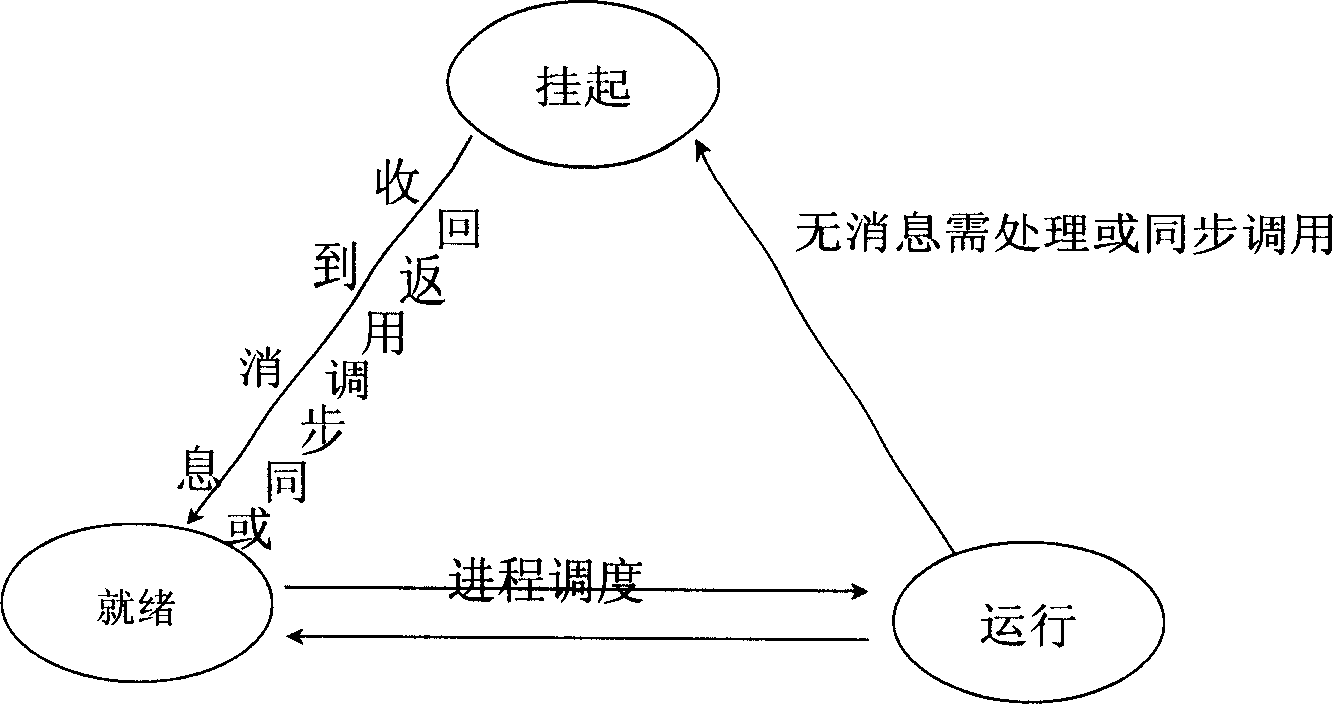
Method for leaking memory of positioning virtual operation system
A virtual operating system and memory leak technology, applied in the field of locating memory leaks in virtual operating systems, can solve problems such as insufficient memory, no unified structure, and difficult analysis, and achieve the effects of easy memory leak location, small impact, and simple data structure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
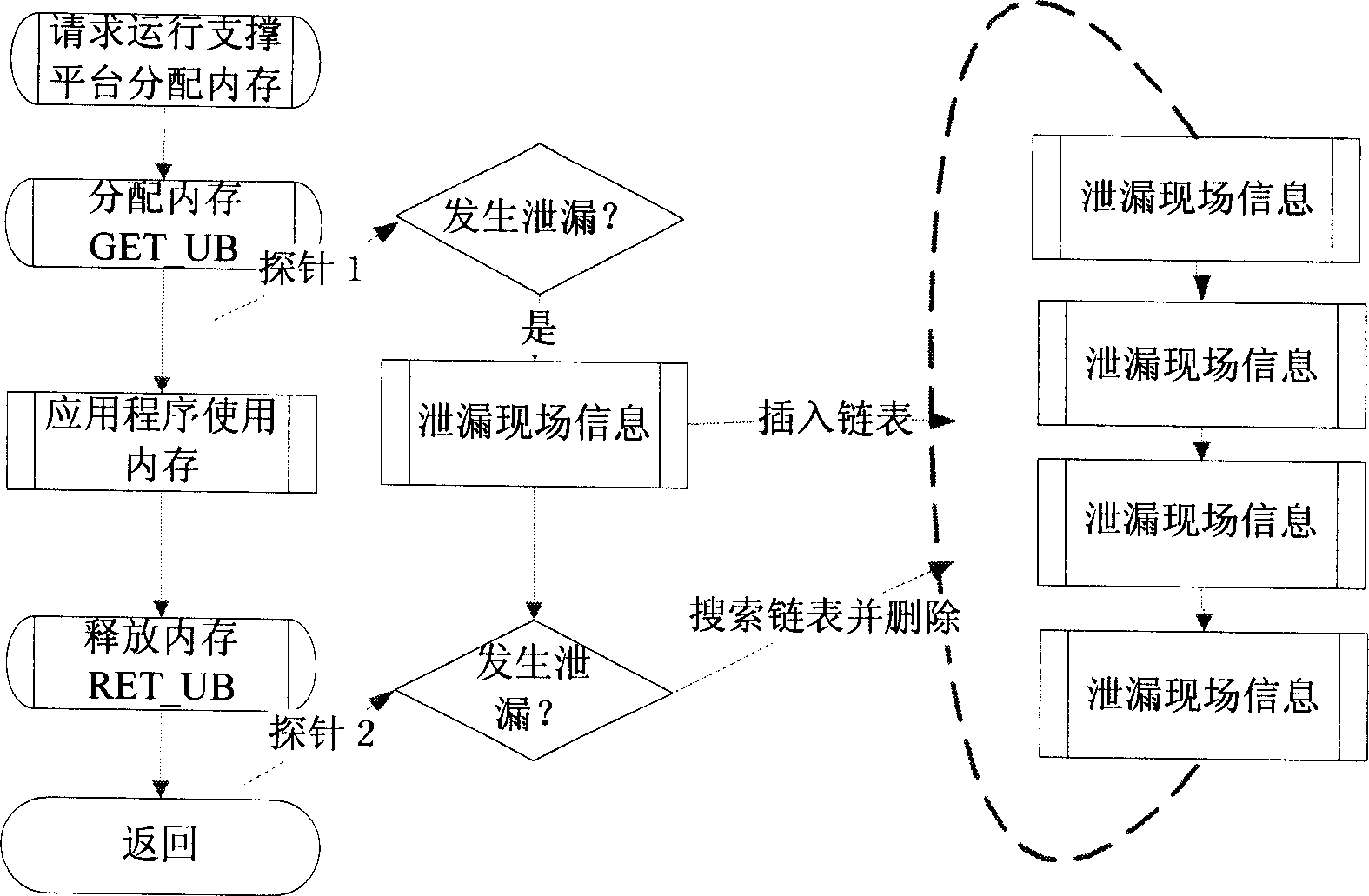
[0025] Combine below image 3 The implementation of the present invention is described in detail:
[0026] 1. First, you need to set the criteria for judging memory leaks and the threshold for recording files to the hard disk. If the available memory is less than 30%, it is considered that a memory leak has occurred. When the available memory is less than 10%, start saving the linked list to the hard disk.
[0027] 2. Construct a structure UBLEAK_REG to save the system running status of the leak point. The structure ( image 3 A box on the right represents a structure) The system running state information saved at least includes the following content, mainly the PCB content of the scheduled process at the leak point:
[0028] The line number where the memory allocation function (GET_UB) was called
[0029] The name of the file that calls the free memory function (GET_UB)
[0030] The address of the memory block (UB)
[0031] current task number
[0032] current process ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com