Method for negotiating about cipher key shared by users and application server
An application server and shared key technology, applied in the field of negotiating shared keys, can solve problems such as attacks, lack of user authentication in one-way authentication, and achieve the effect of two-way authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
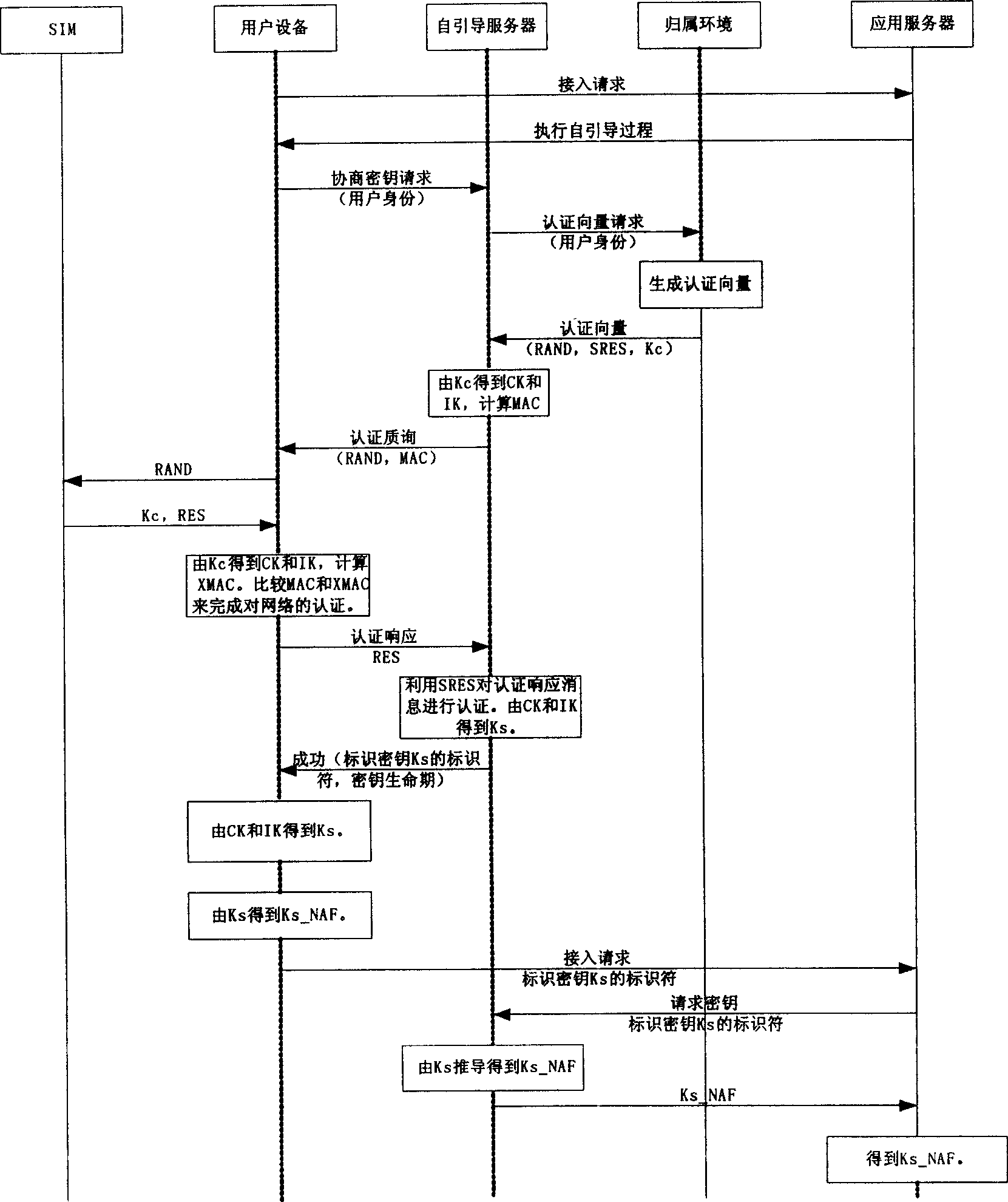
[0030] Below in conjunction with accompanying drawing, the implementation of technical scheme is described in further detail:
[0031] 1. The user device initiates an access request to the application server. At this time, the user and the application server do not share a valid pre-shared key.
[0032] 2. The application server sends a response to the user, requesting the user to perform a self-guidance process with the self-guidance server.
[0033] 3. The user equipment sends a negotiation key request to the bootstrap server, which contains the identity of the user.
[0034] 4. The bootstrap server requests the authentication vector from the home environment according to the identity of the user.
[0035] 5. Attribution environment According to the identity of the user, the user is a 2G user, and the corresponding authentication vector is generated as a GSM triplet (RAND, SRES, Kc).
[0036] 6. The home environment sends the authentication vector to the bootstrap server. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com