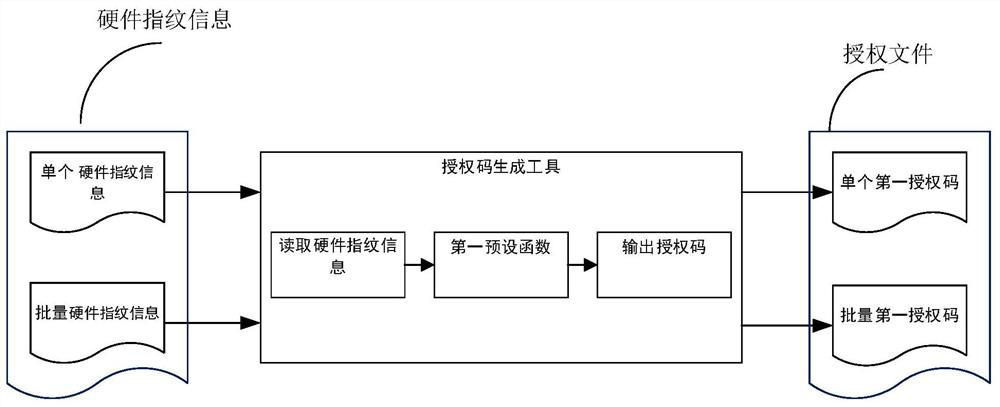
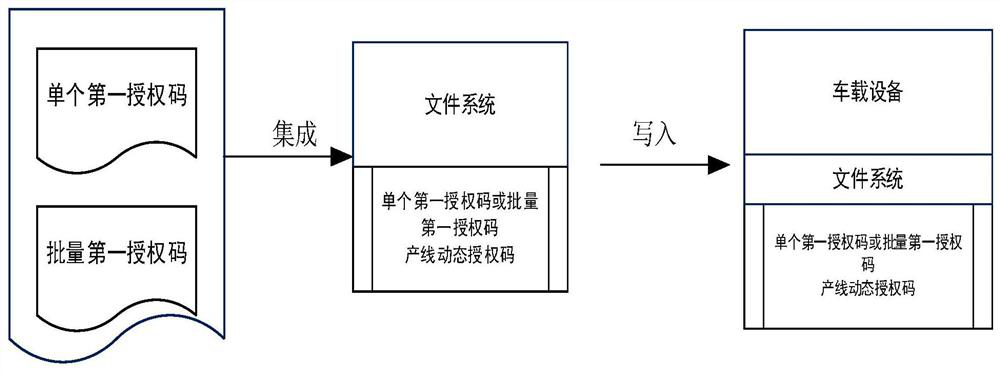
Countable software authorization method for vehicle-mounted system
A technology of software authorization and vehicle-mounted system, which is applied in the vehicle-mounted field, can solve the problems of inconvenient statistics and abnormal use of machines, and achieve the effects of ensuring safety, simple authorization, and avoiding cumbersomeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to have a clearer understanding of the technical features, purposes and effects of this document, the specific implementation manners of the present invention will now be described with reference to the accompanying drawings, and the same symbols in each figure represent the same parts. In order to make the drawings concise, the schematic diagrams in the drawings show the relevant parts of the present invention, but do not represent the actual structure of the product. In addition, in order to make the drawings concise and easy to understand, in some drawings, only one of the components having the same structure or function is schematically shown, or only one of them is marked.
[0039] As for the control system, functional modules and application programs (APP) are well known to those skilled in the art, they can take any appropriate form, either hardware or software, multiple functional modules discretely set, or It is multiple functional units integrated int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com