Contactless CPU card compatible to logic encryption card
A logic encryption card and non-contact technology, which is applied to record carriers used in machines, instruments, computer components, etc., can solve the problems of system transformation and transition that cannot be solved at once, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
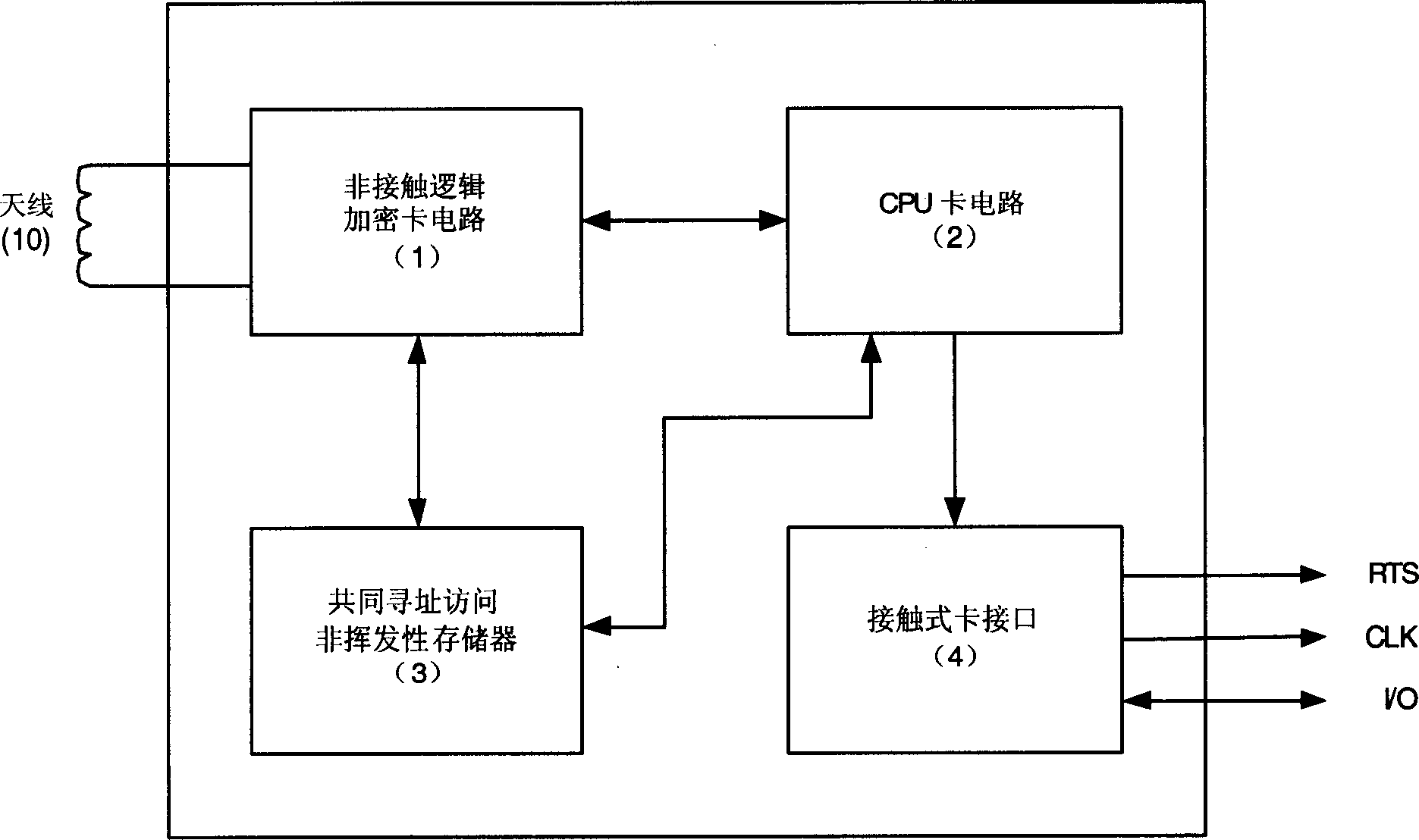
[0021] The invention provides a non-contact CPU card compatible with a logic encryption card, which comprises a non-contact logic encryption card function compatible circuit (1), a CPU card circuit (2) and a common addressing access non-volatile memory(3);
[0022] The non-contact logical encryption card function compatible circuit (1) is connected to the CPU card circuit (2) and the common addressing access non-volatile memory (3). compatible;
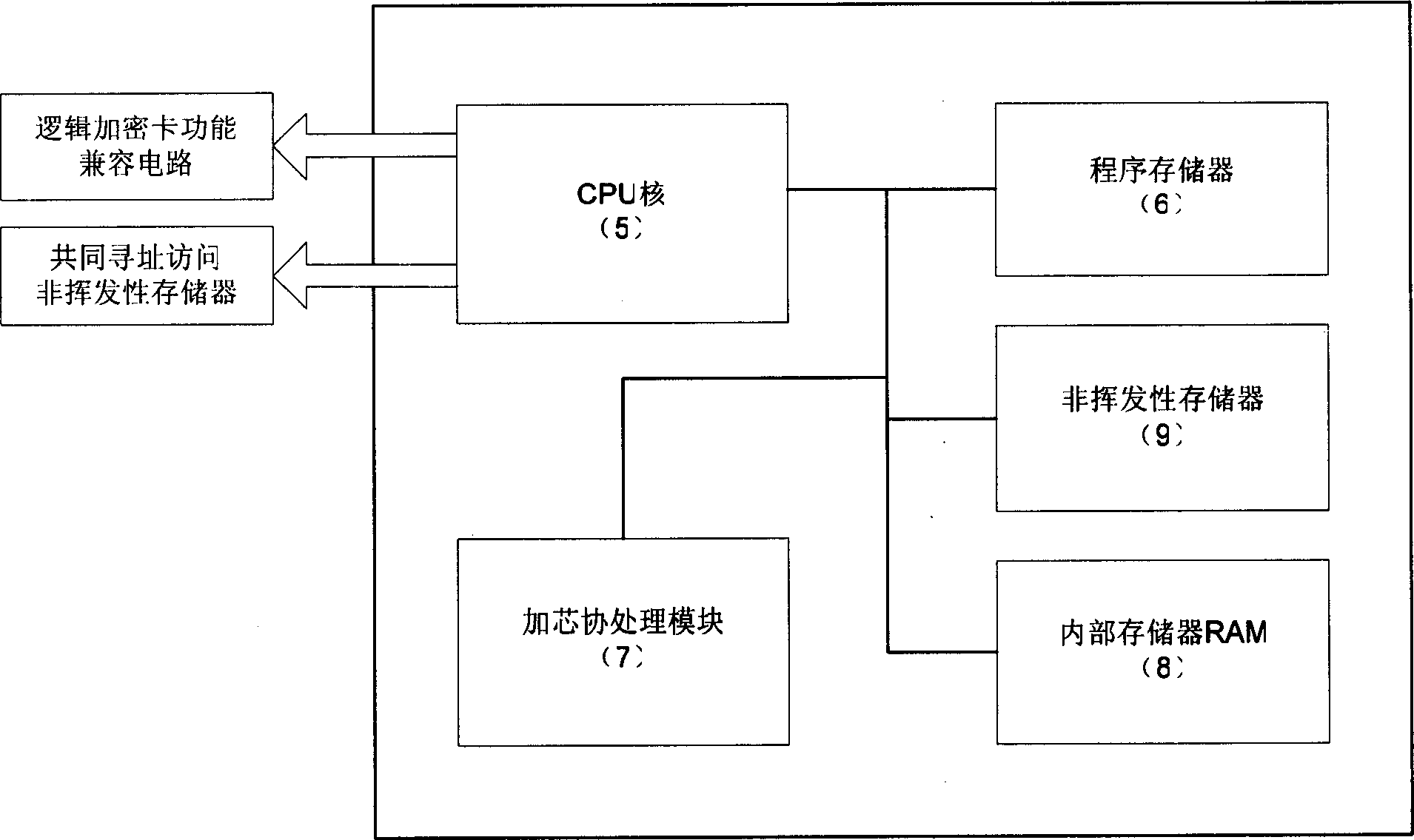
[0023] The CPU card circuit (2) is connected to a non-contact logic encryption card function compatible circuit (1) and a common addressing access non-volatile memory (3), and the circuit includes a CPU core (5) and a program memory (6) connected to each other. ), non-volatile memory (9), internal memory (8) and encryption co-processing module (7);
[0024] The circuit of the common addressing access non-volatile memory (3) is connected with the non-contact logic encryption card function compatible circuit (1) and the CPU card circu...
specific Embodiment
[0033] The key data in logical encryption card applications, for example, for a typical electronic wallet application (such as public transportation cards, wallets in campus cards), the key data is the cumulative top-up amount (or cumulative top-up value) and wallet (i.e. accumulated consumption amount), when the CPU card COS is processing, it is necessary to check whether the accumulated replenishment amount stored in the non-volatile memory (3) of common addressing access is the same as that stored in the non-volatile memory used by the CPU ( 9) Whether the value (or authentication code) in 9) matches, if not, it means that the data has been illegally changed, then the further use of the card is prohibited or a corresponding reminder is given, for the wallet data (or the accumulated consumption amount), then The value stored in the non-volatile memory (3) for common addressing access must be greater than or equal to the value stored in the non-volatile memory (9) used by the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com