Active decoy method and system
An active and subsystem technology, applied in the field of network security, can solve the problems of active deception, self-updating attack detection rules, incapable of real-time detection of hacker attacks, etc., to achieve the effect of improving defense capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
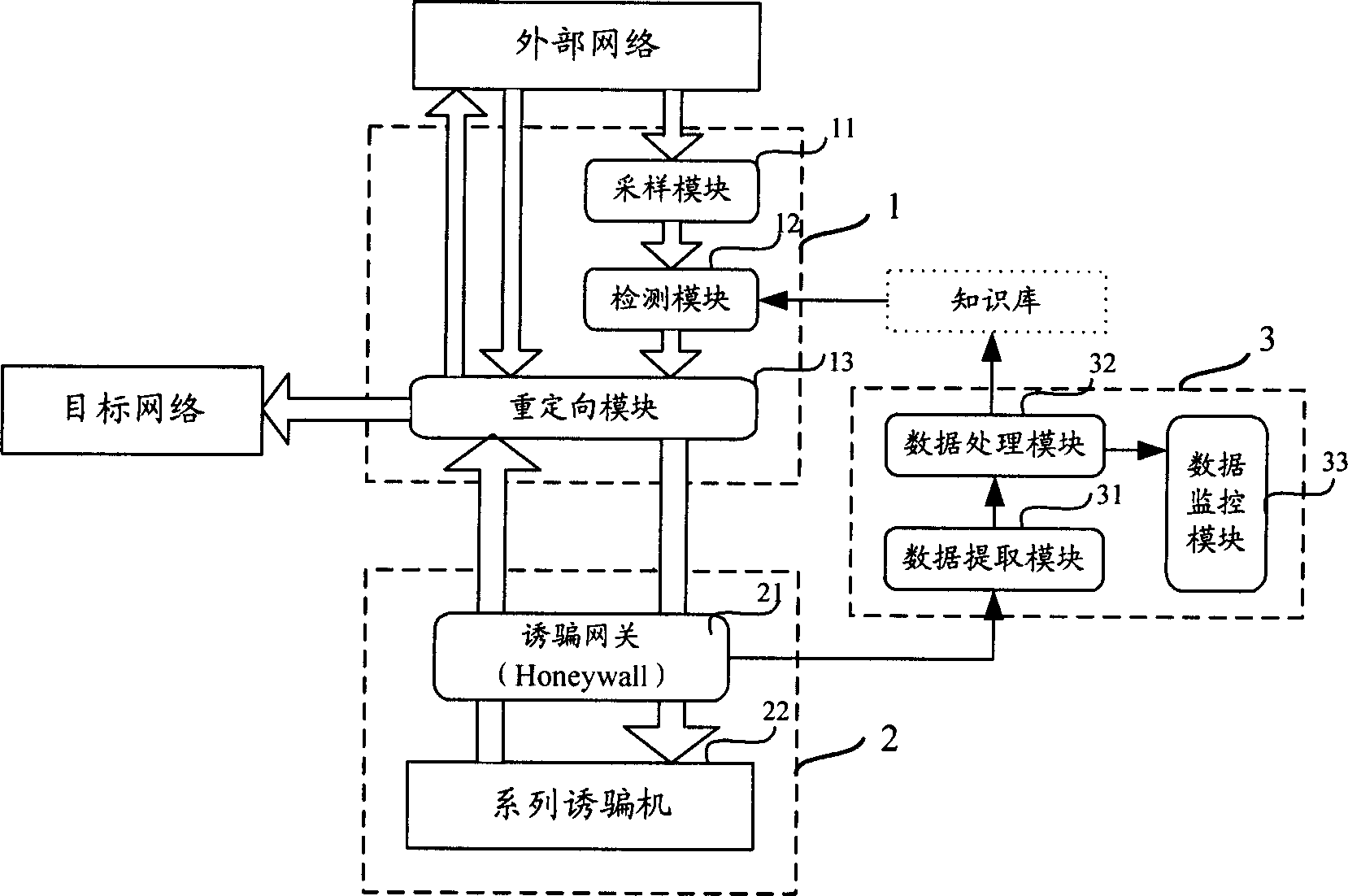
[0052] see image 3 , is a schematic diagram of the structural modules of the decoy system of the present invention, including: a detection and diversion subsystem 1 , a decoy network 2 and a data analysis subsystem 3 .
[0053] Among them, the detection and diversion subsystem 1 samples the data flow sent to the target network, and matches the sampled data with the characteristic information of hacking behavior stored in the detection module (the characteristic information of hacking behavior can be stored separately in a knowledge base) , redirect the suspicious / abnormal data flow to the decoy network 2 according to the matching result, and redirect the normal data flow to the target network;
[0054] Decoy network 2 is separated from the target network, simulates the target network to process suspicious / abnormal data, and captures hacker attack behavior data in the decoy network and sends it to the data analysis subsystem 3;
[0055] The data analysis subsystem 3 analyzes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com