Graphic engine authentication detection method and system applied to embedded terminal
An embedded terminal and graphics engine technology, applied in the direction of digital data authentication, etc., can solve problems such as insufficient security and inability to effectively realize single authentication, and achieve the effect of avoiding losses and convenient authorization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The principles and features of the present invention will be described below with reference to the accompanying drawings. The examples are only used to explain the present invention, but not to limit the scope of the present invention.
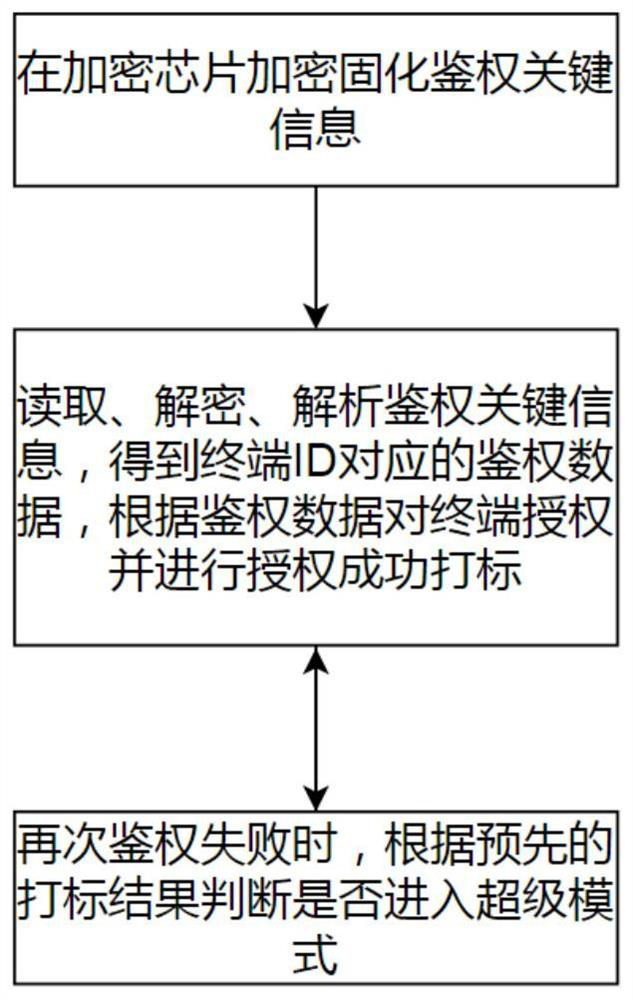
[0029] figure 1 This embodiment provides a flowchart of a graphics engine authentication detection method applied to an embedded terminal. like figure 1 As shown, a graphics engine authentication detection method applied to an embedded terminal provided by this embodiment includes:
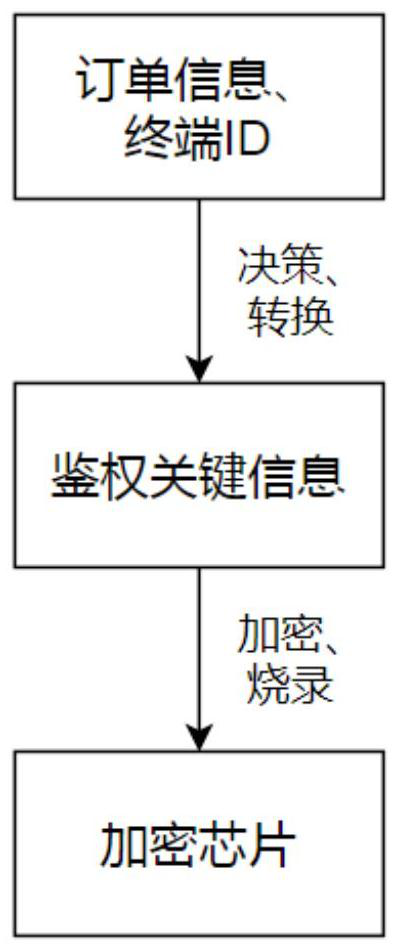
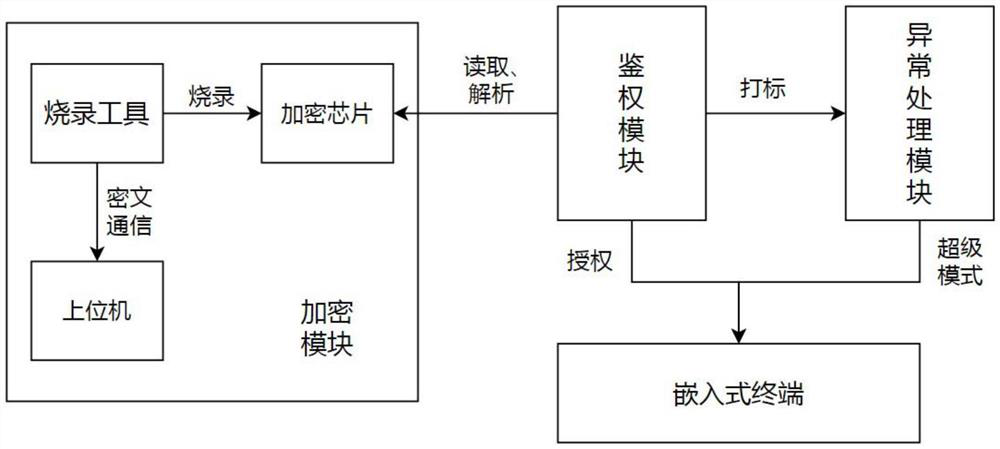
[0030] Authentication step: read and decrypt the key authentication information encrypted and solidified in the encryption chip, parse the key authentication information to obtain the terminal ID and authentication data, grant the corresponding graphics engine system usage authority to the current terminal according to the authentication data, and The terminal that is successfully authorized is marked;
[0031] Abnormal handling steps: when an abnormalit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com