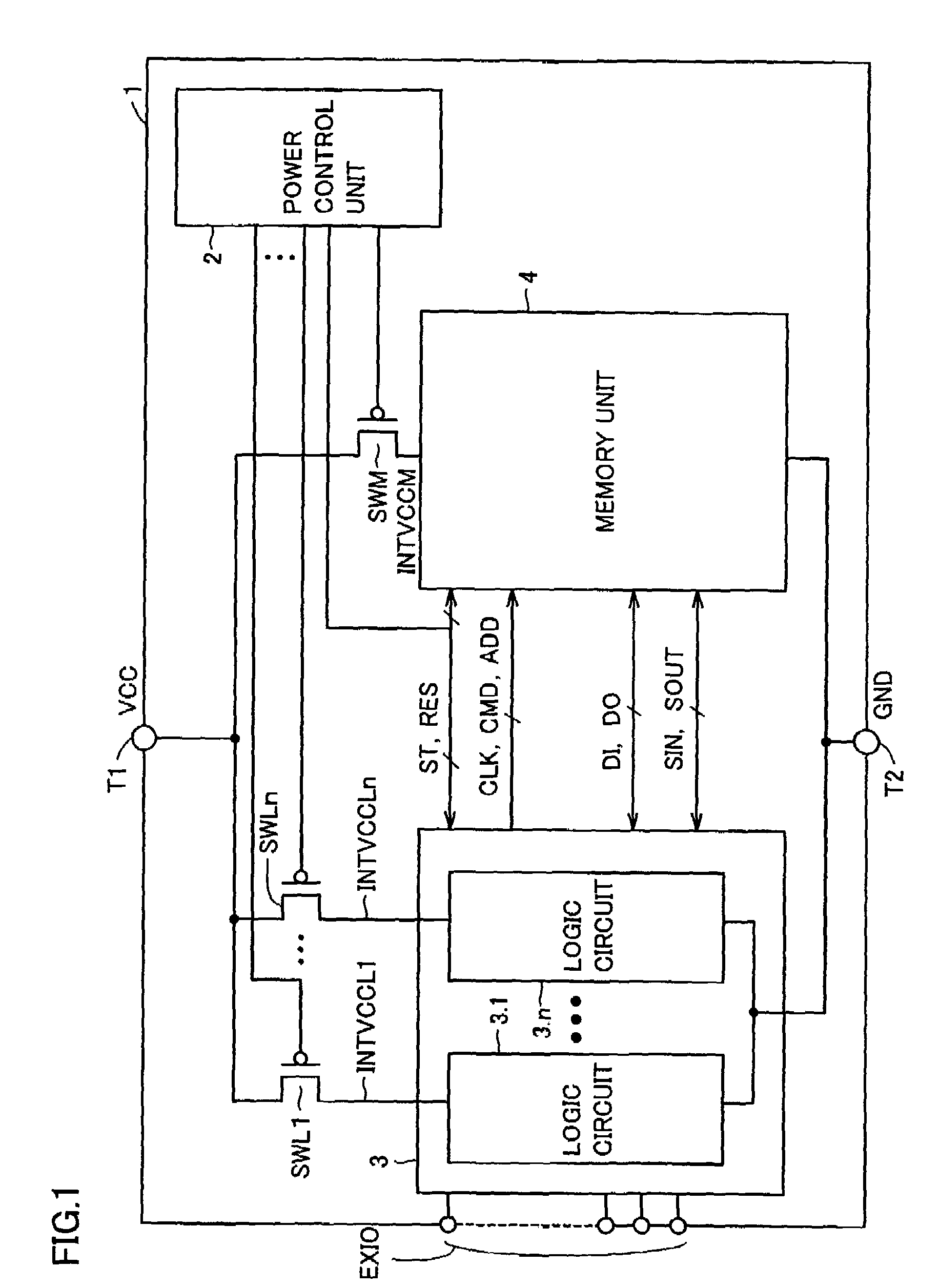
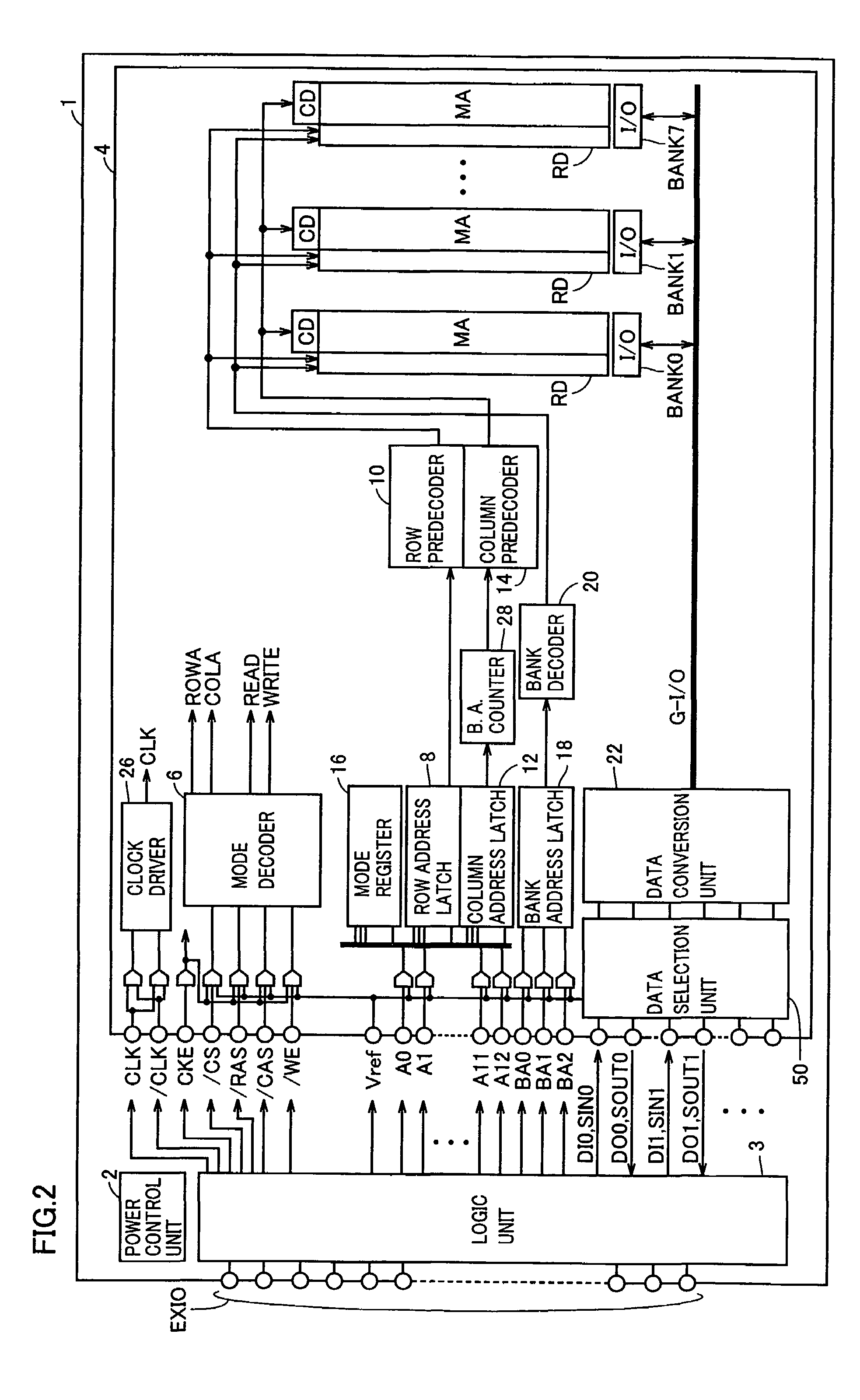
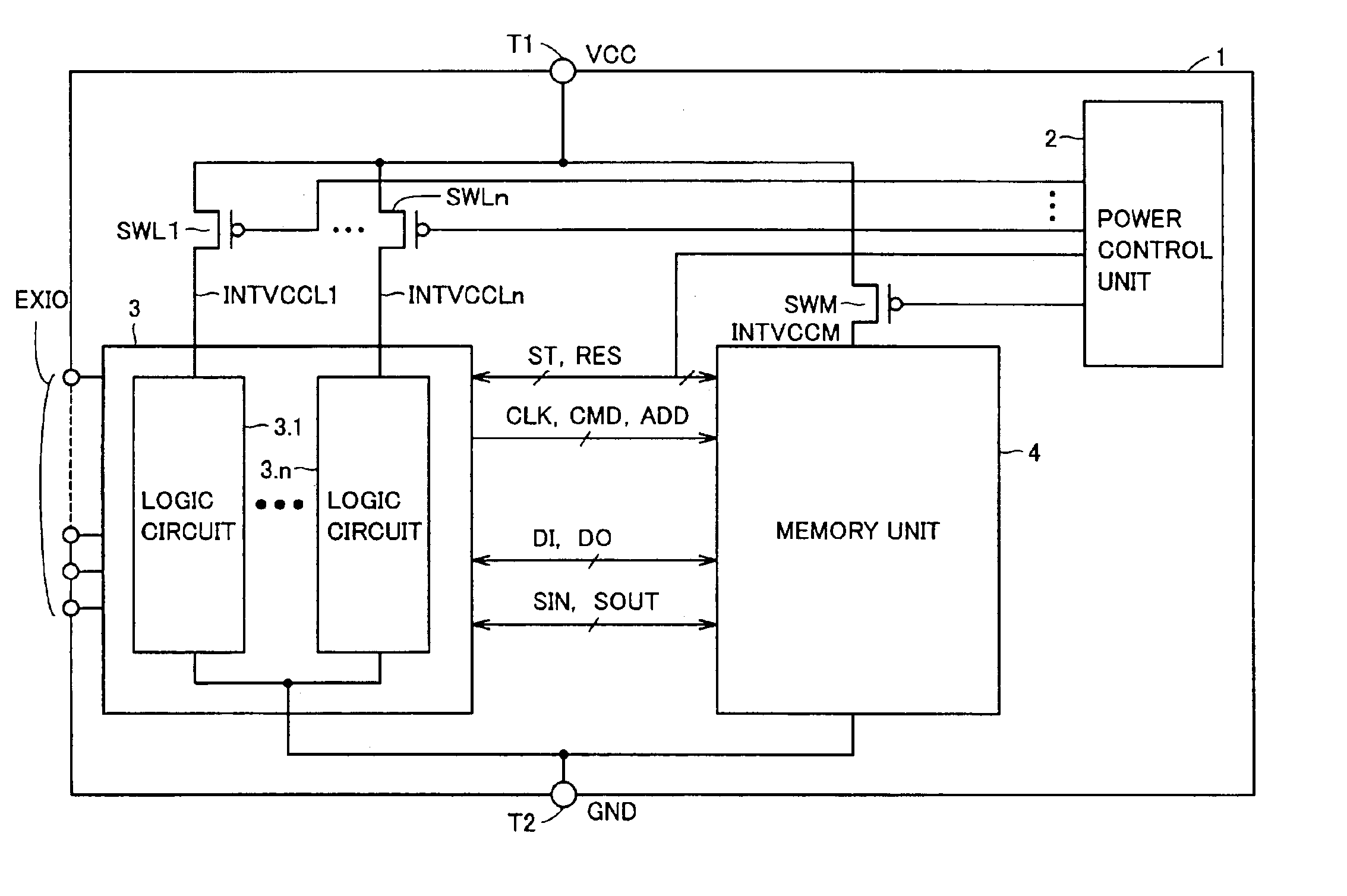
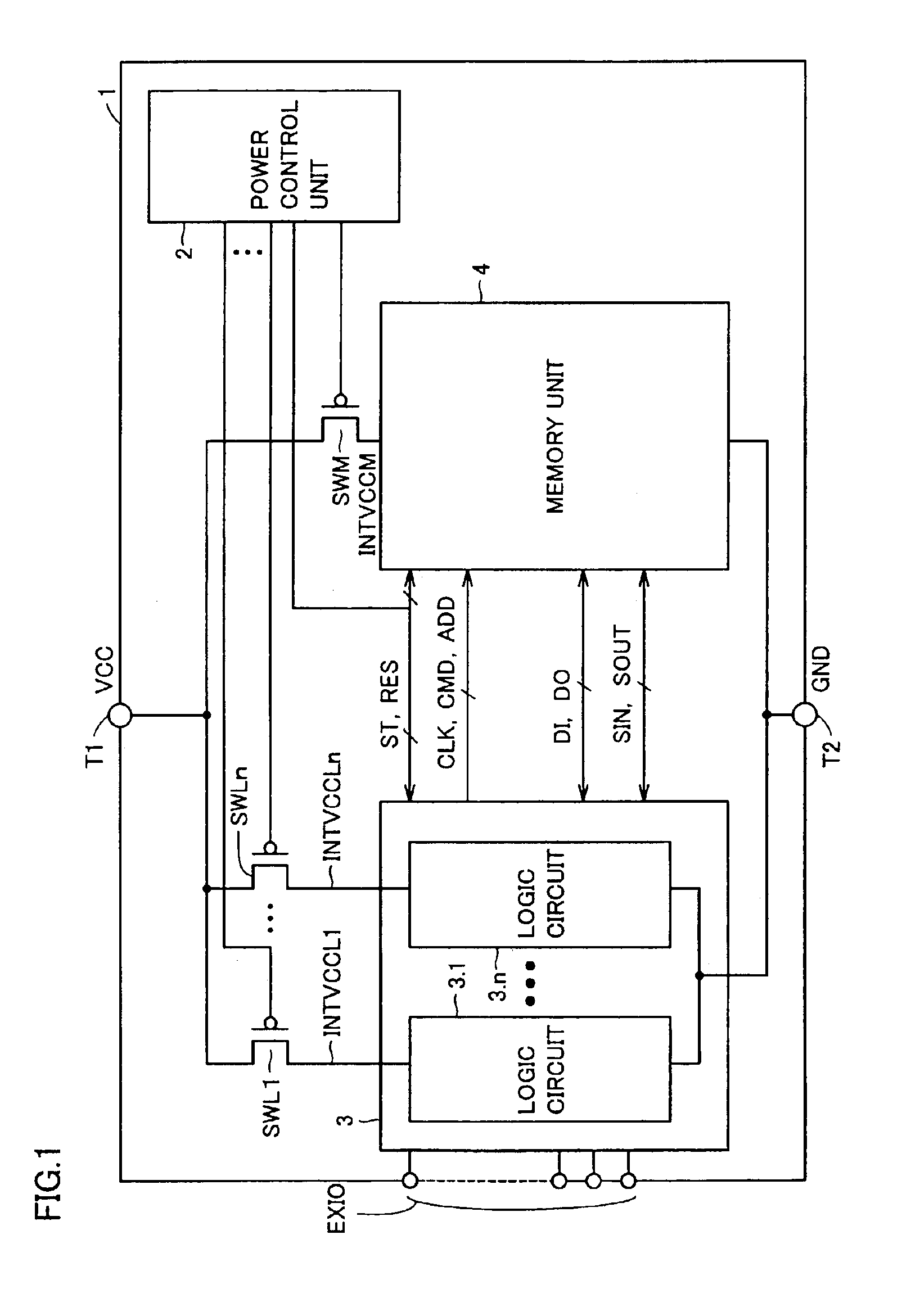
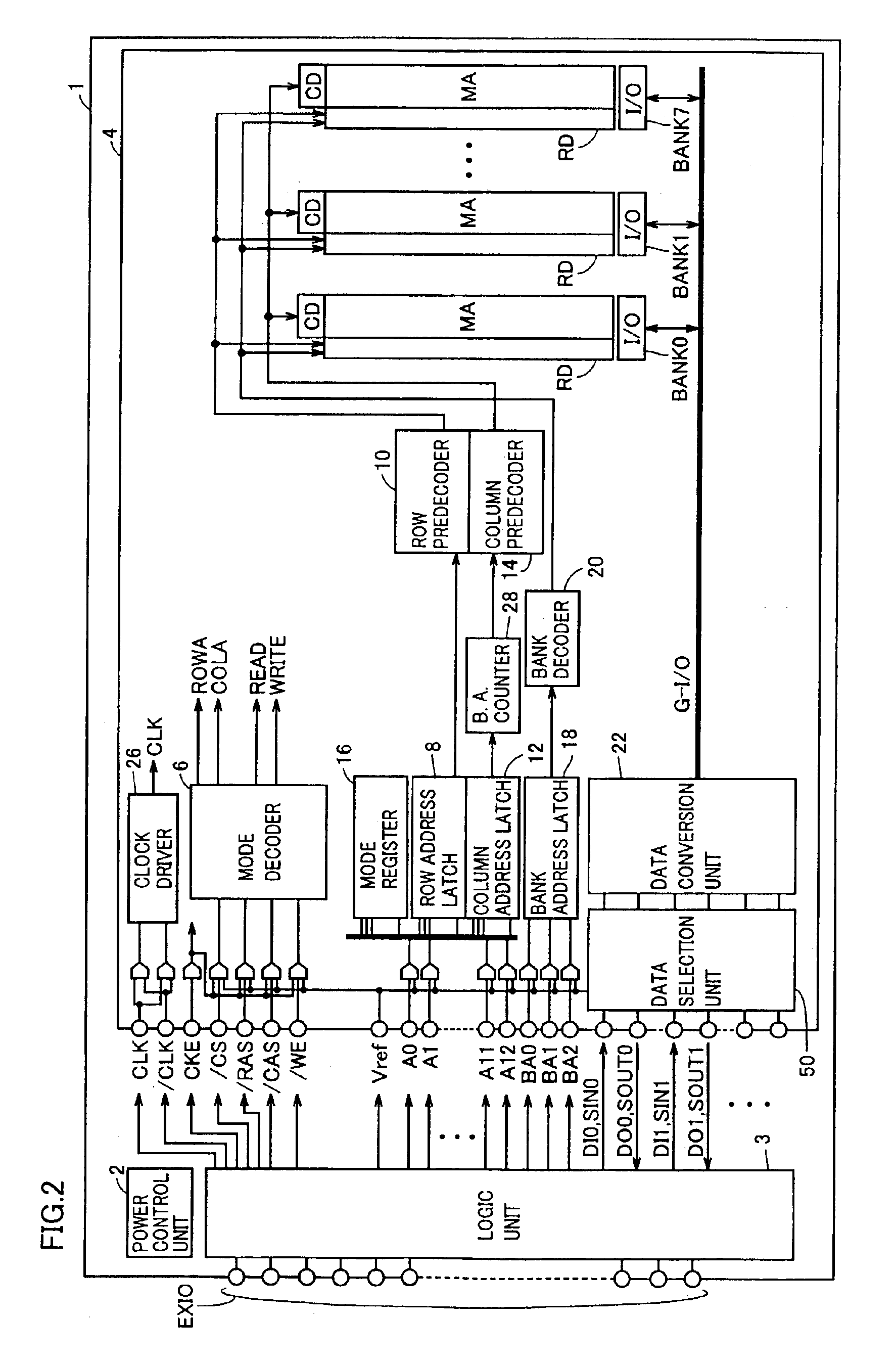
Semiconductor device saving data in non-volatile manner during standby
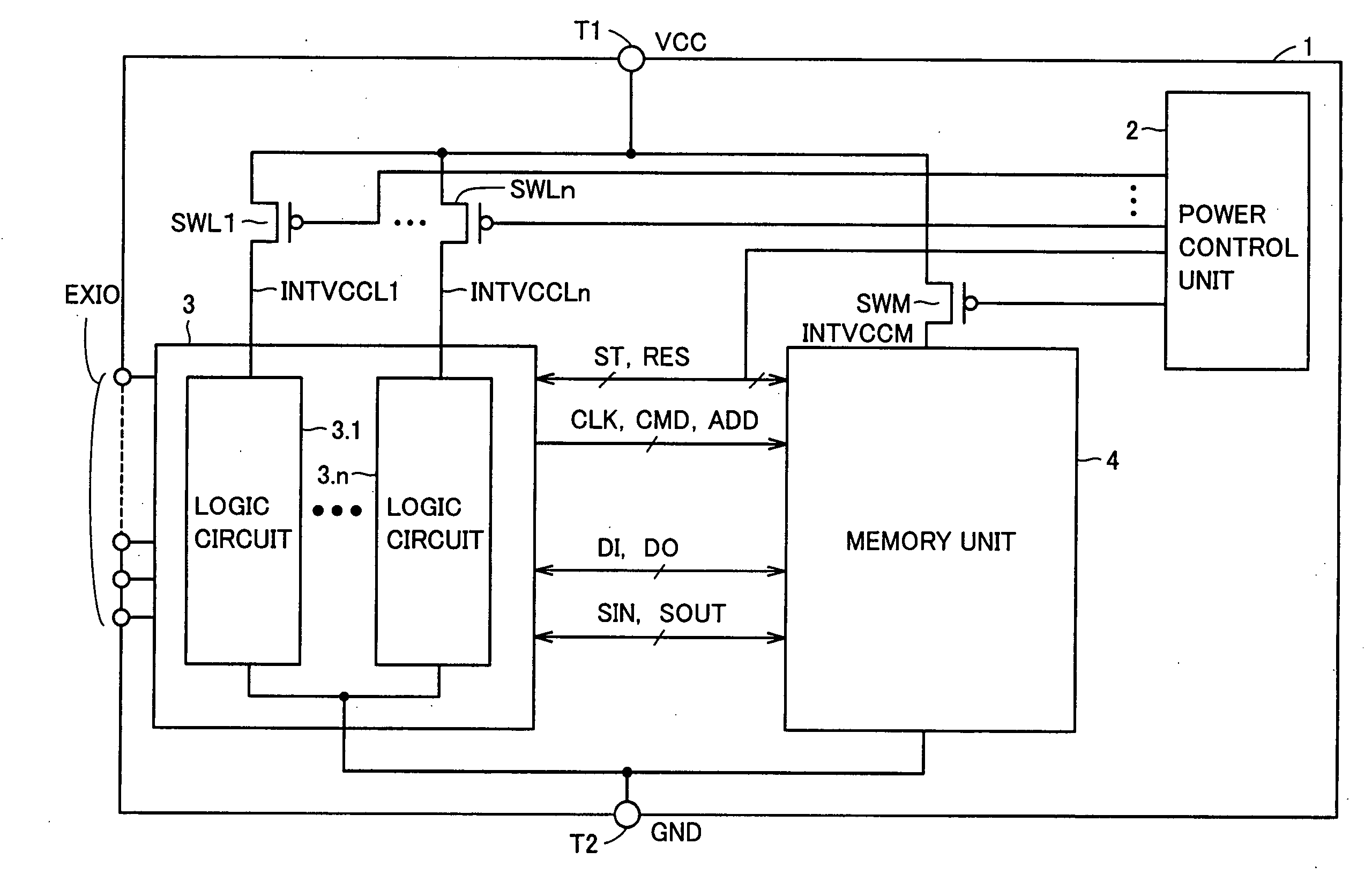
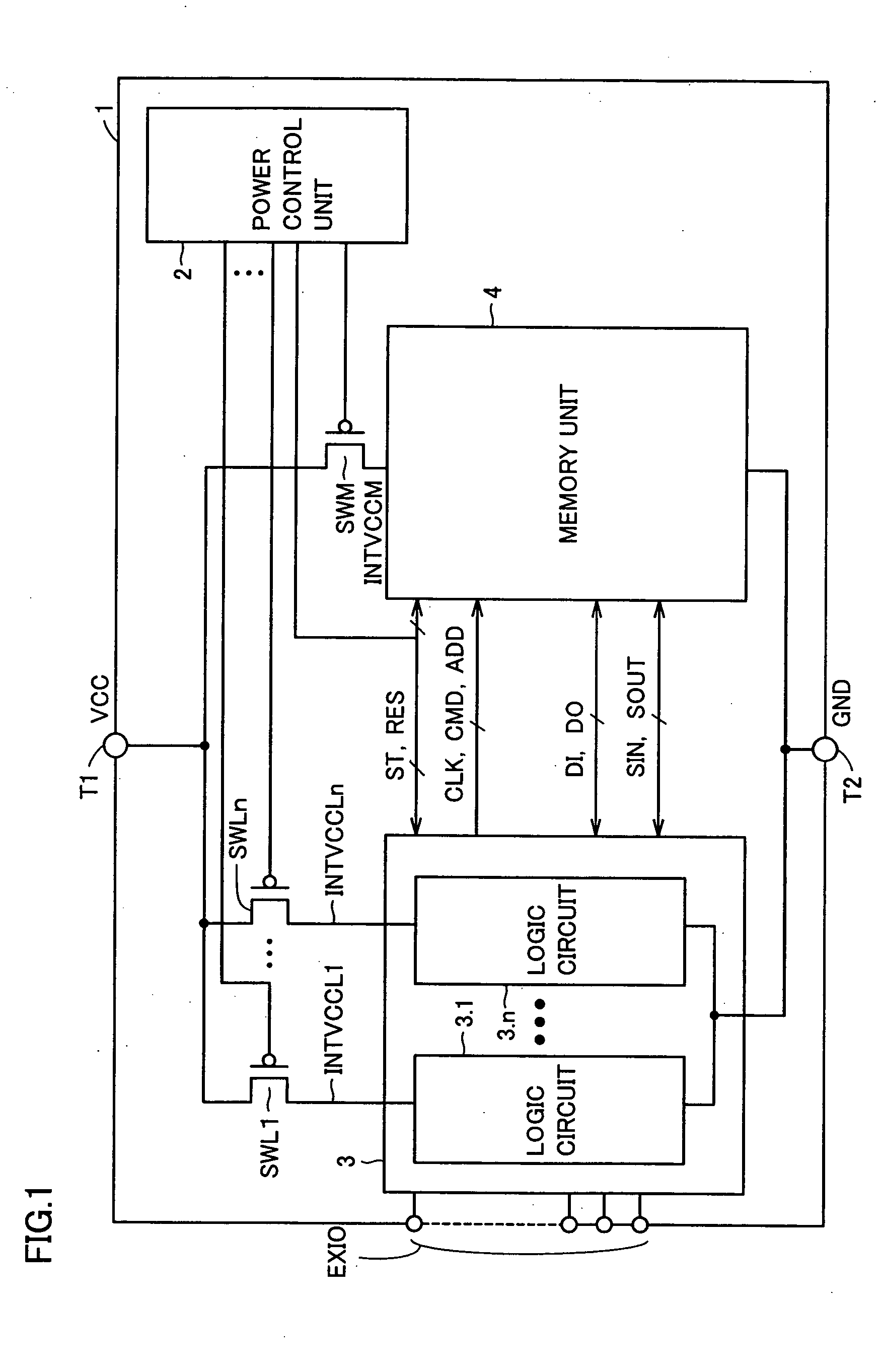
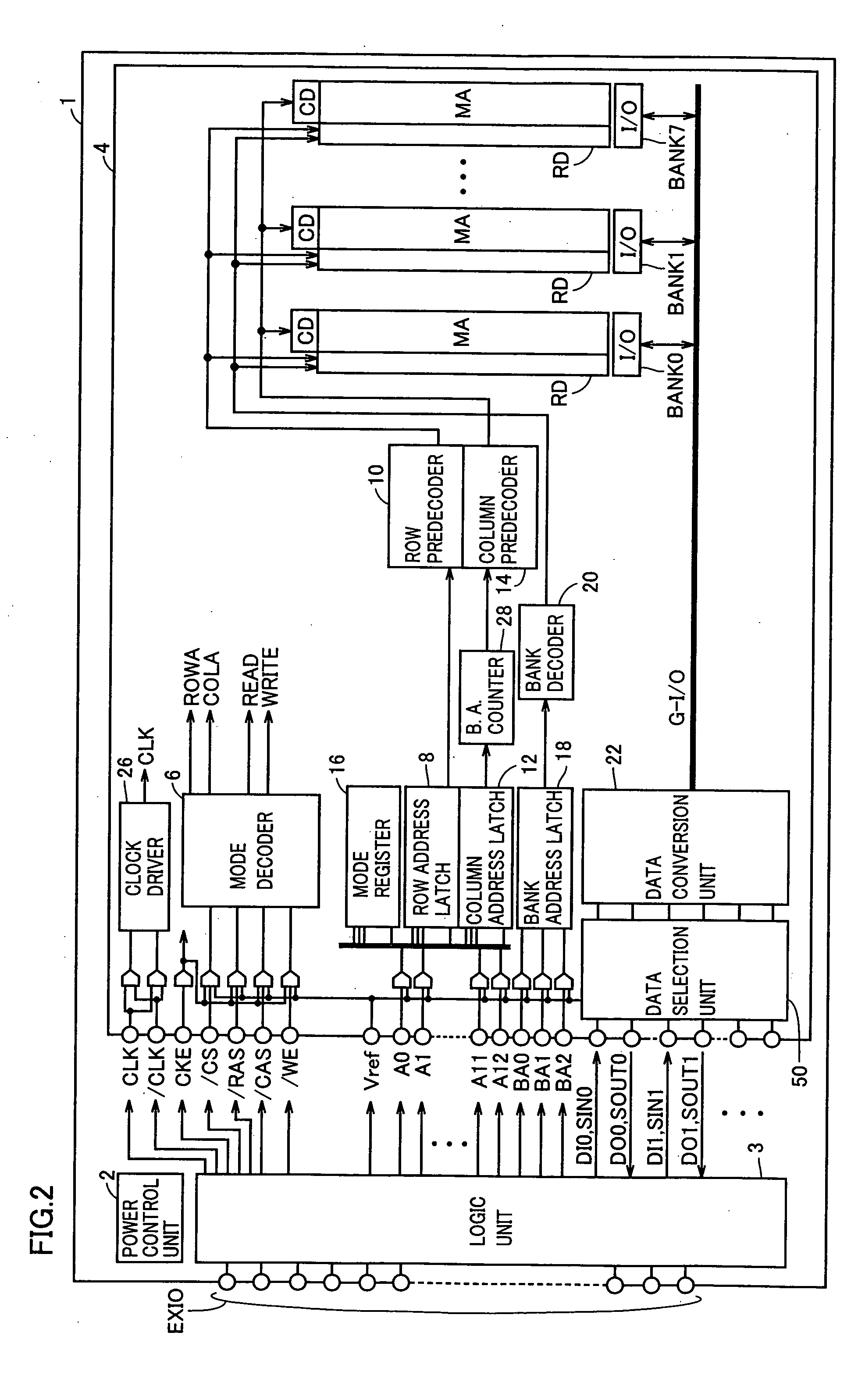
A power control unit activates a control signal ST for a circuit block to be set to a standby state before turning off power of the circuit block or a whole chip, and saves an operation result of data processing of the circuit block into a memory unit. When the power is again supplied to the circuit block in the standby state, the power control unit activates a control signal RES after the power supply is started and restores the data saved in the memory unit to the circuit block. Flip-flops in the circuit block are connected in series when the saving or restoring of data is performed, and perform a data transfer operation with a path different from that in a normal operation. Therefore, a semiconductor device can be provided which can rapidly transit to a standby mode having reduced current consumption while holding internal information.
Owner:RENESAS TECH CORP
Handover between software and hardware accelarator
ActiveUS20060101427A1Synchronization is simpleGeneral purpose stored program computerSpecific program execution arrangementsInput selectionHandover
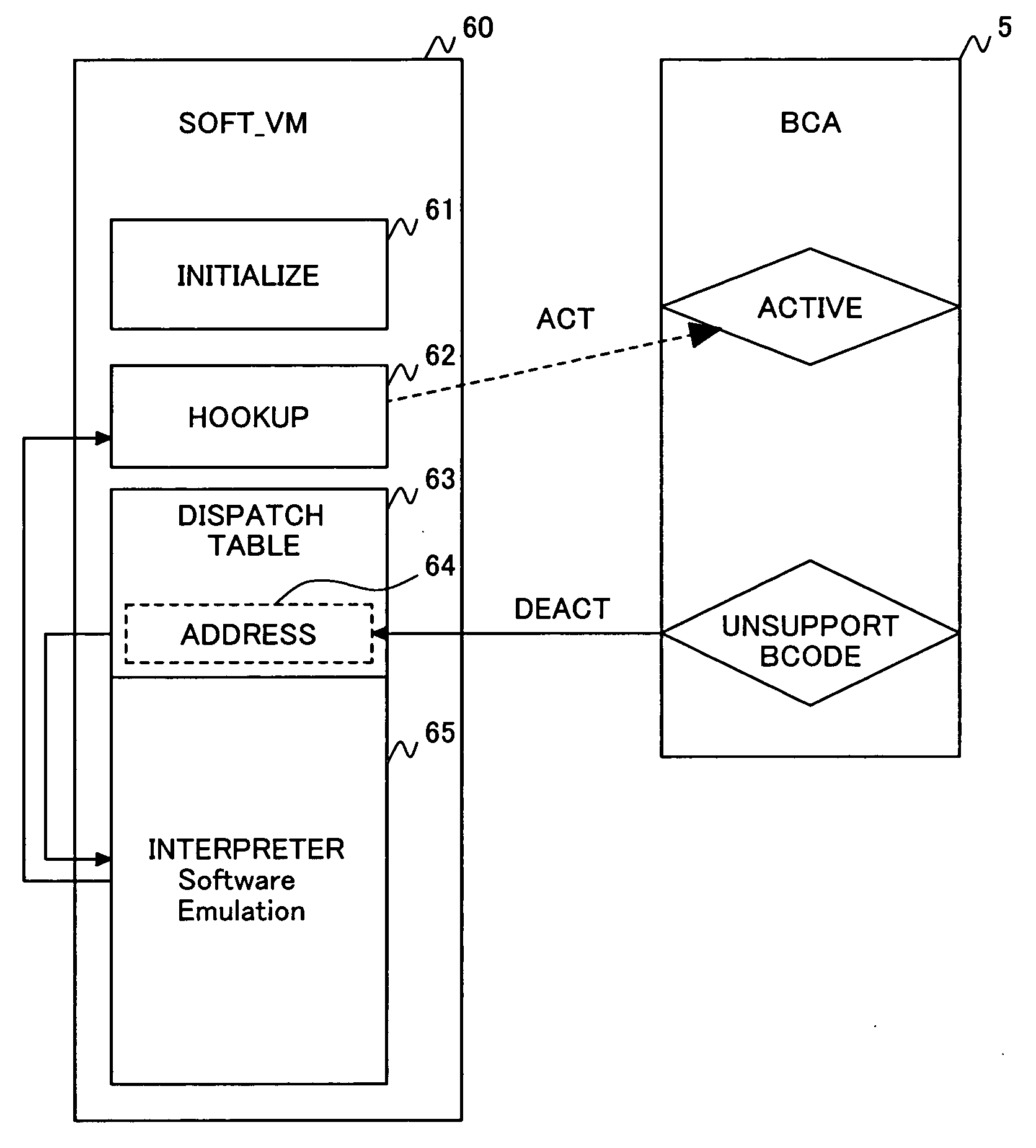
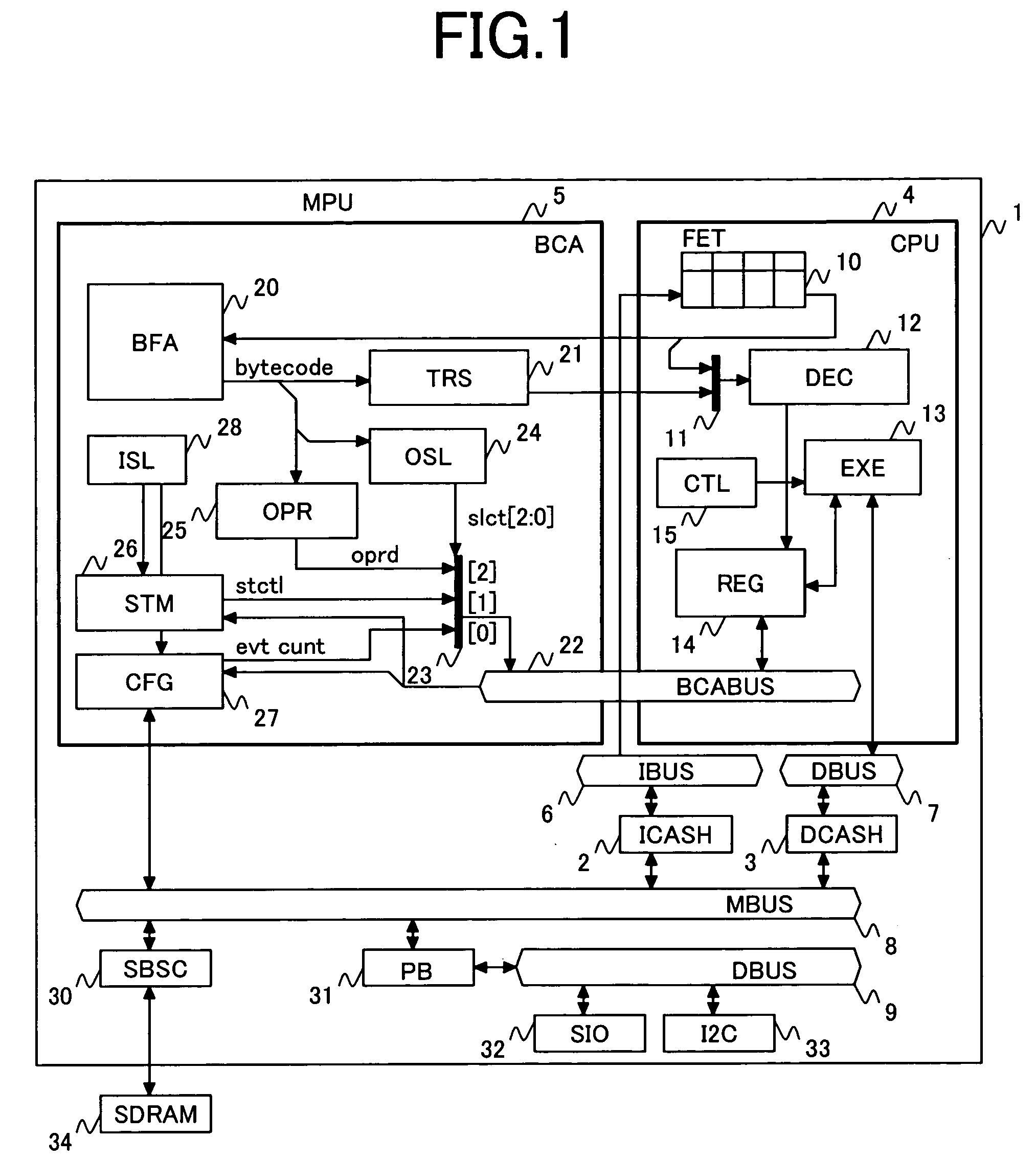
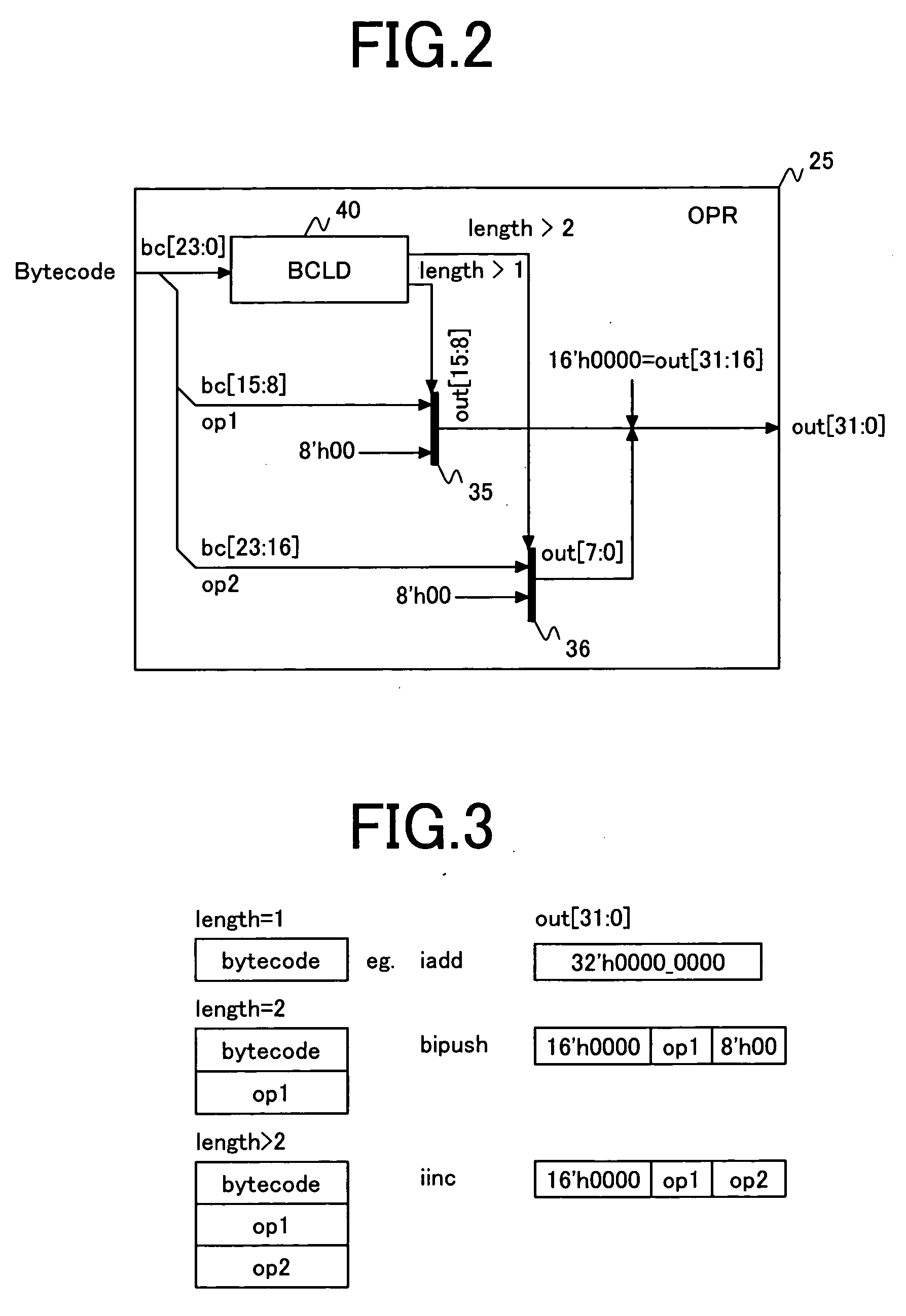
A bytecode accelerator which translates stack-based intermediate language (bytecodes) into register-based CPU instructions transfers plural pieces of internal information from a register file of a CPU to the bytecode accelerator by means of an internal transfer bus between the bytecode accelerator-and the CPU and an input selection logic of the bytecode accelerator when the bytecode accelerator is started and transfers plural pieces of internal information in the bytecode accelerator to the register file of the CPU by means of the internal transfer bus, an output selector and an output selector selection logic of the bytecode accelerator when the bytecode accelerator ends its operation in transition between hardware processing and software processing by software virtual machine.
Owner:RENESAS ELECTRONICS CORP
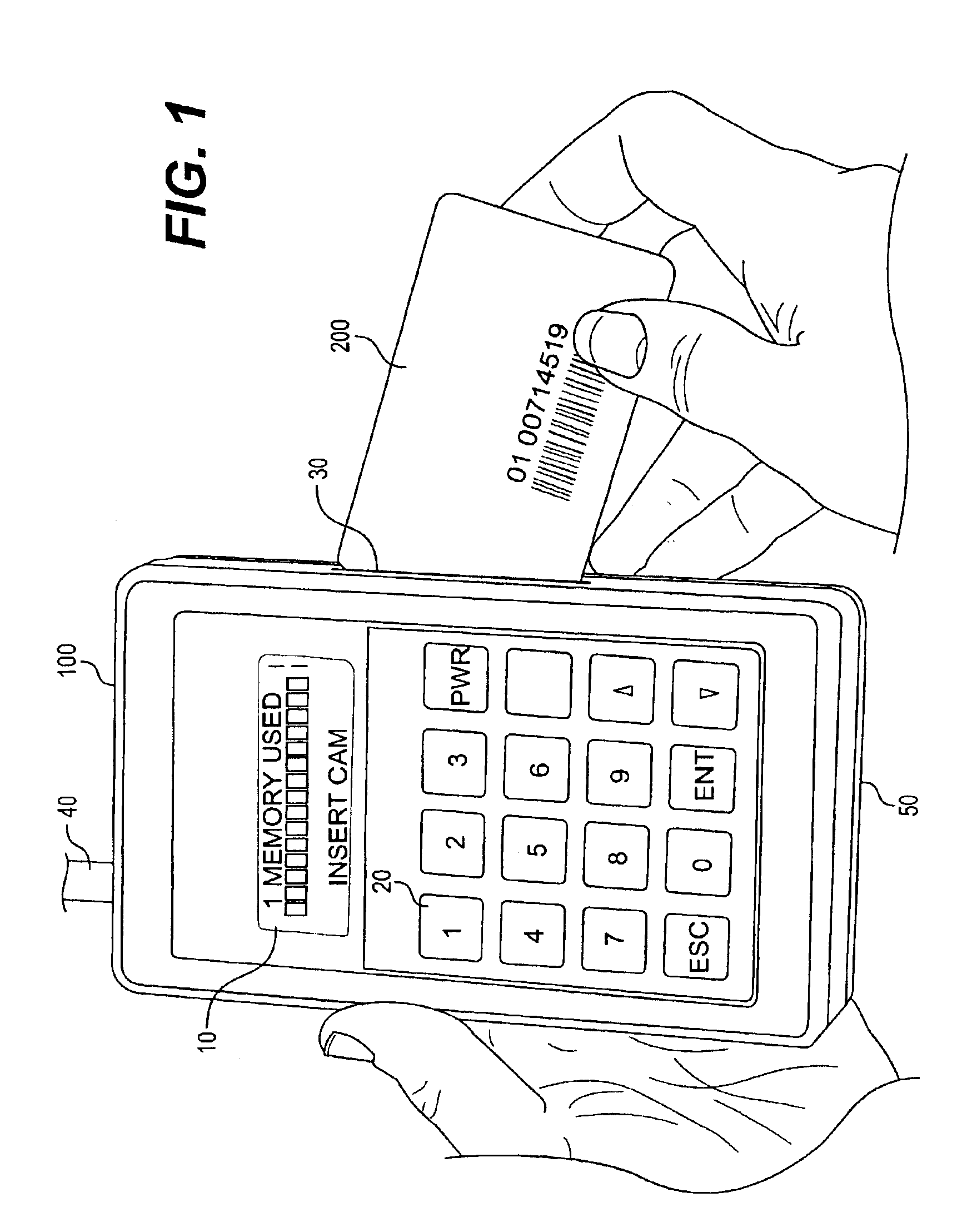
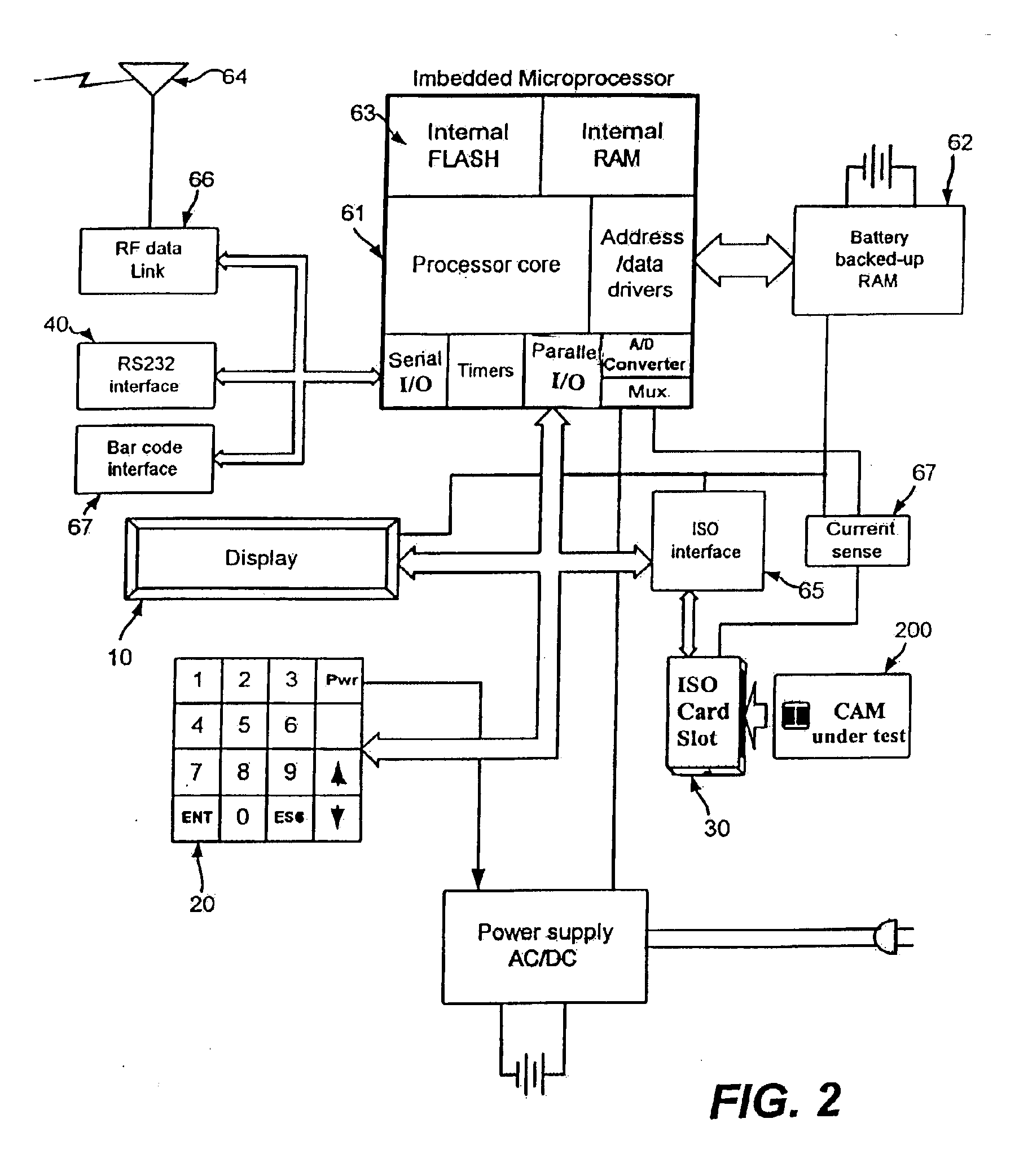
System for testing, verifying legitimacy of smart card in-situ and for storing data therein
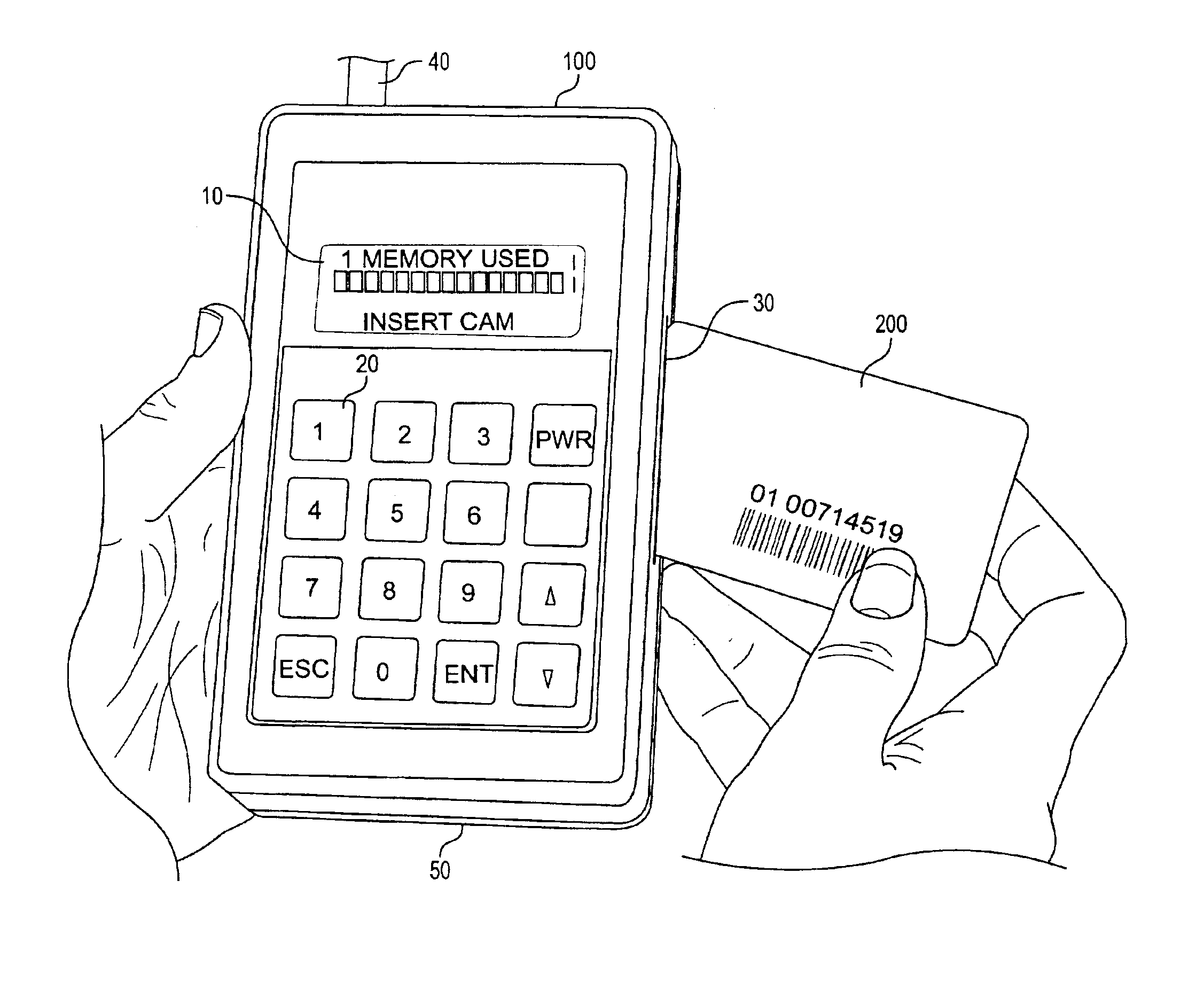
A hand-held battery-operated device for interrogating and / or programming ISO7816 smart cards by means of an ISO7816 compliant card slot, in conjunction with a display, a keypad and barcode reader for data entry, a battery backup RAM for temporary storage of collected data, flash memory for storage of proprietary information provided by a smart card issuer, a RS232 port and RF link for communication with a host computer, in-system programming port for updating the flash program, all connected operatively to an internal microprocessor which perform clock or power glitching to access internal information of a smart card to determine whether the card has been tampered, compromised, and functionality.
Owner:NDS
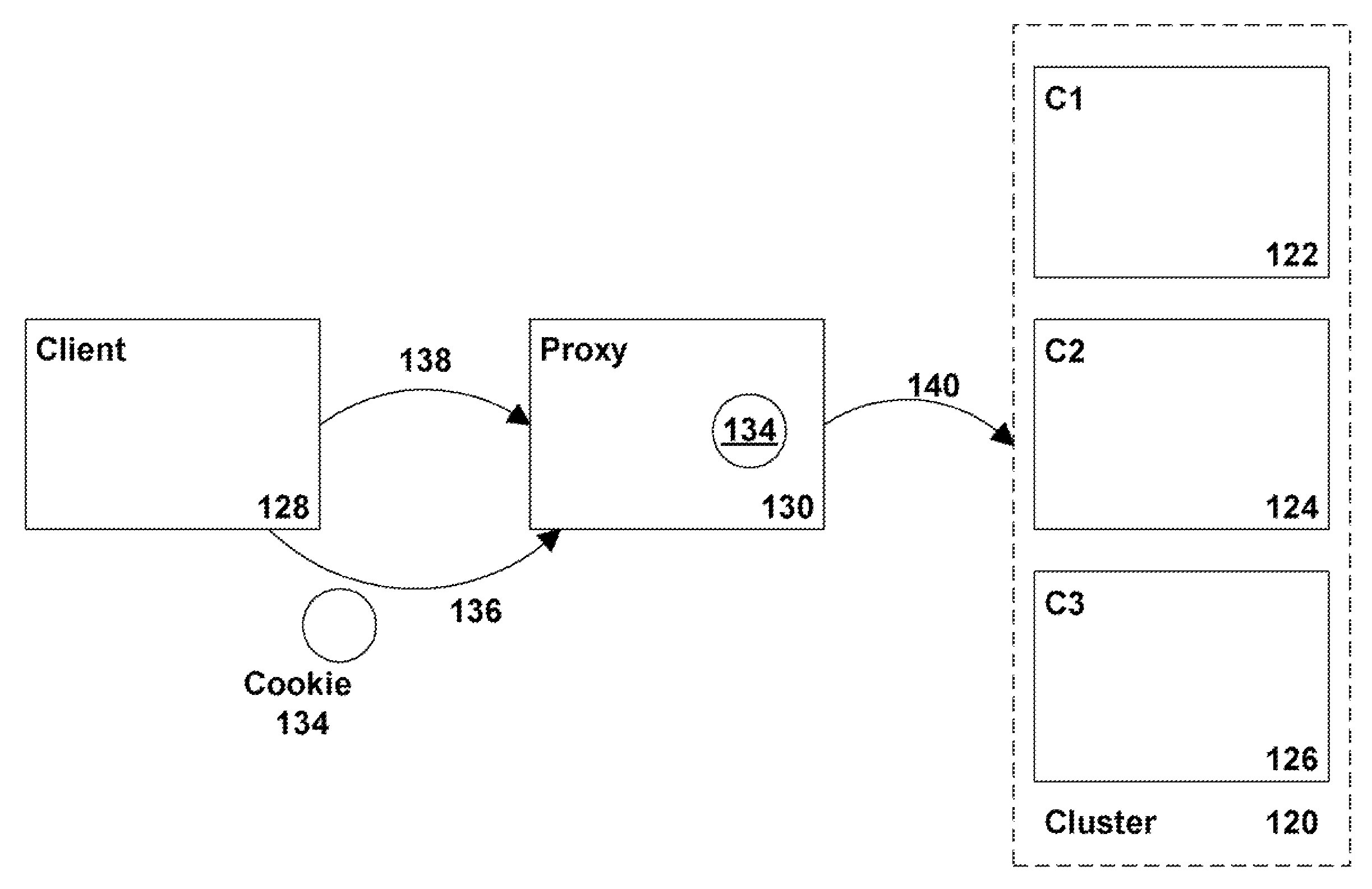
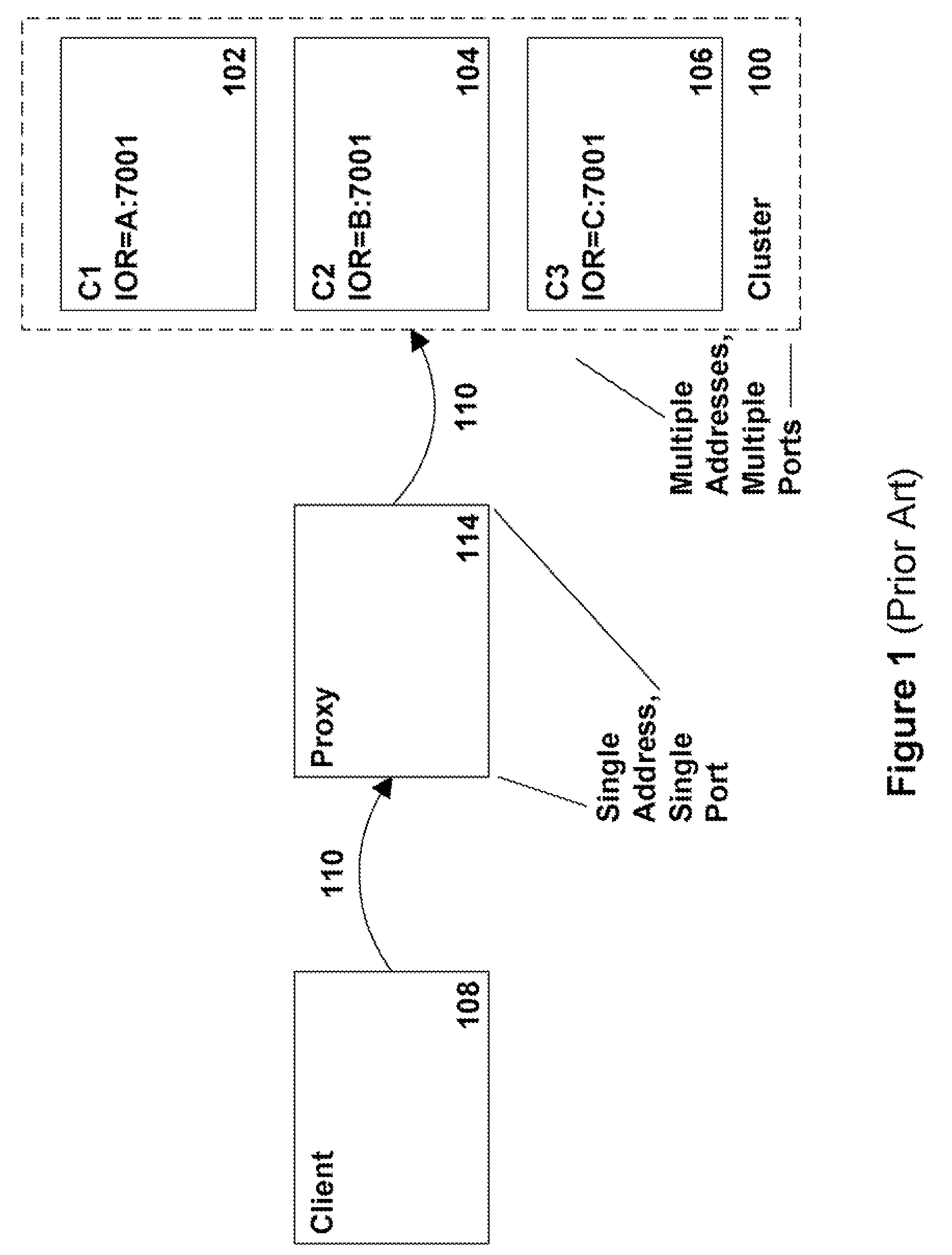
System and method for clustered tunneling of requests in application servers and transaction-based systems
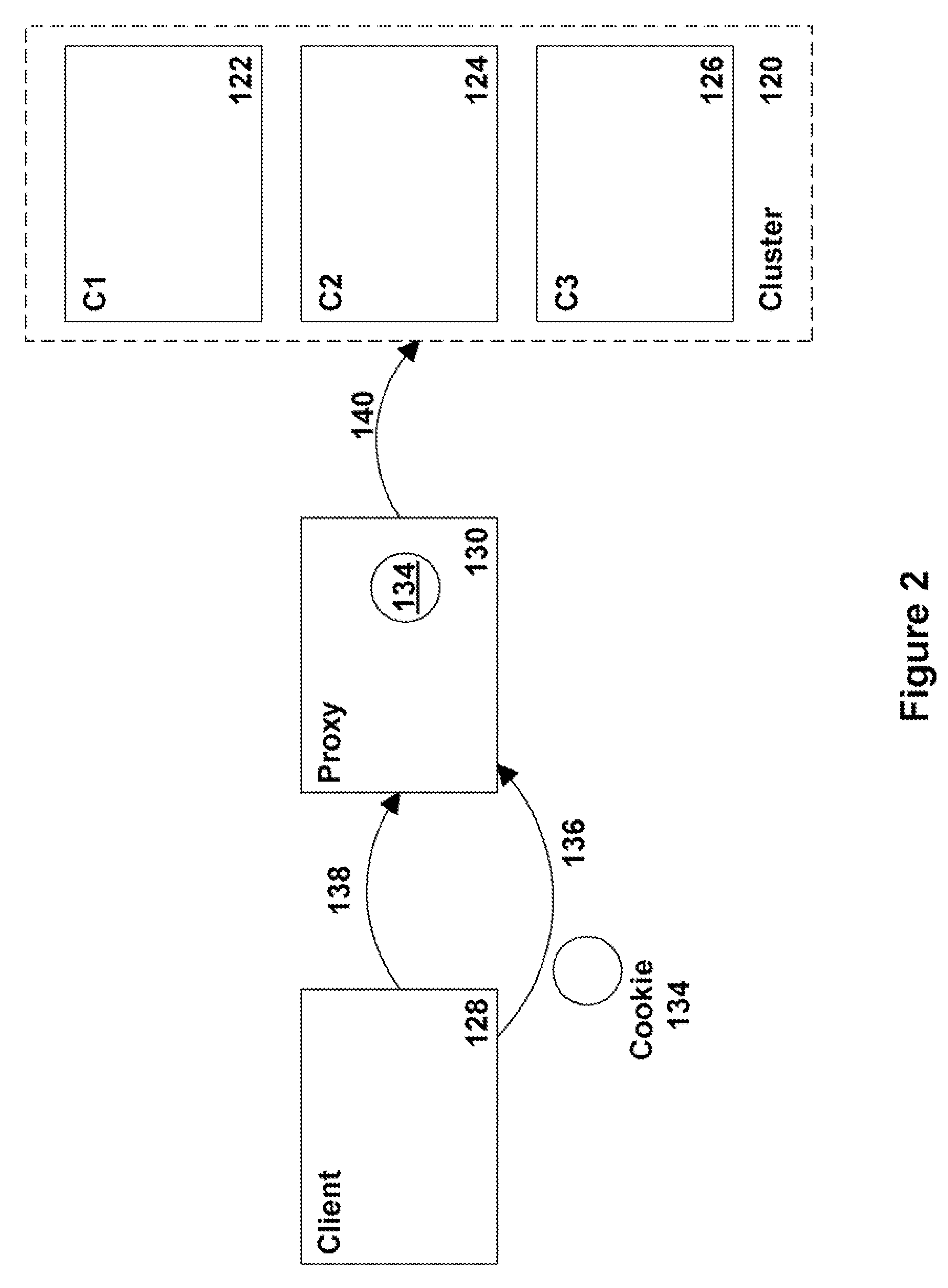
ActiveUS7603454B2Digital data processing detailsMultiprogramming arrangementsApplication serverClient-side
A system and method for clustered tunneling of requests in application servers and other systems is provided. The system includes a client, a cluster having a plurality of members, and a proxy. The cluster does not advertise the internal addresses of its members since clients might attempt to directly connect to that member. Instead, the client is configured to include a tunneling layer within which the proxy address is set. The advertised address of the cluster member is then set in a header at the client. During runtime, the client connects to the proxy as before, but then uses its internal information to connect or communicate with the appropriate cluster member. In accordance with an embodiment the client sets a cookie which is then sent to the proxy. The proxy re-writes the cookie with the appropriate cluster member information and uses this information to tunnel the request to the appropriate server.
Owner:ORACLE INT CORP
Memory system and memory initializing method
InactiveUS20090222636A1Memory architecture accessing/allocationMemory adressing/allocation/relocationComputer hardwareStart up
A memory system includes a controller that writes internal information concerning an operation state of the memory system in a special LBA area allocated to a predetermined logical address range in a second storing memory and writes the internal information in a first storing memory, and reads out, when the memory system is started up, the internal information to manage the operation state. The controller stores the internal information written in the first storing memory in the second storing memory as a snapshot when a predetermined condition is satisfied and, when an error occurs and the internal information written in the special LBA area cannot be read out when the memory system is started up, captures the internal information stored as the snapshot into the first storing memory and reads out the internal information.
Owner:KK TOSHIBA
Method and system for scoring texts
ActiveUS20110072011A1Reduce dependenceMore valueDatabase updatingDigital data processing detailsSubject matterInside information
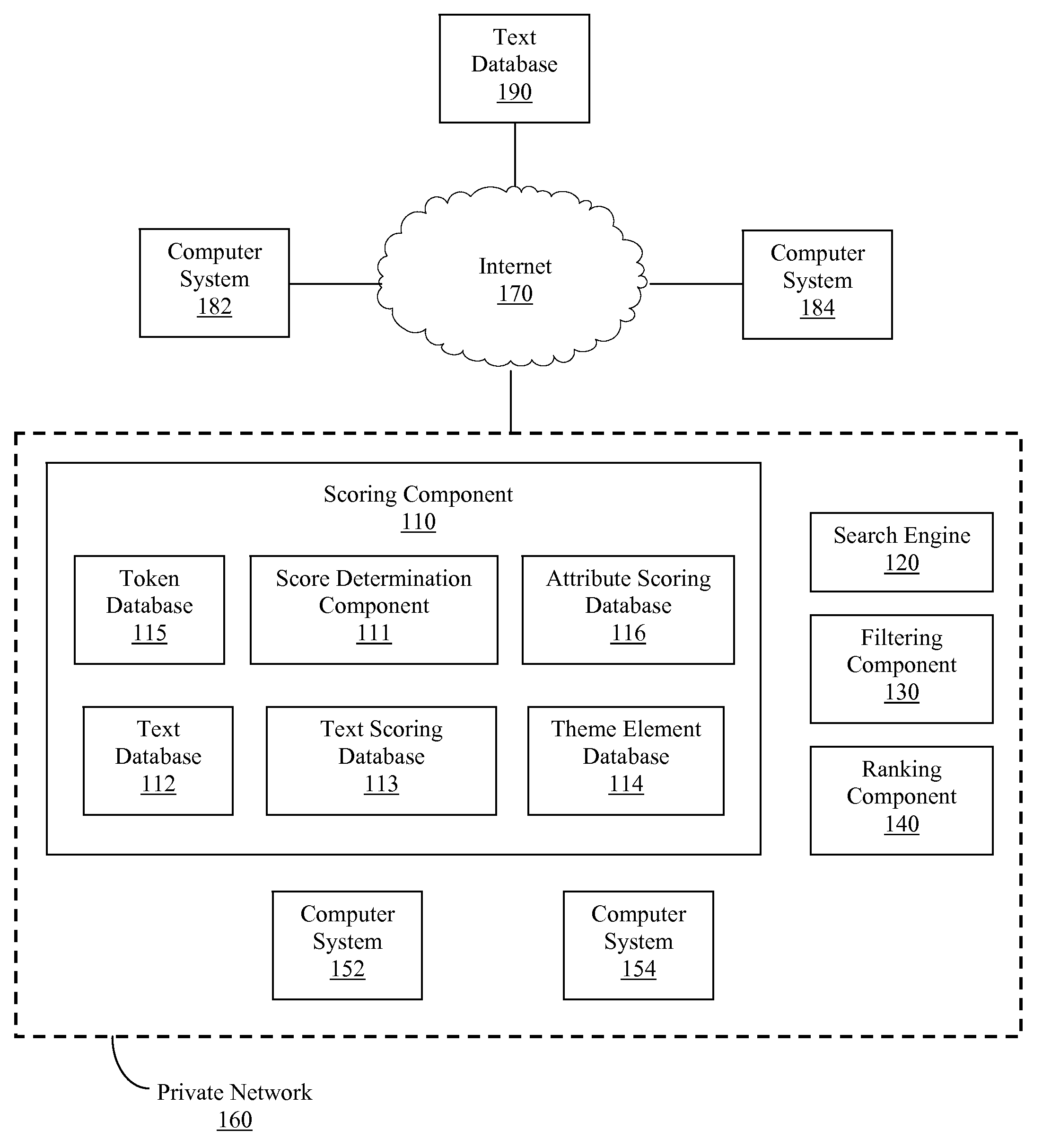
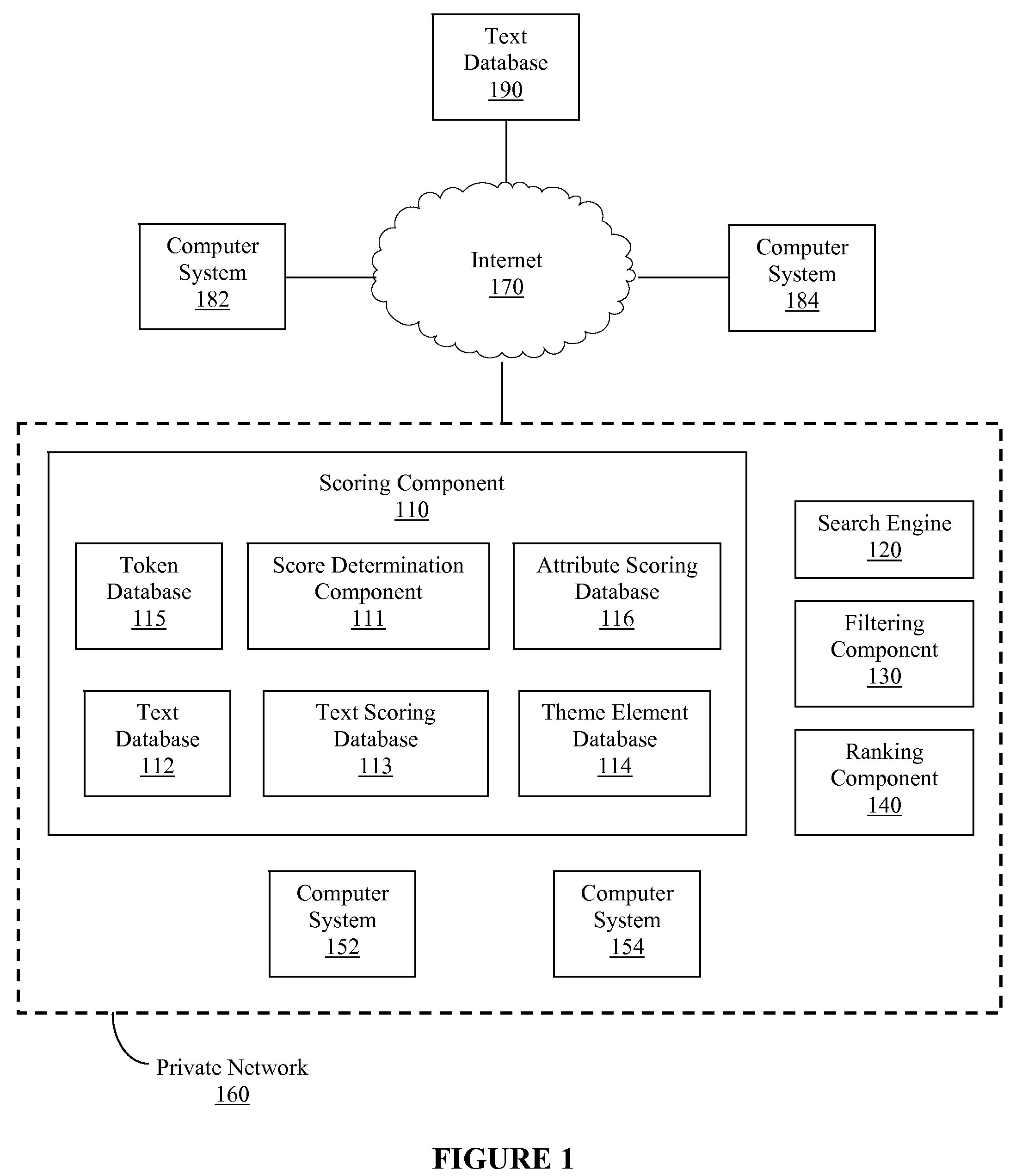
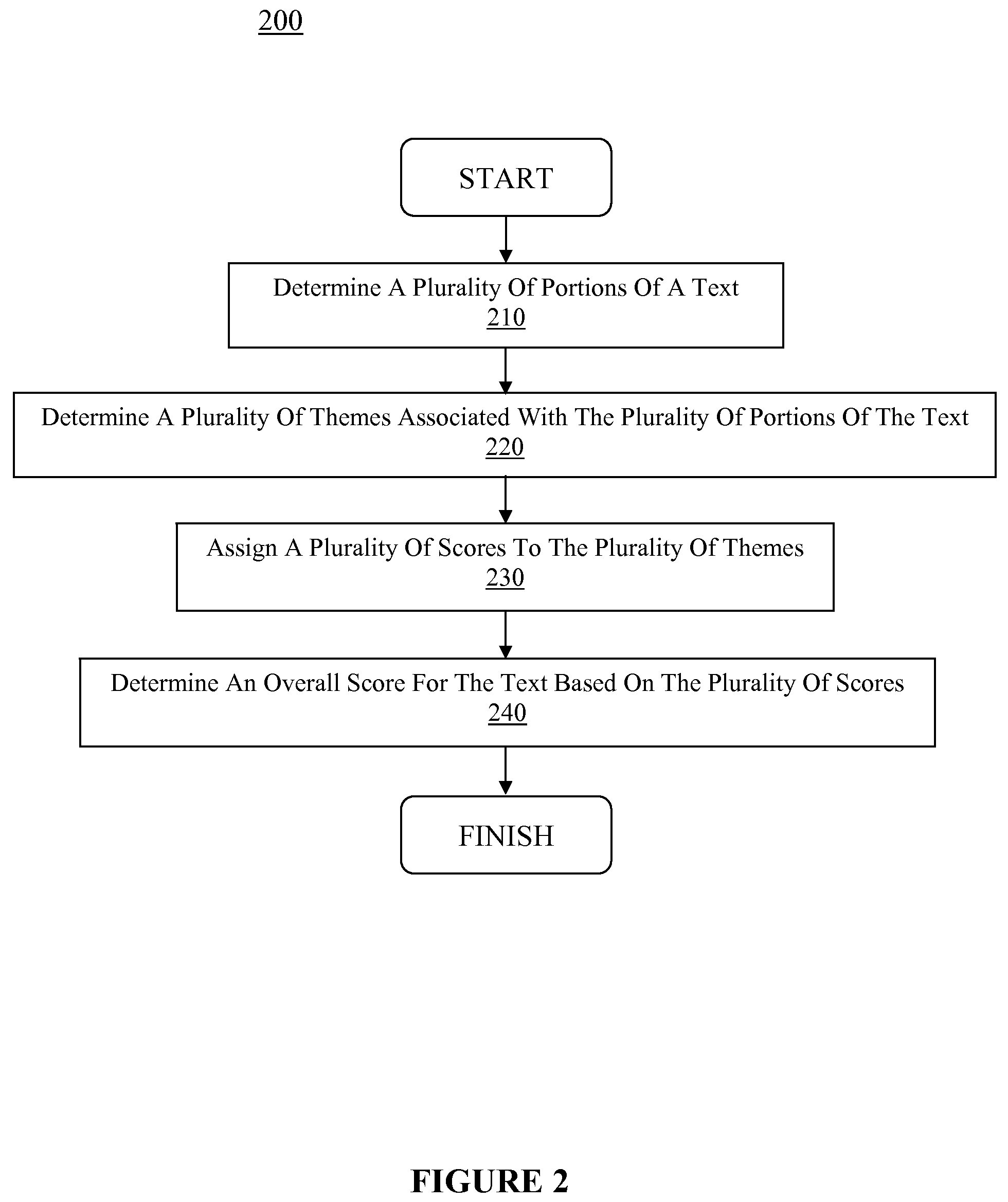
A computer-implemented method, computer-readable medium and system for scoring a text are disclosed. Themes within one or more texts may be determined and used to score each text, where an overall score for each text may indicate a respective importance and / or value of each text. The score for each text may be determined based upon a number of themes, type of themes, frequency of theme elements associated with the themes, distribution of theme elements associated with the themes, location of themes in the text, some combination thereof, etc. In this manner, the importance or value of one or more texts may be determined more accurately using information within each text with reduced reliance upon external information. Additionally, more relevant search results can be returned to a user by using internal information to perform ranking operations and / or filtering operations associated with a search.
Owner:LEXXE
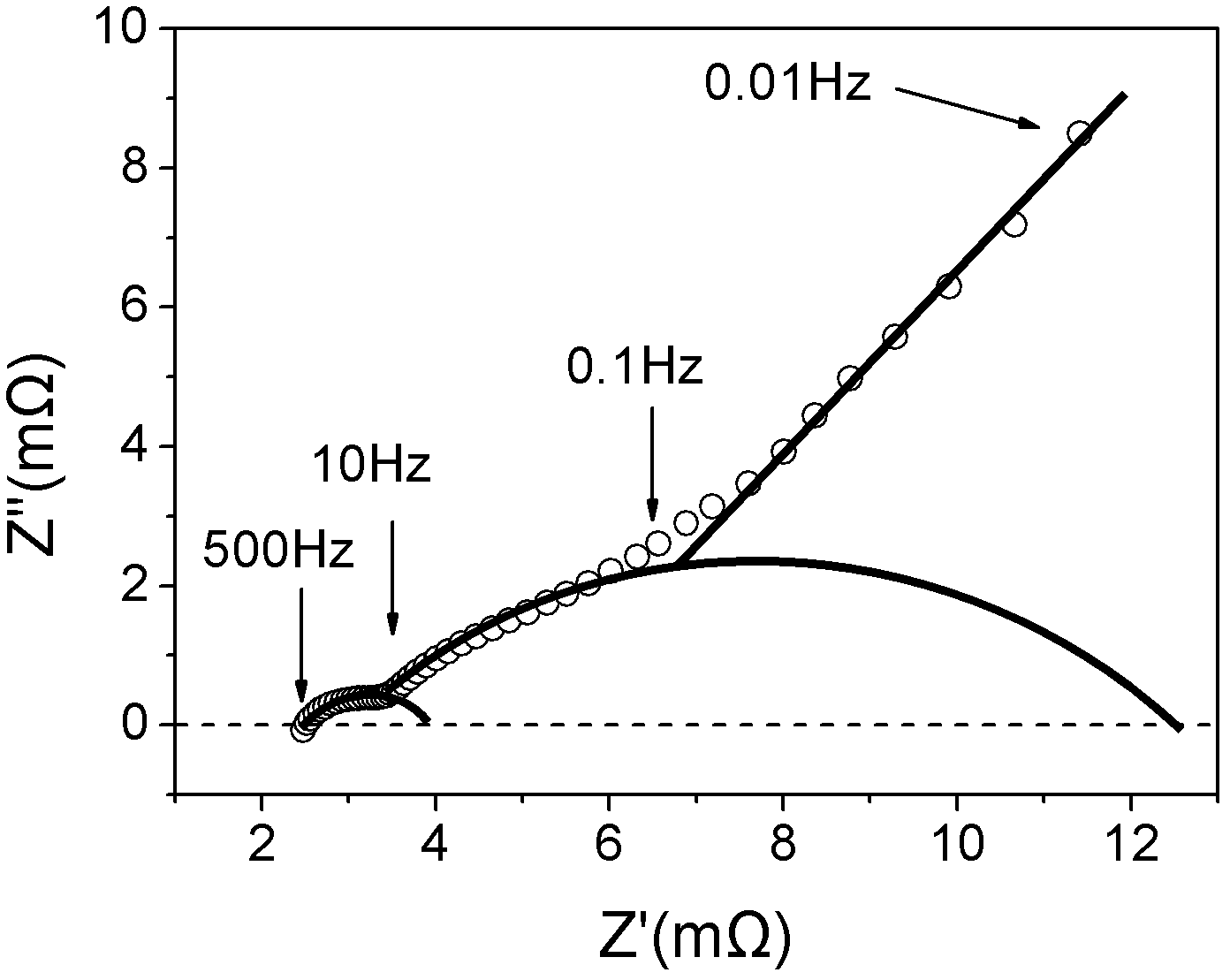
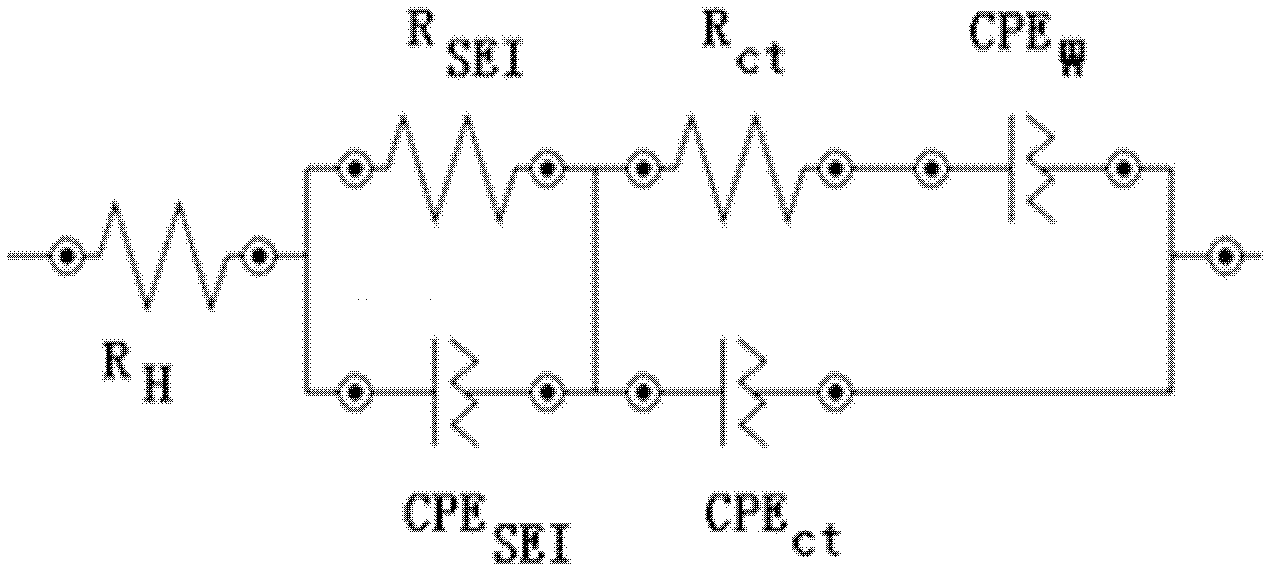
Battery sorting method based on alternating-current impedance spectrum
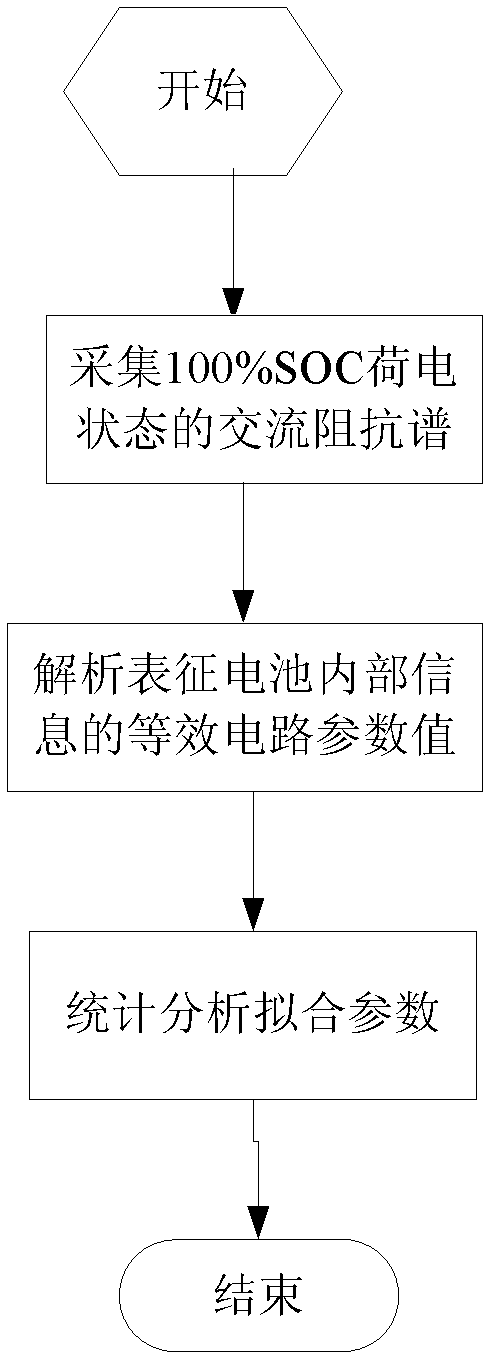
ActiveCN102553838AAccurate reflection of healthAccurately reflects electrolyte concentrationSortingLithiumElectrical battery
The invention relates to a lithium ion secondary battery, in particular to a sorting method based on an alternating-current impedance spectrum. The method comprises the steps of (1) acquiring the alternating-current impedance spectrum; (2) analyzing equivalent-circuit parameters; and (3) conducting statistic analysis on the equivalent-circuit parameters. In the method provided by the invention, an electrode structure inside a battery system can be detected without damaging a battery, the inner information such as health condition of the battery, the electrolyte concentration, diaphragms and SEI (Solid Electrolyte Interface) membranes are accurately reflected; and according to the information, the coefficient of concordance is calculated by utilizing the principle of statistics, so that the consistency of the inner structure of the sorted battery can be ensured sufficiently, the differences of the sorted batteries are reduced obviously, and the defects of a sorting method in prior arts can be overcome.
Owner:许昌许继电科储能技术有限公司
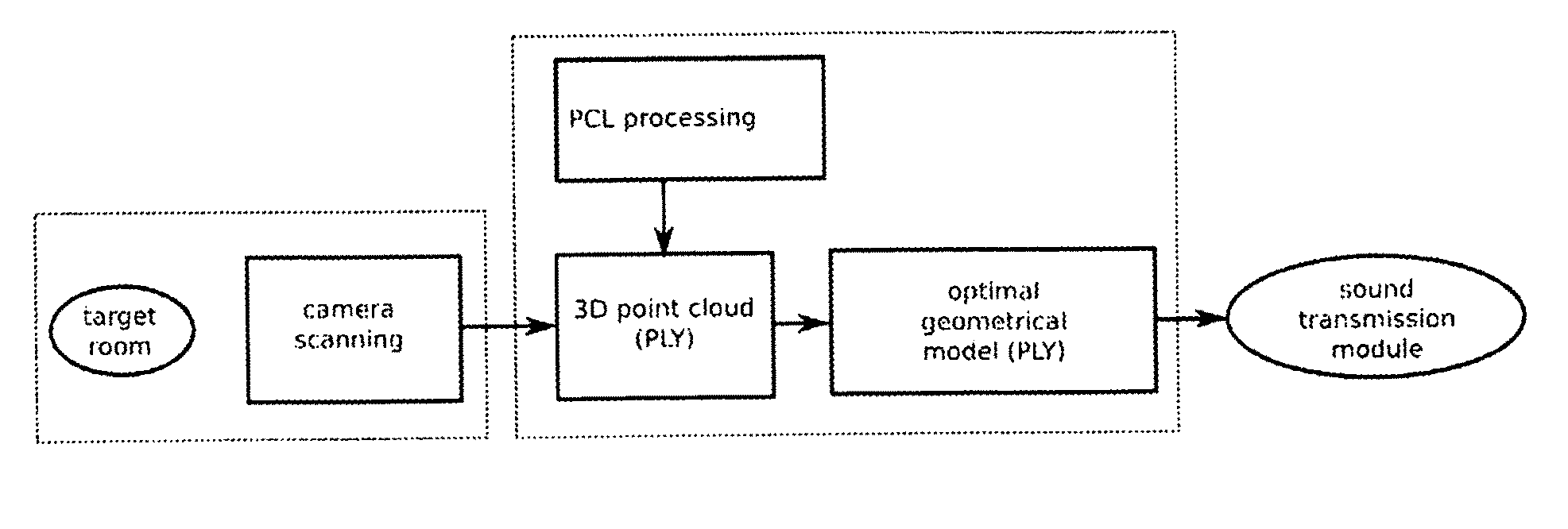
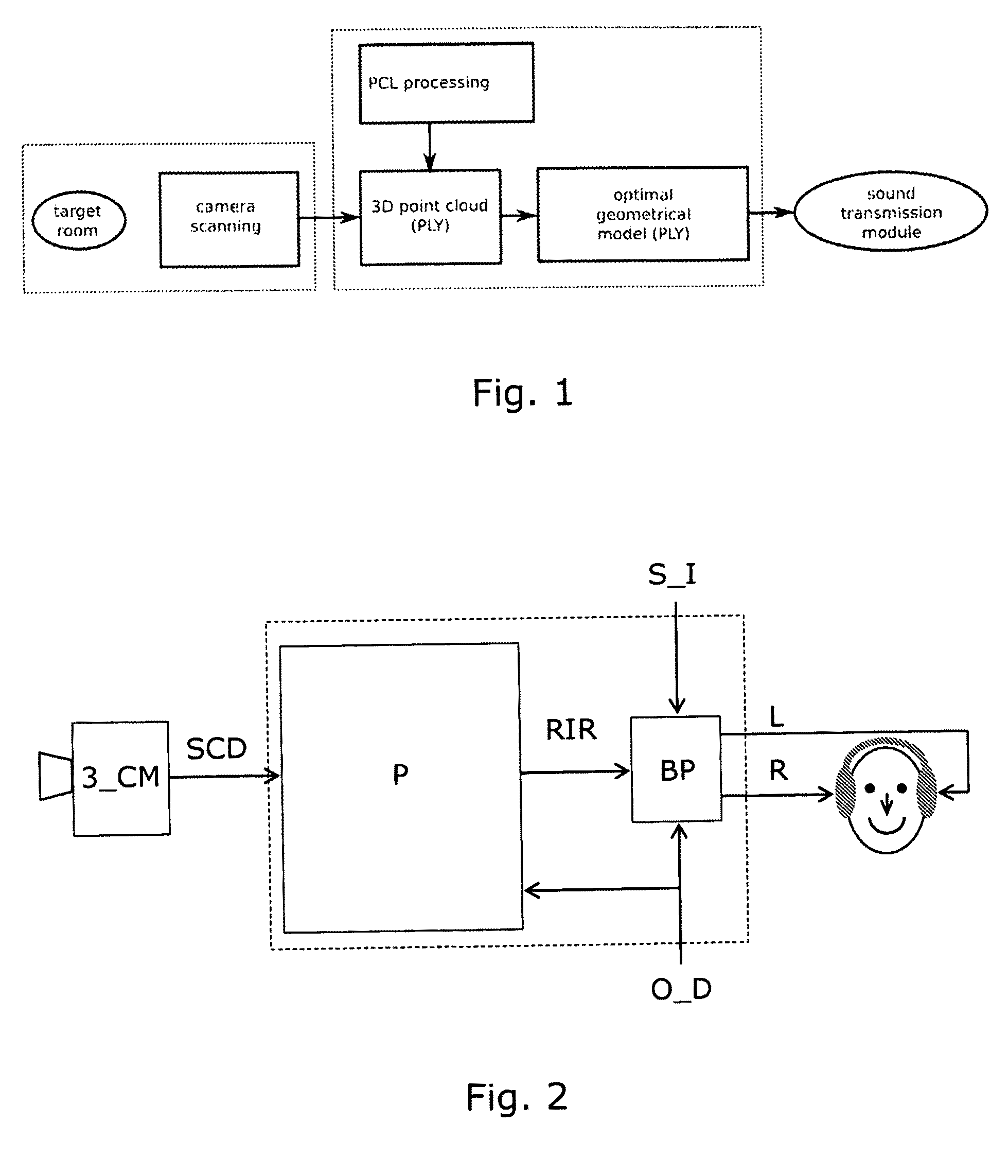
Method and device for modelling room acoustic based on measured geometrical data
InactiveUS20160109284A1Convenient verificationEasily be real-time updatedReverberation timeFrequency/directions obtaining arrangementsAcoustic transmissionRough surface
The invention provides a method for generating an output indicative of acoustical sound transmission in a room. By using e.g. a point cloud representation of an acoustic environment, it is possible to calculate its acoustics from the interior information obtained from the depth camera. This approach is suitable e.g. for run-time applications since it is not based on an audible excitation that can disturb running audio. Also, the point-cloud model can be updated in real time according to the scene changes detected by depth-camera. This allows efficient acoustical simulation of dynamic, interactive environments. Although only geometrical information of a room is provided, high amount of surface details leaves possibility for implementation of material recognition algorithms that involve semantic mapping. This can provide information of reflective properties of surfaces or objects at a point level. Also, a high amount of details allows a good approximation of complex geometries, e.g. porous materials, and rough surfaces, thus a more natural simulation of wave phenomena like diffraction and scattering is possible.
Owner:AALBORG UNIV
Semiconductor device saving data in non-volatile manner during standby
InactiveUS6914845B2Saving dataTotal current dropSafety arrangmentsDigital storageControl signalEngineering
A power control unit activates a control signal ST for a circuit block to be set to a standby state before turning off power of the circuit block or a whole chip, and saves an operation result of data processing of the circuit block into a memory unit. When the power is again supplied to the circuit block in the standby state, the power control unit activates a control signal RES after the power supply is started and restores the data saved in the memory unit to the circuit block. Flip-flops in the circuit block are connected in series when the saving or restoring of data is performed, and perform a data transfer operation with a path different from that in a normal operation. Therefore, a semiconductor device can be provided which can rapidly transit to a standby mode having reduced current consumption while holding internal information.
Owner:RENESAS ELECTRONICS CORP
Semiconductor device saving data in non-volatile manner during standby
InactiveUS20050195664A1Saving dataTotal current dropDigital storageControl signalCurrent consumption
A power control unit activates a control signal ST for a circuit block to be set to a standby state before turning off power of the circuit block or a whole chip, and saves an operation result of data processing of the circuit block into a memory unit. When the power is again supplied to the circuit block in the standby state, the power control unit activates a control signal RES after the power supply is started and restores the data saved in the memory unit to the circuit block. Flip-flops in the circuit block are connected in series when the saving or restoring of data is performed, and perform a data transfer operation with a path different from that in a normal operation. Therefore, a semiconductor device can be provided which can rapidly transit to a standby mode having reduced current consumption while holding internal information.
Owner:RENESAS TECH CORP
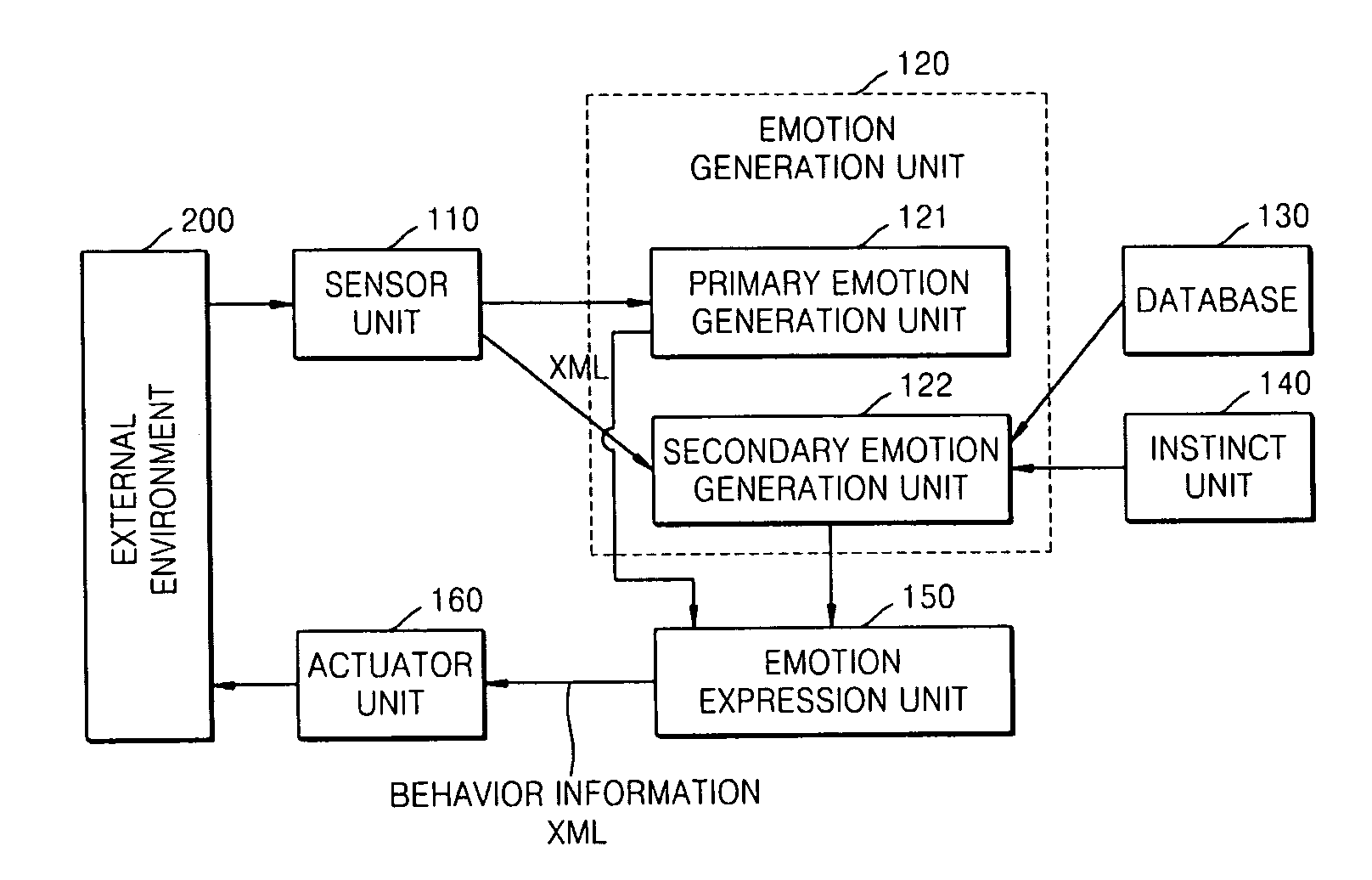
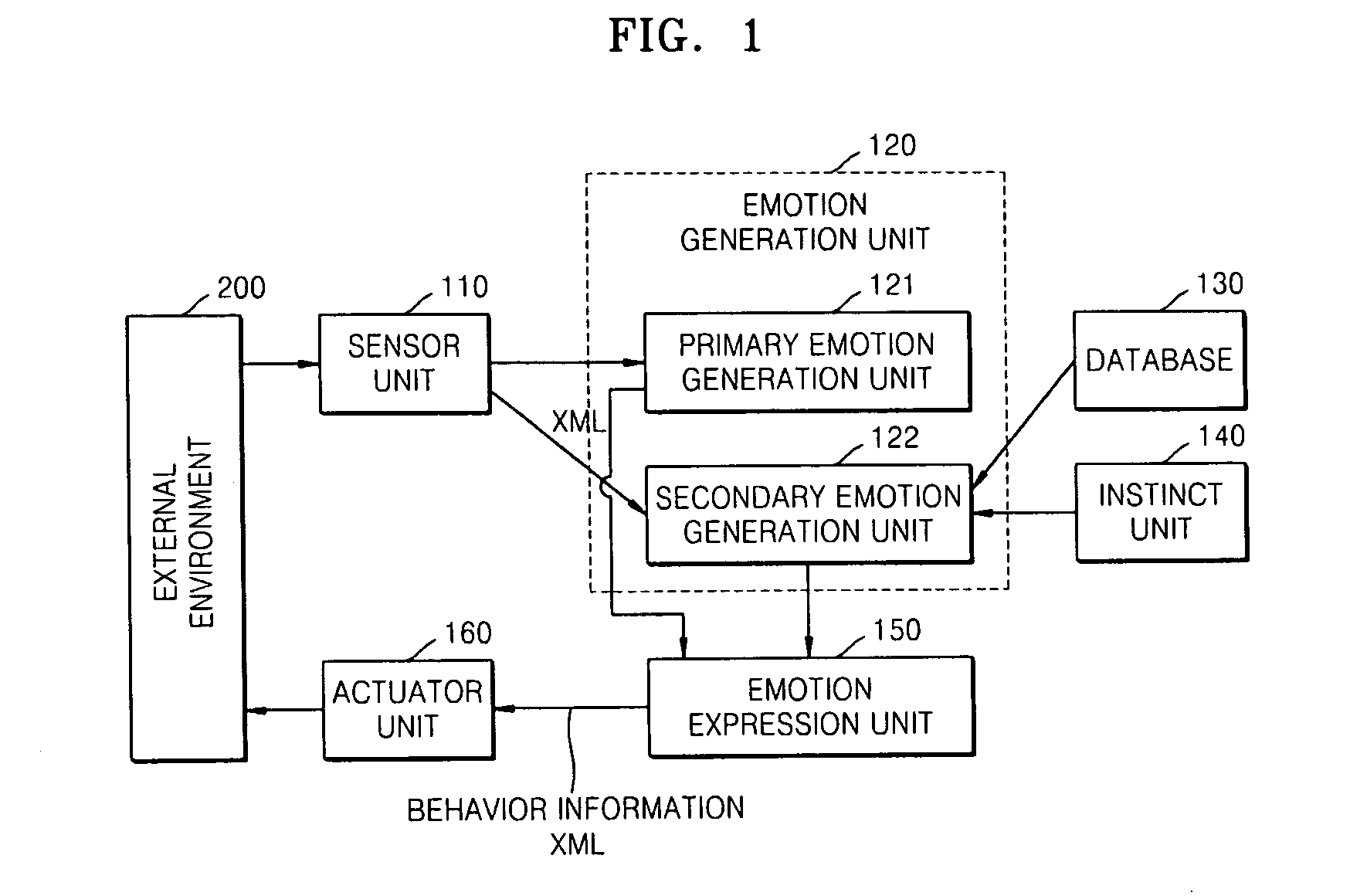
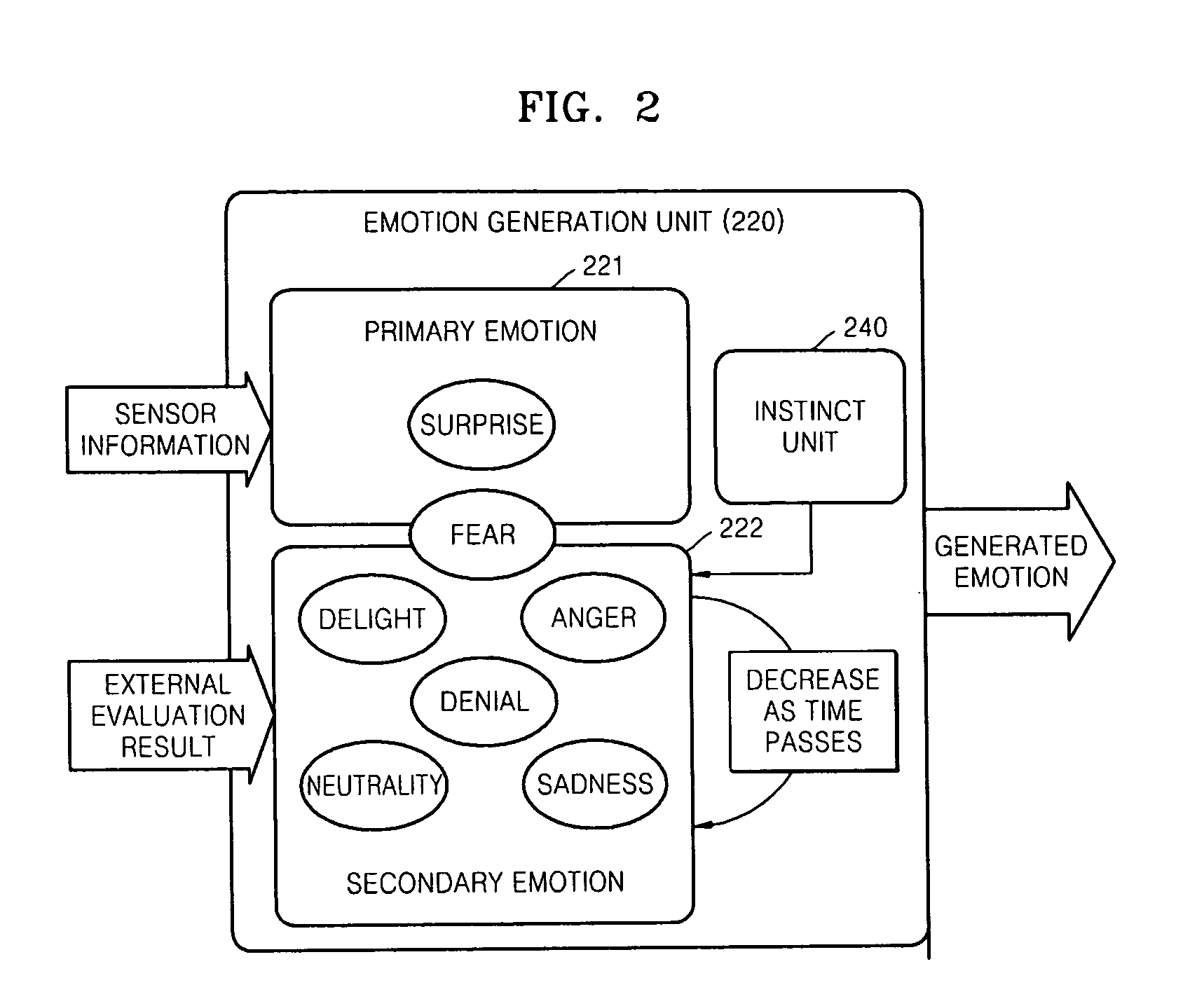
Robot for generating multiple emotions and method of generating multiple emotions in robot
A robot for generating multiple emotions is provided. The robot includes a sensor unit sensing external environment information, a database unit storing a predetermined list including information on types of behavior the robot is allowed, a user's reaction corresponding to each behavior of the robot, and favorite objects of the robot, a primary emotion generation unit generating an emotion corresponding to characteristics of the sensed information when the sensed information exceeds a predetermined threshold value, and a secondary emotion generation unit generating an emotion corresponding to characteristics of the sensed information based on the information sensed by the sensor unit, the list stored in the database unit, the amount of internal power of the robot, internal information on the robot indicating the existence of an operational error and an elapse of time.
Owner:ELECTRONICS & TELECOMM RES INST
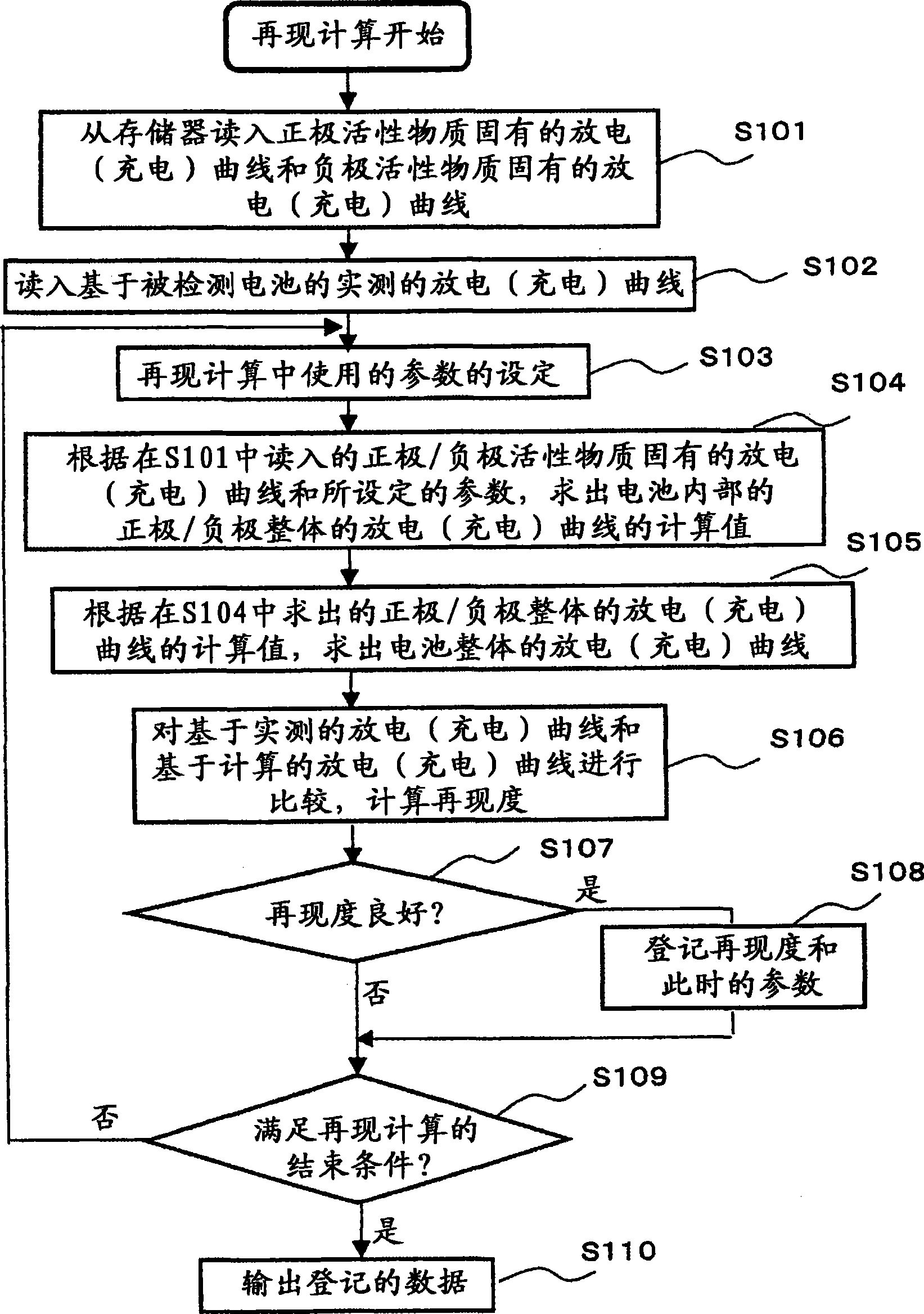
Internal information testing method of secondary battery and apparatus
The present invention aims to detect the situation of positive electrode in a secondary battery and the situation of a negative electrode therein without disassembling the battery by a simple method. The present invention provides a method for detecting internal information of a secondary battery, comprising a first step for acquiring charge and / or discharge curves inherent in a positive electrode material and a negative electrode material, as reference data, and acquiring charge and / or discharge curves of a detected battery as actually-measured values, a second step for determining charge and / or discharge curves of a positive electrode and a negative electrode therein, using the charge and / or discharge curves inherent in the positive electrode material and inherent in the negative electrode material,; the charge and / or discharge curves of the detected battery as the actually-measured values, and predetermined correction parameters, and a third step for outputting at least one of the charge and / or discharge curves of the positive electrode and the negative electrode and the correction parameter used for calculation, which have been determined at the second step.
Owner:HITACHI AUTOMOTIVE SYST LTD
Holistic dynamic information management platform for end-users to interact with and share all information categories, including data, functions, and results, in a collaborative secure venue
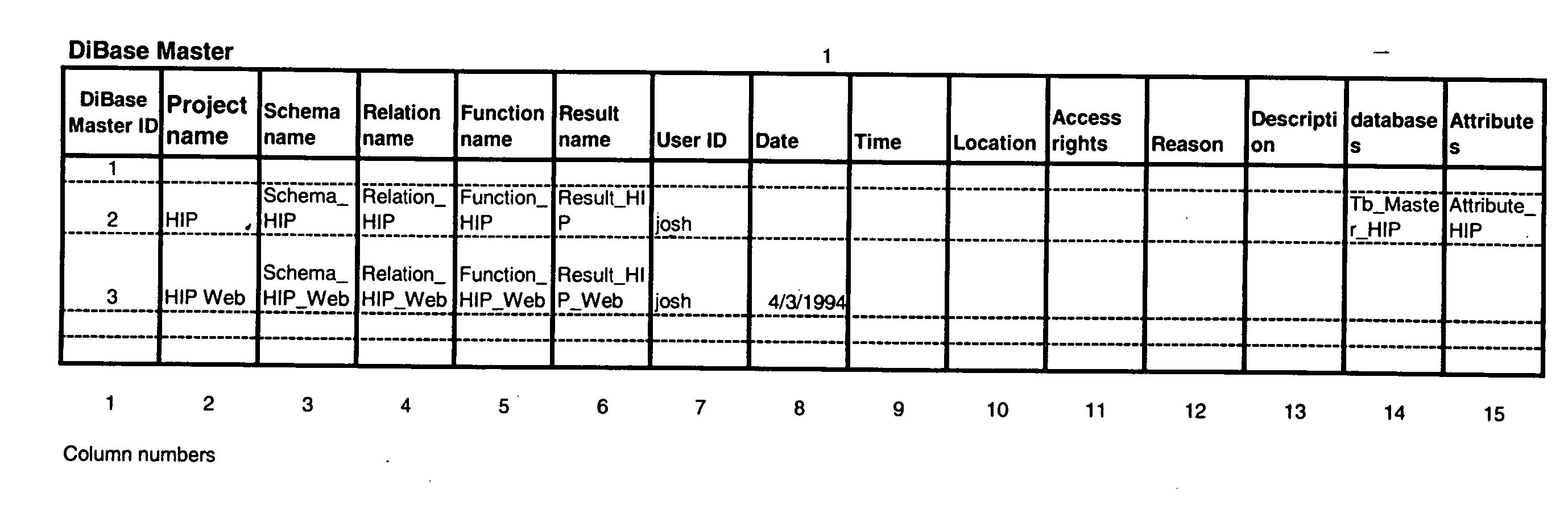
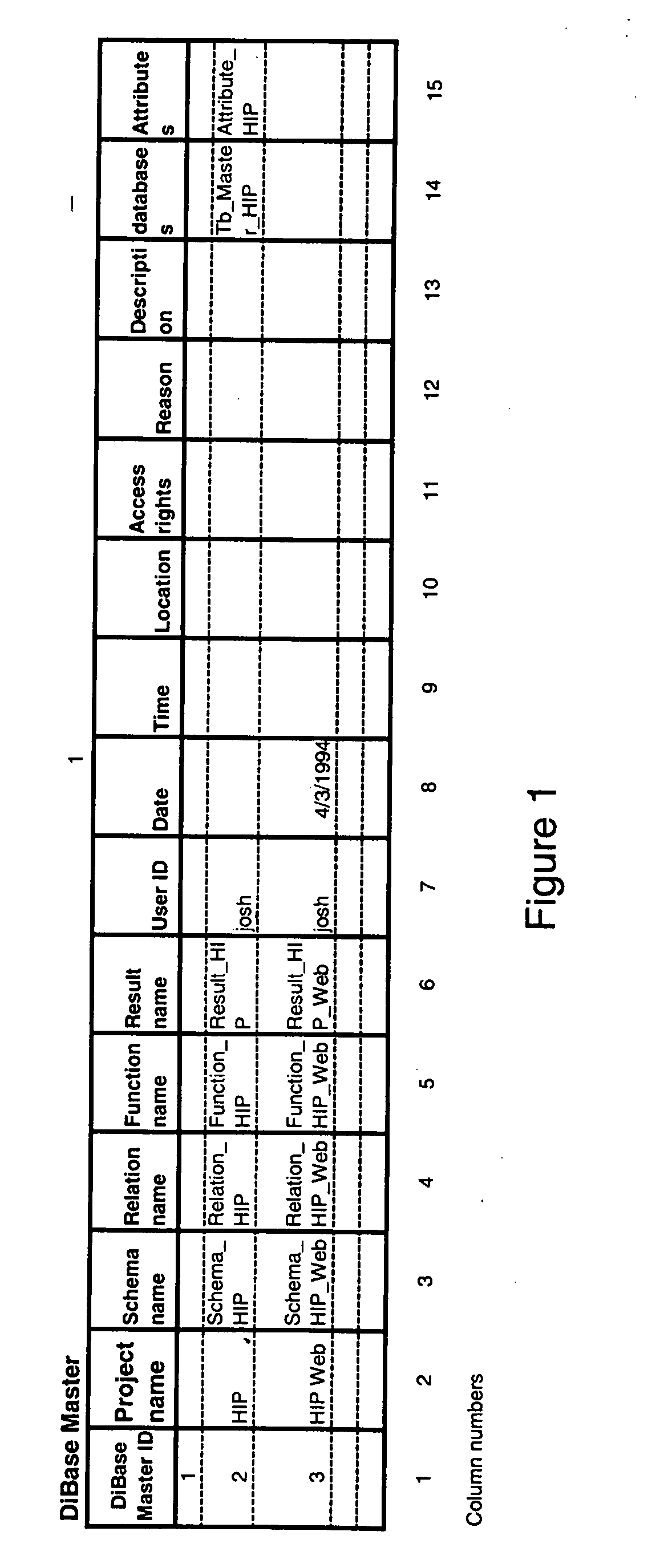
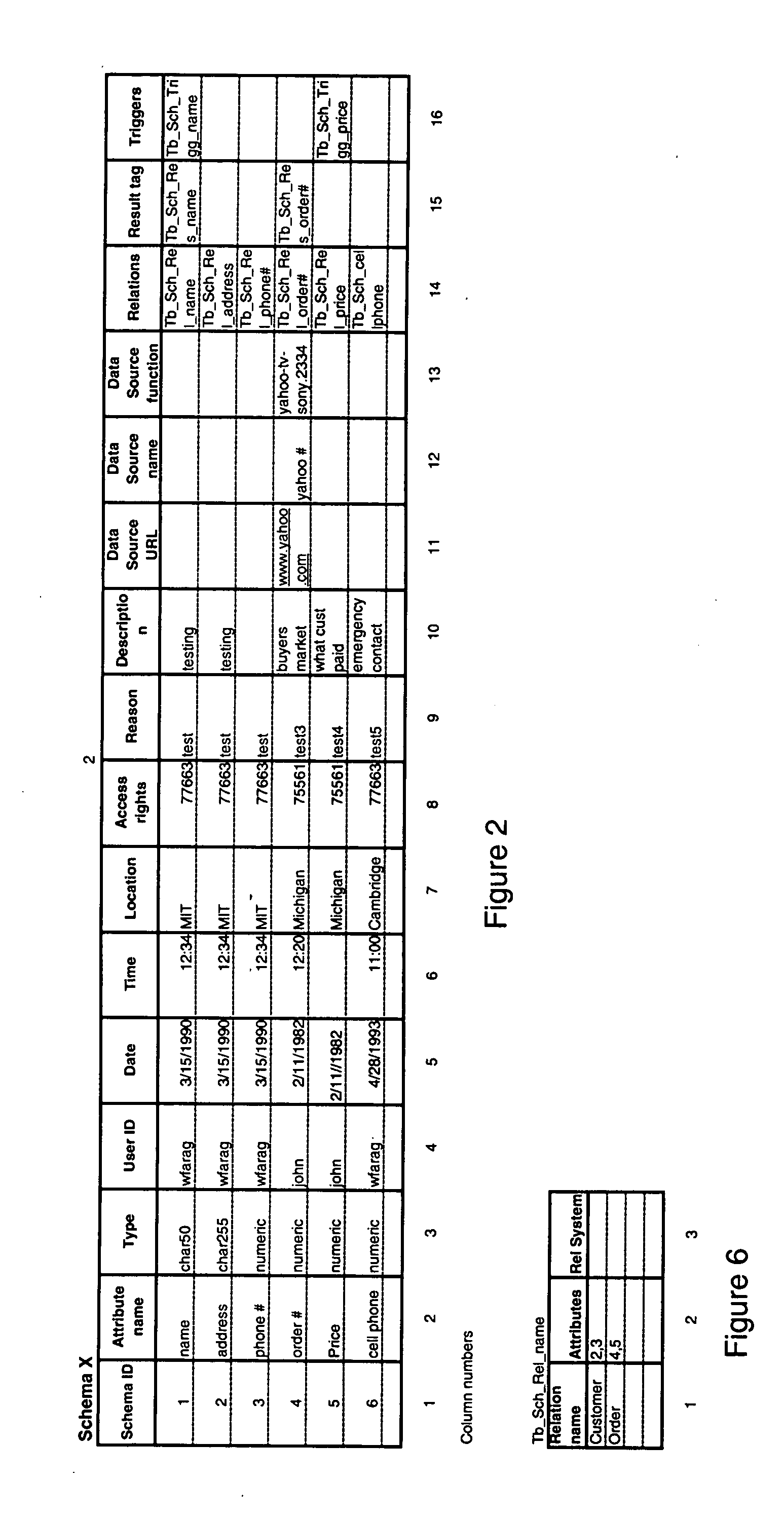
InactiveUS20050021523A1Digital data processing detailsWebsite content managementSystems managementLibrary science
A method, apparatus, and article of manufacture consistent with the present invention provide a development tool that enables end-users or automated systems to independently or collaboratively develop and manage all information item types as stored in the different categories to dynamically manipulate them across internal information categories or items from external sources in a networked environment. Manipulate enables users to securely on-the fly do activities best described as: to access, create, store, delete, modify, discover, collaborate, integrate, execute, re-run, track, limit-access-to, and share of information items. Information items of same type, for example, data items, are grouped together in a category for system management purposes, i.e. DBMS. However, all information categories are easily accessible to be linked together. The tool provides an integrity engine with modifiable rules to best suite the policies and procedures on how information items are manipulated by users as mandated by the entity managing the tool.
Owner:FARAG WAFIK
Techniques for analyzing data from multiple sources
ActiveUS20120030202A1Well formedDigital data information retrievalDigital data processing detailsMultiple criteriaData storing
Owner:ORACLE INT CORP
Graphical user interface based sensitive information and internal information vulnerability management system
ActiveUS8140664B2Rapid assessmentEasily identify and assessMemory loss protectionError detection/correctionTime informationOutput device
Owner:TREND MICRO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com