Patents
Literature
30results about How to "Convenient authorization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
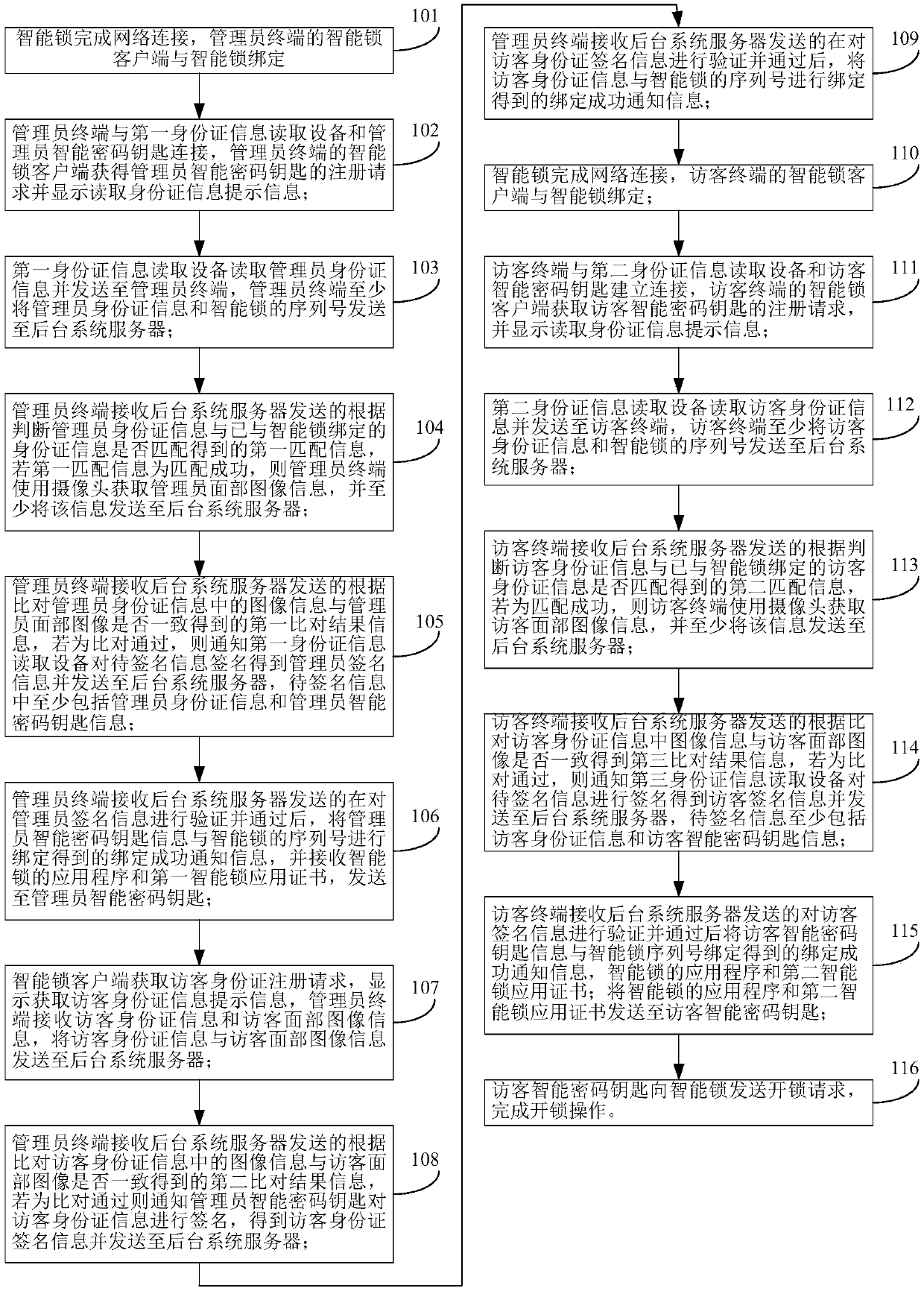
Intelligent terminal application program installing file networking digital signature method
ActiveCN103036894ARisk of preventing signing and passing signature authenticationSolve the legality checkUser identity/authority verificationSignature fileSource Data Verification
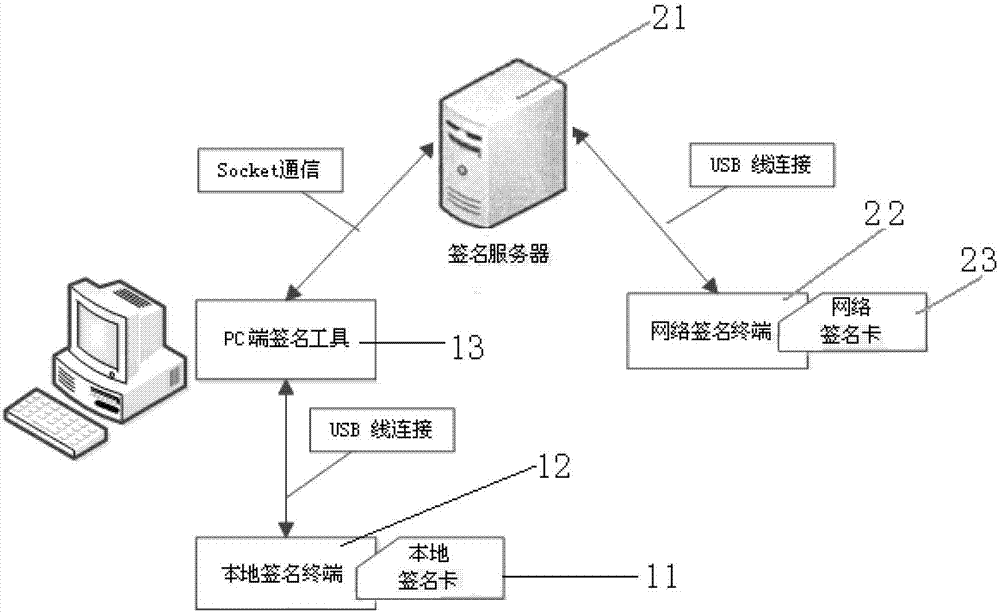
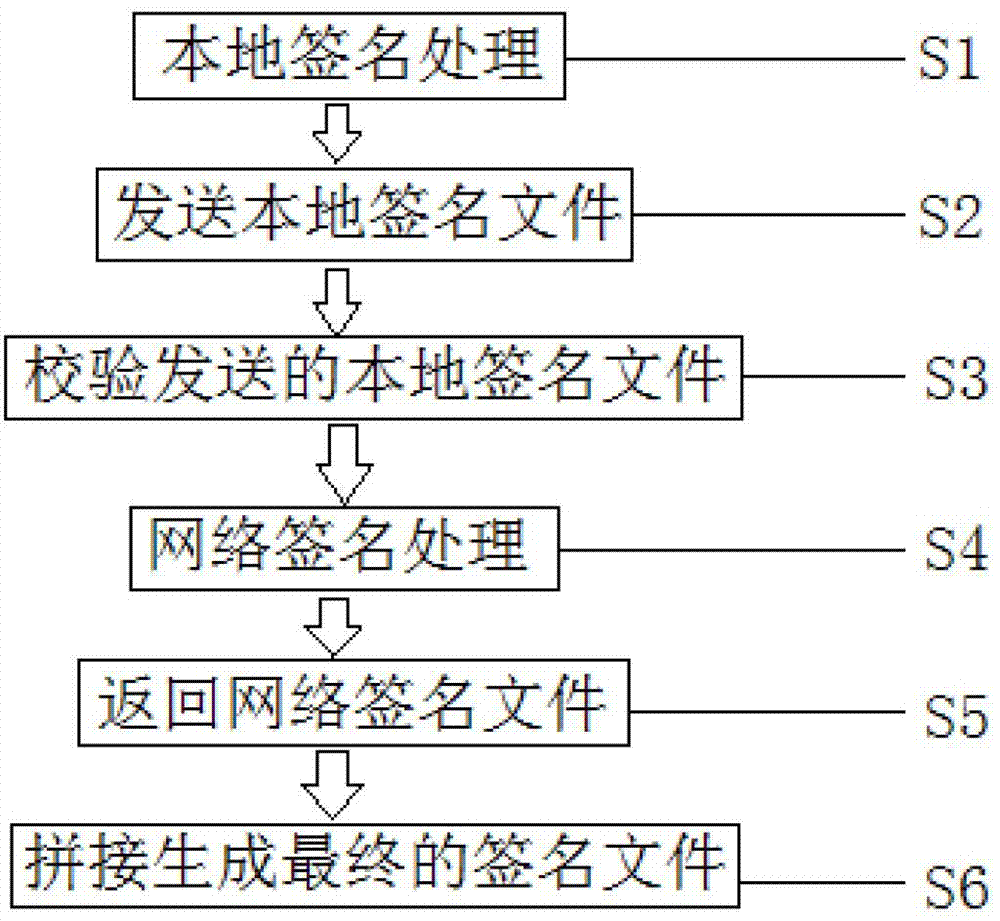
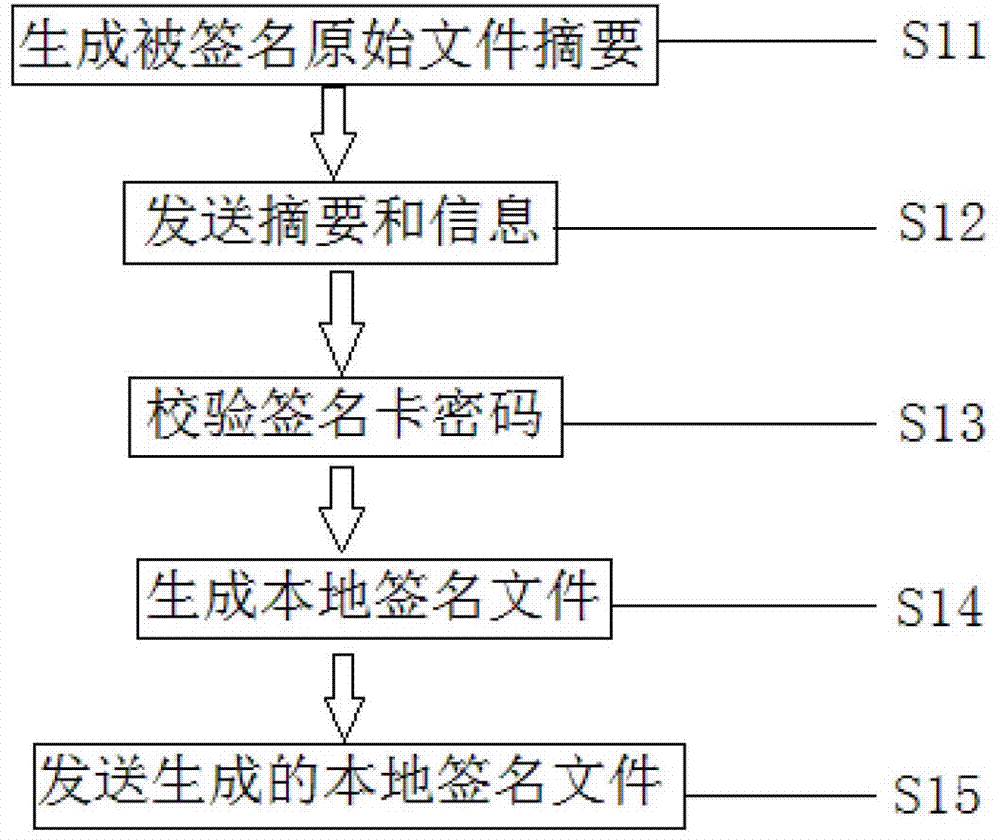
The invention relates to an intelligent terminal application program installing file networking digital signature method. A developer uses a local signature card to sign a to-be-signed source file to generate a local signature file with a local end signature tool. The local signature file is sent to a signature server. After the local signature file passes data verification of the signature server, the local signature file is sent to a network signature terminal, a network signature card of a manufacturer is used for signature, a network signature file is generated and is sent back to the signature server, and network signature file is sent to the local end signature tool to generate a final signature file. Private key data is stored in the signature card and cannot be read, a private key of the signature card can be used for signature only after code verification is passed, the storing and using safety of the private key is improved, a signature server end verifies local signature data accuracy, local certificate validity, developer identity legality, and the manufacturer can authorize and control signature authority limit.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
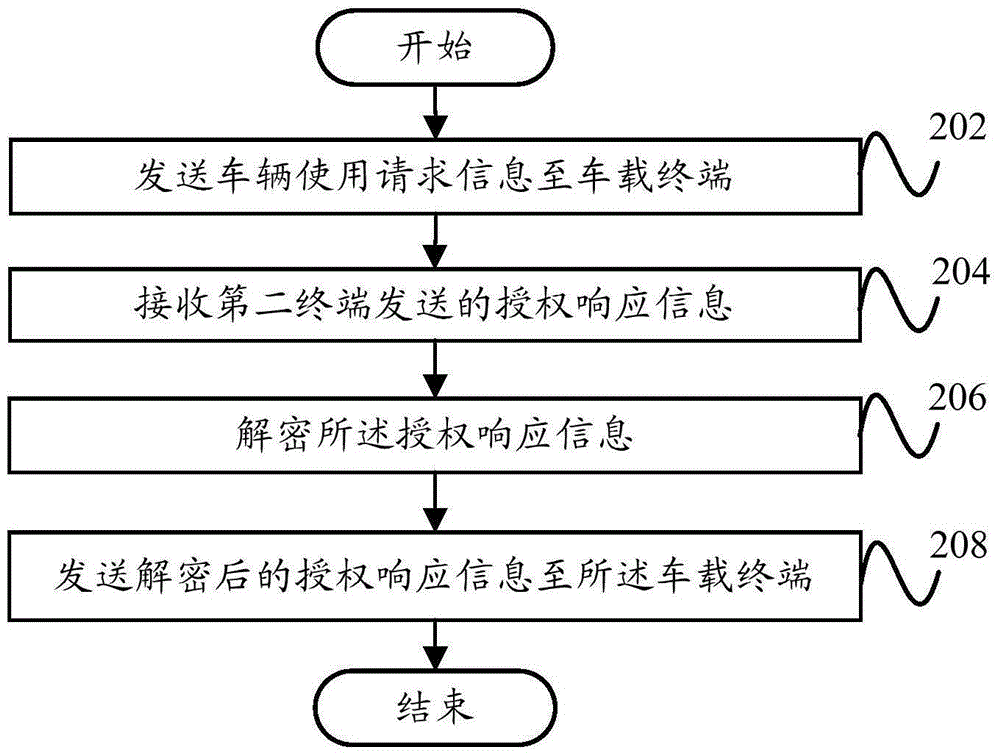
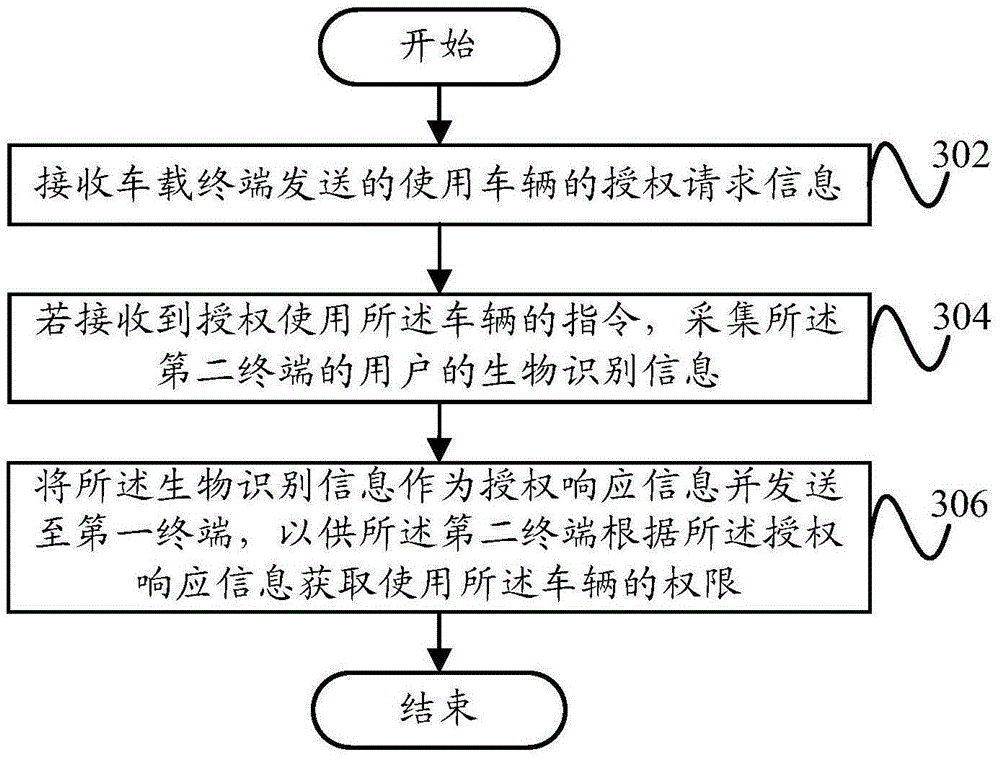
Vehicle authorization method, device, vehicle-mounted terminal, terminal and system
InactiveCN105187442AImprove experienceConvenient authorizationTransmissionAuthorizationEmbedded system
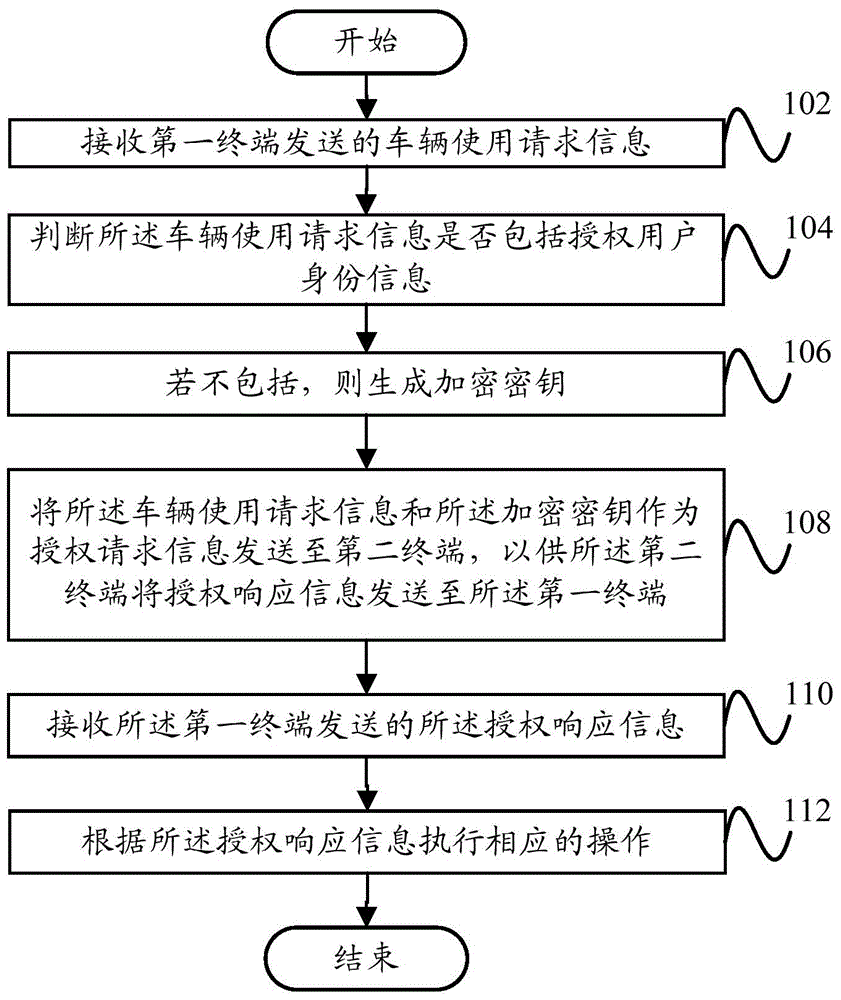
The present invention proposes a vehicle authorization method, a vehicle authorization device, a vehicle-mounted terminal, a terminal and a vehicle authorization system. The vehicle authorization method comprises the following steps: receiving vehicle use request information sent by a first terminal; judging whether the vehicle use request information comprises authorization user identity information or not; if no, generating an encryption key; using the vehicle use request information and the encryption key as authorization request information and sending the authorization request information to a second terminal, so that the second terminal sends authorization response information to the first terminal; receiving the authorization response information sent by the first terminal; and performing a corresponding operation according to the authorization response information. Through the adoption of the technical solution of the present invention, an unauthorized terminal can be conveniently and rapidly authorized to use the vehicle, thereby promoting the user experience.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
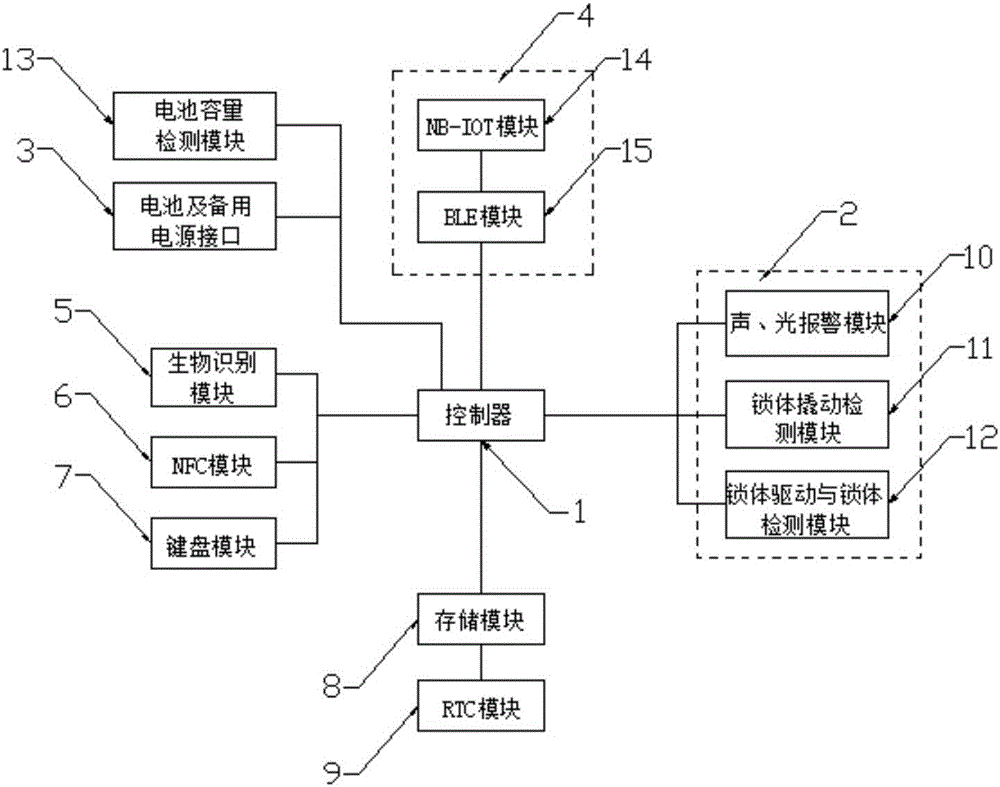
Low-cost NB-IOT (Narrow Band Internet of Things) wireless intelligent lock
InactiveCN106548556ALow costReduce power consumptionIndividual entry/exit registersElectrical batteryComputer module
The invention discloses a low-cost NB-IOT (Narrow Band Internet of Things) wireless intelligent lock, which comprises a controller, a safety lock, a battery and a communication module, wherein the controller is electrically connected with a biological recognition module, an NFC (Near Field Communication) module, a keyboard module and a storage module; the safety lock comprises a sound and light warning device, a lock body picking detection module and a lock body driving and lock body detection module; the battery is electrically connected with the battery volume detection module; the battery is electrically connected with the controller, the safety lock and the communication module; the communication module also comprises an NB-IOT module and a BLE module. By using the NB-IOT technology, the low-cost NB-IOT wireless intelligent lock has the characteristics that the power consumption is low; the signal coverage range is wide. The BLE module realizes the Bluetooth low energy consumption, so that the electric power is further saved; on one hand, the problem of short service life of the battery power supply equipment such as the intelligent lock is solved; on the other hand, the condition that a gateway needs to be additionally arranged for intelligent lock communication conversion is avoided. The device has the advantages of multifunction, low cost, energy conservation and environment protection.
Owner:INNO ELECTRIC INC
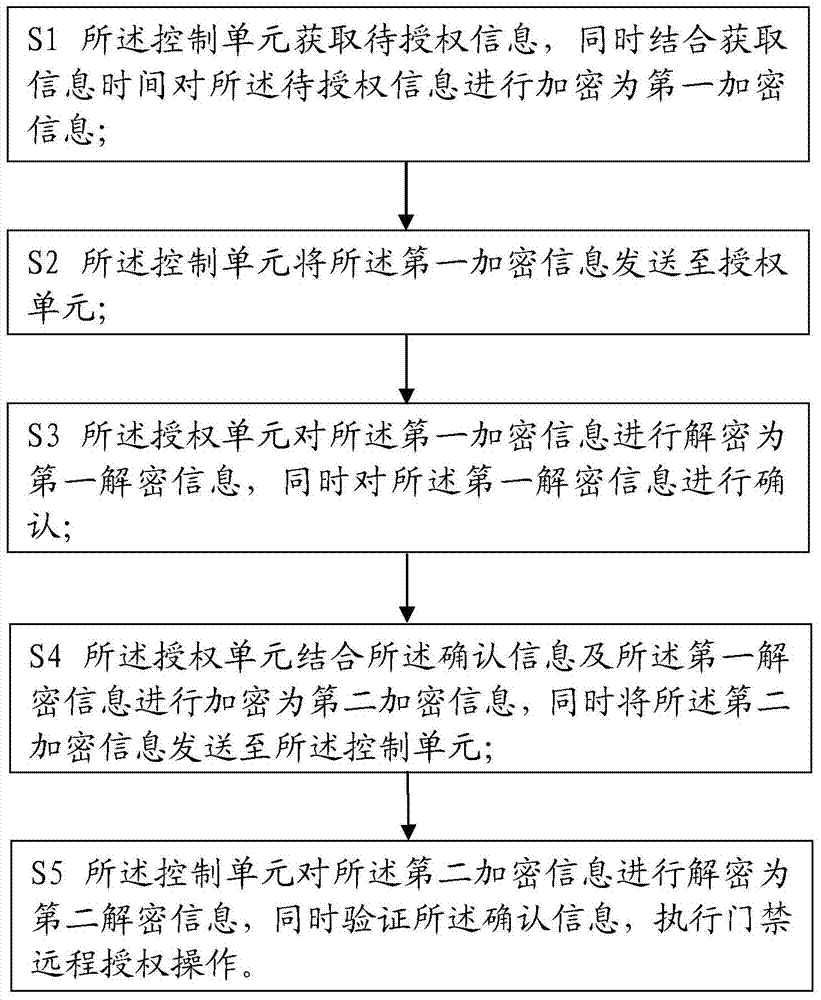
Access control remote authorization method
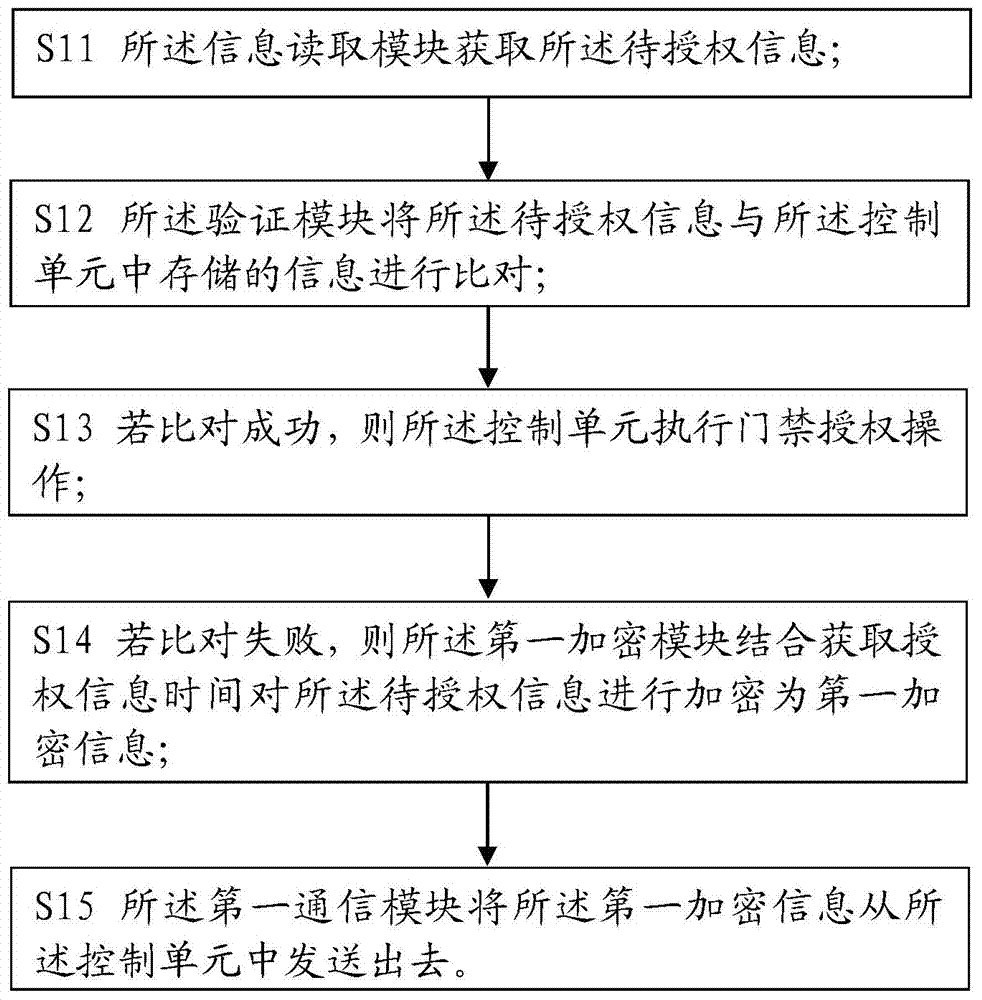
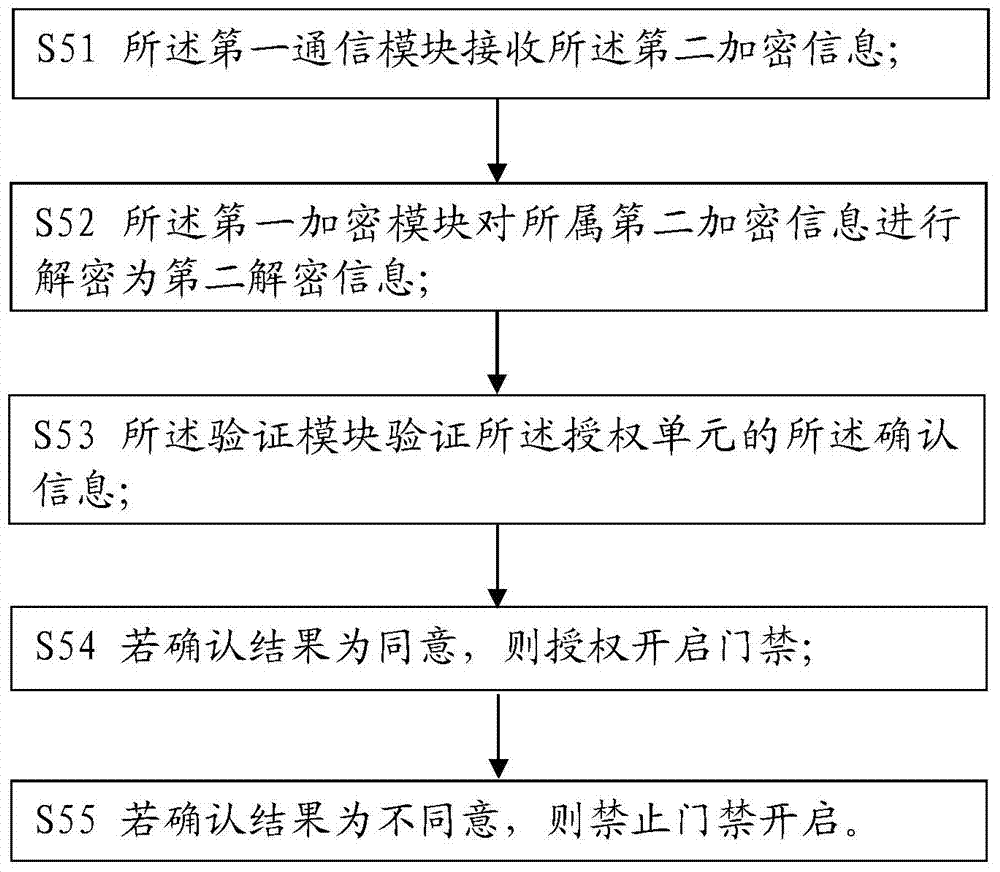
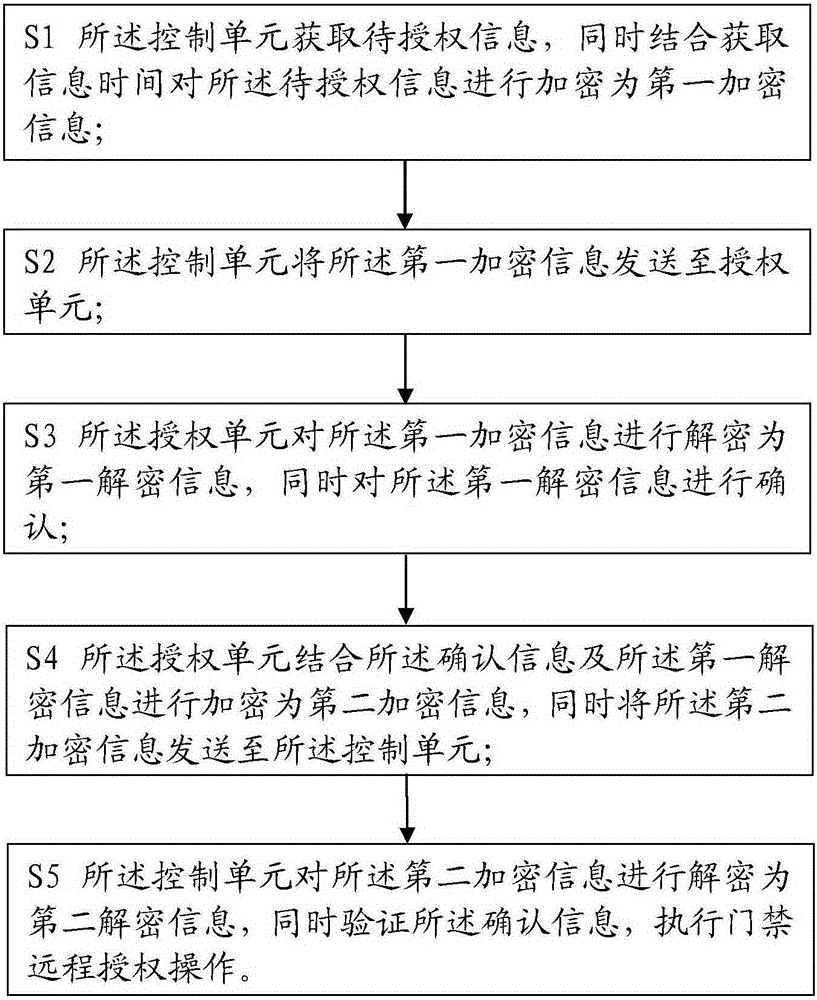
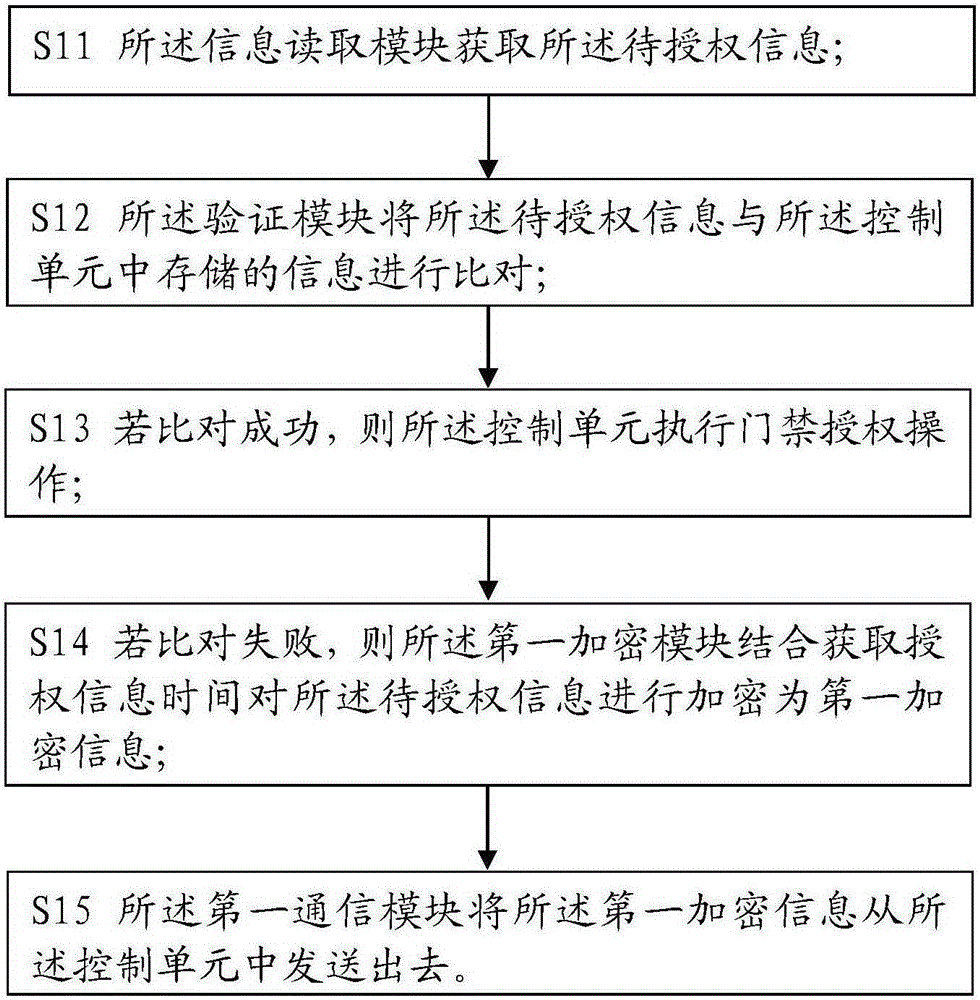
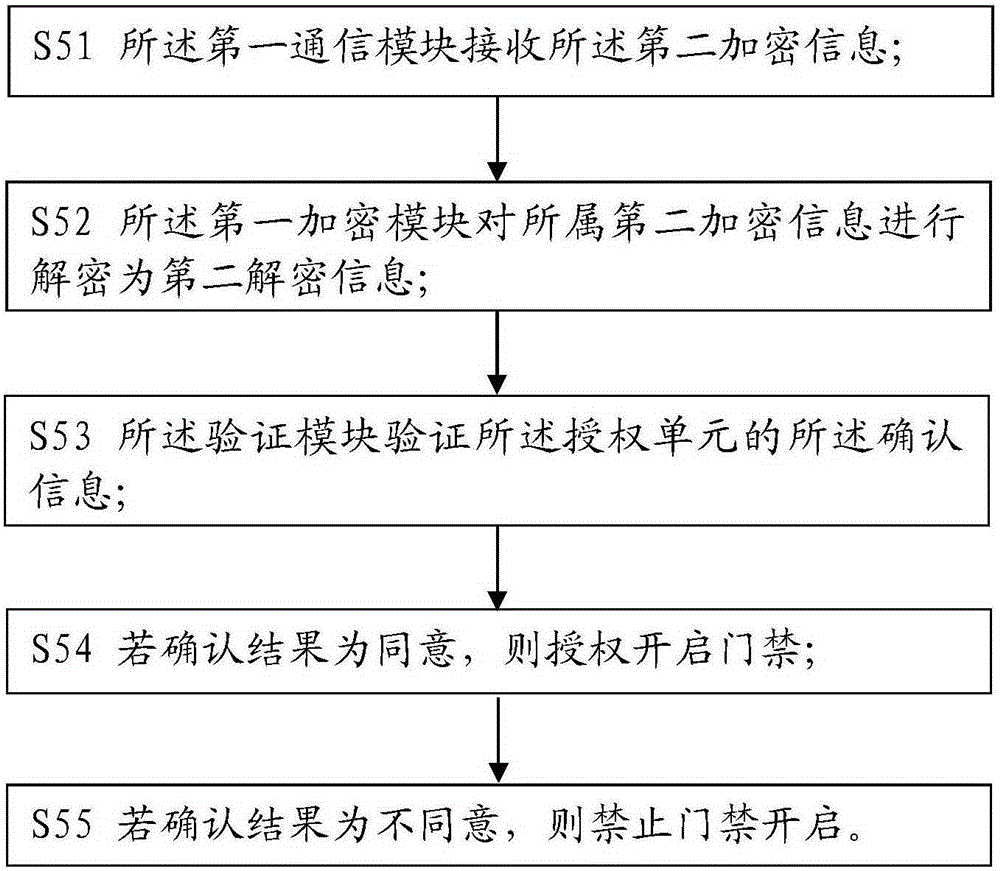
ActiveCN104123777AEnsure safetyImprove experienceIndividual entry/exit registersTransmissionAuthorizationInformation acquisition
The invention relates to the field of safety protection, and in particular relates to an access control remote authorization method which comprises the following steps of acquiring information to be authorized by a control unit, and encrypting the information to be authorized by combining information acquisition time to form first encrypted information; sending the first encrypted information into an authorization unit by the control unit; decrypting the first encrypted information by the authorization unit to form first decrypted information, and confirming the first decrypted information; encrypting the first decrypted information by combining the confirmation information by the authorization unit to form second encrypted information, and sending the second encrypted information into the control unit; decrypting the second encrypted information by the control unit to form second decrypted information, and confirming the information by verification; and executing access control remote authorization operation. According to the access control remote authorization method, an encryption module and a communication module are arranged in the control unit and the authorization unit, respectively, so that the safety of the information to be authorized is guaranteed in the communication process, and the remote communication between the control unit and the authorization unit can be realized.
Owner:SHANGHAI PEOPLENET SECURITY TECH
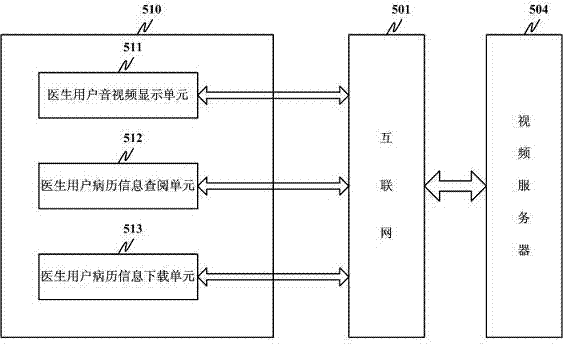
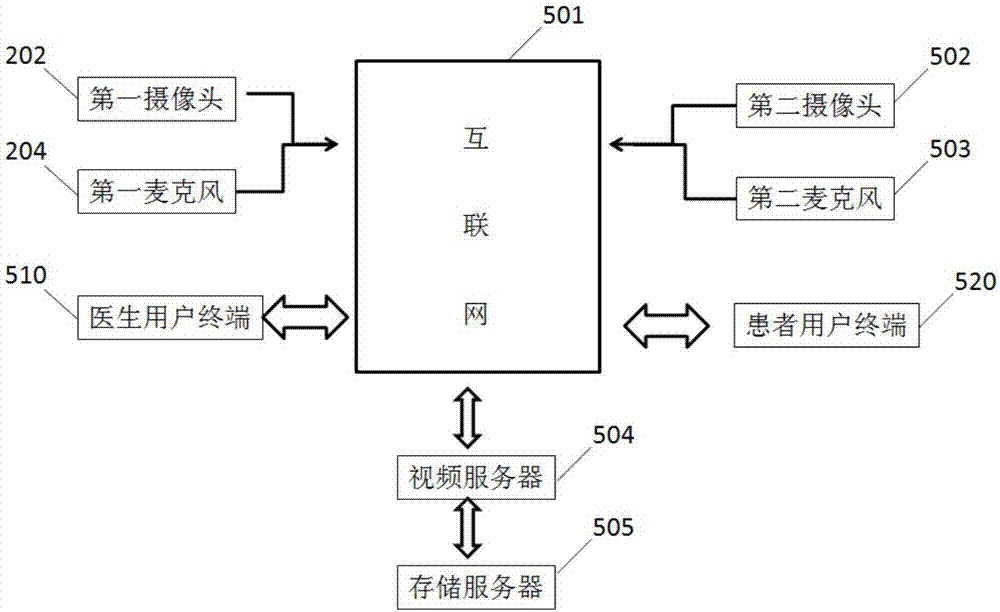
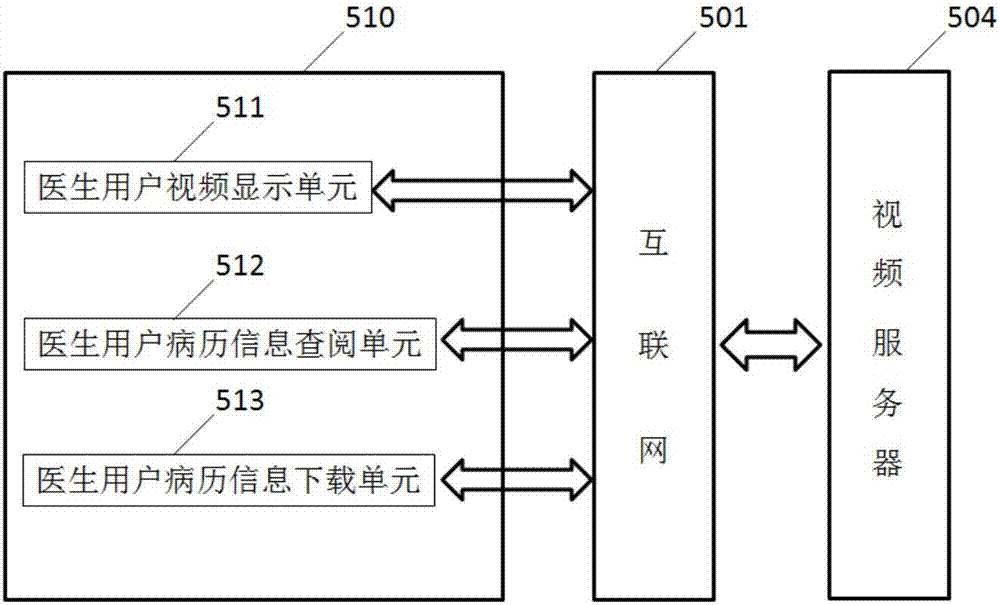
Video electronic medical record system based on internet
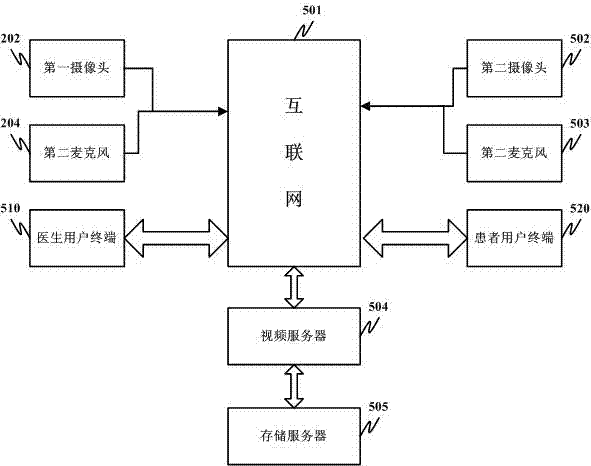
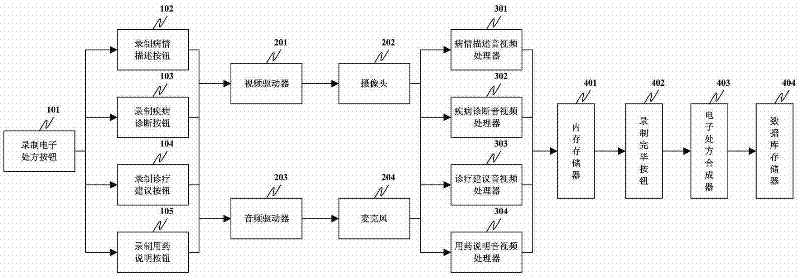
InactiveCN102254084AImprove convenienceImprove efficiencyTelevision system detailsColor television detailsMedical recordDisease
The invention discloses a video electronic medical record system based on the internet. The video electronic medical record system comprises a first camera, a first microphone, a doctor user terminal, a second camera, a second microphone, a patient user terminal, a video server and a storage server. By using the video electronic medical record system, the convenience for the inputting of electronic medical record information is improved, the time for inputting the electronic medical record information is shortened, and the overall treatment efficiency of doctors is increased. The electronic medical record information is stored in an internet platform, thus the information is convenient to authorize, share and download, and is convenient for investigation and evidence collecting in medical disputes. The video electronic medical record system replays a diagnosing process, and is greatly helpful for a doctor to diagnose diseases. Electronic prescriptions are transcribed and played independently, and can be used for obtaining the judgment of subjective conditions of patients, diagnosis results, diagnosis suggestions and medical information made by the doctor simply and conveniently.
Owner:DALIAN YICHUANG TIANDI TECH DEV
System and method for network accession utilizing single clicking single pointing
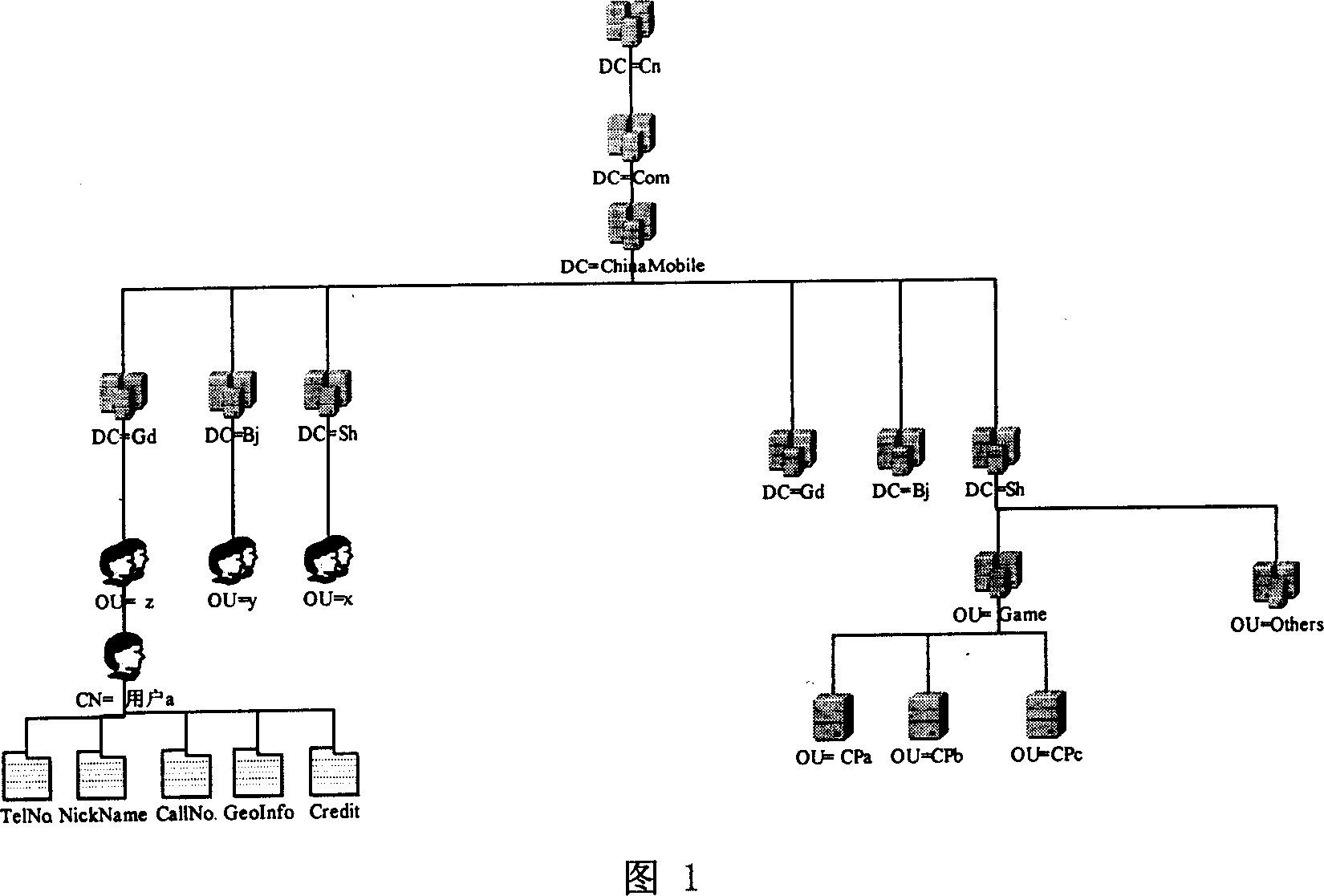
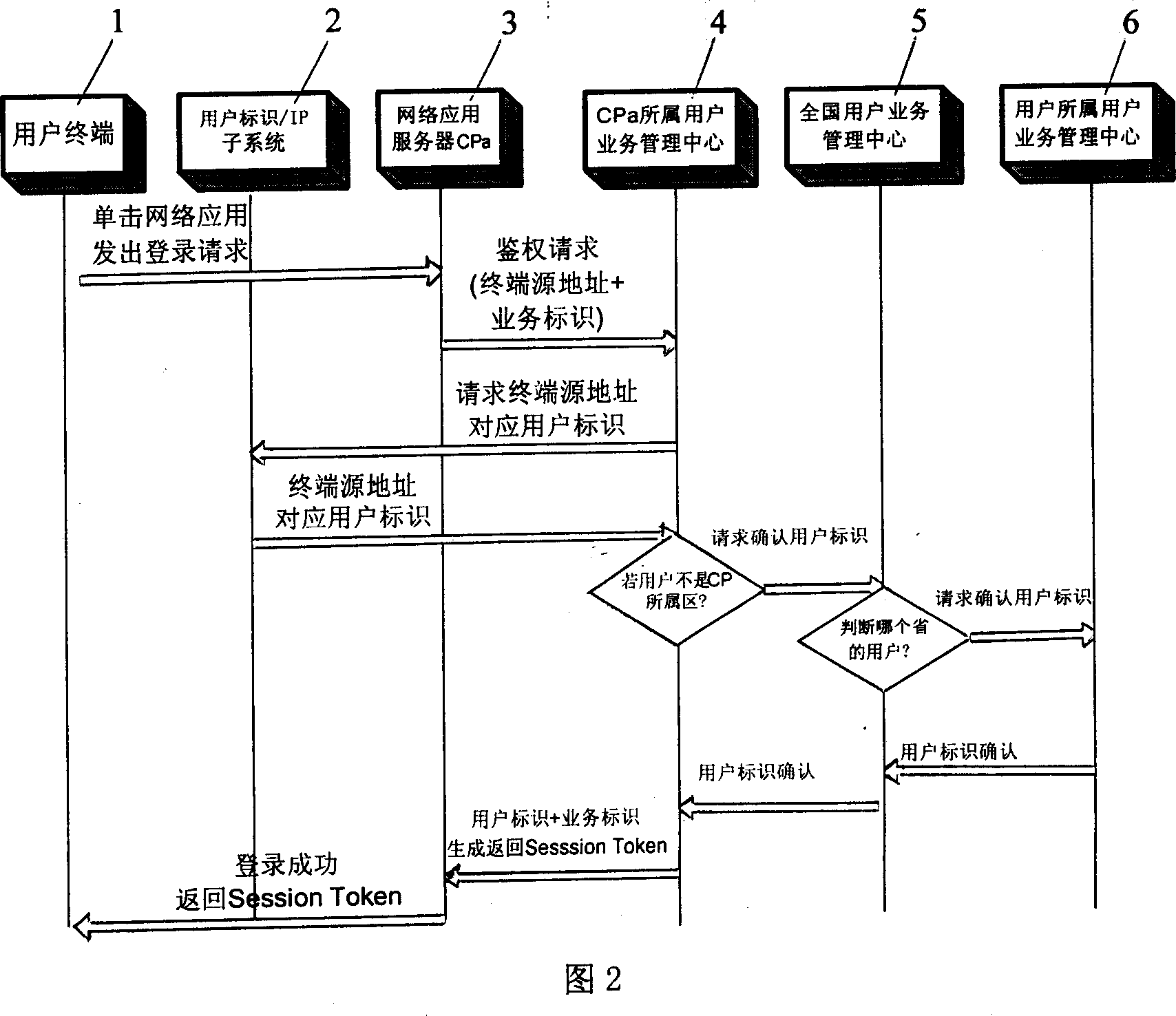
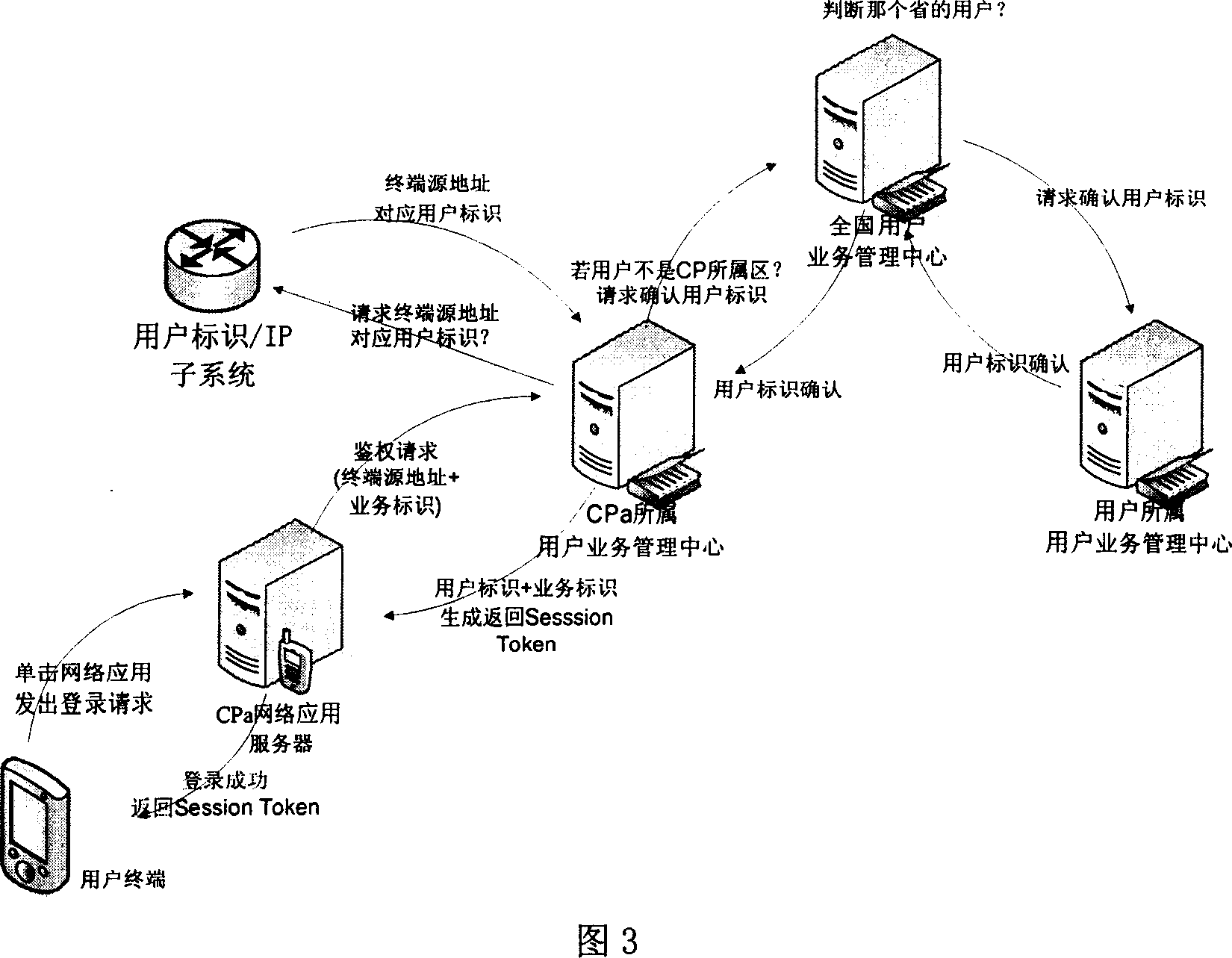
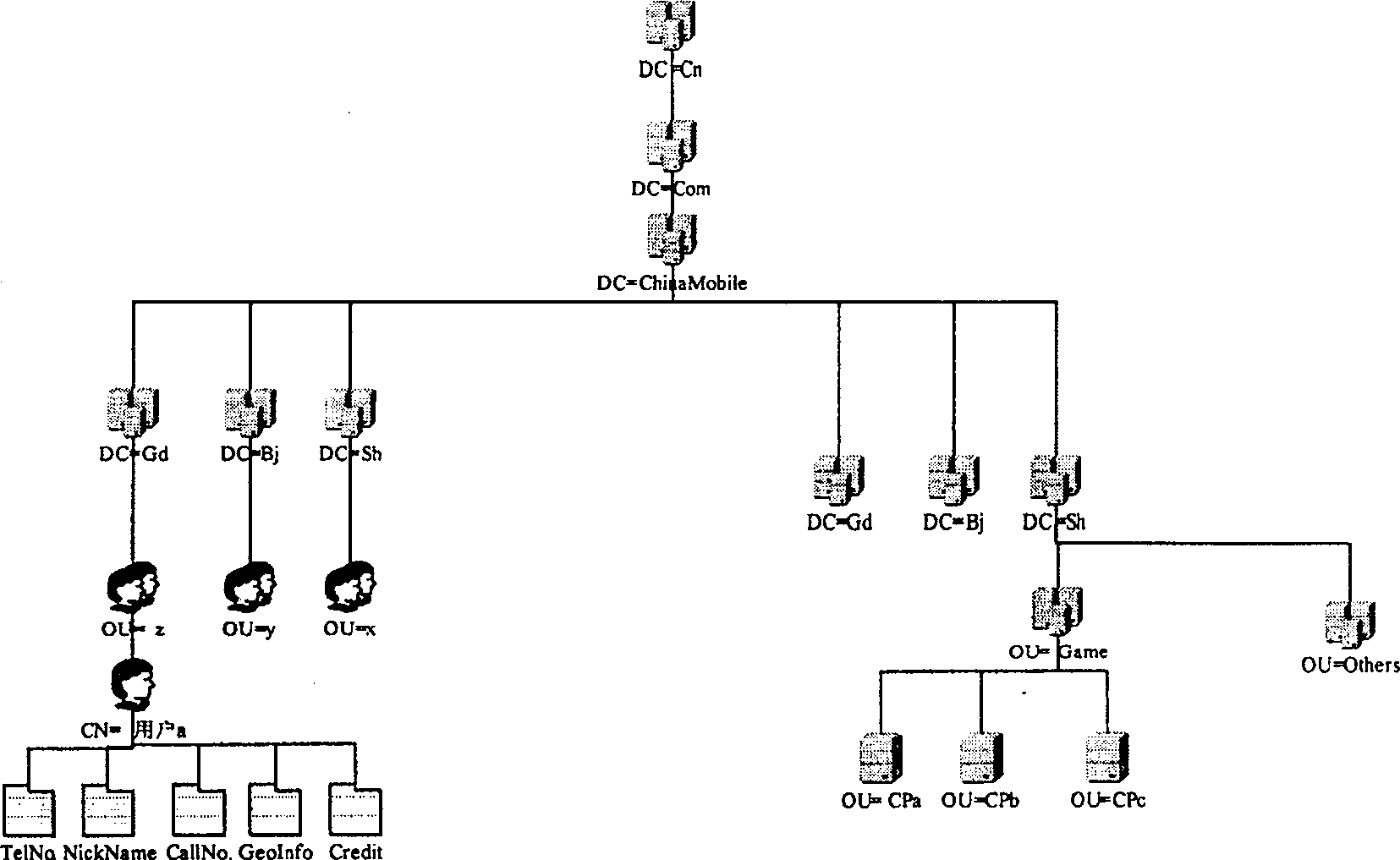
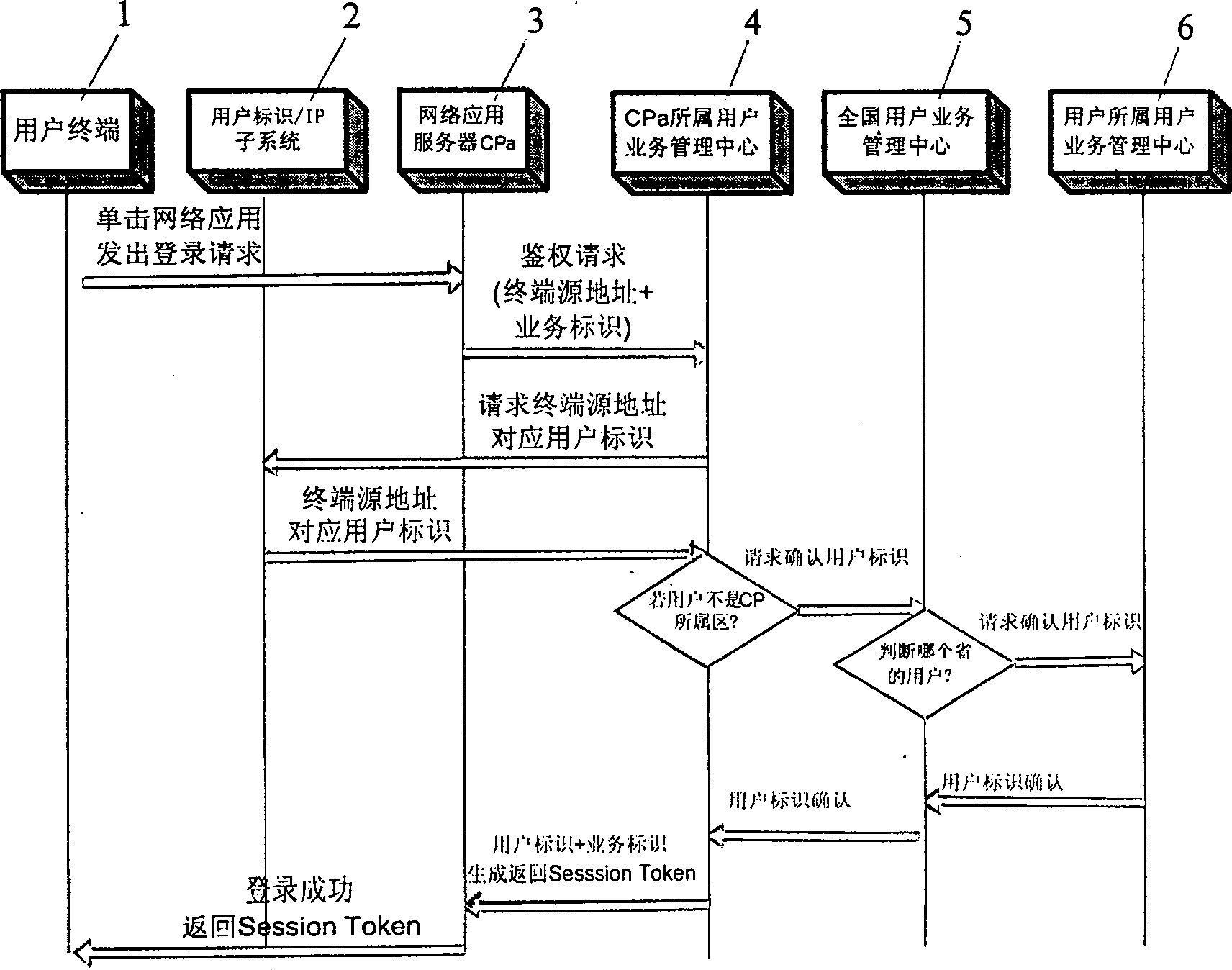
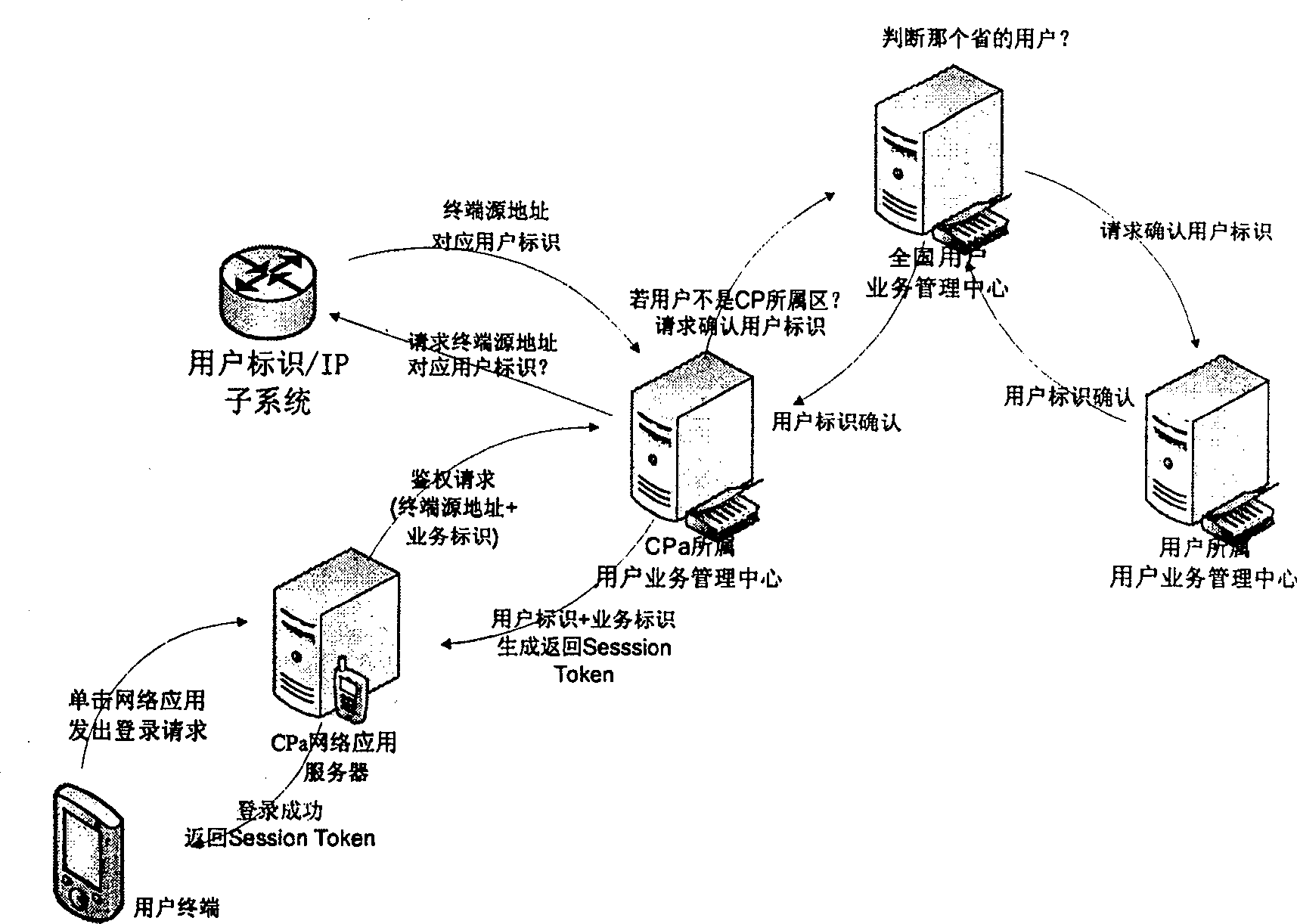
InactiveCN1933483ASimplify Management ComplexityEasy to useUser identity/authority verificationData switching by path configurationIp addressUser management
A user management and certification system of network application comprises user terminal, user identification / ZP subsystem, network application server CPa, user service management center of network application server CPa, user service management center of nationwide and user service management center of the user. It is featured as allowing trustful network application system or network application certifying system to check user information by using user identification / ZP subsystem to switch on interface.
Owner:王伟珣
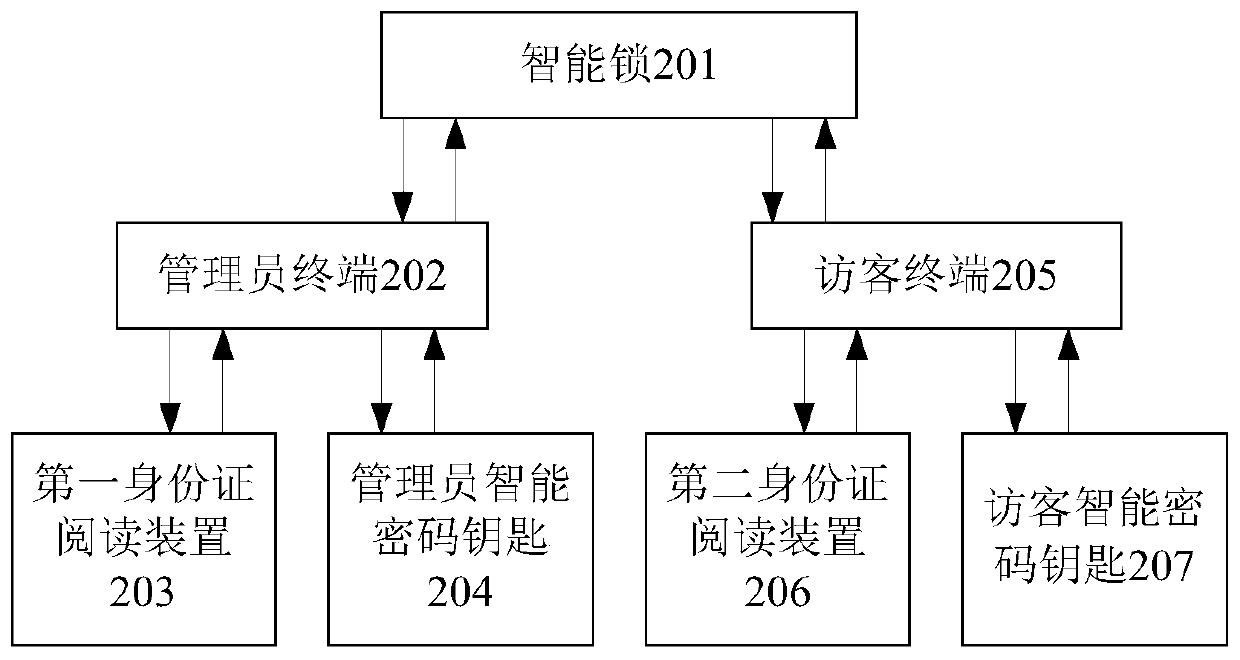
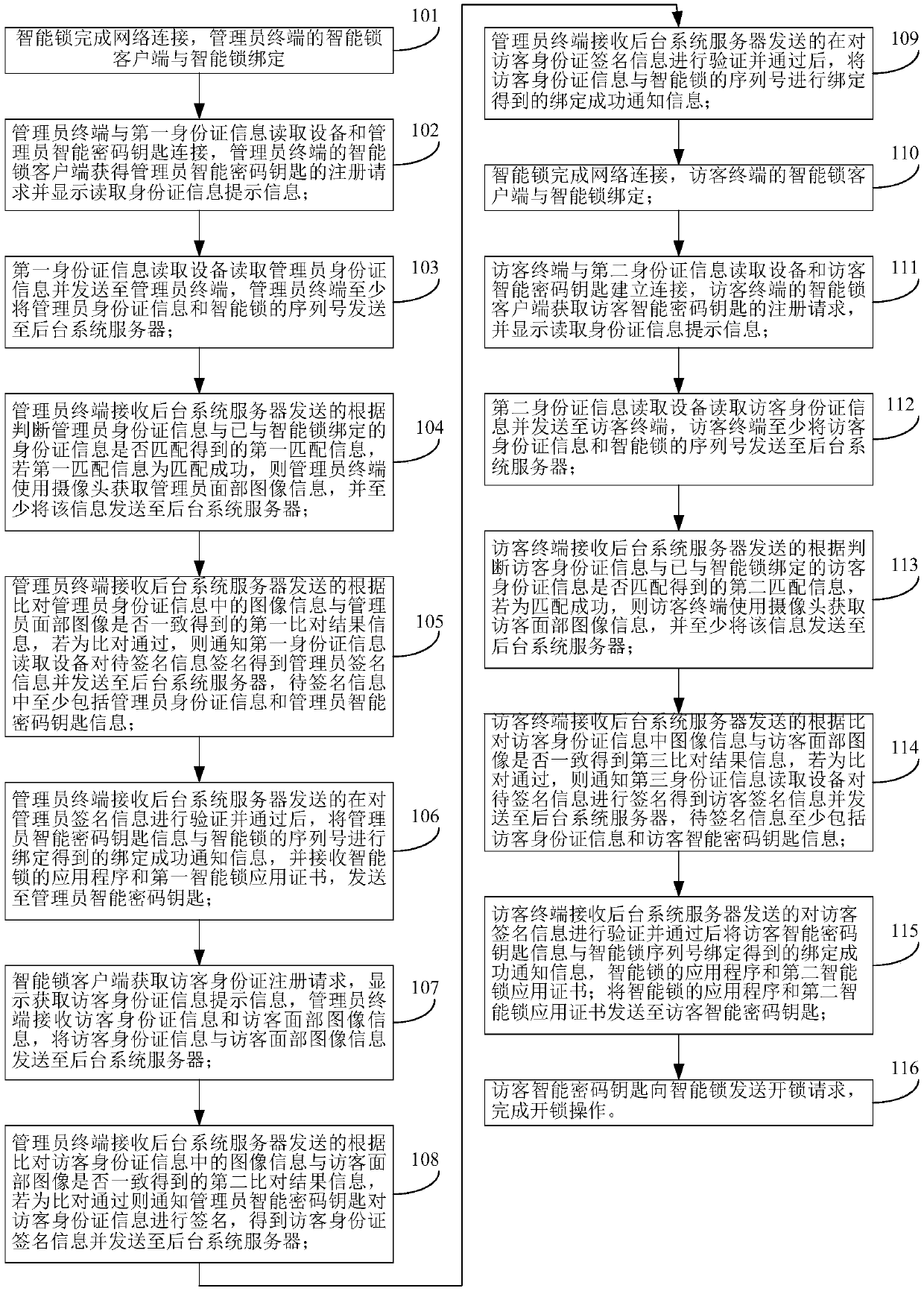
Intelligent lock unlocking method and system
ActiveCN109920100AImprove securityConvenient authorizationIndividual entry/exit registersComputer hardwarePassword
The invention provides an intelligent lock unlocking method and system. The intelligent lock unlocking method comprises the steps that an administrator intelligent password key is authorized through an authorized administrator identity card, a visitor identity card is authorized through the authorized administrator intelligent password key, and a visitor intelligent password key is authorized through the obtained authorized visitor identity card. When the administrator identity card has the authority to unlock the intelligent lock, the intelligent lock can be unlocked, the visitor intelligentpassword key is authorized to obtain the unlocking authority, a visitor can open the intelligent lock by using the intelligent password key, the intelligent lock can also be unlocked by using the visitor identity card, and the administrator can also unlock the intelligent lock by using the administrator identity card and the administrator intelligent password key, so that on one hand, the administrator can authorize other intelligent lock users and use very conveniently, and on the other hand, the safety of the intelligent lock is improved.
Owner:TENDYRON CORP
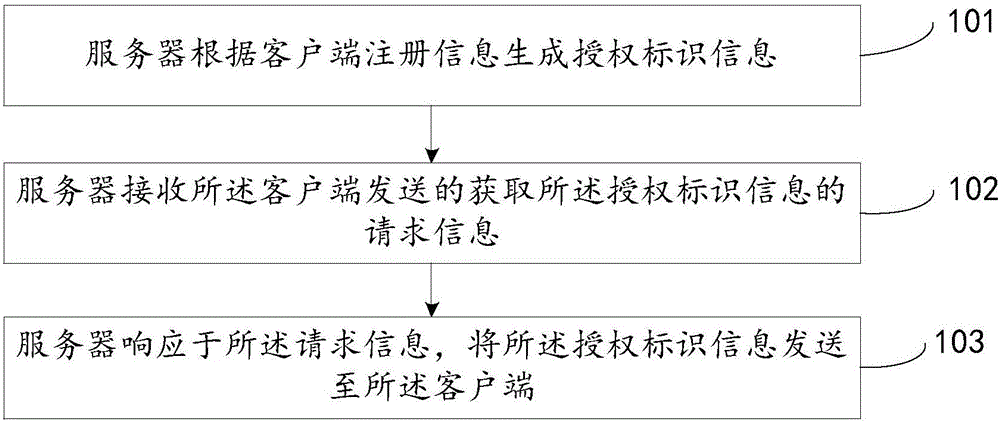
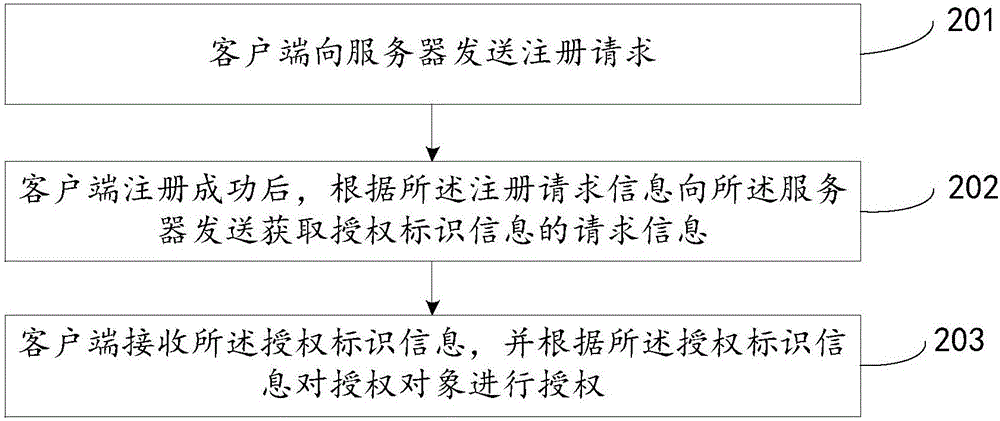
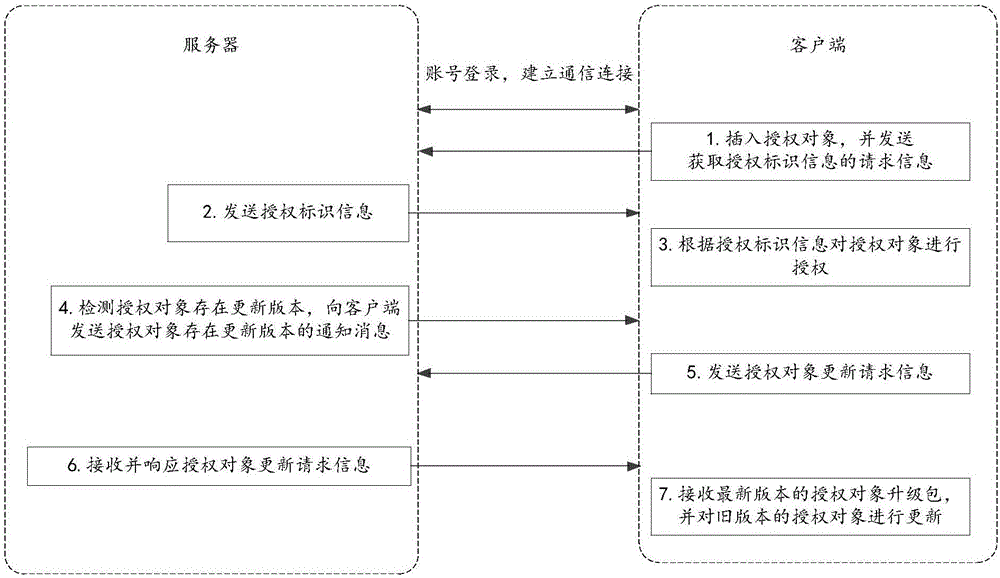
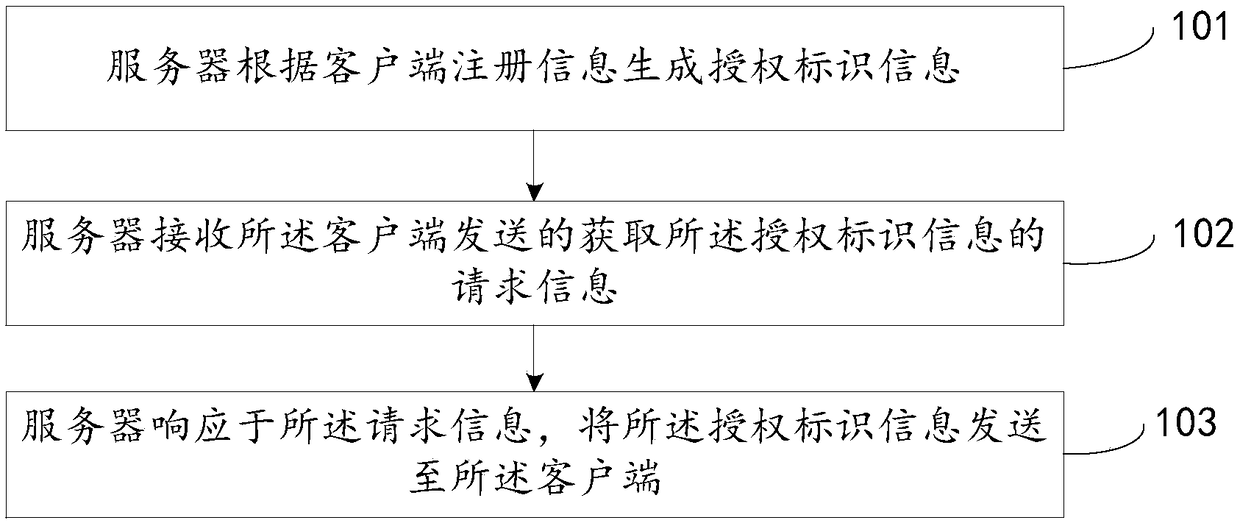
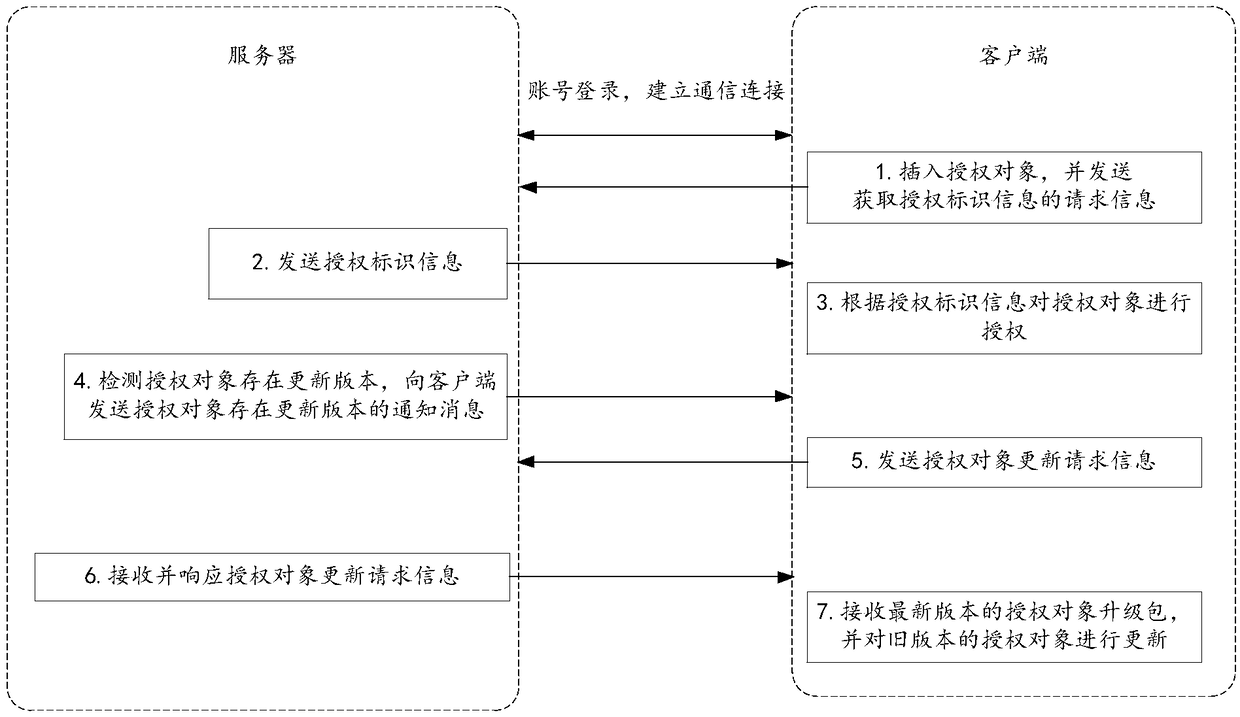
Authorization method, client-side, server and system
The invention discloses an authorization method, a client-side, a server and a system, relates to the technical field of internet and mainly aims at solving the problem that the operating process is complicated during authorization of an authorization object (control lock) in the prior art and achieving the authorization step of the authorization object. According to the main technical scheme, the authorization method comprises the steps that server generates authorization identification information according to registration information on the client-side; request information for acquiring the authorization identification information sent by the client-side is received; responding to the request information, the authorization identification information is sent to the client-side so that the client-side conducts authorization on the authorization object according to the authorization identification information.
Owner:BEIJING SENSESHIELD TECH
Medicine research and development software warehouse and software package management system thereof
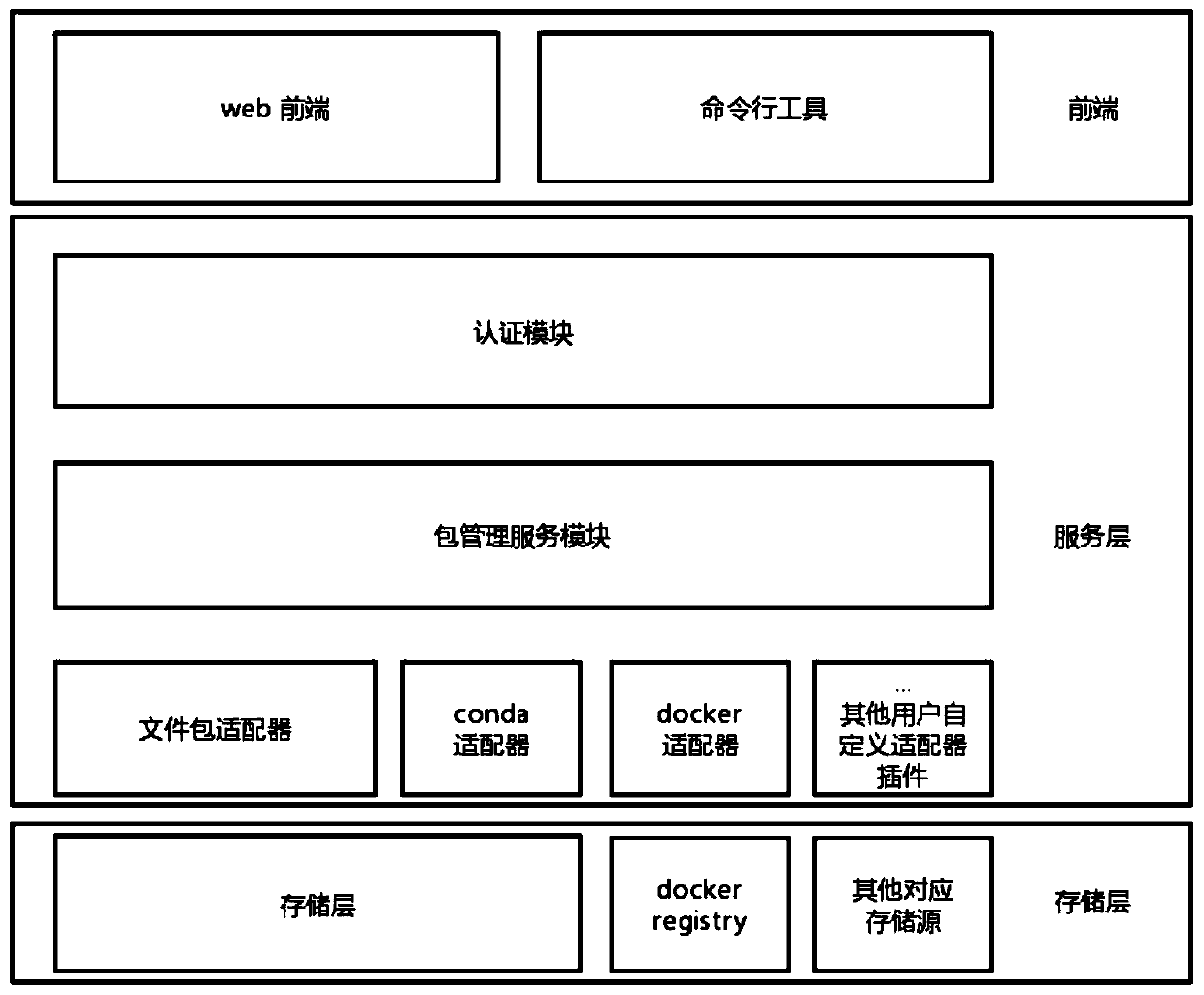
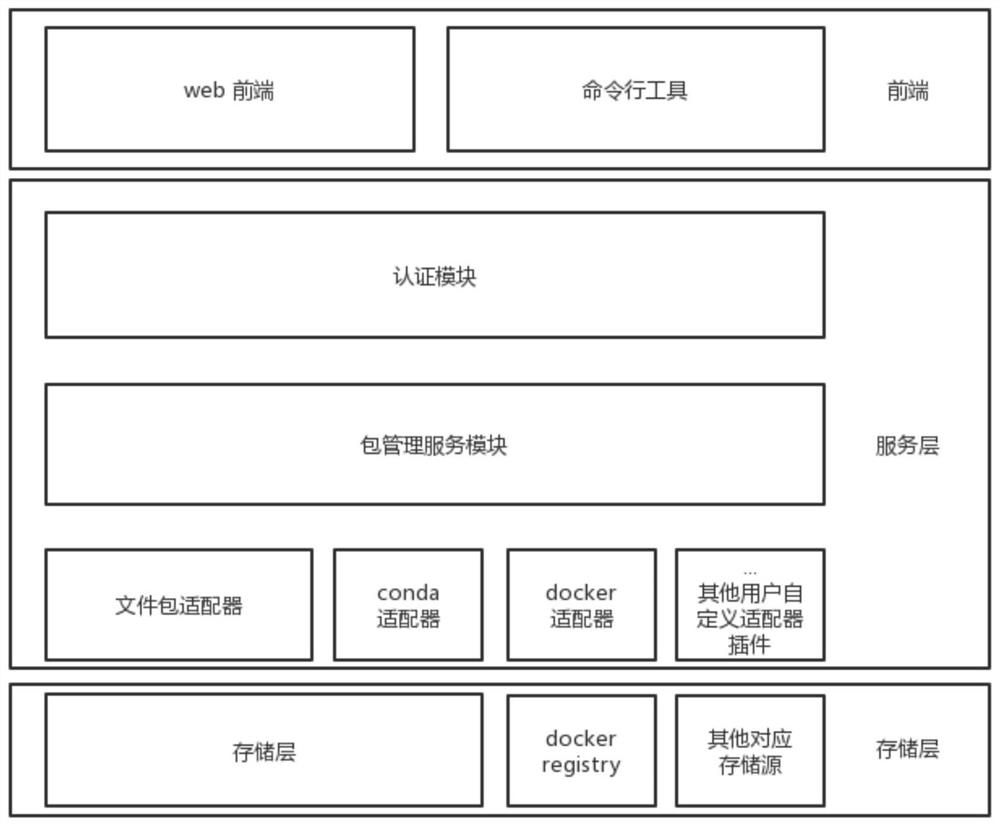
ActiveCN111221562AAchieve cross-platformConvenient authorizationDigital data protectionSoftware maintainance/managementSoftware distributionSoftware system
The invention provides a medicine research and development software warehouse and a software package management system thereof. The medicine research and development software warehouse comprises a user authentication module, a software package uploading and index creation module, a baseline release management module, an authorization management module, a software package retrieval and downloadingmodule, an adapter plug-in and a storage layer. The software package management system comprises an authentication module, a package management service module, a web front-end module and a command line tool module. Through a plug-in mode, various object storage services and software warehouses can be docked, so that cross-platform and multi-development-language software package management is realized; an authentication function and a software authorization function are added, so that a user can conveniently authorize software researched and developed in a company to a partner for use, and a software distribution mode is simpler; and a baseline management function is added, so that the software is more concise to publish to the outside, and meanwhile, the cooperation efficiency of internaldevelopers in developing different software packages of the same software system is improved.
Owner:SHENZHEN JINGTAI TECH CO LTD
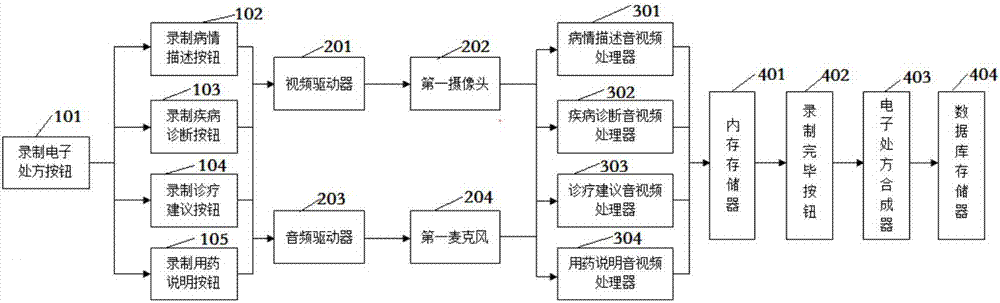
Video electronic prescription system
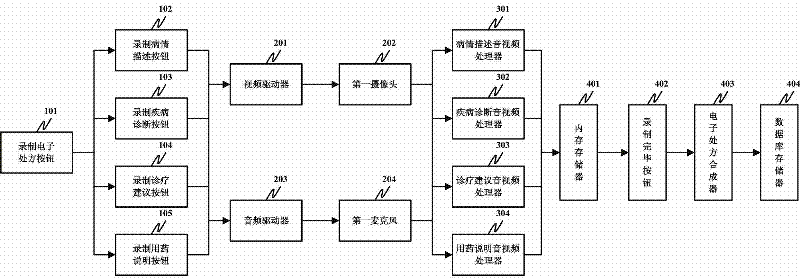
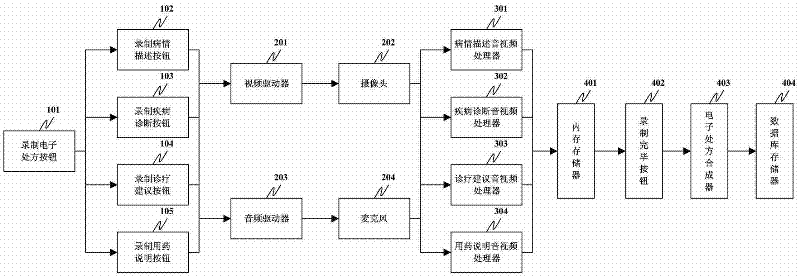
InactiveCN102236743AImprove convenienceImprove the efficiency of medical treatmentTelevision system detailsColor television detailsDiseaseThe Internet
The invention discloses a video electronic prescription system which comprises an electronic prescription button for recording, a camera, a microphone, an audio / video processor for disease state description, an audio / video processor for disease diagnosis, an audio / video processor for diagnosis and treatment suggestion, an audio / video processor for drug administration introduction, and a database memory. The system shortens the information input time for diagnosis and treatment prescription, and enhances the overall efficiency for doctor diagnosis; the electronic diagnosis and treatment prescription can be stored on an Internet platform, and is convenient for authorization, sharing and downloading; and every stage is an independent individual, and can be played independently, so that the patient can simply and quickly acquire the doctor's judgment, diagnostic result, diagnosis and treatment suggestion and drug administration introduction on the disease state at that time.
Owner:DALIAN YICHUANG TIANDI TECH DEV
Form operation permission authorization method based on role
InactiveCN107301335AImprove form authorization efficiencyConvenient authorizationDigital data authenticationOffice automationAuthorizationDatabase
The invention discloses a form operation permission authorization method based on a role. The method comprises the following steps that: selecting an authorized role: selecting one or a plurality of roles as authorized roles, wherein each role is an independent individual but is not groups / categories, one role in the same time period only can be associated with a unique user, and one user is associated with one or a plurality or roles; selecting a form: when the number of the selected authorized role is one and the number of the selected form is one, displaying the existing permission state of the authorized role for the selected form; when the number of the selected forms is at least two, displaying blank form operation permission; carrying out form operation permission authorization on the authorized form; and after above steps are finished, storing the permission of the authorized role. By use of the method, the authorization efficiency of the form operation permission is improved, the method is simple in operation, the safety performance of a system is improved, and a risk that losses are caused for enterprises due to the leakage of information can be reduced.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
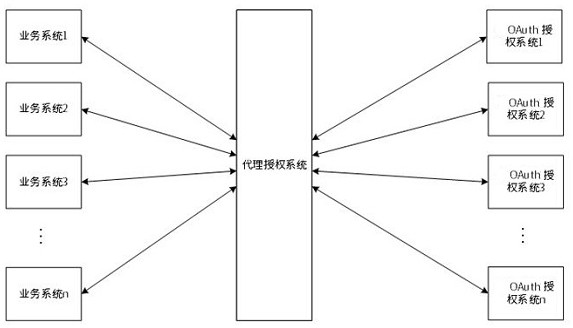
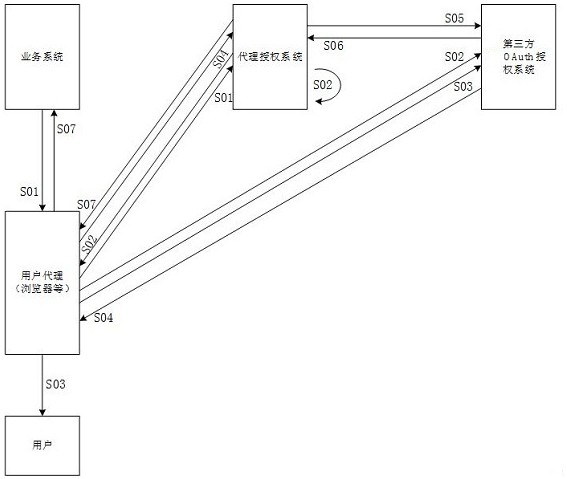
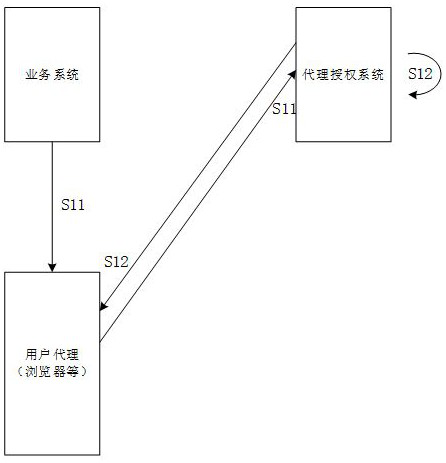
Secure OAuth agent and credible domain mixed authorization method
PendingCN111835722AReduce docking costsAchieve accessUser identity/authority verificationThird partyAuthorization Mode
The invention discloses a secure OAuth agent and credible domain mixed authorization method in the technical field of user authorization protocol transformation and single sign-on implementation. Themethod comprises an agent authorization method and a credible domain verification method. A safe agent authorization mode comprises: based on a mode that the agent authorization service is in butt joint with a third-party OAuth authorization system and then a sevice system is in butt joint with the agent authorization service, obtaining a third-party resource service access token, encrypting the access token in an asymmetric encryption mode, and finally transmitting the encrypted information back to the service system. Credible domain verification comprises: comparing parameters carried by theHTTP protocol request based on URI recorded during registration of the service system, performing determination, and returning user information under the corresponding security level if the verification is passed Realizing single sign-on through mixed verification comprises: realizing single sign-on of the user through agent authorization of OAuth and credible domain verification.
Owner:郑州泰来信息科技有限公司
Video electronic medical record system with internet virus detection component
InactiveCN107358037AImprove convenienceImprove efficiencyPlatform integrity maintainanceTwo-way working systemsMedical recordDisease
The invention discloses a video electronic medical record system with an internet virus detection component. The system comprises a first camera, a first microphone, a doctor user terminal, a second camera, a second microphone, a patient user terminal, a video server, a storage server and the internet virus detection component. According to the system, the convenience of electronic medical record information input is improved, the time consumption of electronic medical record information input is decreased and the overall efficiency of doctor visiting is improved; the electronic medical record information is stored on a platform of internet, so that the authorization, share and downloading are convenient; investigation and evidence collection in medical disputes is convenient; the diagnosis and treatment process are really restored, so that great help is provided for the later disease diagnosis of the doctors; and through single recording and later single playing of electronic prescriptions, the subjective illness state judgement, diagnosis results, diagnosis and treatment suggestions and pharmacy explanation provided by doctors for patients can be simply and rapidly obtained, and meanwhile, due to the presence of the internet virus detection component, the device can be prevented from virus infection.
Owner:罗颖莉
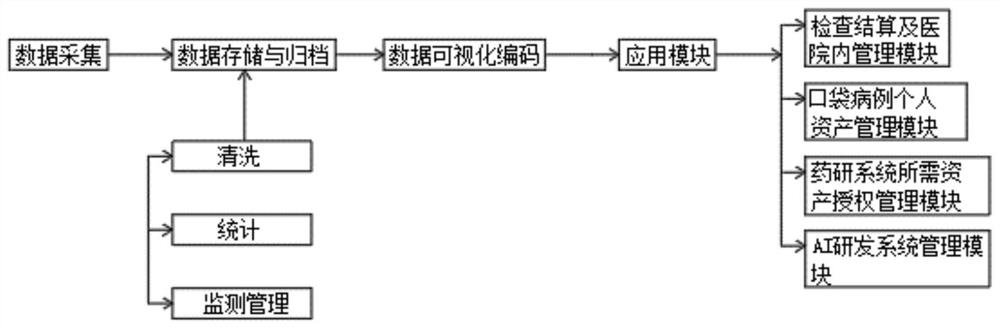
Medical data asset management system platform
PendingCN114038523ARealize capitalizationConvenient authorizationMedical reportsInstrumentsMedical recordDisease
The invention discloses a medical data asset management system platform. The specific working method comprises the steps of 1, collecting original medical data from each business application system of a hospital, enabling a data collection module to be in butt joint with electronic medical records (EMR), image examination RIS and examination LIS of all hospitals in an area under jurisdiction, collecting infectious disease data, non-infectious disease data and the like from a public health data center, rapidly positioning and collecting all data by applying technical research and development of a 5G novel network architecture, and synchronizing the data to the cloud; and 2, performing preliminary data cleaning and formatting on the archived and stored data, and performing multi-dimensional cleaning on original data acquired by a data center. According to the medical data asset management system platform, data can be effectively monitored and traced, coding management can be conveniently carried out on the data, data capitalization is realized, and subsequent query, classification, sharing, supervision, tracing, transaction and the like can be conveniently carried out on data assets by using the platform.
Owner:杭州联众医疗科技股份有限公司
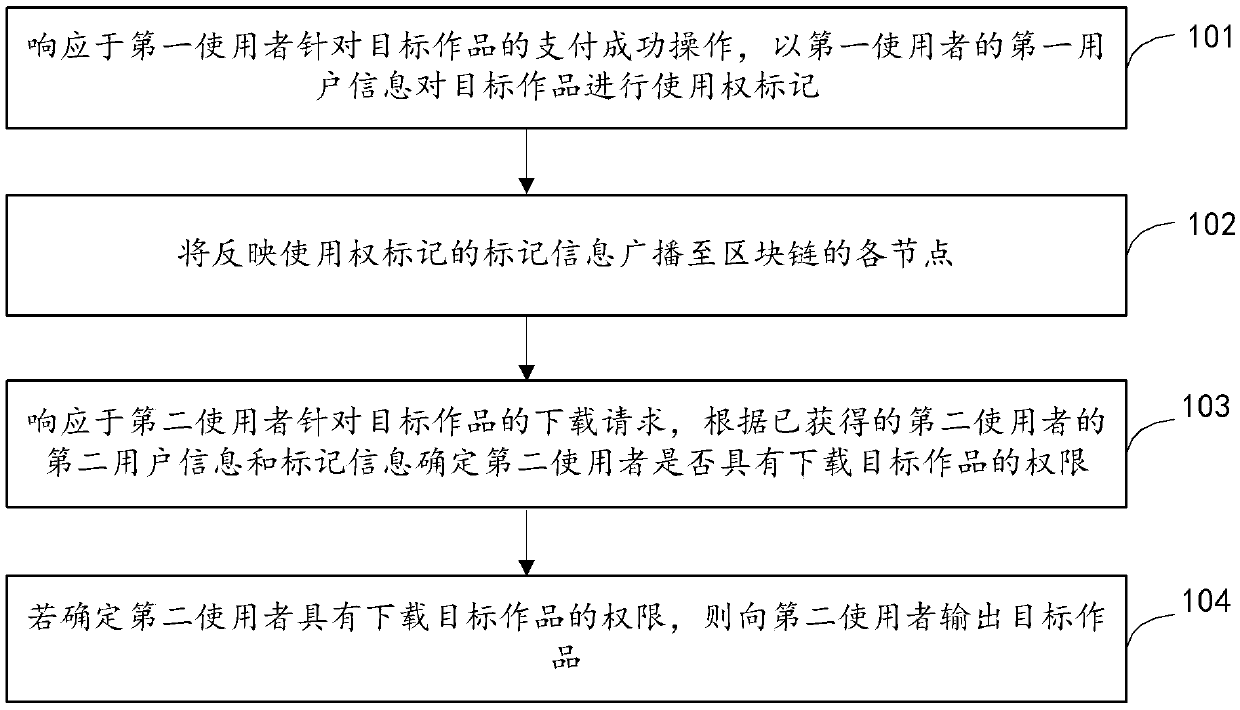
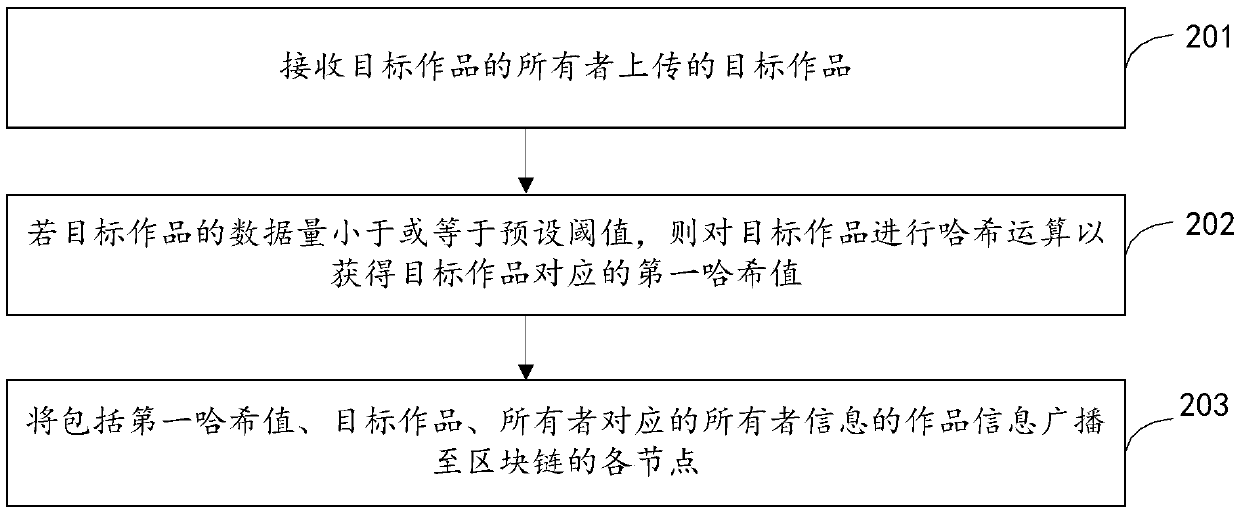
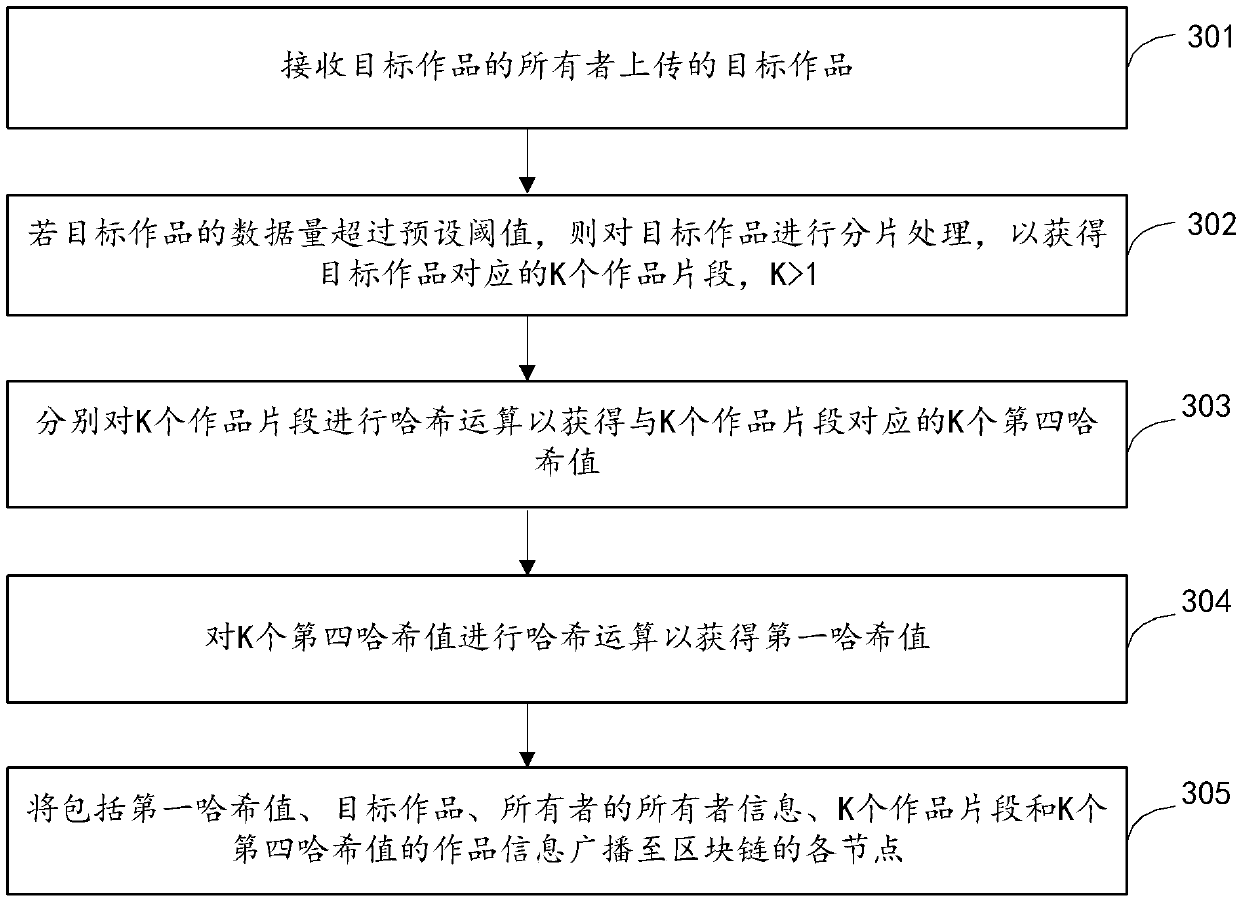
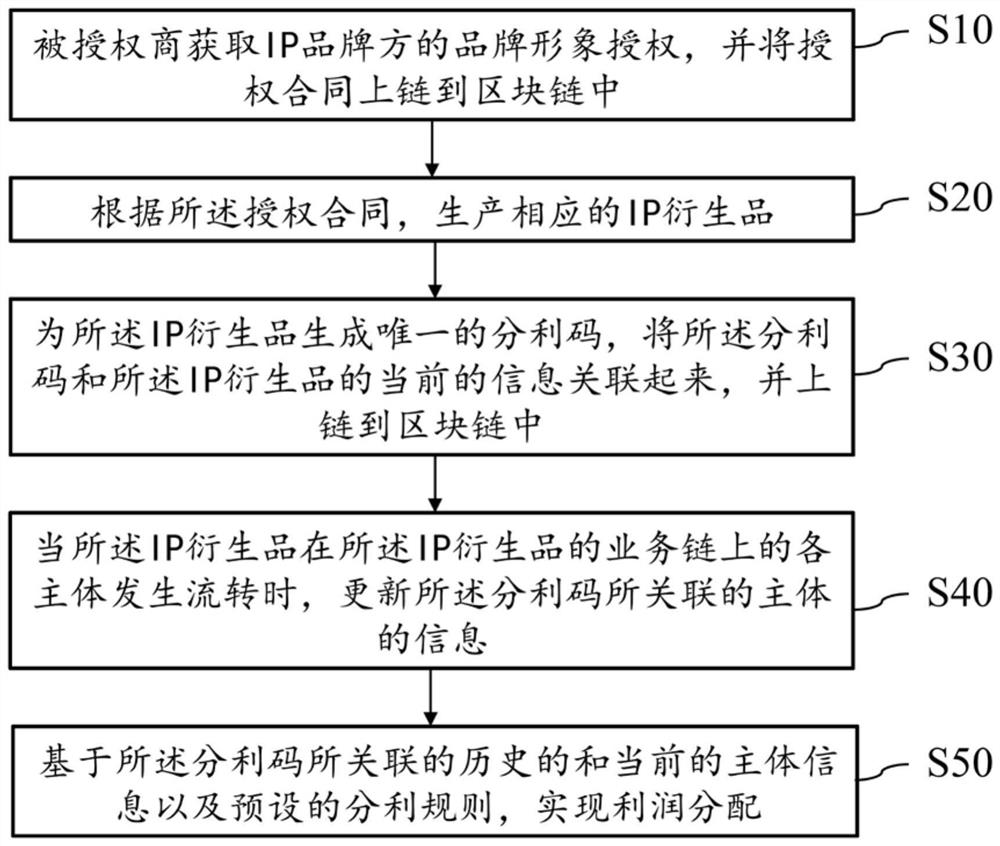
Work management method and device based on block chain, and equipment
InactiveCN110502870AGuaranteed validityAvoid infringementData processing applicationsProgram/content distribution protectionBlockchainAuthorization
The embodiment of the invention provides a work management method and device based on a block chain, and equipment. The work management method comprises the steps: responding to the payment success operation of a first user for a target work, and carrying out the use right marking of the target work through the first user information of the first user; broadcasting the mark information reflectingthe use right mark to each node of the block chain; and in response to a downloading request of a second user for the target work, if it is determined that the second user has the permission to download the target work according to the obtained second user information and the mark information of the second user, outputting the target work to the second user. When a user wants to use a certain target work, the use right of the user is marked for the target work, so that authorization of an owner is obtained, and authority verification of a downloader can be completed based on the use right marking information of the target work when the target work is downloaded, and effectiveness of use behaviors of the target work is guaranteed.
Owner:北京果仁宝软件技术有限责任公司
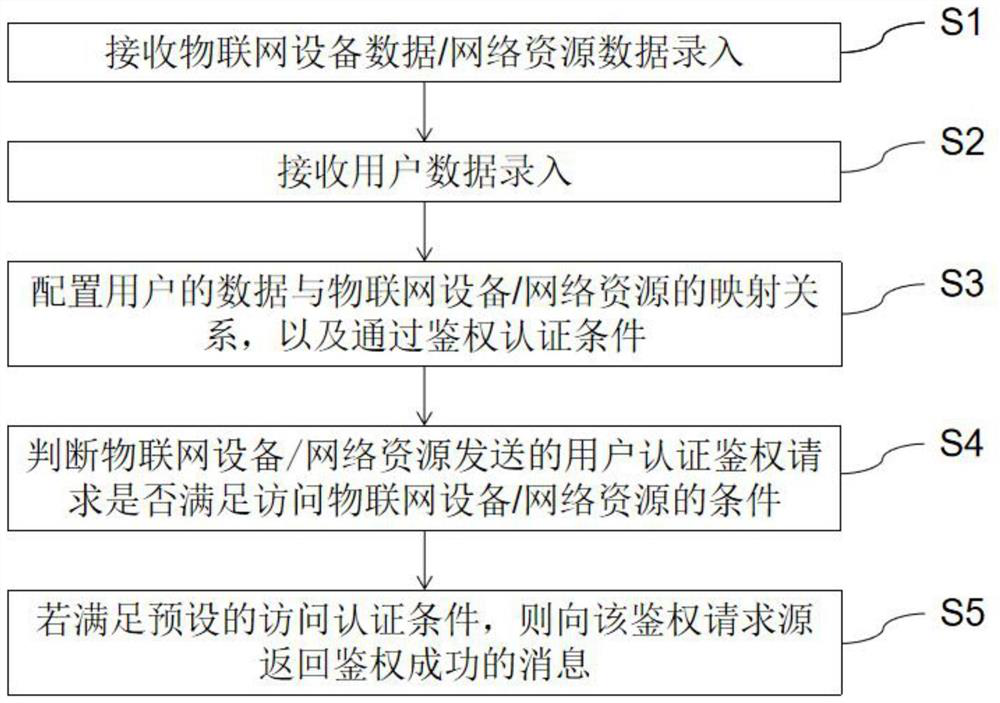
Authentication method, device and system and computer storage medium
ActiveCN113037736AImprove business efficiencyReduce risk of leakageIndividual entry/exit registersTransmissionThird partyInternet privacy
The invention discloses an authentication method, device and system and a computer storage medium. The authentication method is applied to local network equipment. The authentication method comprises the following steps: receiving Internet of Things equipment data / network resource data entry; receiving user data entry; configuring a mapping relationship between the data of the user and the Internet of Things equipment / network resources, and authenticating conditions through authentication; judging whether a user authentication request sent by the Internet of Things device / network resource meets the condition of accessing the Internet of Things device / network resource; and if the preset access authentication condition is met, returning an authentication success message to the authentication request source. According to the invention, third-party authentication service can be provided for Internet of Things equipment, internal application service and the like in a local area network. Herein, the ownership and the use authorization of the internet of things equipment main body and the local area network internal resources are separated, and the use authentication authority and the ownership of the equipment are logically separated.
Owner:SICHUAN JIUZHOU ELECTRONICS TECH
Remote authorization method and device in abnormal state, equipment and medium
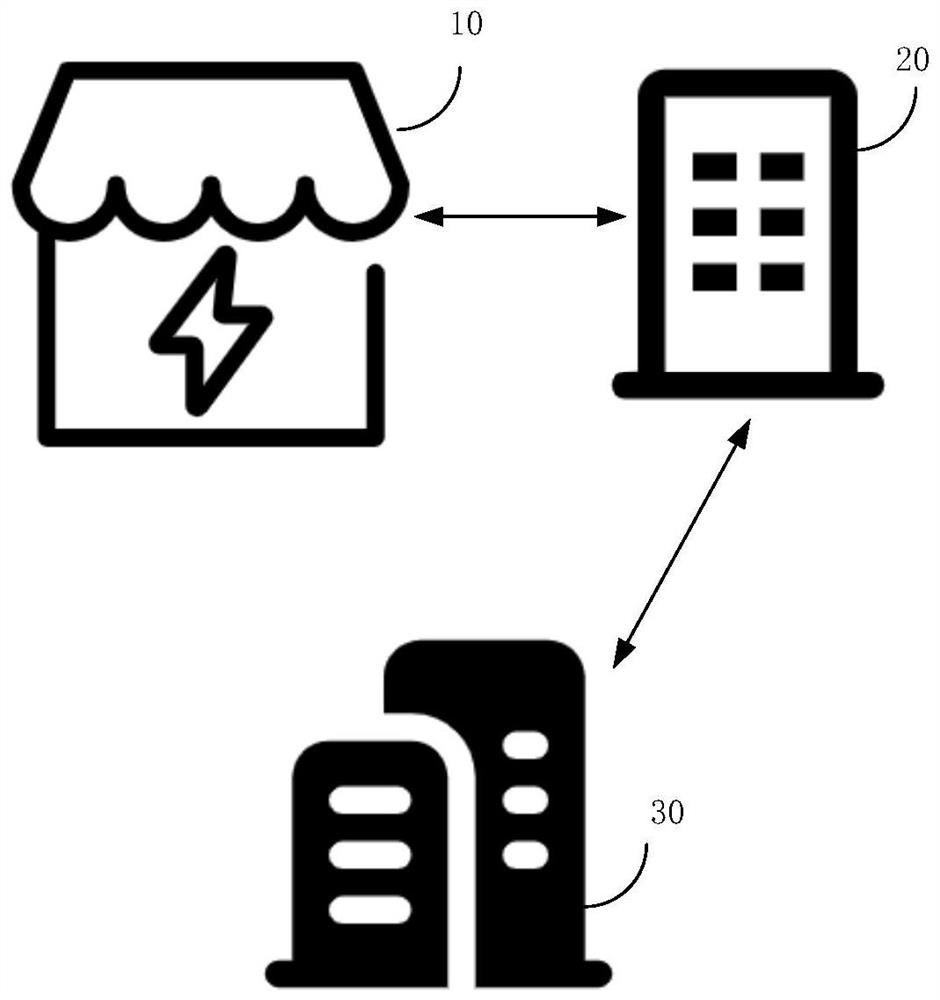
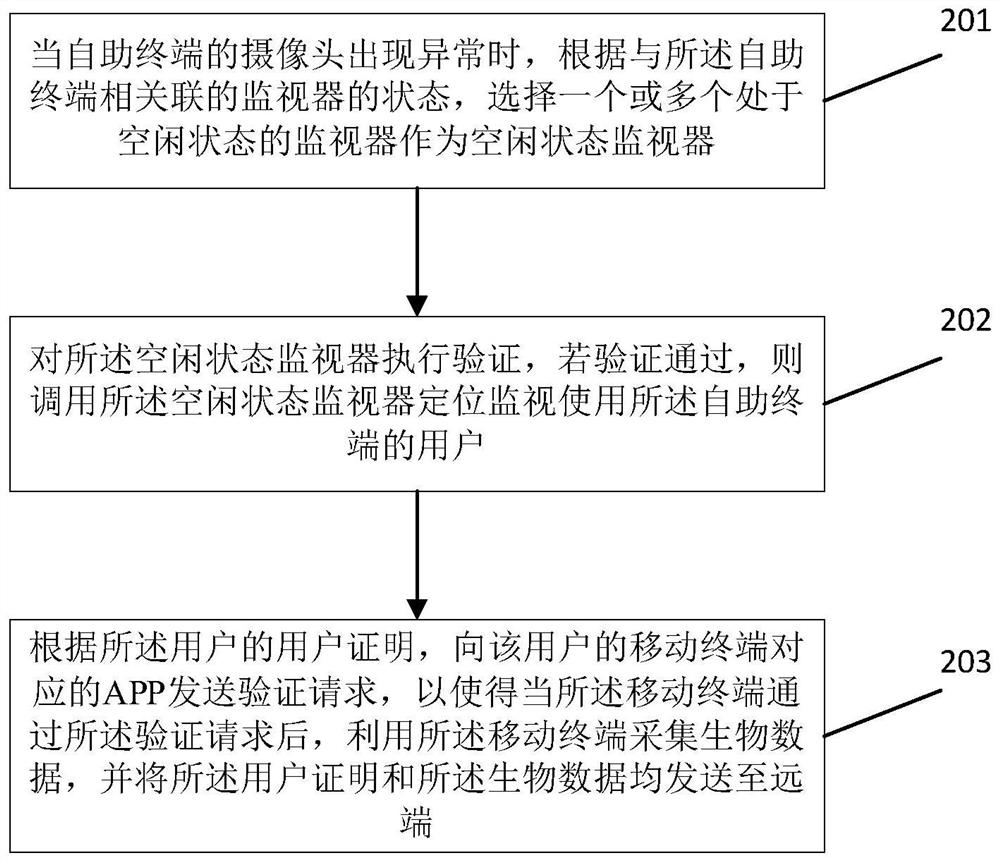
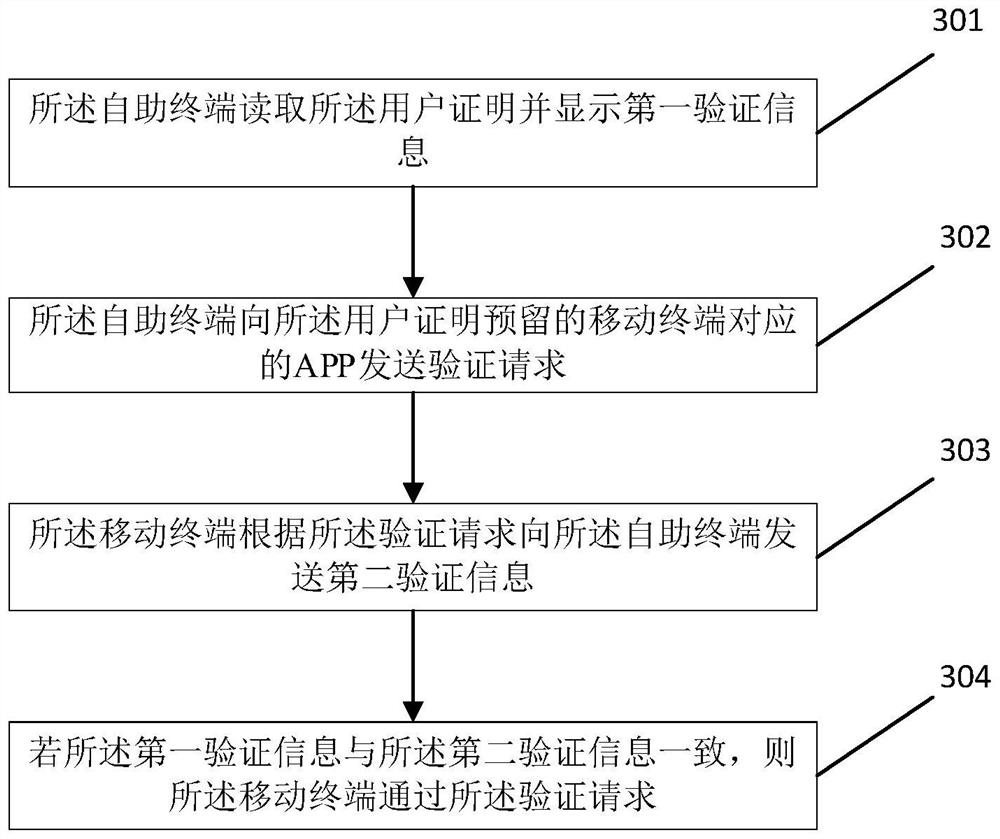
ActiveCN114596680AImprove experienceConvenient authorizationComplete banking machinesCharacter and pattern recognitionCollections dataAuthorization
The invention provides a remote authorization method and device in an abnormal state, equipment and a medium, is applied to a self-service terminal, and comprises the following steps: when a camera of the self-service terminal is abnormal, selecting one or more monitors in an idle state according to the state of a monitor associated with the self-service terminal; verifying the idle state monitor, and if the verification is passed, calling the idle state monitor to position and monitor a user using the self-service terminal; and according to the user certificate of the user, sending the verification request to the APP corresponding to the mobile terminal of the user, so that after the mobile terminal passes the verification request, the mobile terminal is utilized to collect the biological data, and the user certificate and the biological data are sent to the remote end, thereby realizing data collection and remote authorization under the abnormal condition of the self-service terminal. And the self-service terminal calls the monitor to monitor the user, so that cheating of the user can be prevented, and the risk of remote authorization is reduced.
Owner:BANK OF JILIN
Drug research and development software warehouse and its software package management system
ActiveCN111221562BAchieve cross-platformConvenient authorizationSoftware maintainance/managementDigital data protectionSoftware distributionSoftware system
The invention provides a drug research and development software warehouse and its software package management system, a drug research and development software warehouse, a user authentication module, a software package upload and index creation module, a baseline release management module, an authorization management module, a retrieval and download software package module, and an adapter Plugins, storage layers. Software package management system, including authentication module, package management service module, web front-end module, command line tool module. The present invention can be connected to various object storage services and software warehouses through plug-in methods, thereby realizing cross-platform, multi-language software package management; adding authentication and software authorization functions, so that users can use the software developed by the company It is convenient to authorize the use of partners, making the way of software distribution more concise; adding the baseline management function, making the software release easier, and improving the collaboration efficiency of internal developers in the development of different software packages of the same software system.
Owner:SHENZHEN JINGTAI TECH CO LTD
Coding and decoding device and method for routing inspection information exchange
PendingCN114120466APrevent counterfeitingReduce logging operationsChecking time patrolsCharacter and pattern recognitionOutput deviceMobile device
The invention relates to a coding and decoding device and method for routing inspection information exchange. The inspection system solves the problems that an inspection system in the prior art is poor in safety and inconvenient to operate. The local device can read field system or equipment information through a network interface, the local device is installed at a position or equipment to be inspected, and the handheld mobile device is connected and communicated with an inspection system through a wireless network. And signal output between the local fixed device and the handheld mobile device is executed by the signal output device, and signal reading is executed by the signal reading device. The invention has the advantages of convenient operation process and safe use.
Owner:浙江嘉科电子有限公司
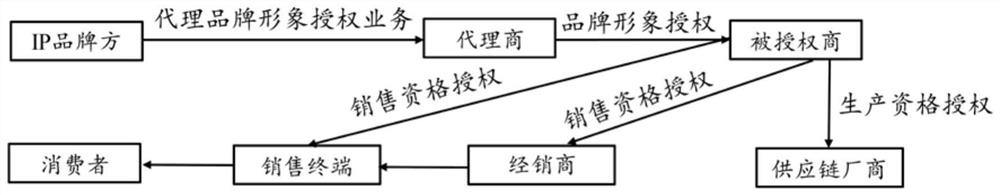
E-commerce platform and method based on profit distribution
PendingCN111967989AImprove data securityHigh data reliabilityFinancePayment protocolsNetwork connectionChain network
The invention discloses an e-commerce platform and method based on profit distribution, relates to the technical field of e-commerce platforms, aims to solve the problem that an existing e-commerce platform is difficult to solve the problem of accurate profit distribution on a service chain of authorized derivatives, and provides the following technical scheme that the e-commerce platform based onprofit distribution comprises an authorization system, a traceability system, a transaction system and a profit sharing system which are all connected with a block chain network; the authorization system is used for service authorization from upstream main bodies to downstream main bodies on a service chain of IP derivatives. The traceability system is used for tracking circulation information ofan IP derivative on a service chain of the IP derivative. The transaction system is used for realizing online and / or offline transaction of IP derivatives; and the profit sharing system is used for carrying out profit distribution according to the circulation information and a preset profit sharing rule.
Owner:广州原仓信息科技有限公司
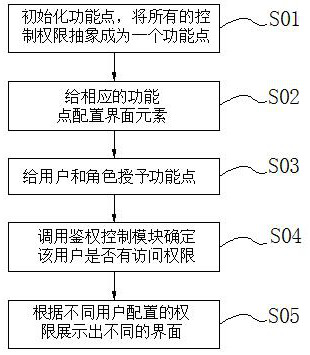
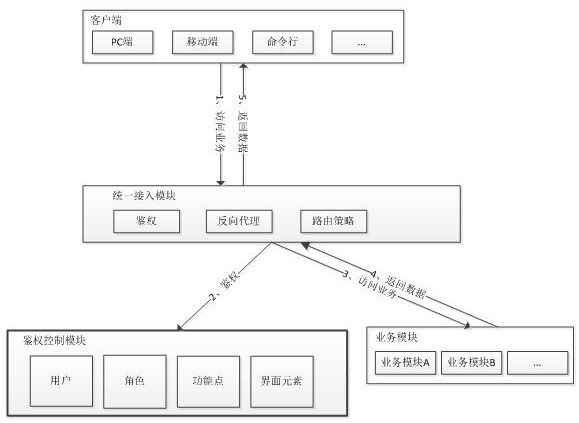
A permission control method and system for multi-terminal sharing
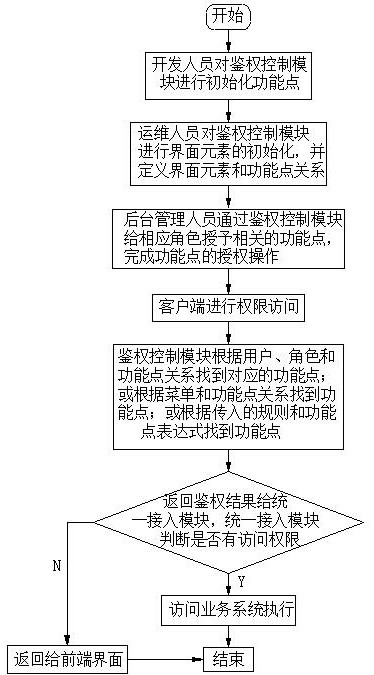
ActiveCN107257337BConvenient authorizationSimple designSoftware engineeringProgram loading/initiatingSpecific functionEngineering
The invention discloses a multi-terminal shared authority control method and system thereof, including four parts: a client, a unified access module, an authentication control module, and a business module. The control method includes initialization function points, and abstracts all control authority Become a function point, which represents a specific function or service; configure interface elements for corresponding function points, define the interface elements corresponding to specific function points, interface elements and display are related to the expression of specific interfaces, and are associated with specific display terminals , the display terminal is a carrier for displaying the interface; authorization, granting function points to users and roles, so that users and function points are associated; authority control, calling the authentication control module to determine whether the user has access rights. The present invention only assigns functional rights to roles by configuring the relationship between rights and interface elements, so that multiple terminals can share the same rights once authorized, without separate authorization for each terminal, and the operation mode is simple.
Owner:重庆扬讯数字科技股份有限公司
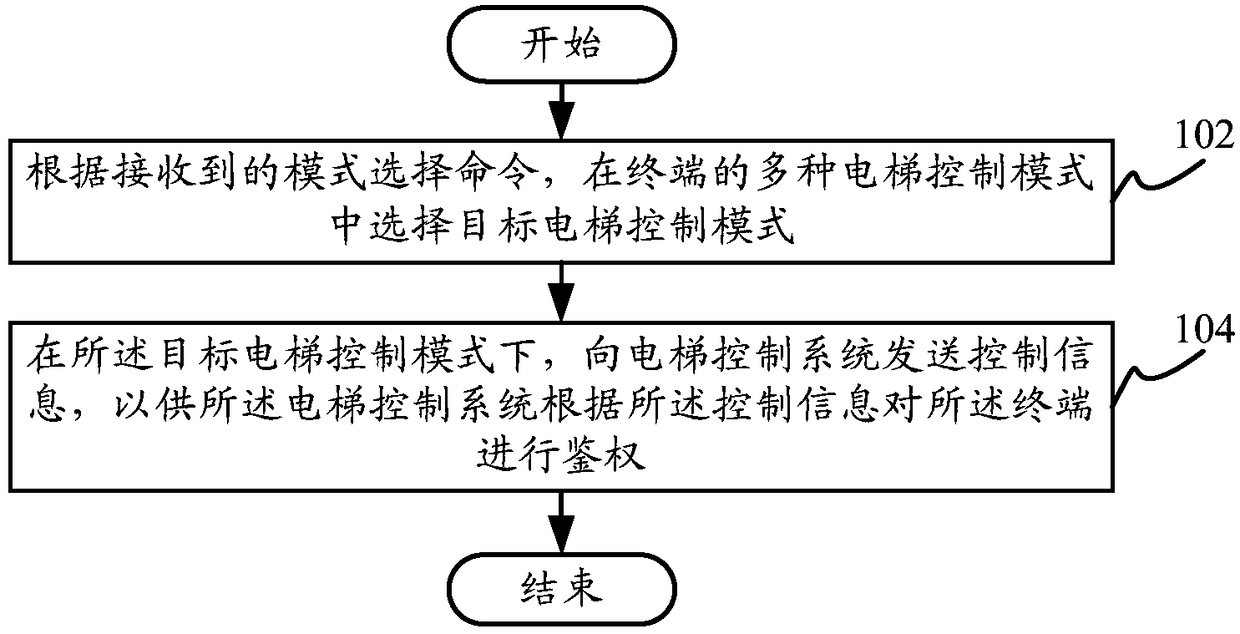
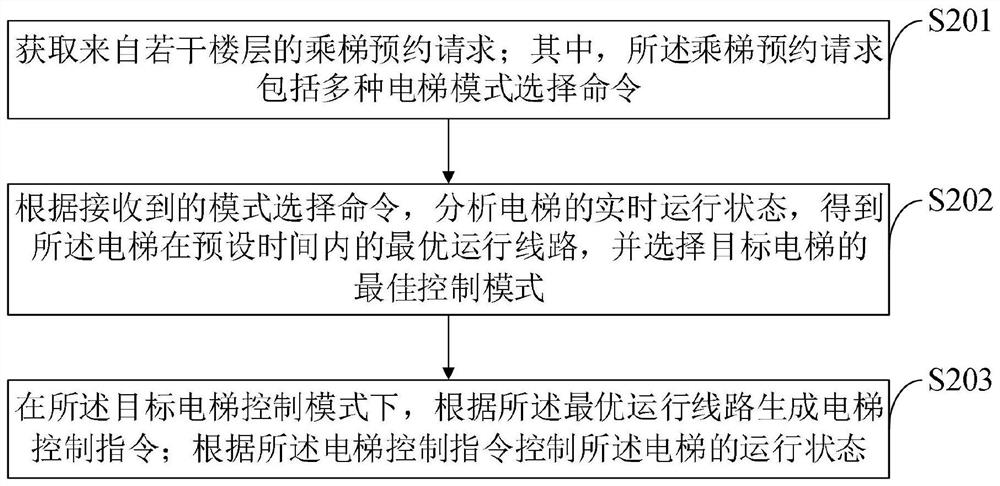
Elevator control method, elevator control device and terminal
Disclosed are an elevator control method, an elevator control device and a terminal. The elevator control method comprises: according to a received mode selection command, selecting a target elevator control mode from a plurality of elevator control modes of a terminal; and sending control information to an elevator control system in the target elevator control mode, for the elevator control system to authenticate the terminal according to the control information. In the control method, an elevator can be manipulated by means of a terminal, thereby avoiding the occurrence of a situation in which the elevator cannot be used due to the fact that a user does not carry an elevator card, and at the same time, facilitating the user to authorize a terminal of a temporary visitor, so that the temporary visitor can use the elevator temporarily, and thus, not only is the safety of use and manipulation of the elevator improved, but also the safety of elevator authentication is guaranteed, and the user experience is improved.
Owner:DONGGUAN COOLPAD SOFTWARE TECH
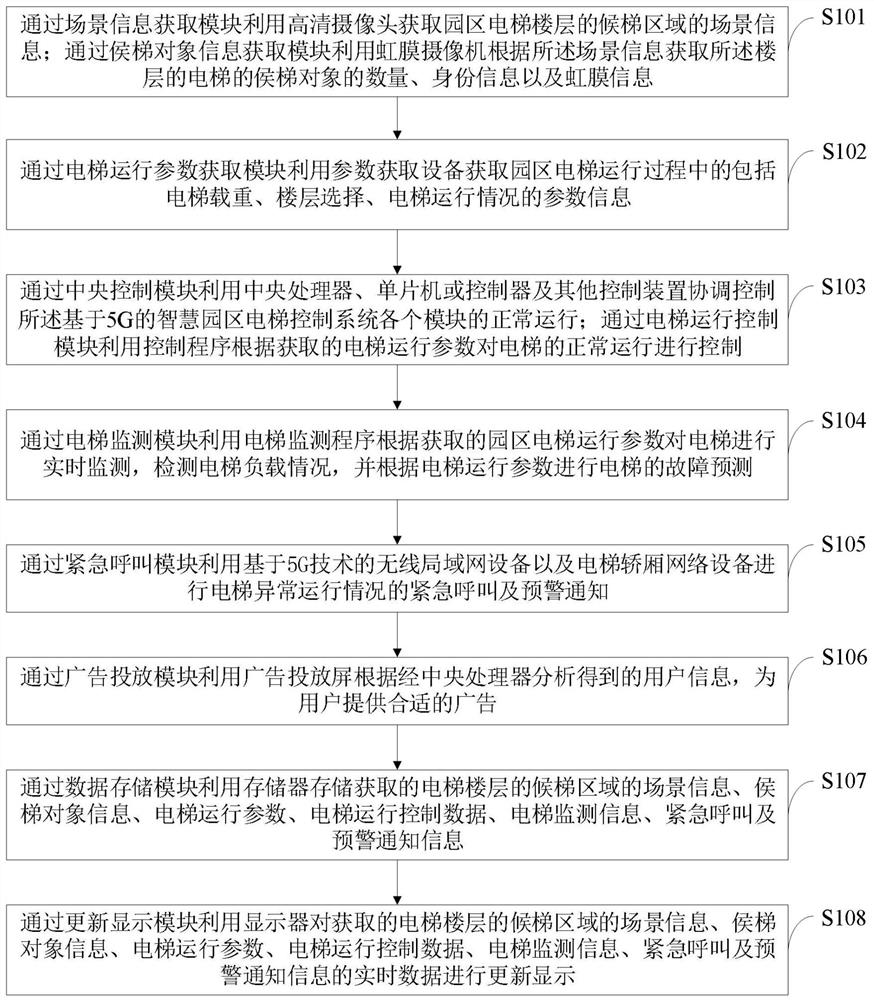
Smart park elevator control method and control system based on 5G
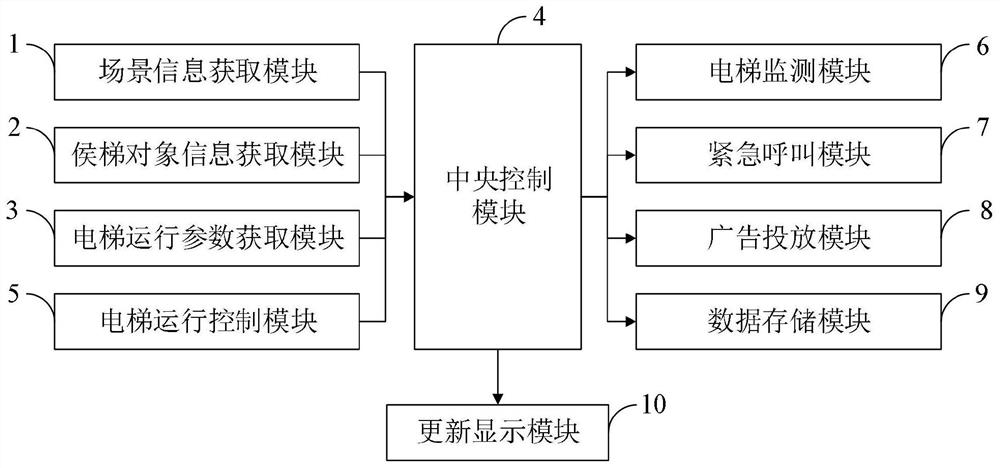
PendingCN112960497AReasonable controlImprove securityNeural architecturesElevatorsFrequency changerControl system
The invention belongs to the technical field of elevator control, and discloses a smart park elevator control method and control system based on 5G. The smart park elevator control system based on 5G comprises a scene information acquisition module, an elevator waiting object information acquisition module, an elevator operation parameter acquisition module, a central control module, an elevator operation control module, an elevator monitoring module, an emergency call module, an advertisement putting module, a data storage module and an update display module. The elevator operation control module provides selection of multiple elevator operation modes, the situation that a user cannot use an elevator due to the fact that the user does not carry an elevator card is avoided, the user can conveniently authorize a terminal of a temporary visitor, the safety of using and controlling the elevator is improved, the safety of elevator authentication is guaranteed, and the user experience is improved; and the elevator load condition is detected, the actual current of a frequency converter is read, the actual load weight of the elevator is calculated, and the elevator can be controlled more reasonably.
Owner:HUNAN HAILONG INT INTELLIGENT TECH CO LTD
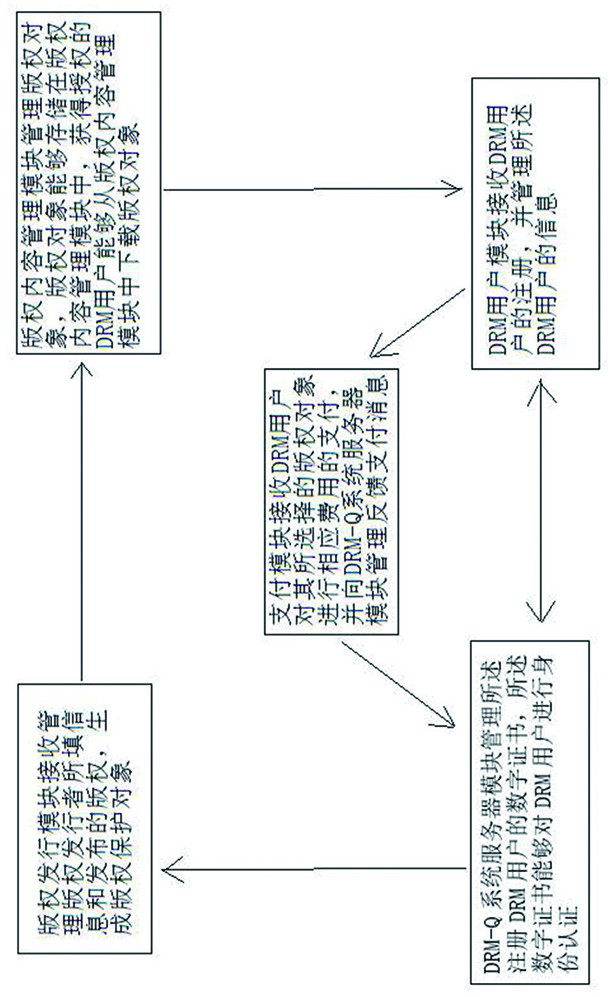
drm-q digital copyright protection method and system
ActiveCN107506619BExempt purchaseNo maintenance feeProgram/content distribution protectionInternet privacyEngineering
The invention relates to the field of communication, in particular to a DRM-Q digital right management method and system. The system comprises a DRM user management module, a right issue module, a DRM-Q system server module, a digital certificate, a right content management module and a payment module, wherein the DRM user management module can store and manage information of a DRM user and send registration information of the DRM user to the DRM-Q system server module; the right issue module receives and manages information filled up by a right issuer and a right issued by the right issuer and generates a right protection object; the DRM-Q system server module receives a request of the DRM user and generates the digital certificate according to the information of the registered DRM user; the digital certificate can provide a secret key for encryption and / or decryption of the right object; the right content management module receives, stores and manages the encrypted right object; and the payment module is used for receiving cost paid by the registered DRM user for the ordered right objet. The system can be seamlessly compatible with a mainstream media player and an electronic reader on the market; and when encrypted data is opened, interception, authentication and authorization are completed in one step, so that comprehensive protection is effectively provided for the digital right.
Owner:创元网络技术股份有限公司
System and method for network accession utilizing single clicking single pointing
InactiveCN100534094CSimplify Management ComplexityEasy to useUser identity/authority verificationData switching by path configurationIp addressUser management
Owner:王伟珣
A remote authorization method for access control
ActiveCN104123777BEnsure safetyRealize remote communicationIndividual entry/exit registersTransmissionAuthorizationInformation acquisition
The invention relates to the field of safety protection, and in particular relates to an access control remote authorization method which comprises the following steps of acquiring information to be authorized by a control unit, and encrypting the information to be authorized by combining information acquisition time to form first encrypted information; sending the first encrypted information into an authorization unit by the control unit; decrypting the first encrypted information by the authorization unit to form first decrypted information, and confirming the first decrypted information; encrypting the first decrypted information by combining the confirmation information by the authorization unit to form second encrypted information, and sending the second encrypted information into the control unit; decrypting the second encrypted information by the control unit to form second decrypted information, and confirming the information by verification; and executing access control remote authorization operation. According to the access control remote authorization method, an encryption module and a communication module are arranged in the control unit and the authorization unit, respectively, so that the safety of the information to be authorized is guaranteed in the communication process, and the remote communication between the control unit and the authorization unit can be realized.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Article management and control system
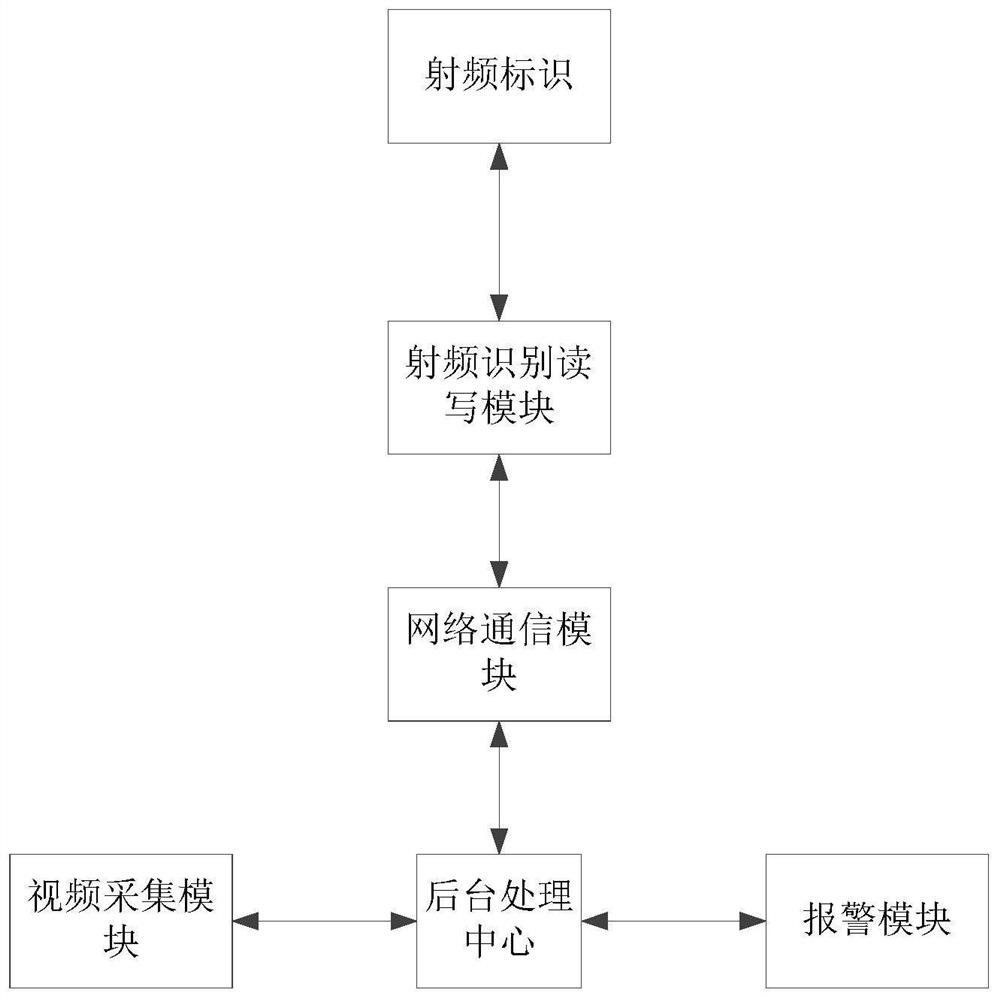
PendingCN112150737AImprove intelligenceHigh degree of automationCo-operative working arrangementsCash registersComputer hardwareControl system
The invention relates to the technical field of article management and control, and discloses an article management and control system. The article management and control system comprises a radio frequency identifier arranged on a managed and controlled article, a radio frequency identification read-write module fixedly or movably arranged, a background processing center, an alarm module and videoacquisition module, wherein the background processing center comprises a memory and a processor; the alarm module is used for carrying out sound-light alarm according to a control instruction; and the video acquisition module is used for acquiring an image of a to-be-verified managed and controlled article, processing the image and sending data to the background processing center. According to the system, the problem that management and control articles are difficult to identify and manage in the circulation process is effectively solved, the anti-counterfeiting effect is effectively ensured,and the management system is intelligent, high in automation degree and relatively wide in application.
Owner:湖南聚沙信息技术有限公司
Rotary dial type self-generating combination lock
InactiveCN106836997ATo achieve long-term continuous workConvenient authorizationNon-mechanical controlsElectric permutation locksGeneral Packet Radio ServiceMicrocontroller
The invention discloses a rotary dial type self-generating combination lock. The combination lock comprises a locking bar, an upper lock formed by a locking tongue connected with a motor as well as an unlocking assembly, wherein two ends of the locking bar are mounted at two ends of the top of a casing respectively; the combination lock further comprises a dial assembly, a generating assembly, a gear potentiometer, a control circuit board and a rechargeable battery, a round dial of the dial assembly is mounted right below the casing, and the generating assembly, the gear potentiometer, the control circuit board and the rechargeable battery are fixed in the casing respectively. Unlocking code input and a generating process are integrated; the combination lock can be remotely connected with a cloud service center through family wifi or GPRS (general packet radio service) directly to facilitate authorization, monitoring and management; by means of a logical operation function of a low-power-consumption single chip microcomputer in the control circuit board, a dynamic password unlocking mode and a virtual-position password unlocking mode can be supported, and the combination lock can also be matched with a fingerprint unlocking module, a magnetic card unlocking module and the like through a single chip microcomputer serial port and the like; the combination lock can be applied to residence buildings and private or shared vehicles such as bicycles, storage battery cars and the like.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY
Graphic engine authentication detection method and system applied to embedded terminal
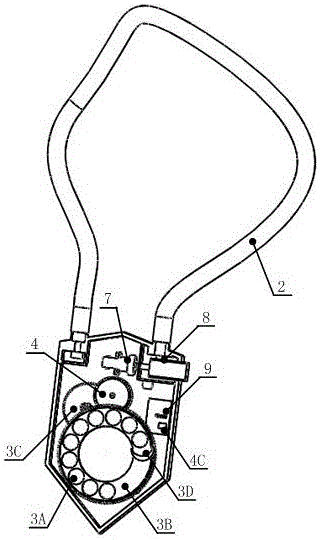
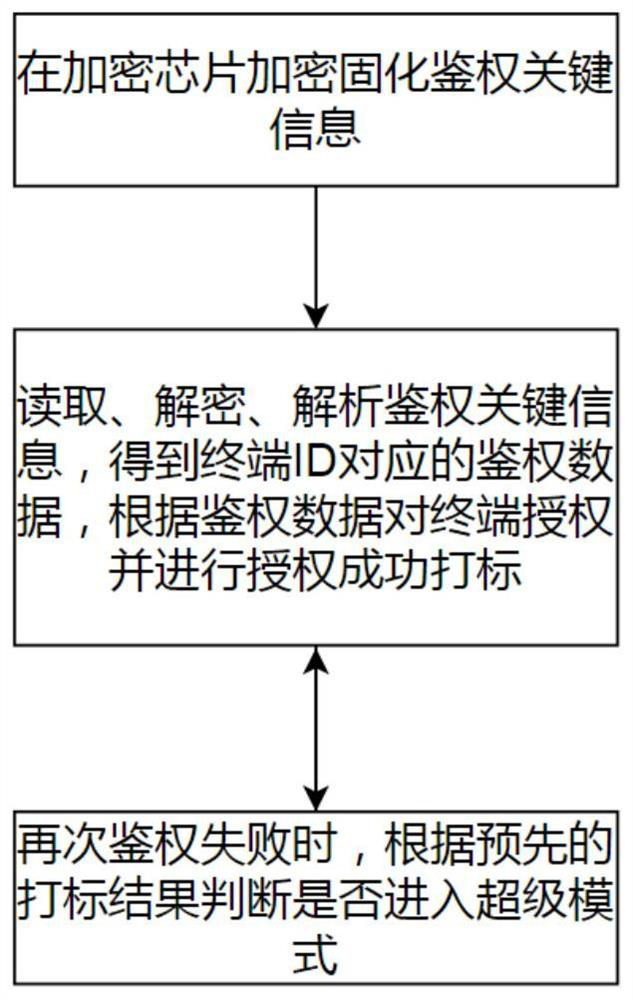
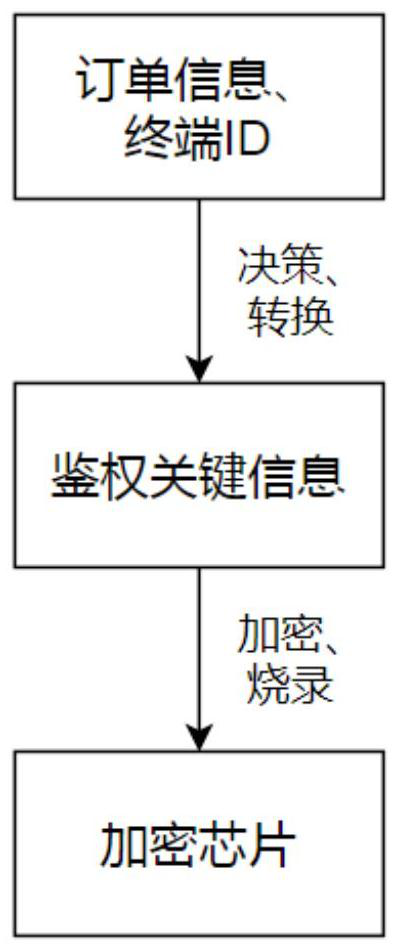
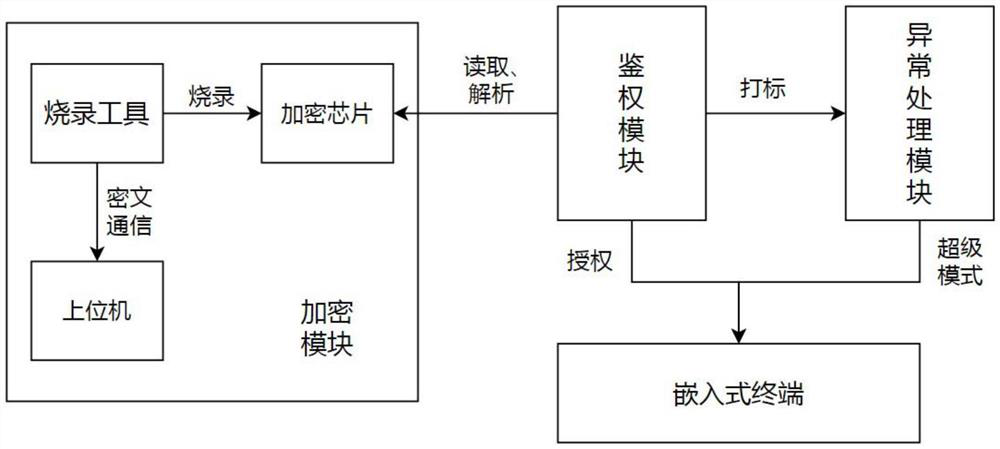
PendingCN114861156AConvenient single authorizationAvoid lostDigital data authenticationGraphicsEmbedded system
The invention relates to a graphic engine authentication detection method and system applied to an embedded terminal. The method comprises the following steps: encrypting and solidifying authentication key information in an encryption chip; reading and decrypting the encrypted and solidified authentication key information in the encryption chip, analyzing the authentication key information to obtain a terminal ID and authentication data, granting a corresponding graphic engine system permission to the current terminal according to the authentication data, and marking the successfully authorized terminal; when the authentication is abnormal again, whether the terminal enters a super mode or not is judged according to a pre-marking result of the current terminal, and the super mode is that the graphic engine works normally and the authentication is reminded to be abnormal. According to the method, the detection of the authentication abnormity of the graphic engine software is effectively realized, the safety is good, and the loss caused by the fact that the software cannot be used when the environment such as hardware abnormally suddenly occurs is avoided.
Owner:WUHAN BLUESTAR TECH CO LTD
An authorization method, client, server and system
The invention discloses an authorization method, a client-side, a server and a system, relates to the technical field of internet and mainly aims at solving the problem that the operating process is complicated during authorization of an authorization object (control lock) in the prior art and achieving the authorization step of the authorization object. According to the main technical scheme, the authorization method comprises the steps that server generates authorization identification information according to registration information on the client-side; request information for acquiring the authorization identification information sent by the client-side is received; responding to the request information, the authorization identification information is sent to the client-side so that the client-side conducts authorization on the authorization object according to the authorization identification information.
Owner:BEIJING SENSESHIELD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com