Dataflow component scheduling using reader/writer semantics
a dataflow and component scheduling technology, applied in multi-programming arrangements, program control, instruments, etc., can solve problems such as data race, unrestricted access to shared mutable states,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
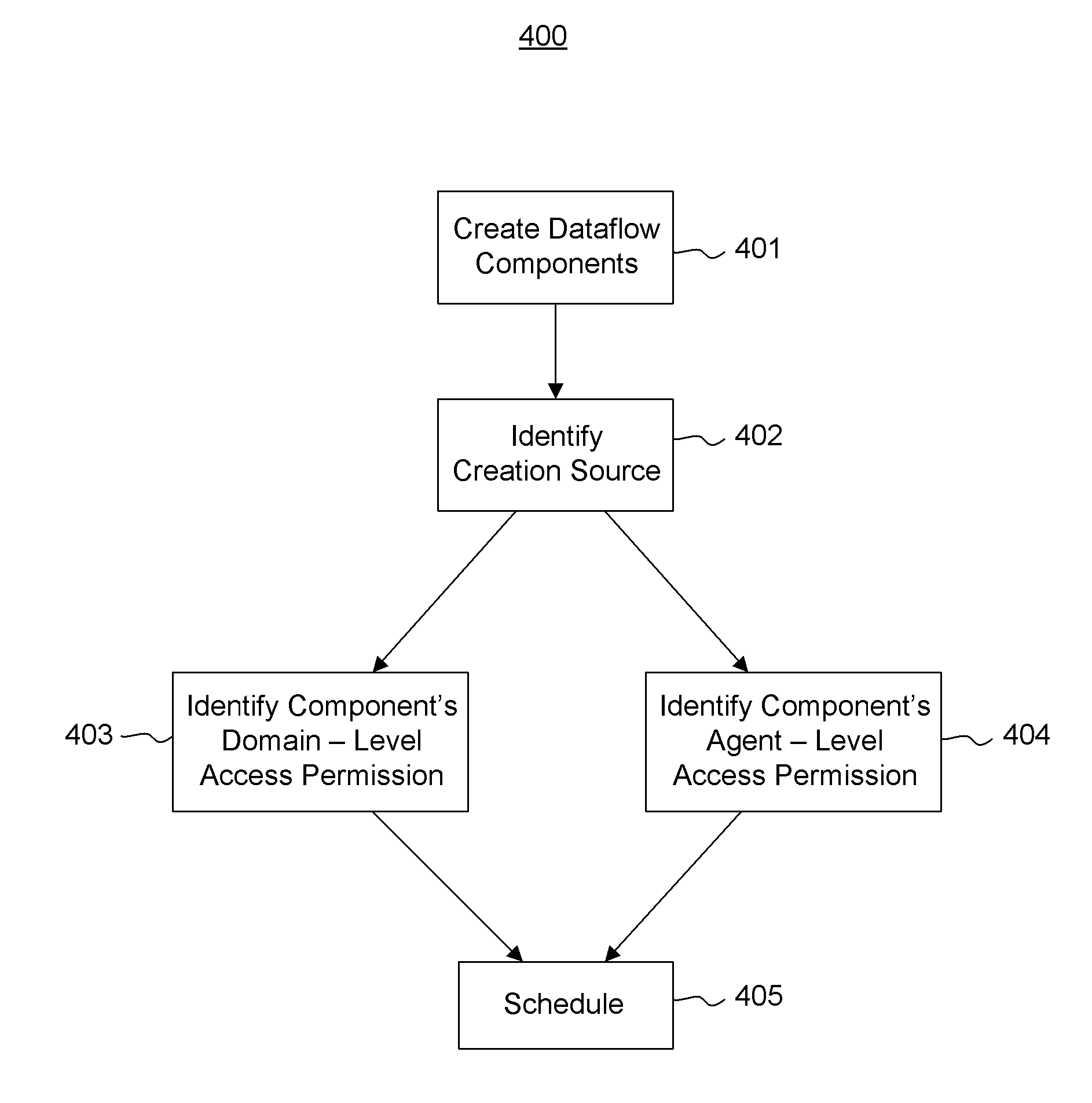
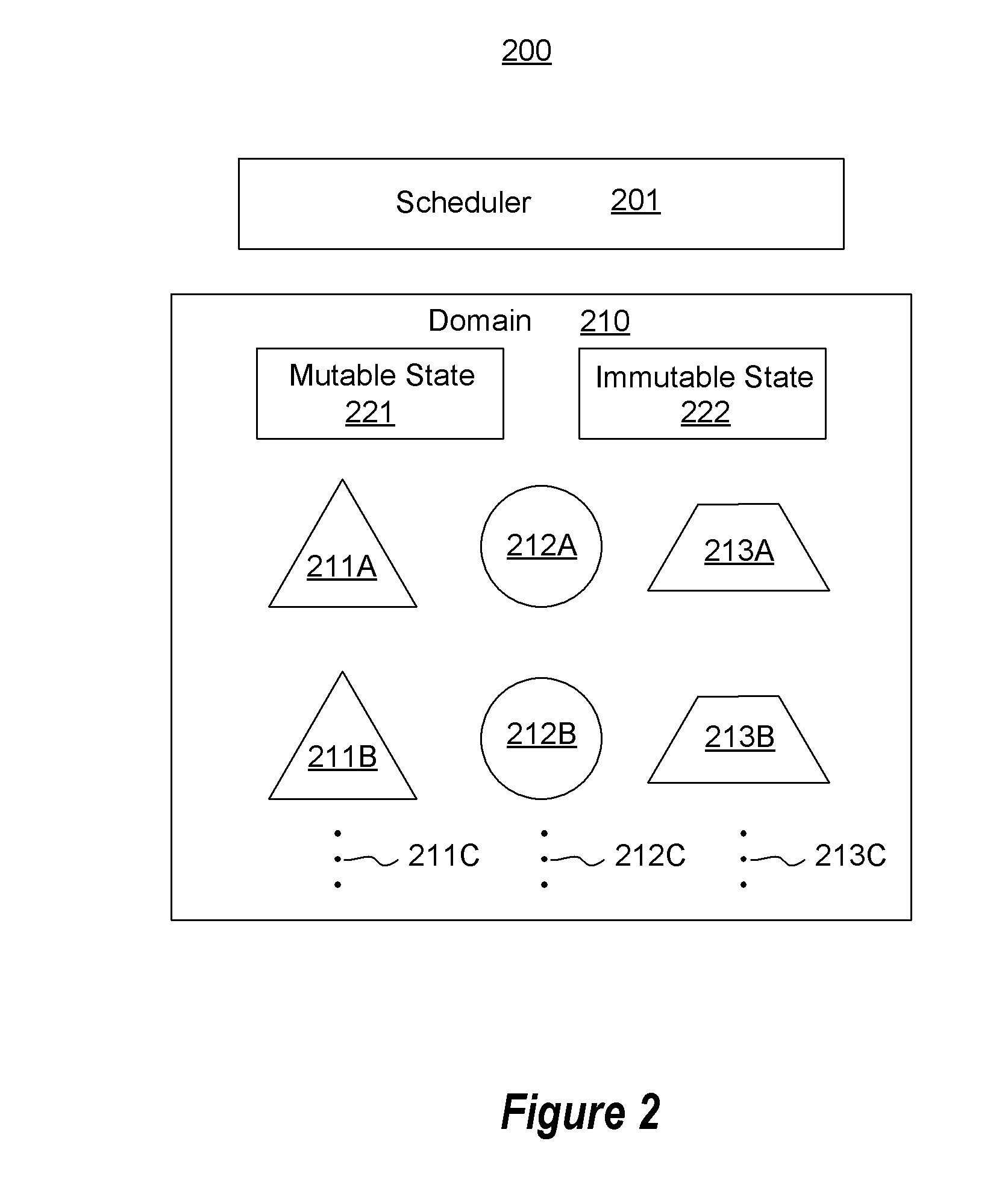
[0014]In accordance with embodiments described herein, the scheduling of dataflow components in a dataflow network is described. A number, if not all, of the dataflow components are created using a domain / agent model. A scheduler identifies, for a number of the components, a creation source for the given component. The schedule also identifies an appropriate domain-level access permission (and potentially also an appropriate agent-level access permission) for the given component based on the creation source of the given component. Tokens may be used at the domain or agent level to control access. First, some introductory discussion regarding computing systems will be described with respect to FIG. 1. Then, various embodiments of the scheduling of dataflow components will be described with reference to FIGS. 2 through 7.
[0015]First, introductory discussion regarding computing systems is described with respect to FIG. 1. Computing systems are now increasingly taking a wide variety of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com