Method for preventing offence between inserted users
A technology for accessing users and accessing devices, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as difficult to achieve firewalls to prevent complex attacks, fail to meet security requirements, etc., achieve low cost and prevent illegal attacks , the effect of high security requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
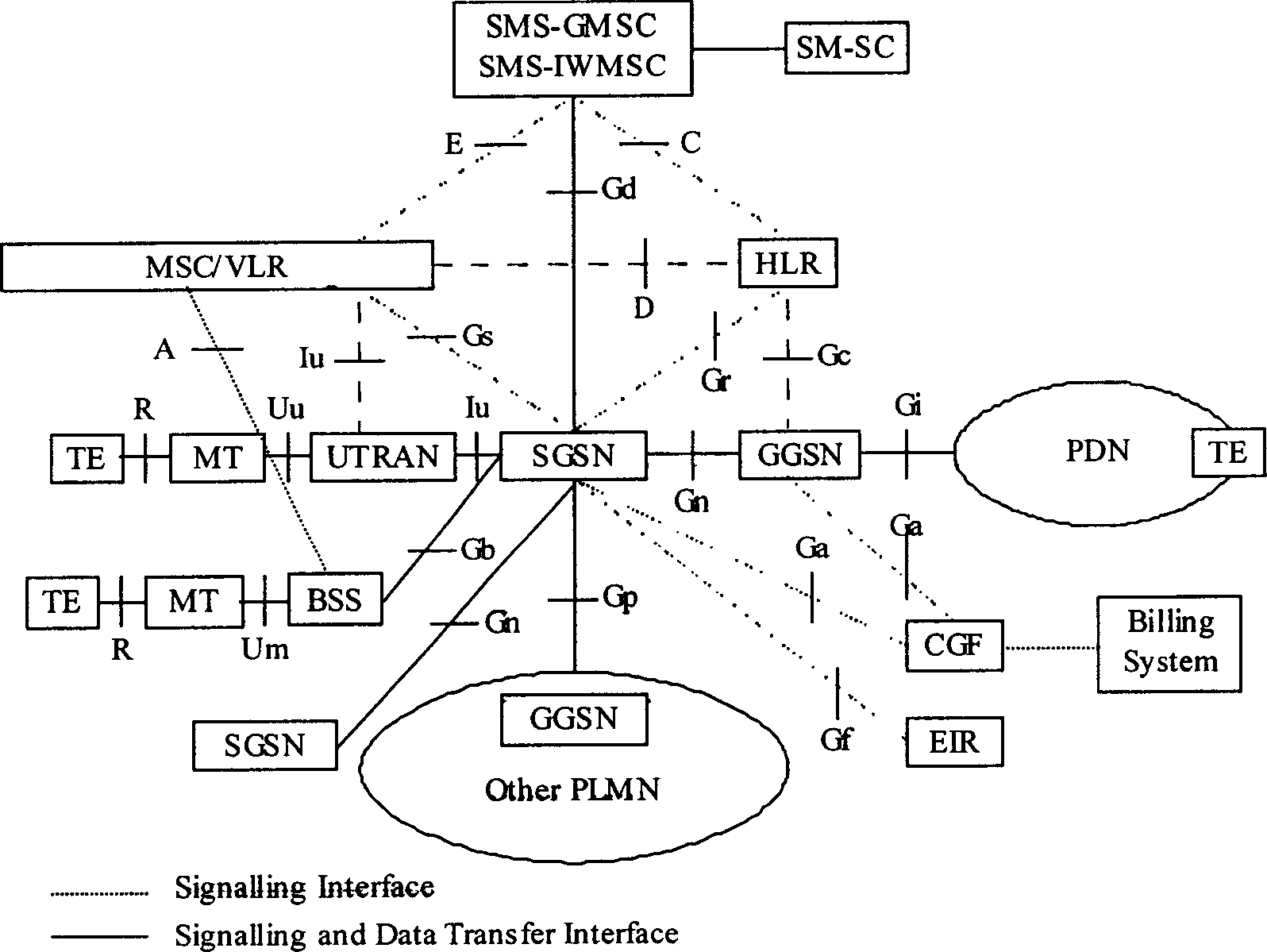
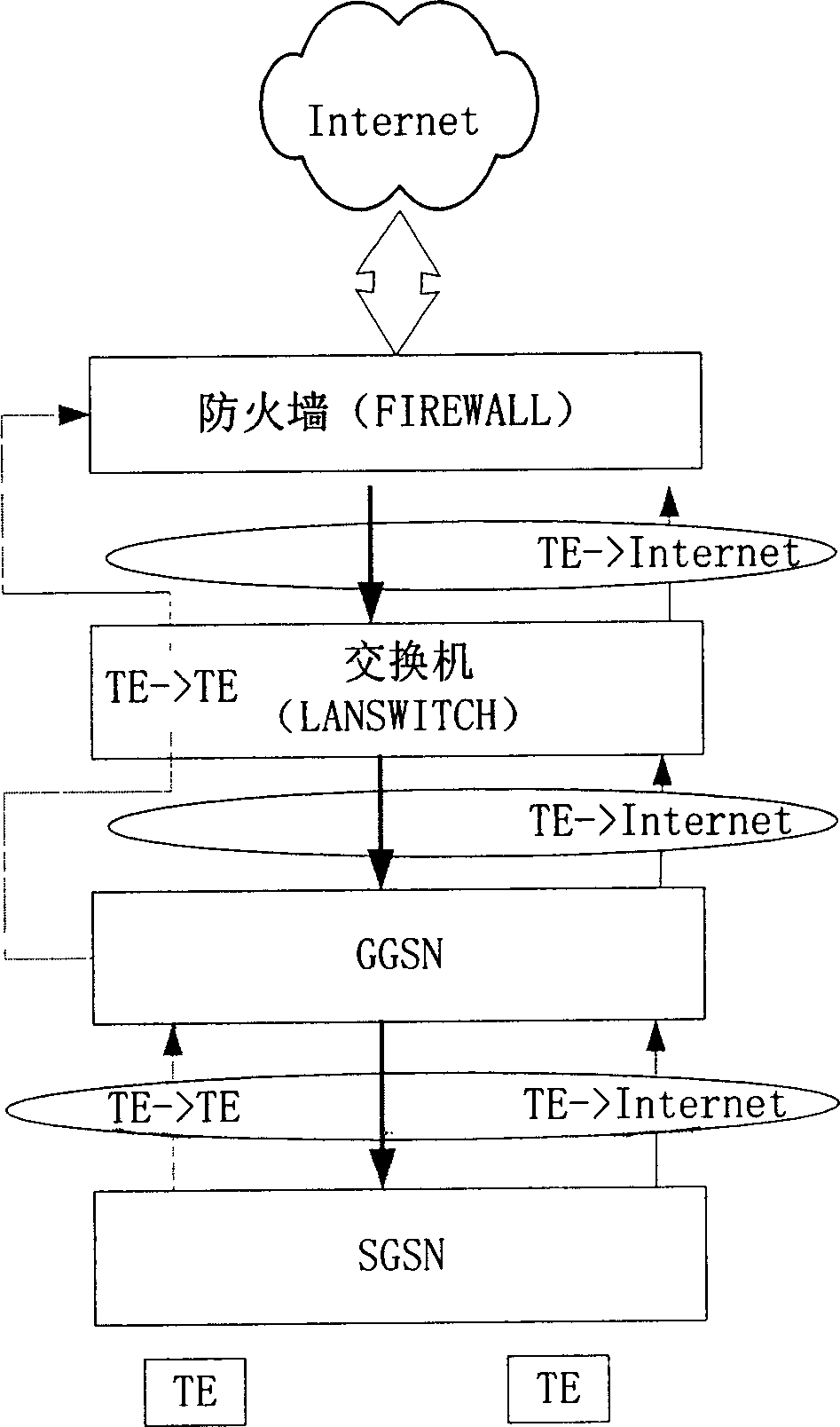
[0023] On the basis of not changing the existing network structure, the present invention realizes the detection and filtering of the data flow between the access users through the mutual cooperation of the GGSN and the firewall equipment, so as to prevent the attacks between the access users . Referring to the accompanying drawings, the method for preventing attacks between access users of the present invention will be described in detail.
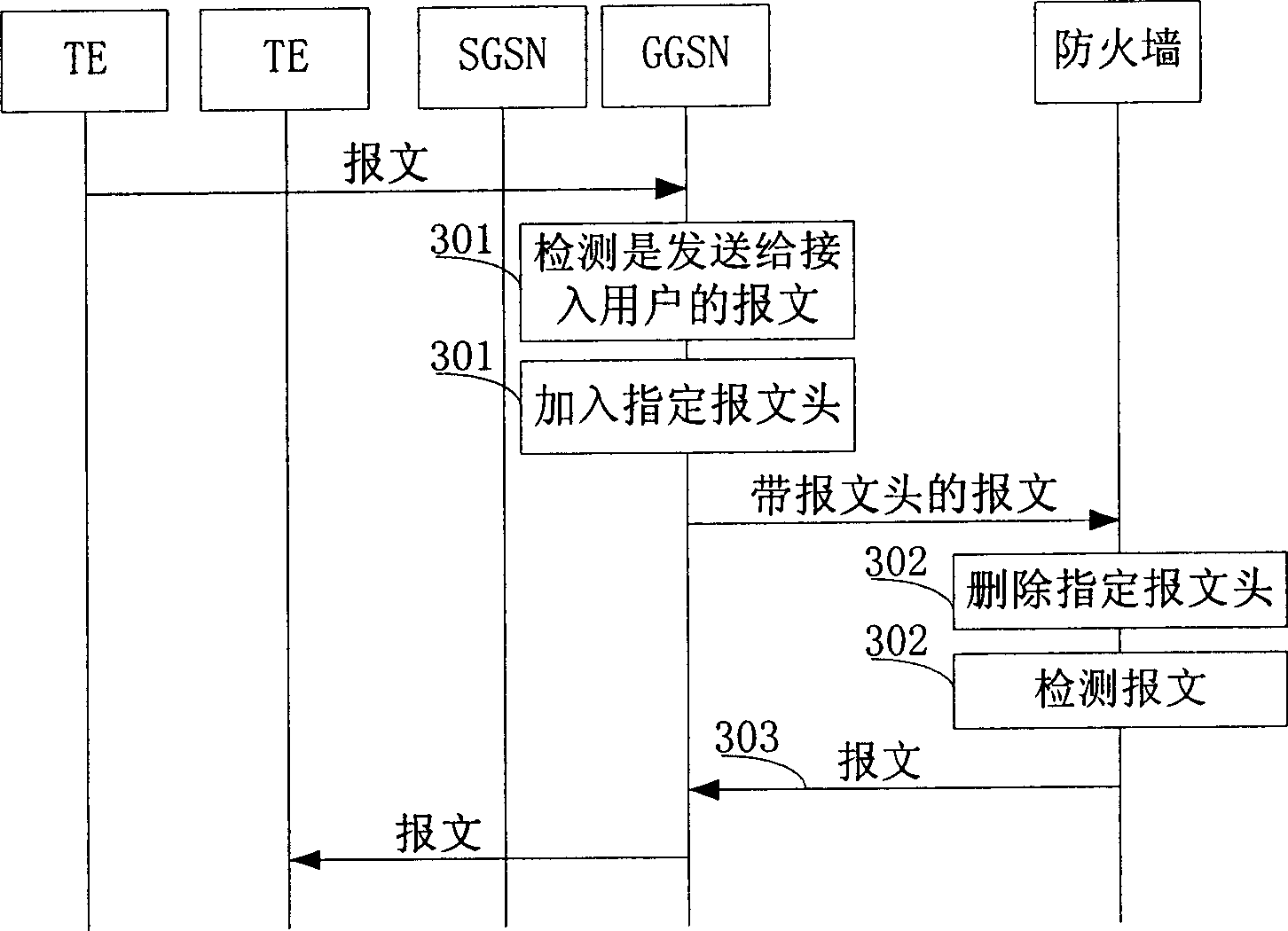
[0024] still use figure 1 In the network structure diagram shown, the firewall is still set between the GGSN and the external packet data network. Such as figure 2 and image 3 As shown, the method includes the following steps:
[0025] Step 301: The access device GGSN receives the message sent by the TE uploaded by the SGSN, and the GGSN judges whether the message is sent to another access user. The destination address of the message is judged, and when it is judged that the message is sent to another user, the specified message he...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com