System and Method for Platform-Independent Biometrically Secure Information Transfer and Access Control
a biometric and access control technology, applied in the field of biometric verification and security of information transfer, can solve the problems of complex and cumbersome process of exchange, no previously known encryption technology enabled the parties, and no known encryption technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
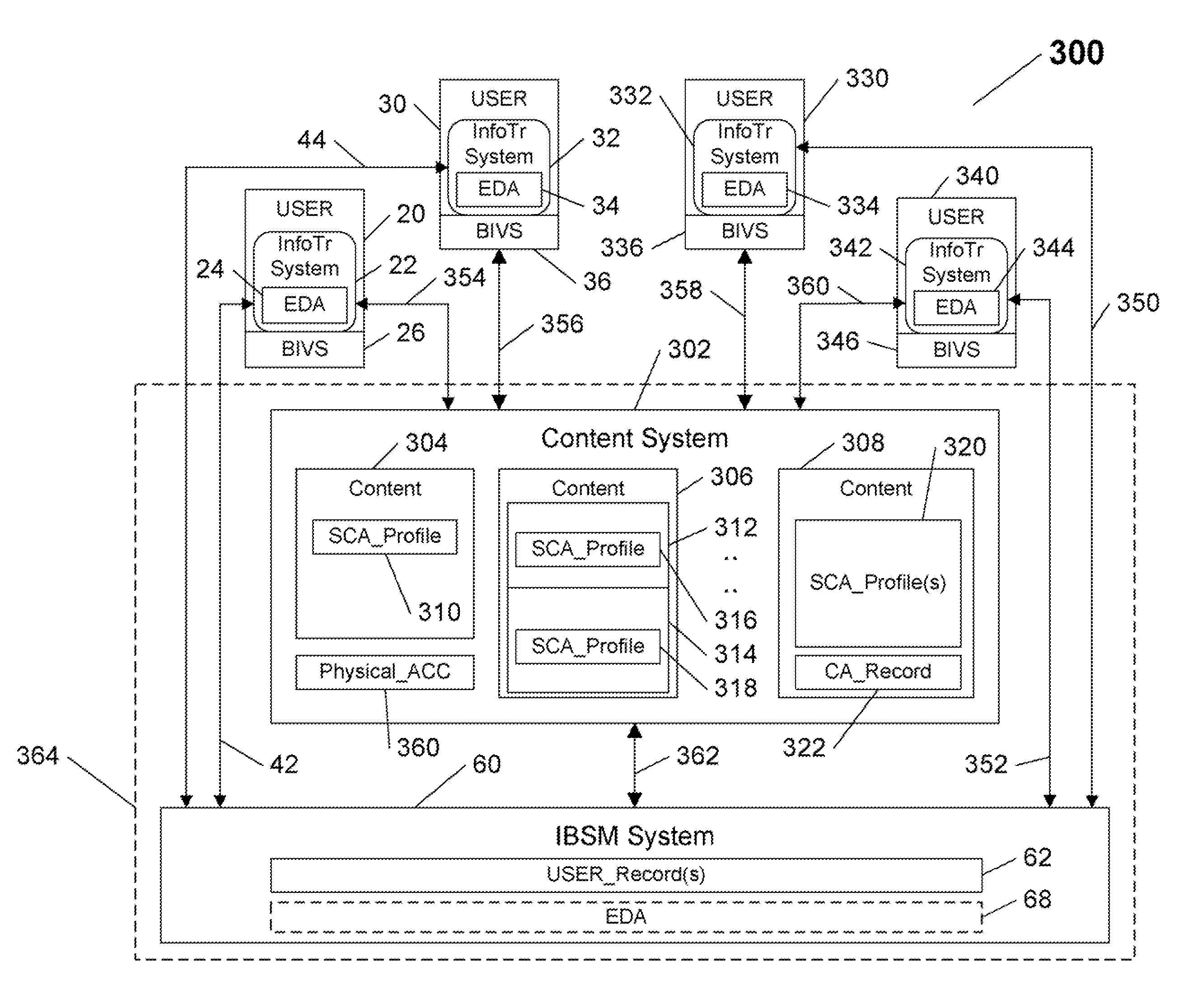
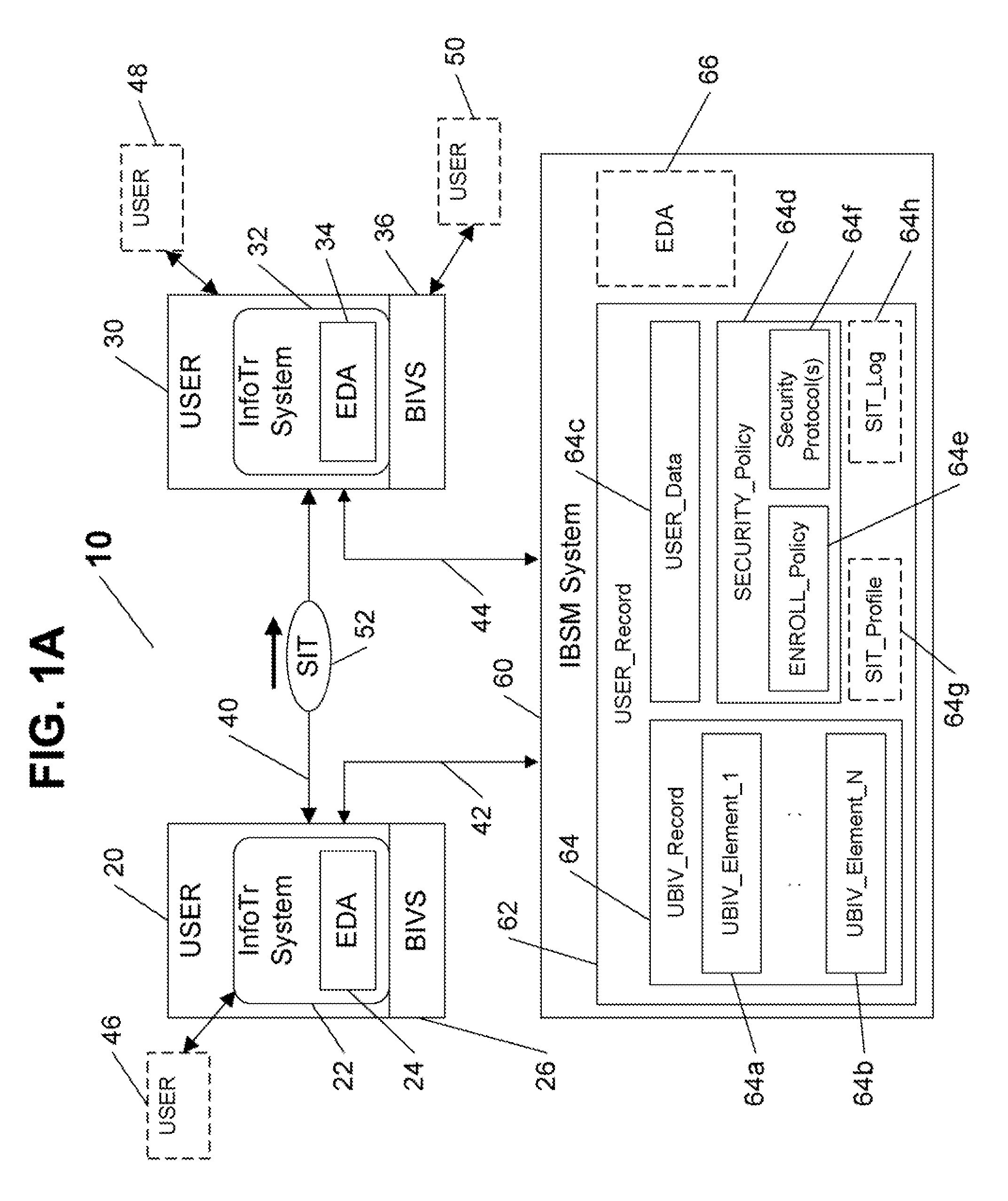
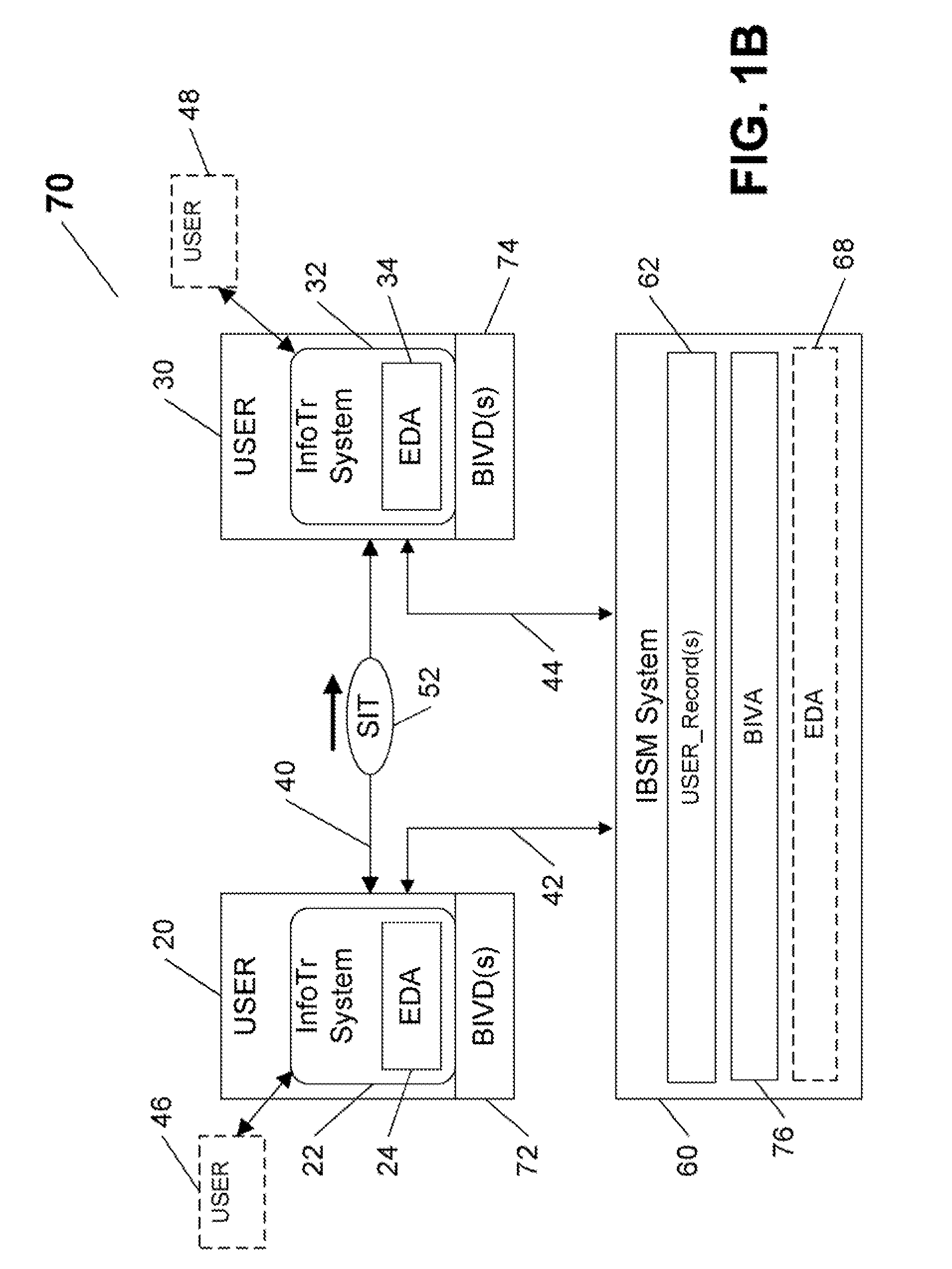
[0044] The system and method of the present invention remedy the disadvantages of previously known biometric solutions directed at verifying and securing information transfer between parties, by providing a platform-independent biometric security management system architecture that enables registered parties to securely transfer information therebetween, and verify the identities of the party enabling the transfer (e.g., by transmission of information, or by enabling secured access to stored information), and / or of the recipient party gaining access to the information (e.g., by receiving the information, and / or by accessing secured stored information), utilizing any biometric identity verification system available, regardless of the type, model, and / or ownership, as long as the utilized biometric system is compatible with one or more of their previously registered multiple biometric enrollments.
[0045] The inventive system and method achieve the above, and other objectives, by enabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com