Authentication method, device and system and computer storage medium
A storage layer and mapping relationship technology, applied in the field of authentication and authentication, can solve the problems of cumbersome operation, complex management, data security, etc., and achieve the effect of reducing concurrent peak overhead, improving business efficiency, and reducing the risk of leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] see figure 1 , this embodiment introduces the application scenario of this method by taking a homestay managed remotely as an example.
[0036] An authentication authentication method, which is applied to a local network device, the local network device includes a gateway or a home router, and the local network device includes a storage layer for storing data, a configuration management layer for management configuration, and a service processing layer Business logic layer.
[0037] Authentication authentication methods include:
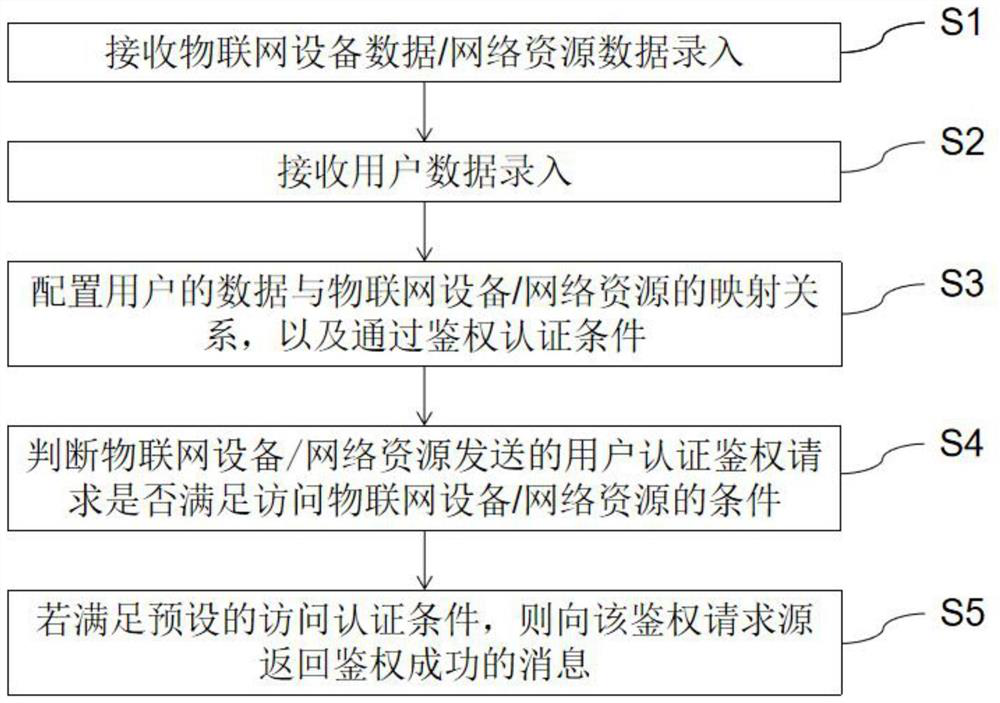
[0038] S1: Receive IoT device data entry.
[0039] Specifically, the IoT device data specifically includes one or more of device identification code, name, device attribute, mac, and public key.
[0040] S2: Receive user data input.
[0041] User data includes one or more of identity information, passwords, and biometric data. When a user needs to stay in the store, create a user data entry transaction, generate the information entry page...
Embodiment 2
[0051] This embodiment introduces the application scenario of the method by taking network resources (such as movies and songs) requiring authentication as examples.
[0052] An authentication and authentication method, the authentication and authentication method is applied to a local network device, the local network device includes a PC or an embedded device (such as NAS), and the local network device includes a storage layer for storing data and a configuration management layer for managing and configuring And the business logic layer for business processing.
[0053] Authentication authentication methods include:
[0054] S1: Receive network resource data entry.
[0055] S2: Receive user data input.
[0056] S3: Configure the mapping relationship between user data and network resources, and pass authentication conditions.
[0057] S4: Determine whether the user authentication request sent by the network resource satisfies the conditions for accessing the network resour...
Embodiment 3
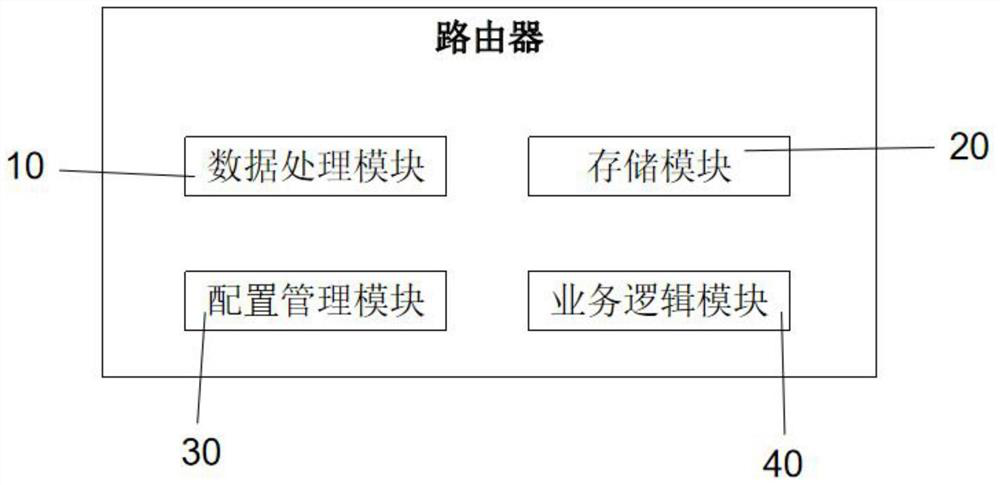
[0059] see figure 2 , an authentication and authentication device, the authentication and authentication device is a local network device, and the local network device includes a gateway, a home router, a PC or an embedded device, and the authentication and authentication device includes:
[0060] The data processing module 10 is used for receiving IoT device data / network resource data entry, user data entry, and addition, deletion, modification, and query of related data;
[0061] The storage module 20 is used to store IoT device data / network resources, user data and mapping relationship data;
[0062] The configuration management module 30 is used to configure the mapping relationship between the user's data and the Internet of Things device / network resource, and pass the authentication and authentication conditions;
[0063] The business logic module 40 is used to judge whether the user authentication request sent by the IoT device / network resource satisfies the condition...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com