Rapid authentication method and system for trusted execution environment
A technology of execution environment and authentication method, applied in transmission systems, digital transmission systems, secure communication devices, etc., and can solve problems such as complex processes, inability to reuse enclaves, and unfavorable applications processing requests from multiple users at the same time. , to achieve the effect of reducing interfaces, improving ease of use and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
[0056] A fast authentication method and system for a trusted execution environment of the present invention, related technical terms and explanations will be involved in the description of the embodiments, summarized in Table 1 below.
[0057] Table 1 Explanation of relevant technical terms.
[0058]
[0059]
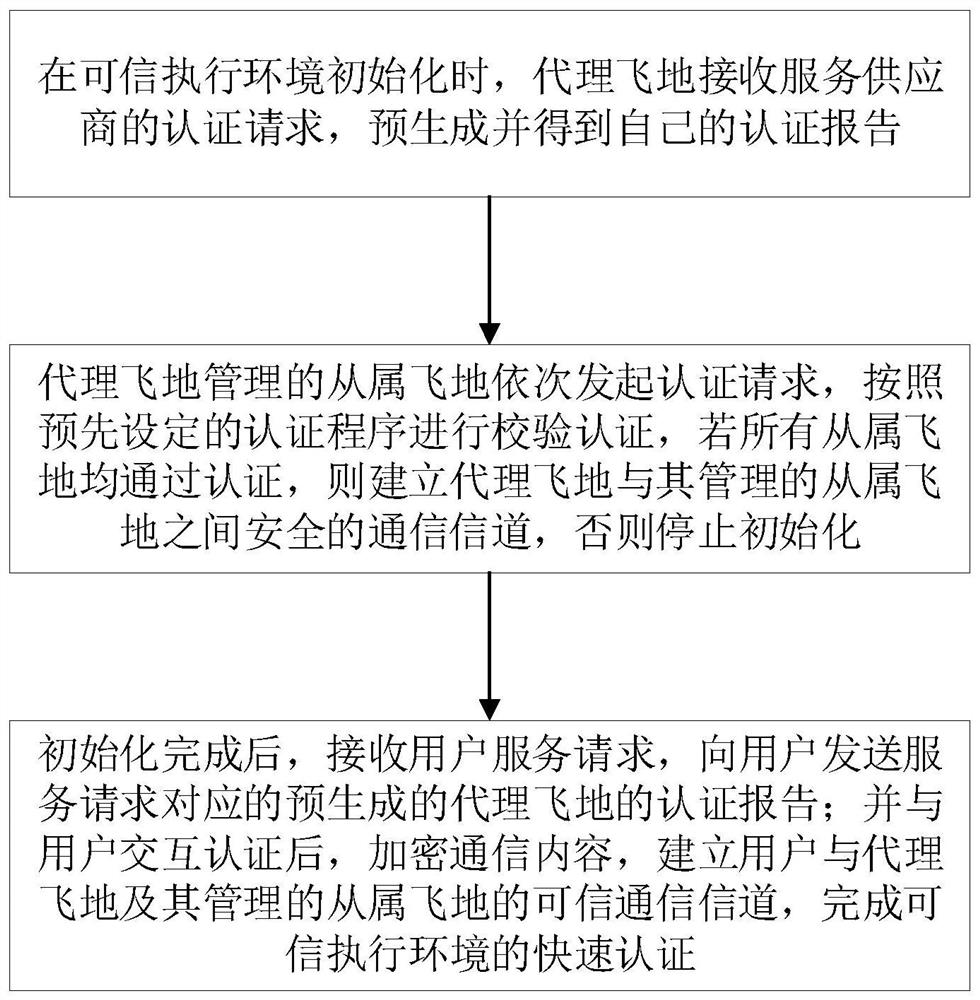
[0060] A fast authentication method of a trusted execution environment in the present invention, such as figure 1 shown, which includes,
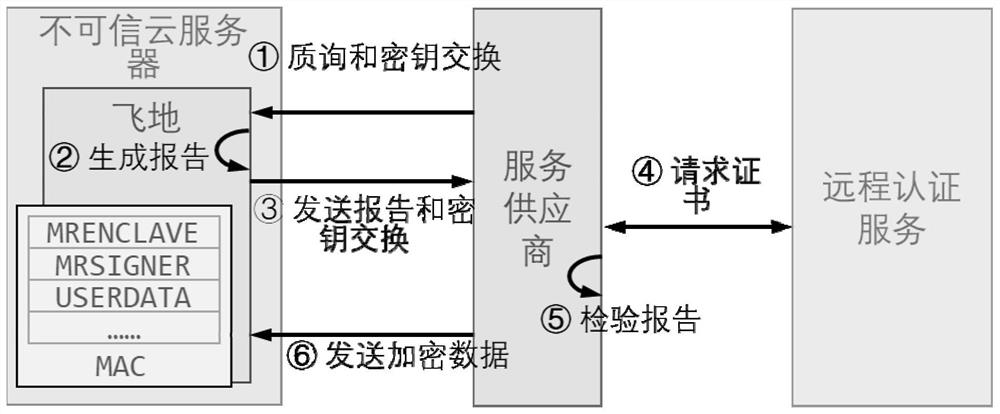
[0061] When the trusted execution environment is initialized, the proxy enclave receives the certification request from the service provider, pre-generates and obtains its own certification report;
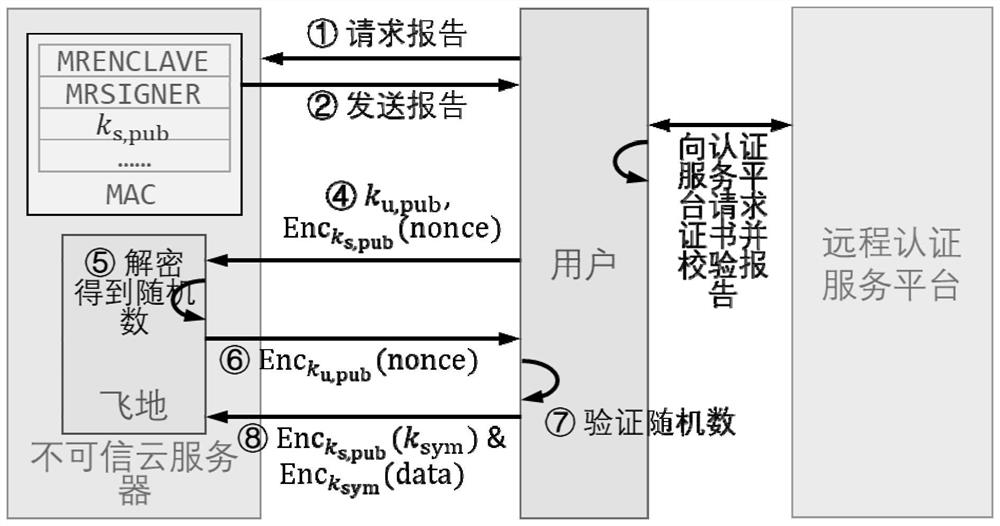
[0062] The subordinate enclaves managed by the proxy enclave initiate authentication requests in turn, and perform verification and authenticat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com