Method for authorizing approval process and approval node thereof for user
A technology of approval nodes and users, applied in data processing applications, special data processing applications, digital data protection, etc., can solve problems such as difficulty in distinguishing the specific differences in the permissions of each role, cumbersome authorization, and cumbersome and troublesome user operations. Achieve the effect of rapid approval process authorization, reduce authorization error rate, and reduce authorization workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
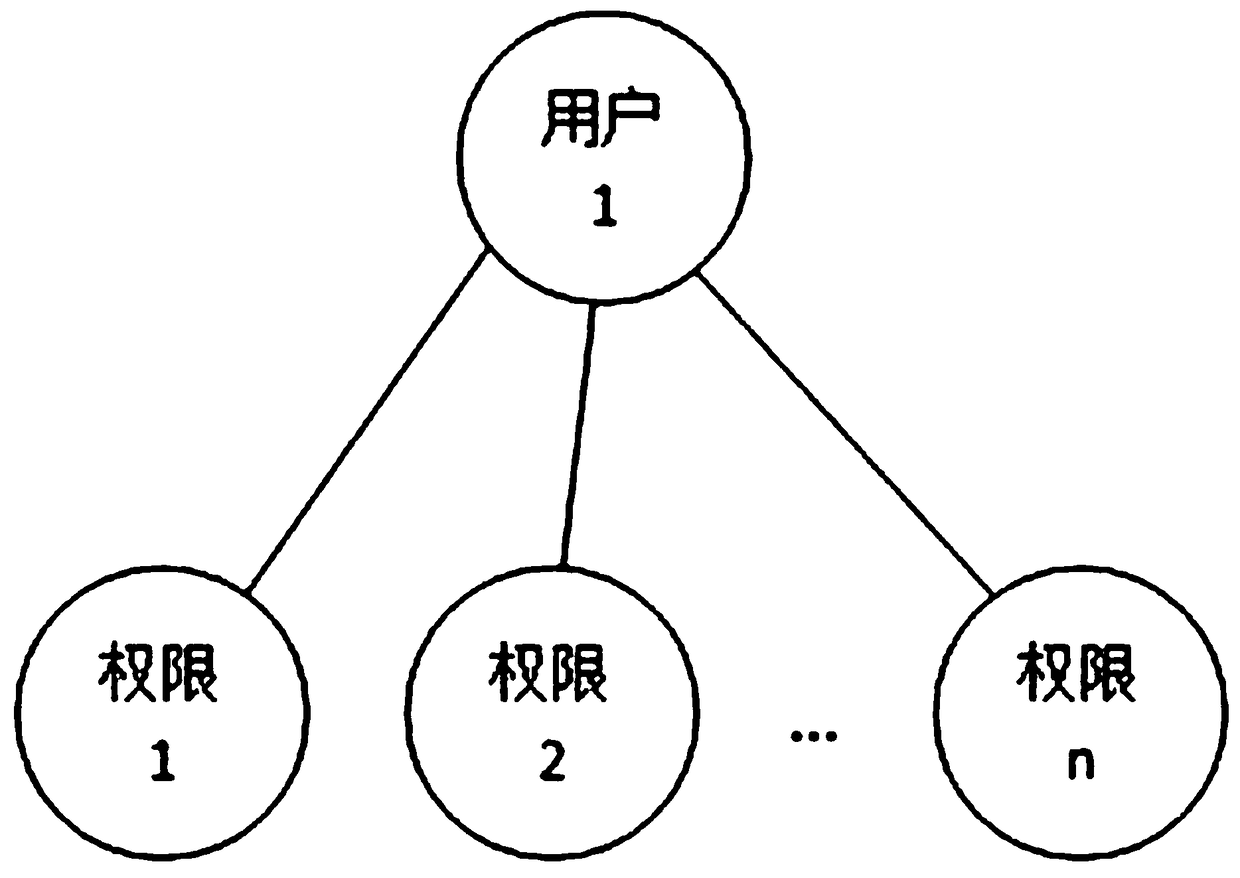
[0052] [Example 1] If Figure 4 As shown, the method for authorizing the user in the approval process includes: S11. Select a user in the system.
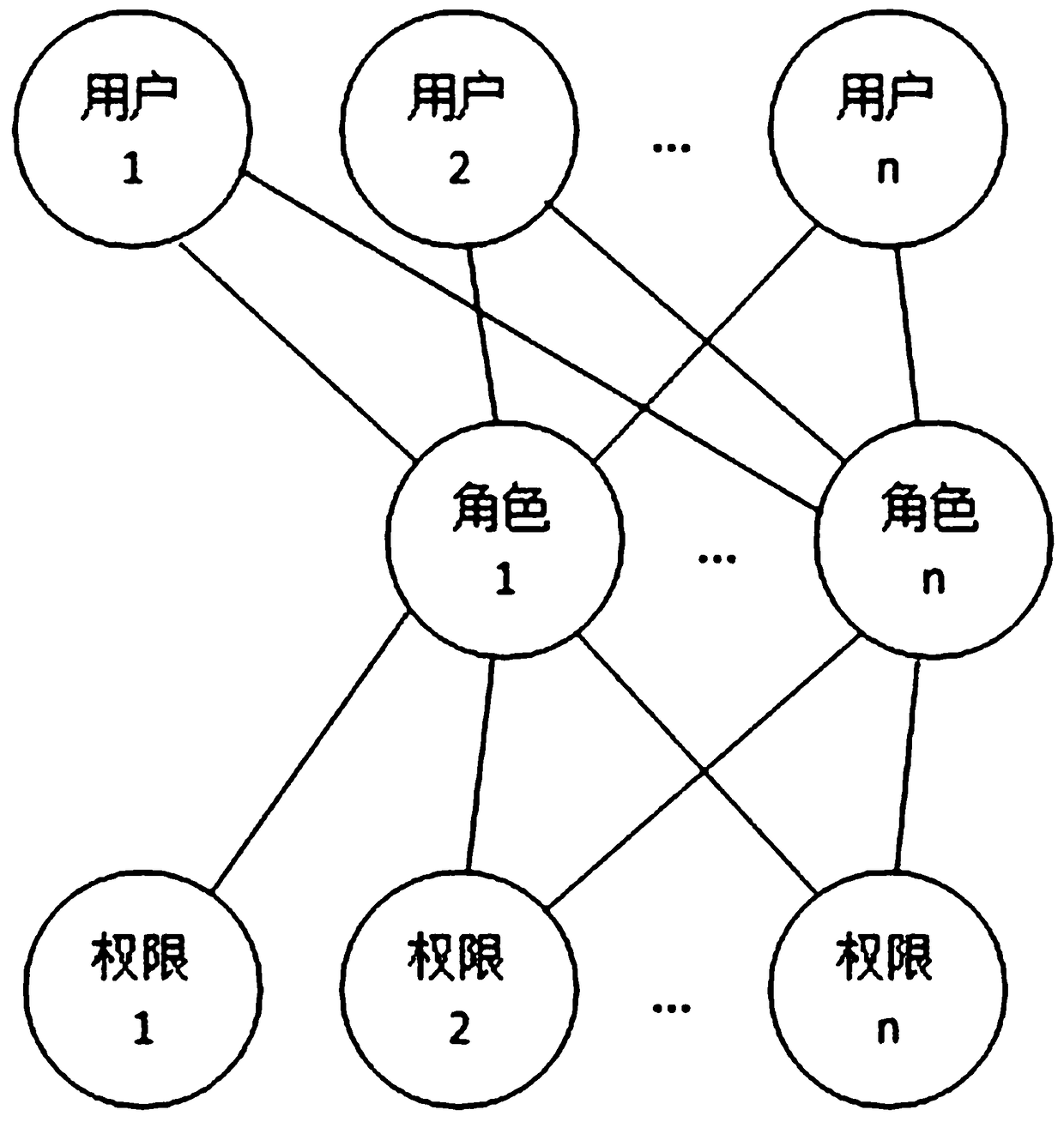
[0053] E.g, Figure 5 Role 1 is selected as the user in .
[0054] The users include one or more of roles, users, employees and groups / classes.
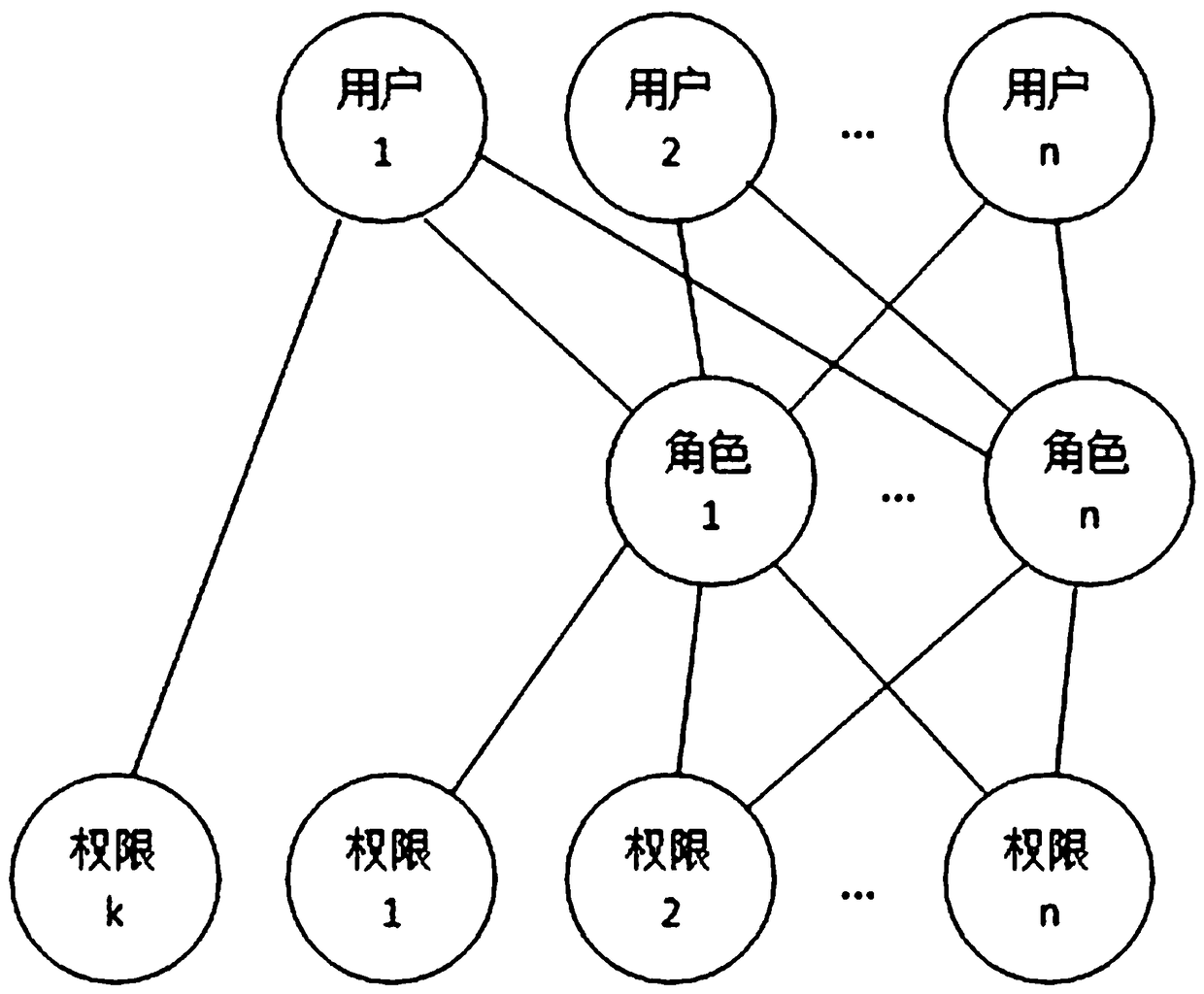
[0055] Such as Image 6 As shown, the role is an independent individual, not a group / class. A role can only be associated with a unique user at the same time, and a user is associated with one or more roles; users obtain the permissions of their associated roles. Select a department for the role when the role is created or after the role is created, the role belongs to the department, and the role is authorized according to the work content of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com