M2M (Machine-to-Machine) terminal security access method and terminal and management platform
A management platform and access method technology, applied in security devices, electrical components, wireless communications, etc., can solve the problems of terminals not providing security mechanisms, lack of application layer security mechanisms, etc., and achieve the effect of high security requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The technical solutions of the present invention will be described in further detail below with reference to the accompanying drawings and embodiments.
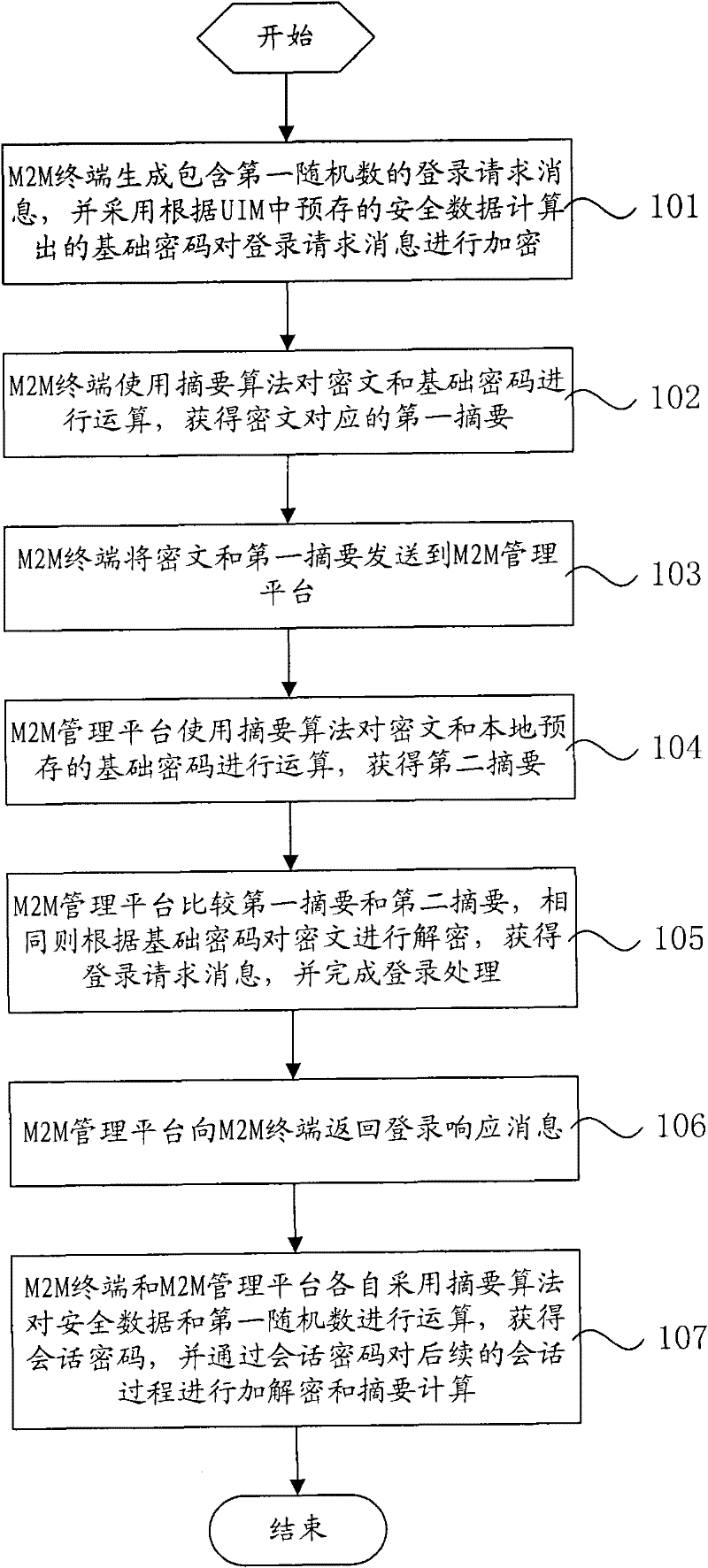
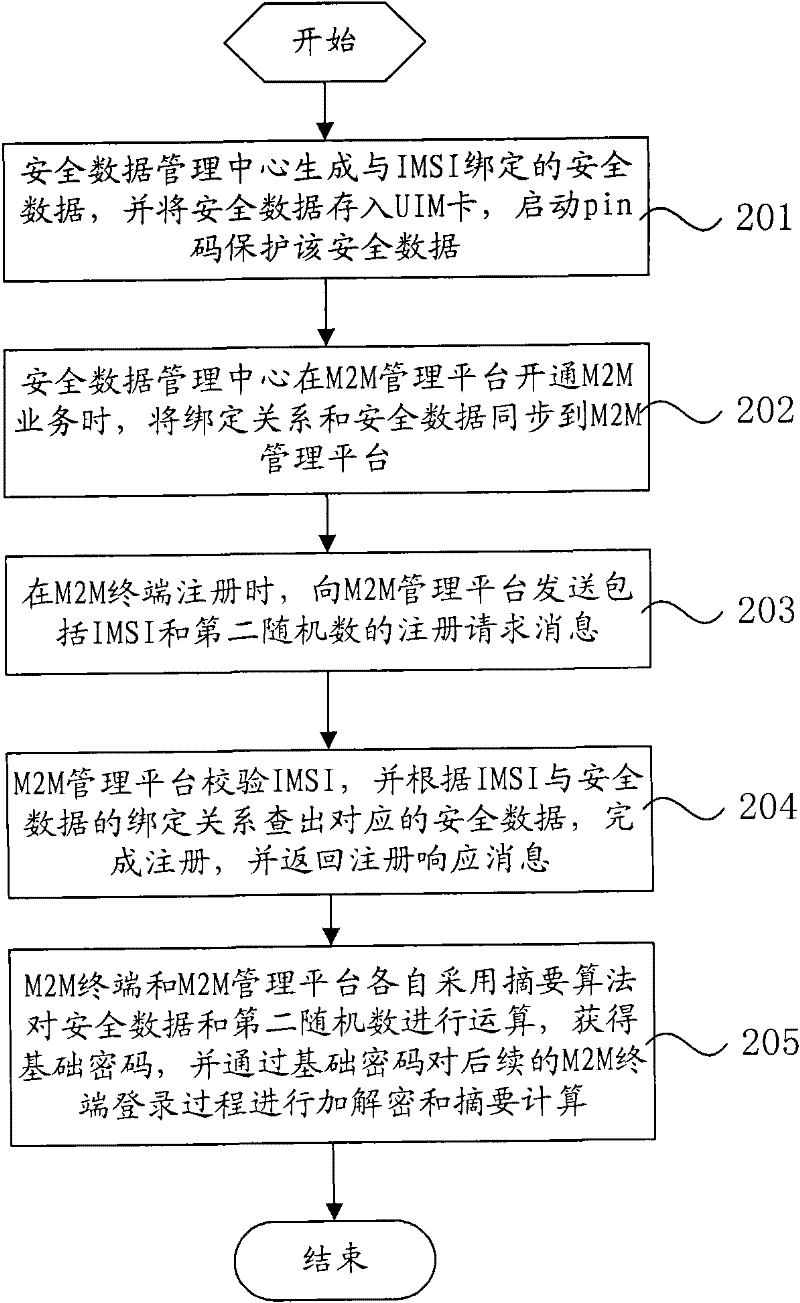
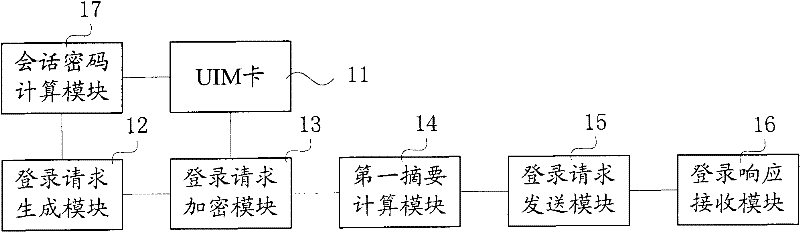
[0047] In the present invention, the built-in User Identity Module (UIM) card in the M2M terminal is used to save the security data, and the security data is also synchronized to the M2M management platform side during the registration process, and the M2M terminal and the M2M management platform are consistent. The security data can be used as the calculation basis of security passwords to realize the encryption and verification of data interaction. This method provides a relatively complete application layer security mechanism for the M2M terminal, which can meet the high security requirements in industry applications.
[0048] The present invention will be described below through several embodiments. Such as figure 1 As shown, it is a schematic flowchart of an embodiment of the M2M terminal secure access method of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com