Realizing method of data stream constraint control
A technology of constraint control and implementation method, applied in the field of communication, can solve the problems of defective burst flow control, low pass rate of long data packets, large storage space occupied by token buckets, etc., so as to improve the pass rate, reduce storage space, The effect of cycle shortening
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Below according to accompanying drawing and embodiment the present invention will be described in further detail:
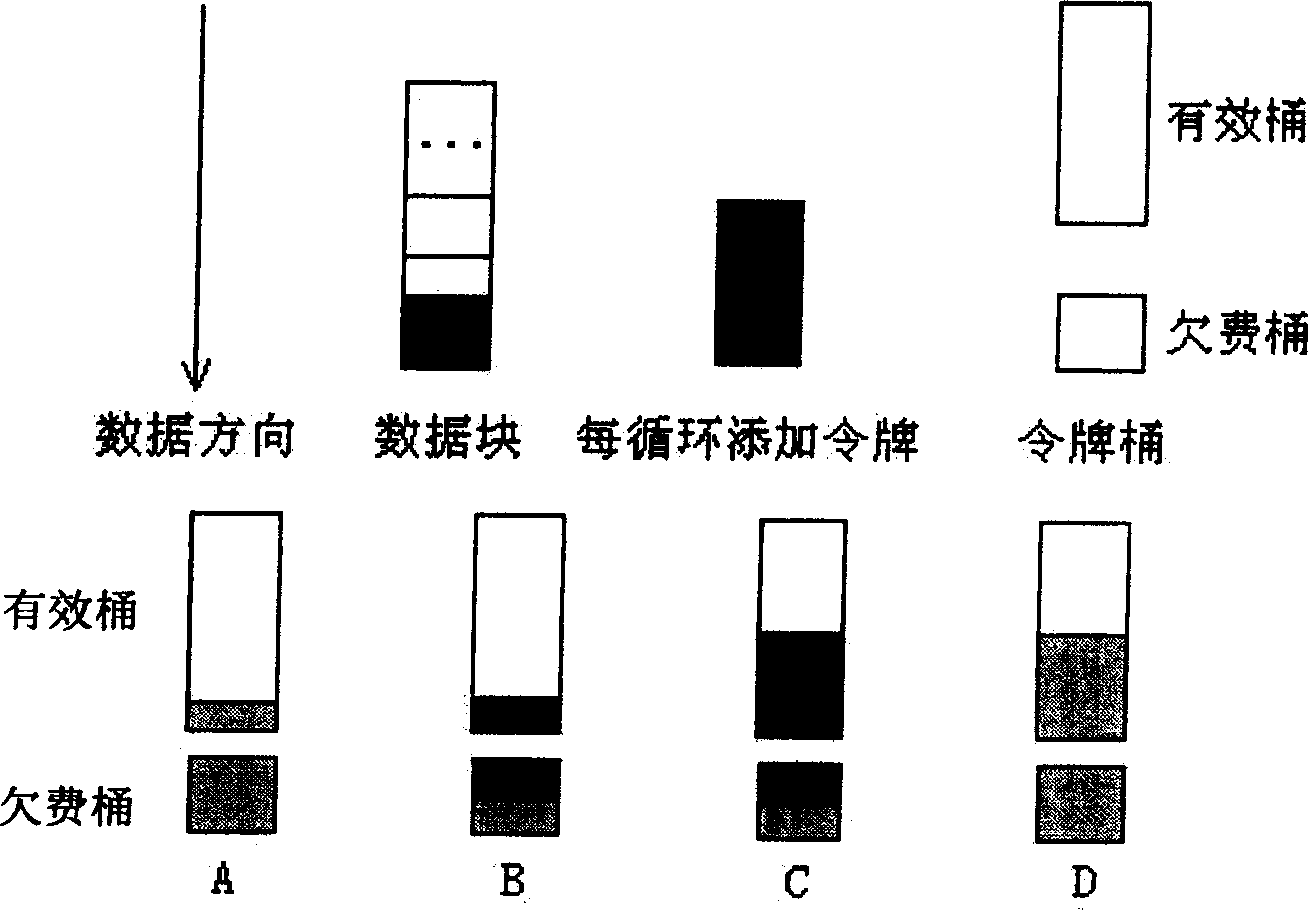
[0027] The present invention provides a method for implementing data flow constraint control, constructing a token bucket, including token bucket depth parameters and bandwidth parameters, and the token bucket depth is a fixed token bucket depth value plus a dynamic token bucket depth value , the fixed token bucket depth is below the dynamic token bucket depth. According to the traffic allocated to the user, the corresponding number of tokens is periodically added to the token bucket, and at the same time, the token is subtracted from the token bucket according to the actual traffic of the user. When the number is less than the fixed token bucket depth value, the traffic is illegal; when adding tokens next time, the fixed token bucket depth value must be filled up first, and then user traffic can pass. The dynamic token bucket depth value can be 2 times t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com