Multidimension object access control method based on roles
A technology of object access and control methods, applied in the field of computer database security solutions, can solve the problems of undefined organic connections, expansion of the number of connections, failure to reflect the software system structure, etc., and achieve the effect of reducing authorization workload and facilitating security management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
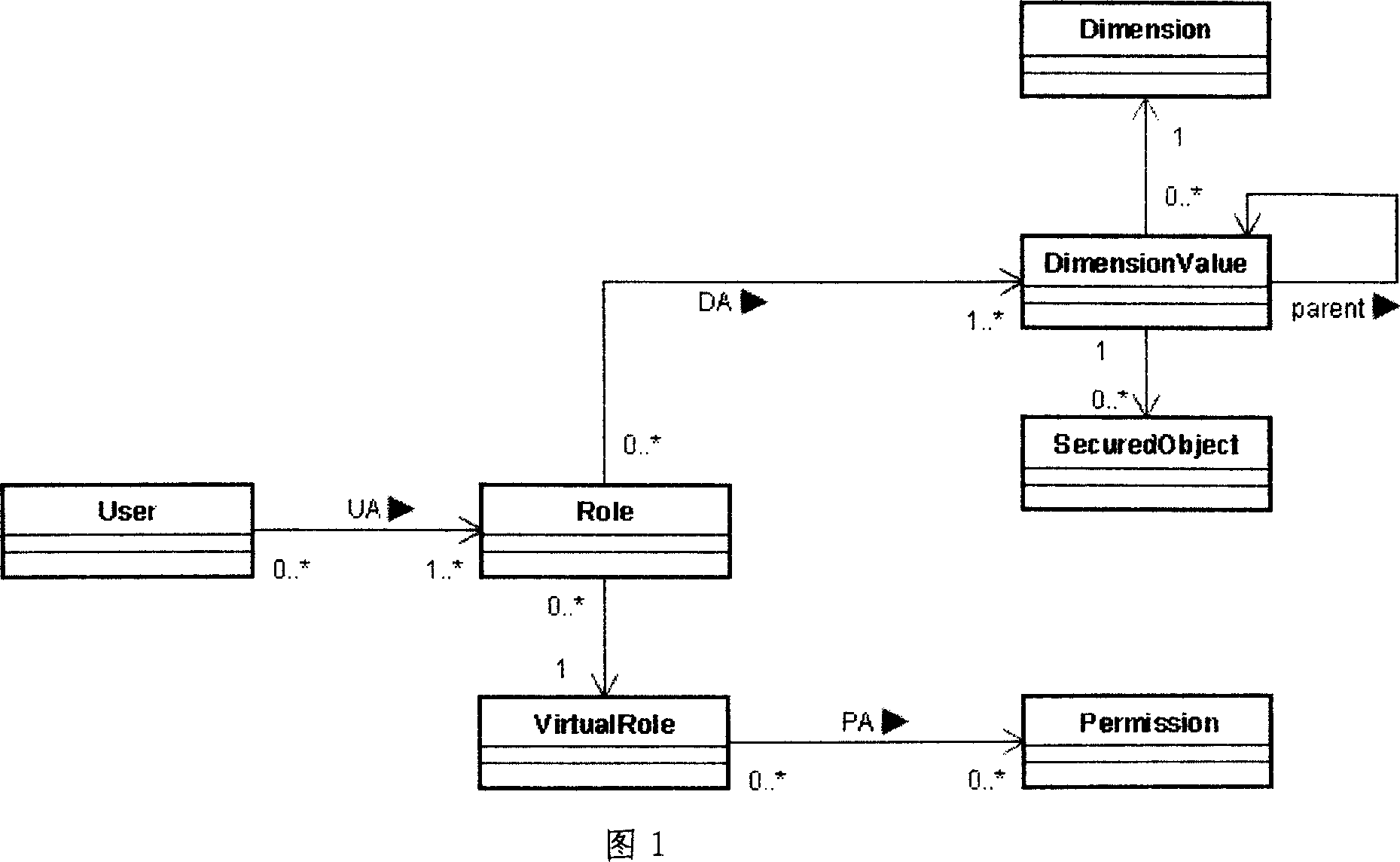
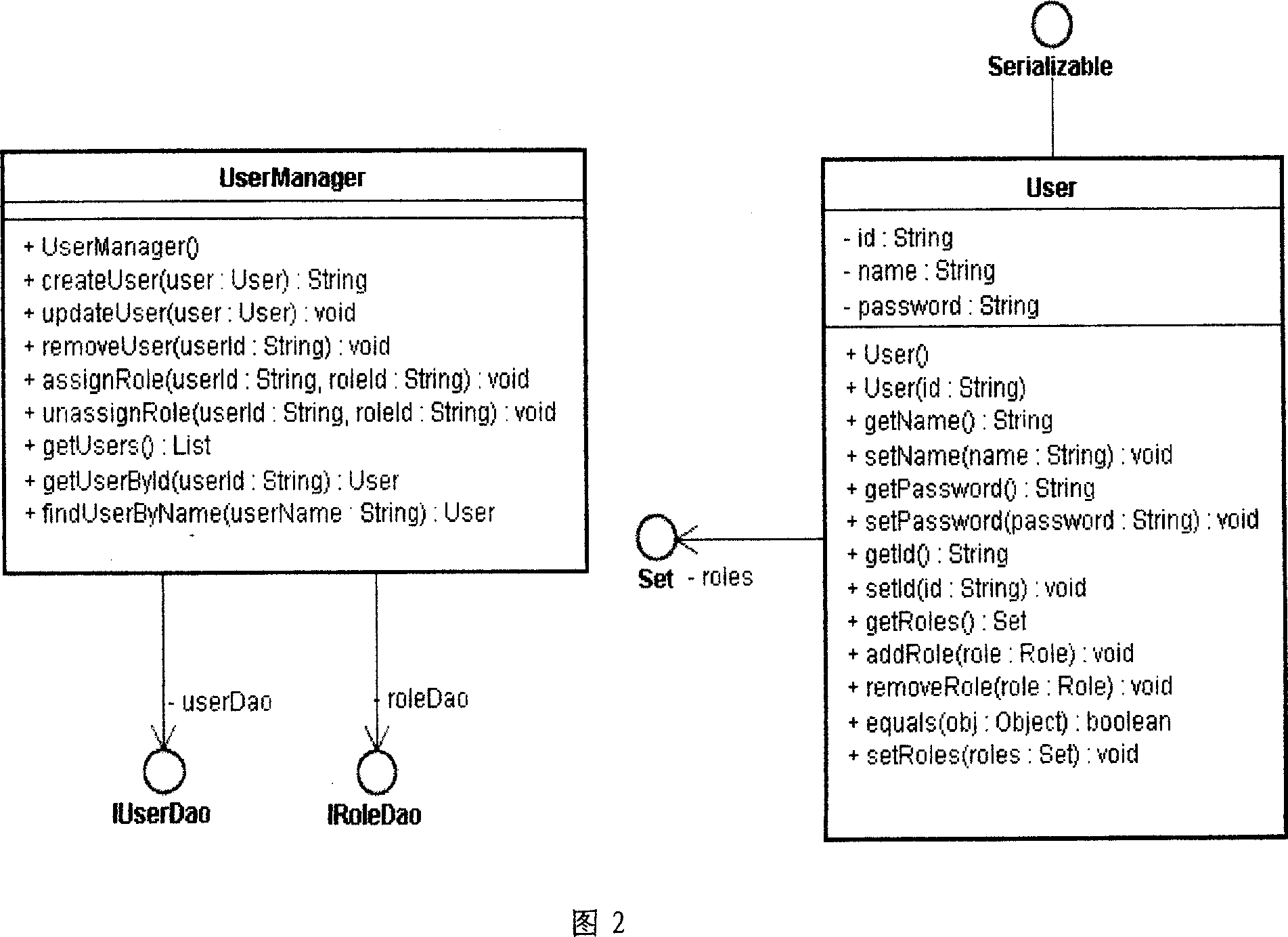
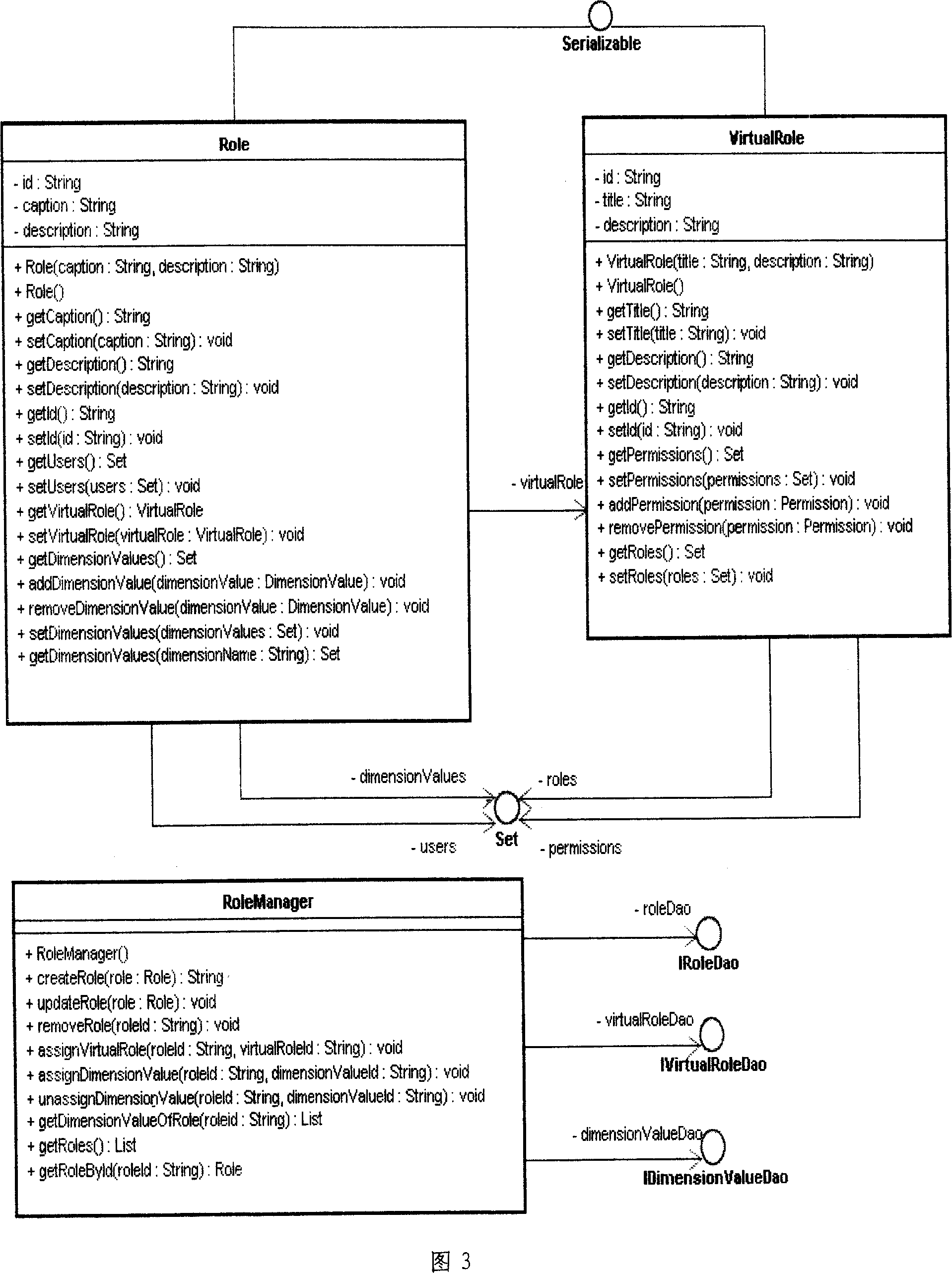
[0037] 1 Implementation background: Assume that there is an existing switch monitoring system to manage each program-controlled switch (SWITCH) in the telecommunication network. System maintenance personnel can complete the following operations:
[0038] 1. Switch status query (SWITCH.READ)
[0039] 2. Switch start and stop (SWITCH.OPER)
[0040] It is stipulated that only the administrator (ADMIN) can perform query and start-stop operations, while ordinary maintenance personnel (ATTENDANT) can only query the status of the switch. During the construction of the project, a total of 4 switches need to be monitored and managed: SWITCH1, SWITCH2, SWITCH3, SWITCH4. According to the division of regions, the system will be maintained by Jiangsu Branch (JIANGSU), Nanjing Branch (NANJING) and Suzhou Branch (SUZHOU) at the same time. Among them, SWITCH1 and SWITCH2 are maintained by Nanjing Branch, SWITCH3 and SWITCH4 are maintained by Suzhou Branch, and the provincial company can ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com