Action control method based on LSM programme
A behavior and program technology, applied in the field of security server equipment, can solve the problems of low detection efficiency, high false alarm rate, huge pattern library, etc., and achieve the effect of high detection efficiency and low false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
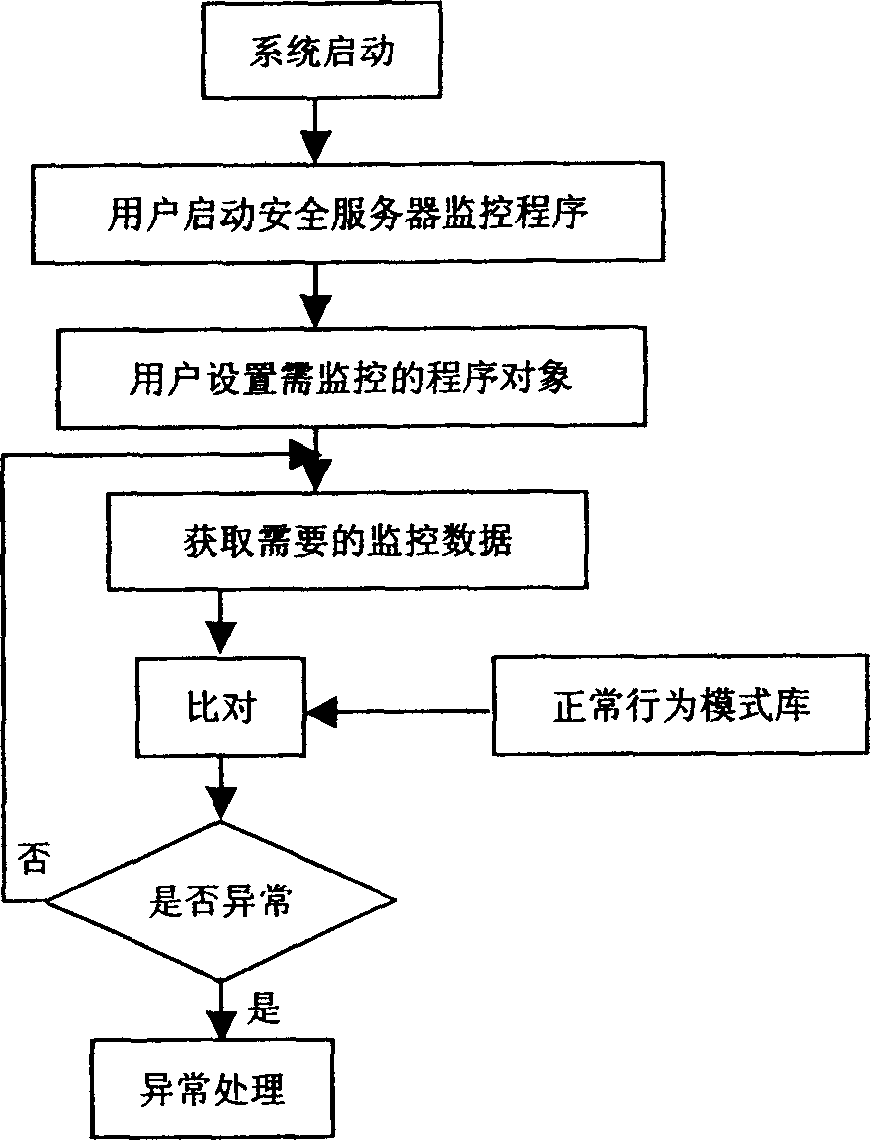
[0012] like figure 1 shown. After the user starts the security server device monitoring program used as an Internet server, the program object to be monitored is manually set according to the requirement. After obtaining the intercepted data of the monitored program, the security server will hand it over to the identification mechanism for processing. Usually, the intercepted data will be compared with the normal behavior pattern database of the monitored program, and necessary exception handling will be performed. If it is normal, it will continue. The prior art library of normal behavior patterns for monitored programs is large.
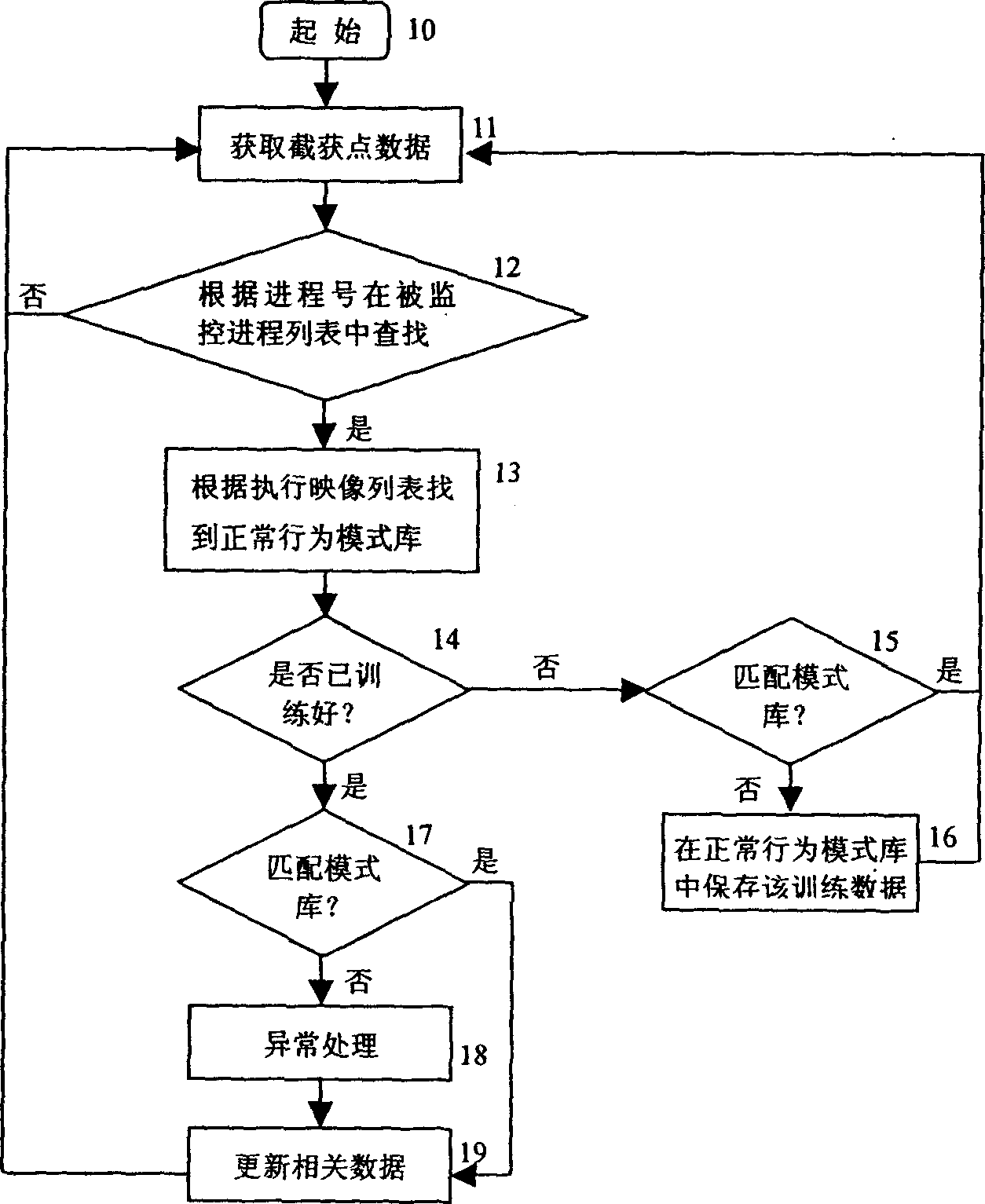
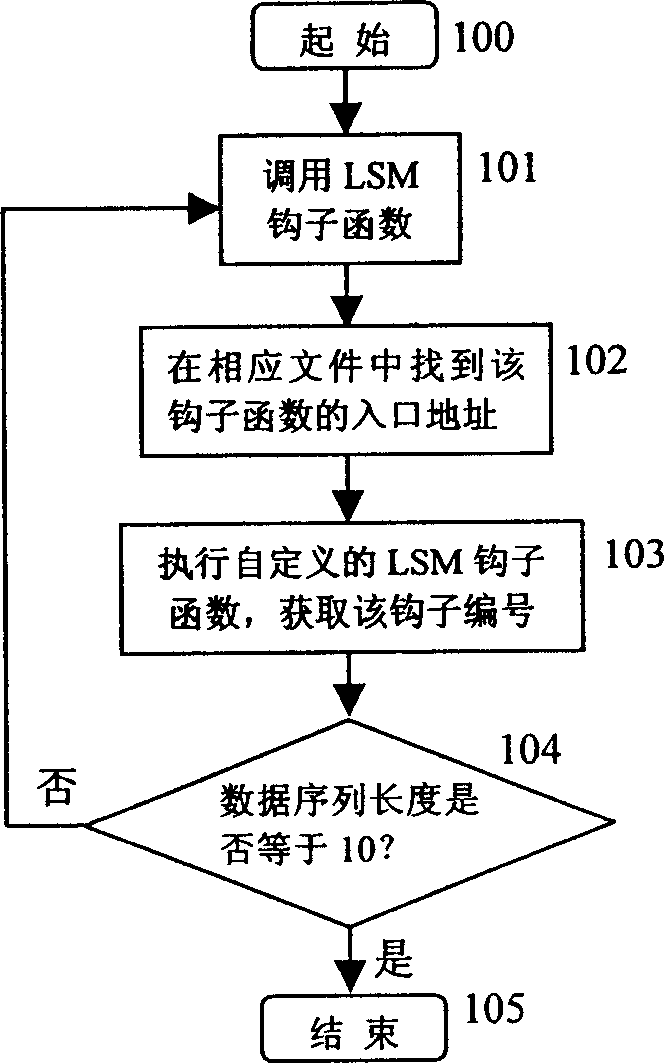
[0013] The inventive method such as figure 2 shown. Step 10 is the initial action. Step 11 completes that the security server device obtains the LSM interception point data and generates an LSM interception point sequence with a length equal to 10. The data sequence is obtained by the specially designed processing method of the present invent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com