Localisation of image tampering
A technology of image and identification bit, which is applied in the field of identification and positioning of image tampering, and can solve problems such as the complexity of identification problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The invention is described in detail below by means of an embodiment described with reference to a surveillance system. However, the invention is not meant to be limited to those exemplary embodiments described with reference to the monitoring system, and modifications and other applications thereof will be readily apparent to a person skilled in the art within the scope of the appended independent claims.
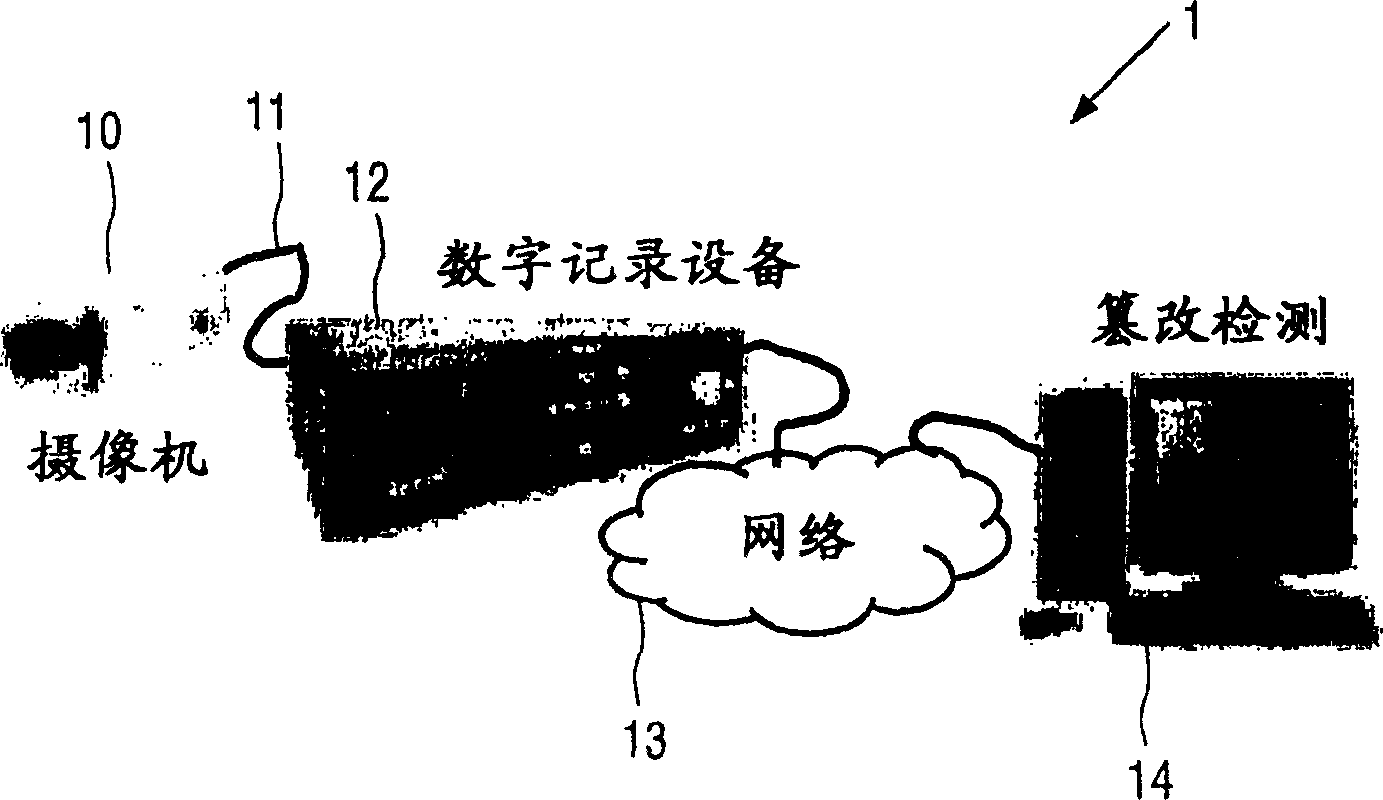
[0036] figure 1 The layout of a typical surveillance system 1 is illustrated. It usually consists of the following components:
[0037] - at least one video camera 10 with a video output 11 usually in an analog format such as PAL or NTSC,
[0038] - a digital recording device 12 which receives video input from a plurality of cameras 10 and applies attenuation compression, and
[0039] - a computer network 13 providing storage and retrieval, and
[0040] - authentication means 14 for compressed video
[0041] The surveillance system 1 adopts various compression ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com