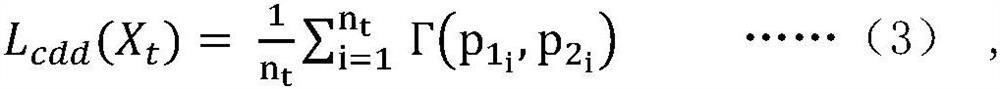Patents
Literature
46results about How to "Identifiable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
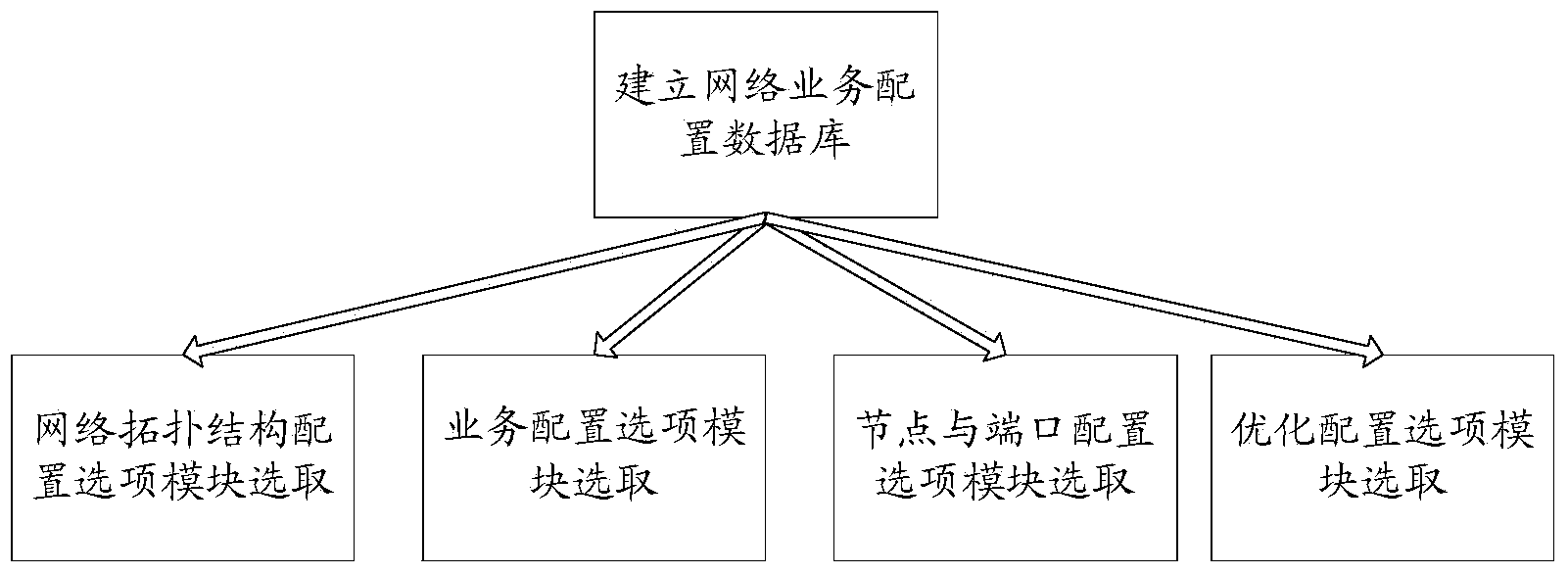
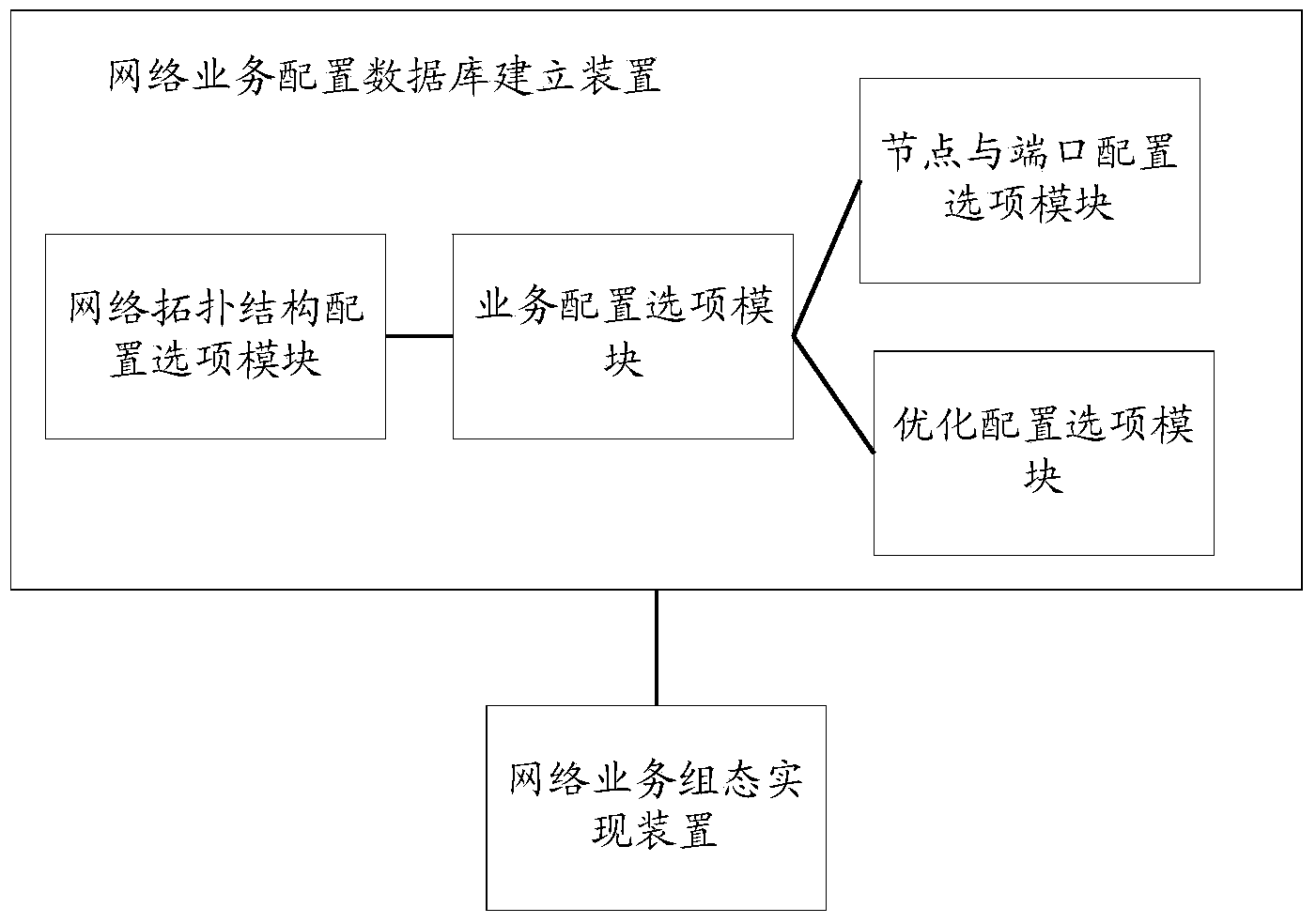
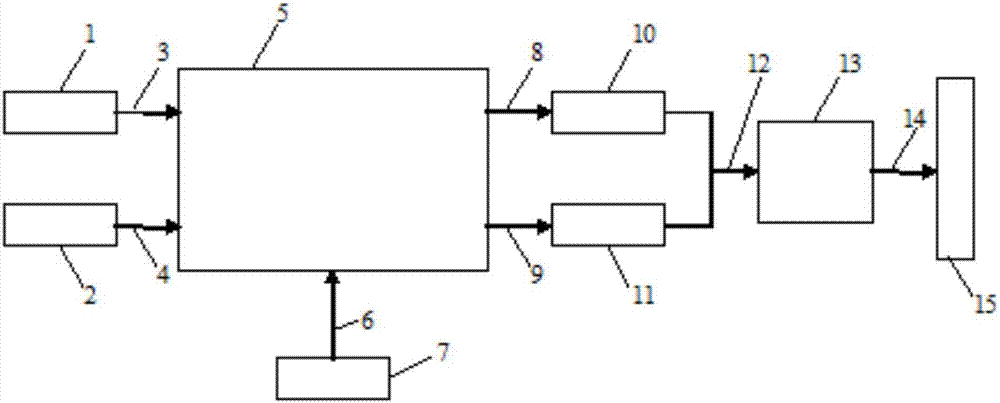
Method and system for implementing configuration on basis of network services
ActiveCN103634177AEfficient self-configuring configurationRapid self-configuration configurationNetworks interconnectionService flowStructure of Management Information
The invention discloses a method and a system for implementing configuration on the basis of network services. The method and the system have the advantages that network service configuration databases are created for users, topological structures, identification of service flows, identification of network devices for carrying the service flows and configuration information of physical ports, VLAN (virtual local area network) selection and the like can be selected from the databases for network topological contents and specific service contents on the basis of network service requirements, accordingly, service types, source MAC (media access control) addresses and target MAC addresses can be identified according to ports for the network devices for carrying the service flows, network topology can be creased on the basis of the identification of the service flows and the configuration information of the ports in the network service configuration databases, the same services can be transmitted in selected VLANs, and the configuration can be implemented; the configuration information can be issued to the various network devices, so that the complexity and the troublesome degree of the network configuration can be lowered, the specific services can be transmitted among the configured networks in an identifiable manner, and network configuration lists are high in reliability.
Owner:KYLAND TECH CO LTD
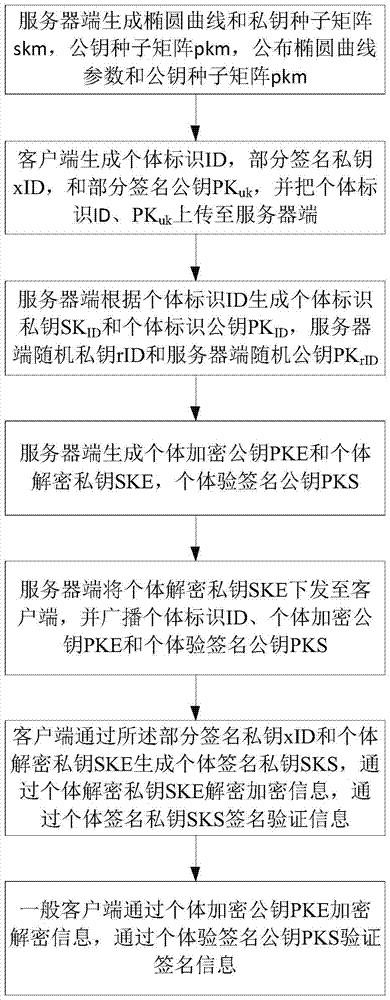
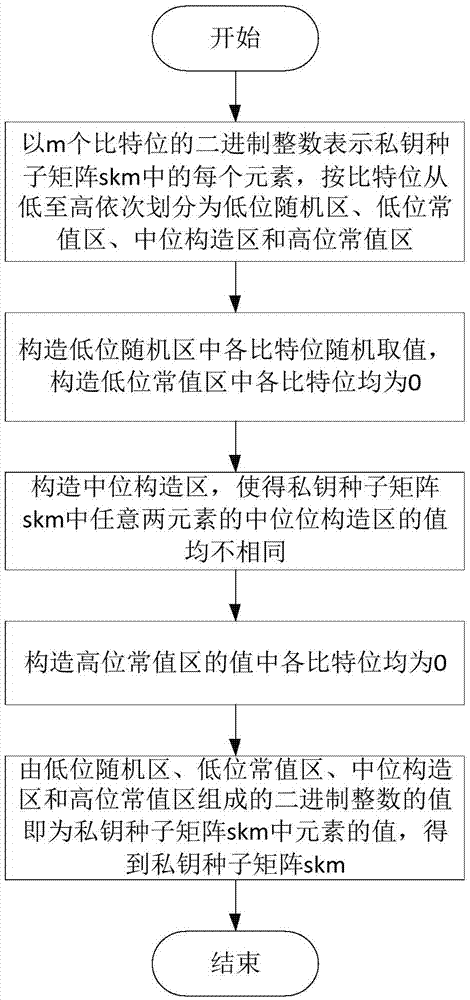
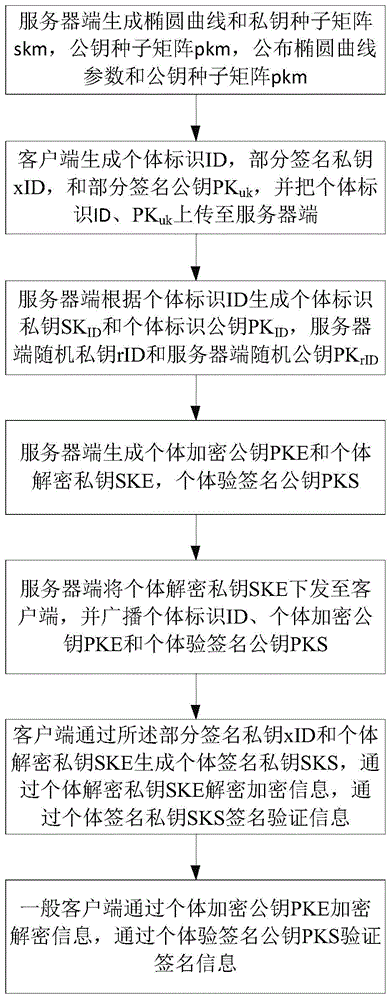
Certificate-free combined secret key generation and application method
ActiveCN105450396ASolve the sum collision problemGuaranteed logo effectKey distribution for secure communicationKey generationNon-repudiation
The invention discloses a certificate-free combined secret key generation and application method. The method comprises the following steps: S1, a server end generating an elliptical curve, skm and pkm, and issuing parameters of the elliptical curve and the pkm; S2, a client generating ID, xID and PKuk, and uploading the ID and the PKuk to the server end; S3, the server end generating SKID, PKID, rID and PKrID; S4, the server end generating PKE, SKE and PKS; S5, the service end issuing the SKE to the client, and broadcasting the ID, the PKE and the PKS; S6, the client generating SKS through the xID and the SKE, and decrypting encryption information through the SKE, and signing verification information through the SKS; and S7, a general client encrypting decryption information and verifying signature information through the PKS. The method provided by the invention solves the problems of non-repudiation of sum bumps, linear collusion and individual signature of a combination public key technology and the like.
Owner:鄂尔多斯市迪曼森密码科技有限公司
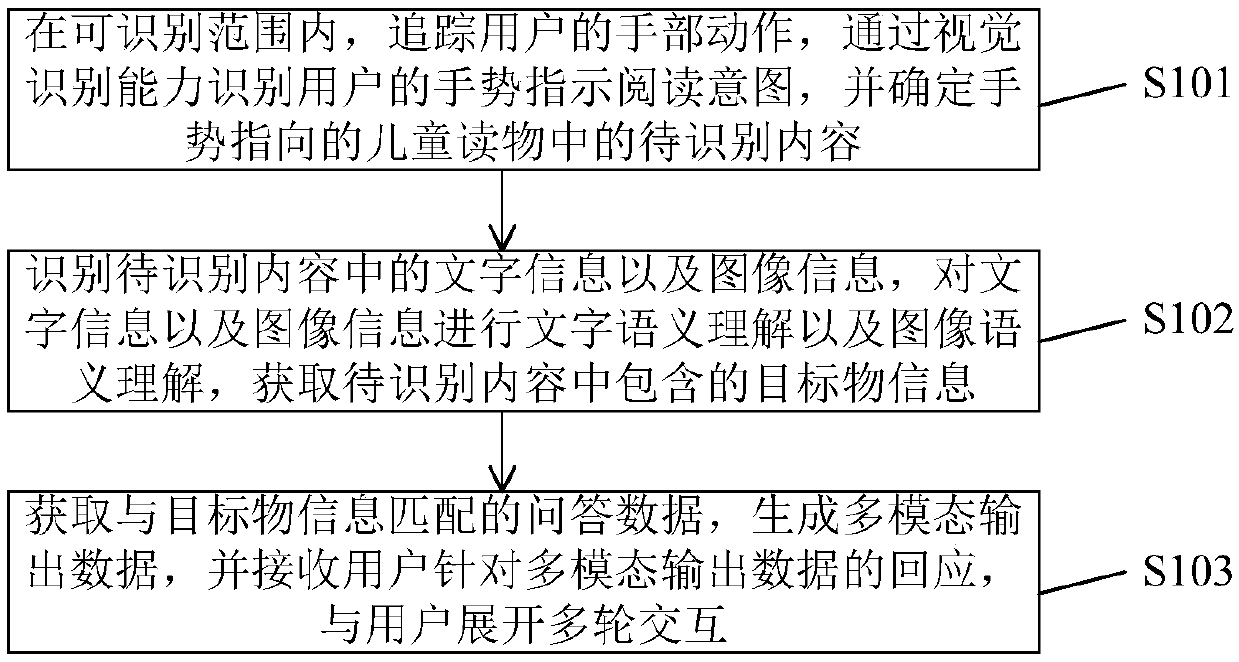
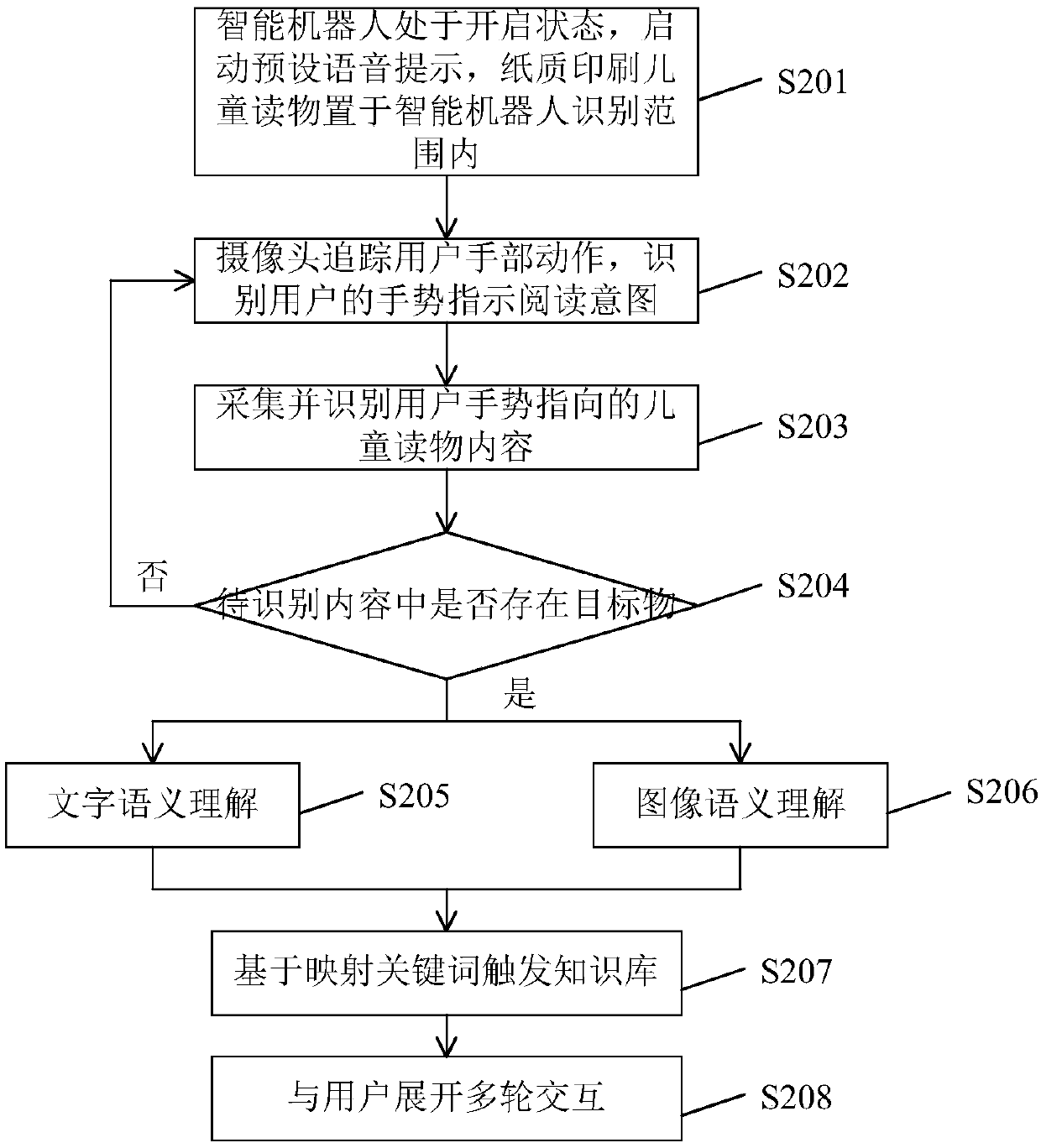
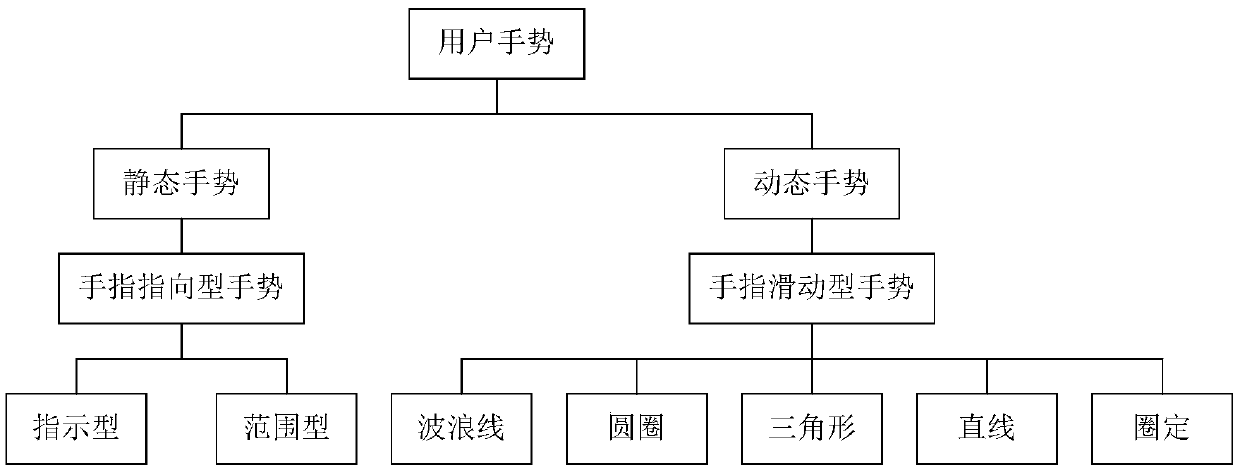
Children reading and interacting method and system based on an intelligent robot
InactiveCN109522835AImprove user experienceReduce reading difficultyCharacter and pattern recognitionTeaching apparatusQuestions and answersVisual perception
The invention provides a child reading and interacting method based on an intelligent robot. wherein the intelligent robot is in an open state to obtain a reading instruction, and the child reading material is placed in an intelligent robot recognition range and comprises the following steps: tracking a hand action of a user in a recognizable range, recognizing a gesture of the user through a visual recognition capability, determining that the gesture has a reading intention, and determining to-be-recognized content in the child reading material to which the gesture points; Identifying text information and image information in the to-be-identified content, and performing text semantic understanding and image semantic understanding on the text information and the image information to obtaintarget object information contained in the to-be-identified content; And obtaining question and answer data matched with the target object information, generating multi-modal output data, receiving aresponse of the user to the multi-modal output data, and performing multi-round interaction with the user. The gesture of the user can be recognized, the content of the child reading material pointedby the gesture of the user is read, the use experience of the user is improved, and the reading difficulty of the child user is reduced.
Owner:BEIJING GUANGNIAN WUXIAN SCI & TECH
Vehicle owner contacting method and system with function of protecting privacy of vehicle owner
ActiveCN105049406APrivacy protectionImprove effectivenessCo-operative working arrangementsData switching networksMobile Telephone NumberMobile device
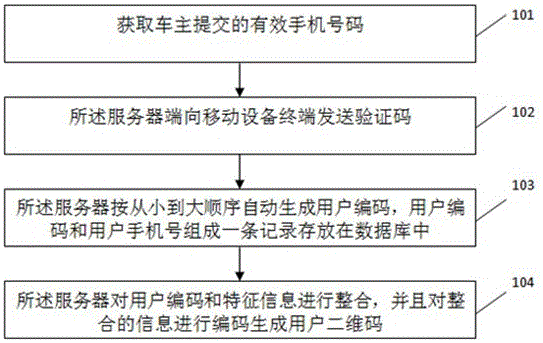
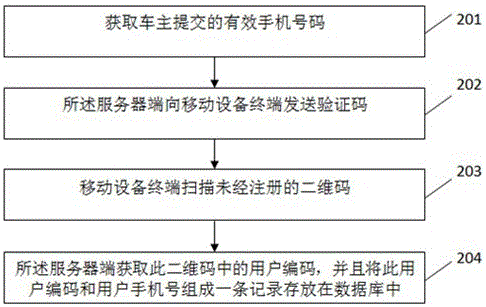
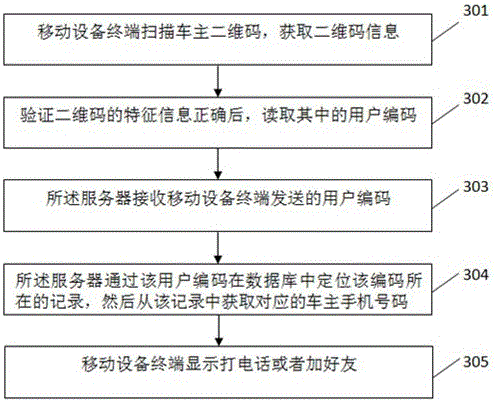
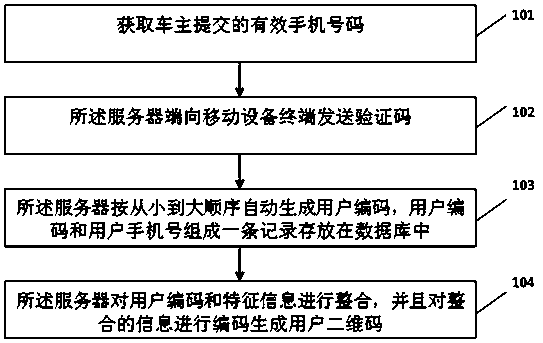
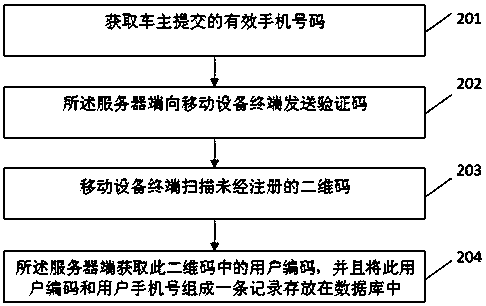
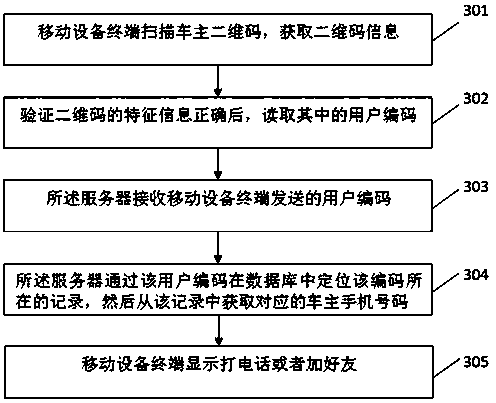
The invention discloses a vehicle owner contacting method and system with a function of protecting the privacy of a vehicle owner, and the method comprises the steps that a server obtains the information of the vehicle owner, and transmits a verification code to a cellphone number submitted by the vehicle owner; a mobile equipment terminal receives the verification code and submits the verification code to the server; the server automatically generates a user serial number; the server enables the user serial number and the cellphone number to form a record stored in a database; the server carries out coding and generates a user two-dimensional code; the mobile equipment terminal scans the user two-dimensional code, verifies the information, and enables the user serial number to be submitted to the server; the server obtains the corresponding cellphone number of the vehicle owner through the positioning of the user serial number in the database; and the mobile equipment terminal carries out the call of a dialing function of a cellphone, and builds the communication connection between the mobile equipment terminal and the vehicle owner. The method and system can achieve the contact with the vehicle owner with no need to expose the telephone number of the vehicle owner, and protect the privacy of the vehicle owner. The vehicle owner can automatically print the generated two-dimensional code, are convenient and quick, also can employ a made exquisite two-dimensional code, and facilitate the drawing of attention.
Owner:OCEAN UNIV OF CHINA
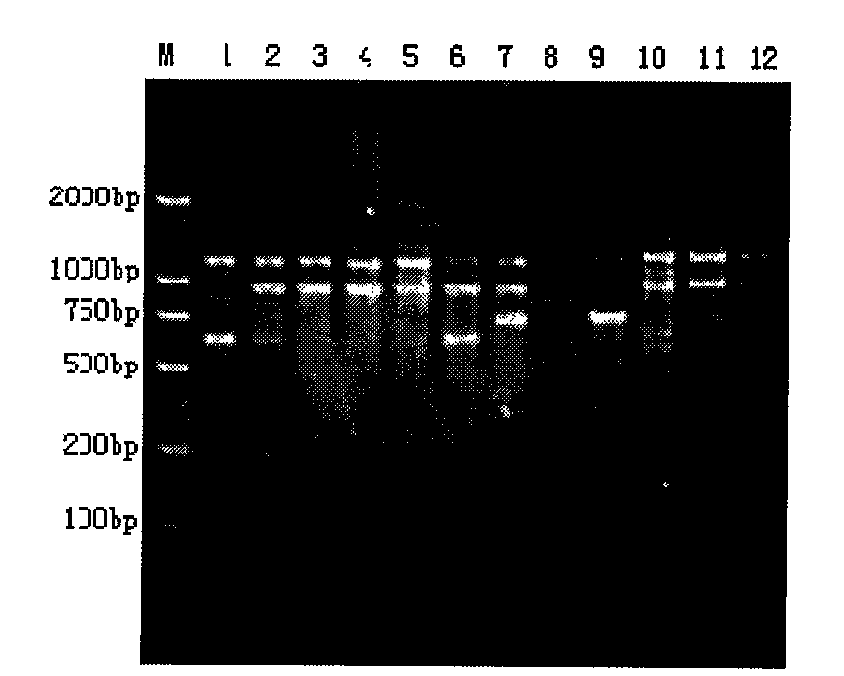
Identification method for quickly detecting purity and truth of rice seeds
InactiveCN101586163ASimple methodEasy to operateMicrobiological testing/measurementAmplification dnaDependability
The invention discloses an identification method for quickly detecting purity and truth of rice seeds. The method comprises the following steps of firstly extracting the DNA of a sample; and then, performing PCR amplification detection on the extracted DNA by an SCAR marker in the patent; and finally, comparing and analyzing the amplified DNA segment. The marker in the invention is used for identifying the purity and truth of rice seeds, not only has the basic characteristics of environmental stability, identifiability of inter-variety variation, smallest intra-variety variation and reliability of experimental result, but also has the advantages of quickness, convenience and low cost on application, and is applied to construction of specific fingerprint picture of plant variety, seed purity quick analysis of large samples, detection and identification of fake and inferior variety, molecular marker-assisted breeding and gene clone.
Owner:WUHAN UNIV
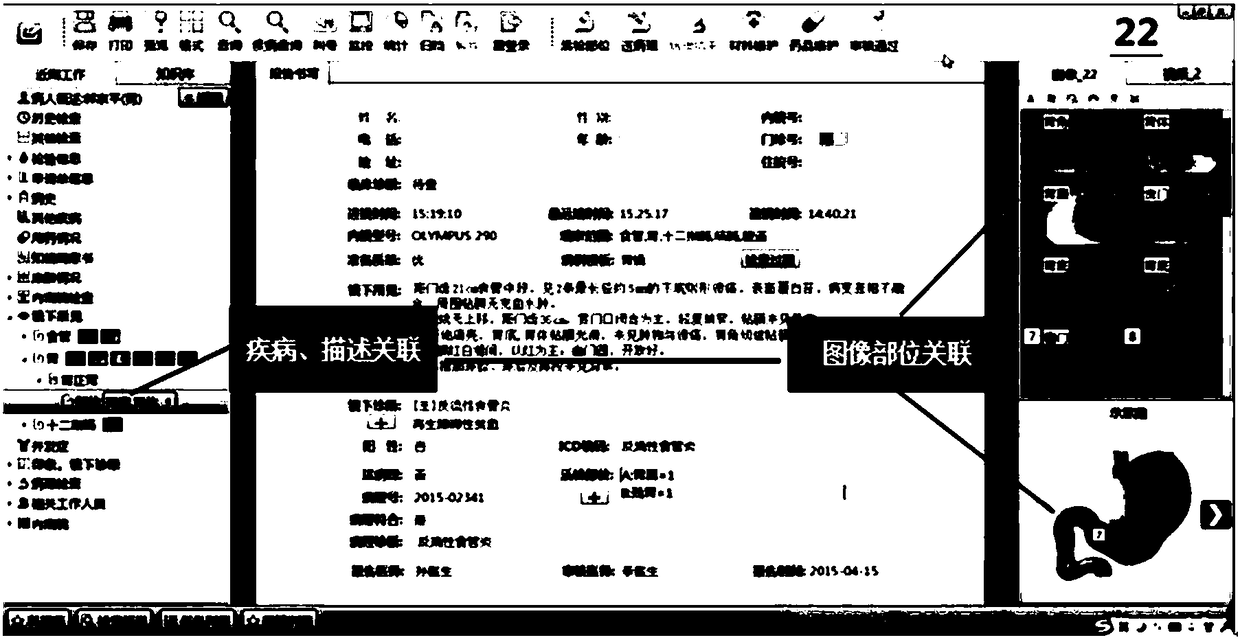
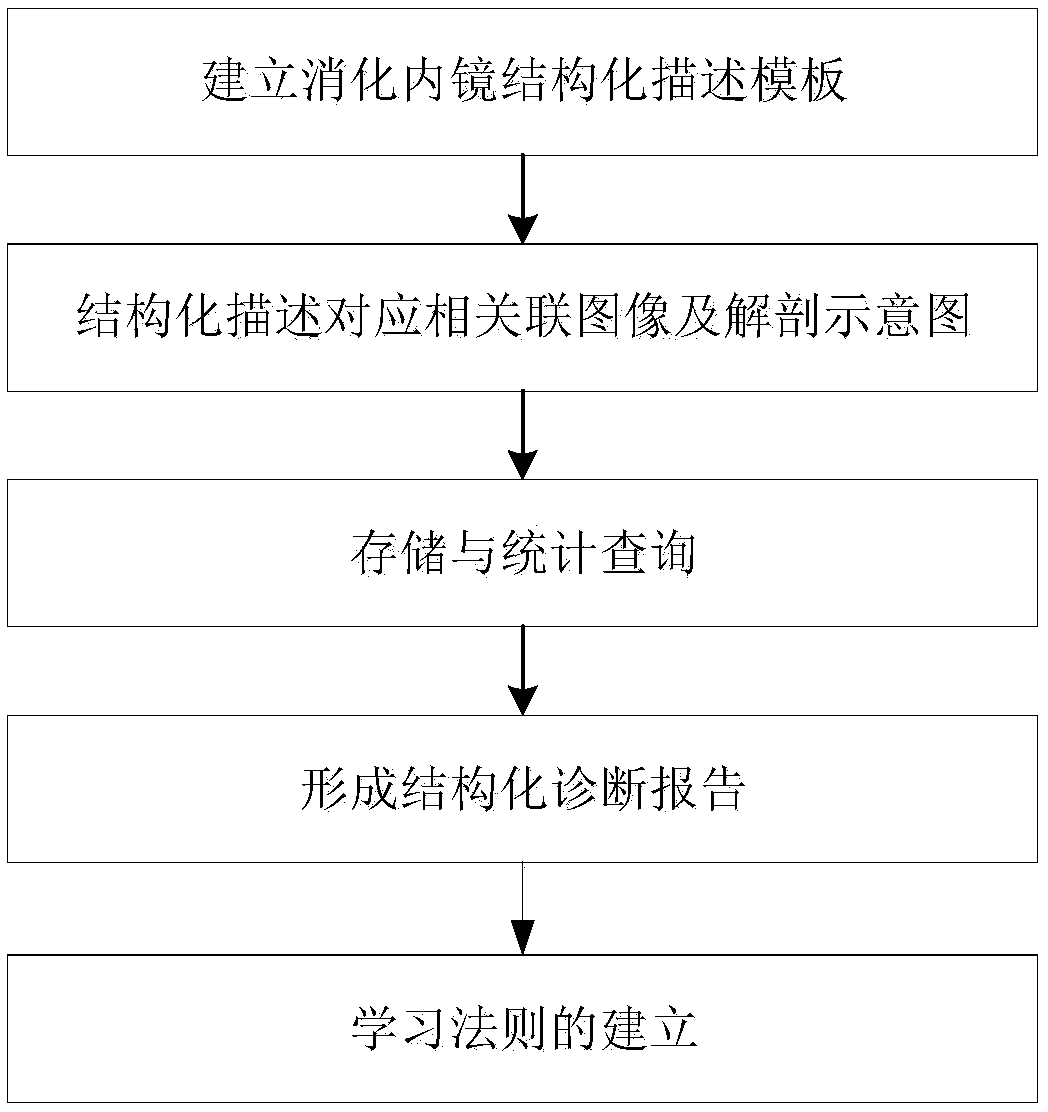
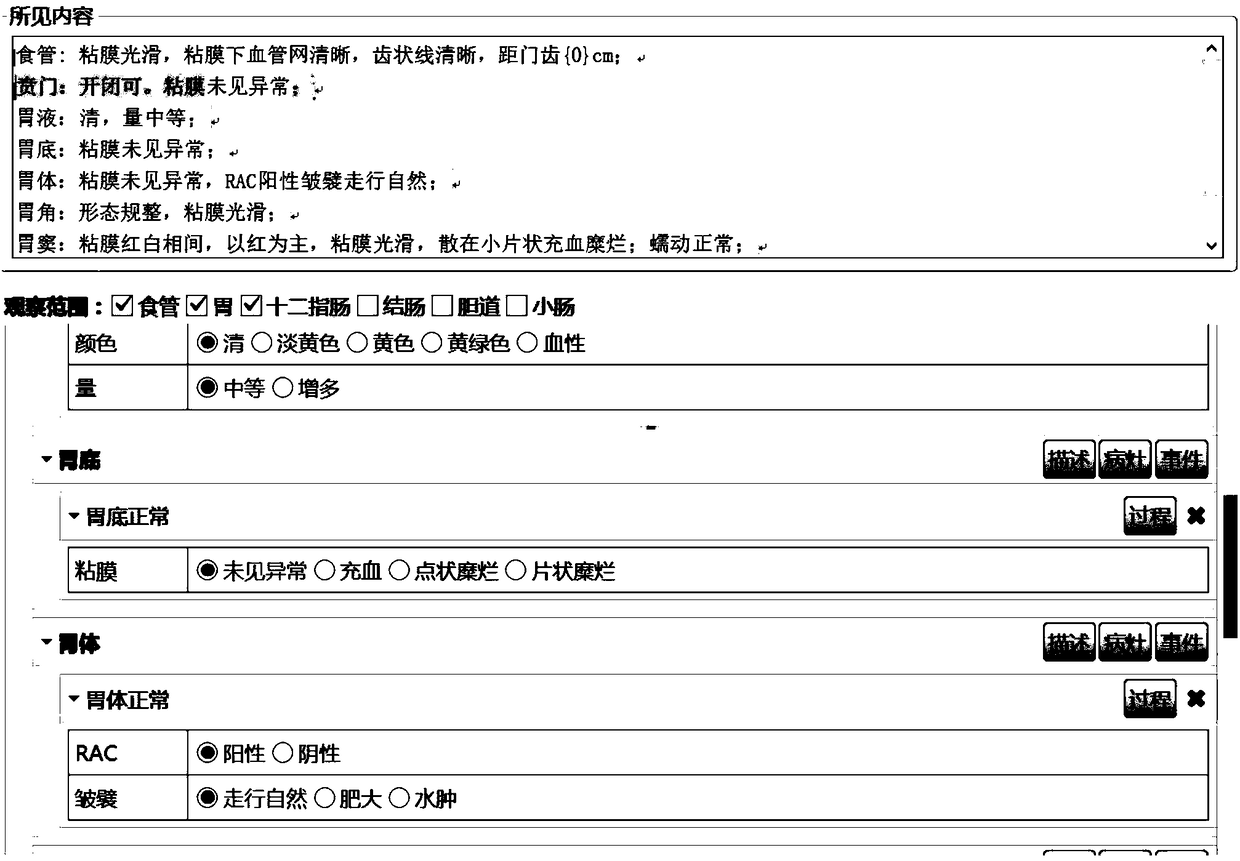
Gastroendoscope structured report system and establishing method thereof
InactiveCN108109681AEnsure comprehensivenessGuaranteed accuracyMedical imagesInstrumentsData acquisitionLesion
The invention relates to a gastroendoscope structured diagnostic report system, belongs to the technical field of the medical PACS image system, and solves the unstructured or semi-structured problemsof nonstandard and incomplete description and diagnosis and failure of deep mining of data. The gastroendoscope structured diagnostic report system comprises a server side module and a client side module. The establishing method of the system comprises the following steps that a standardized gastroendoscope structured description template is established, wherein structured description is corresponding to the associated image and the anatomic diagram; structured data storage and statistical query are supported; microscopic and pathological diagnosis is coded according to the rules; and the standardized report with tables and texts is formed through mouse selection. The process of endoscopic examination and treatment and description of lesions can be converted into natural language to be displayed and released so that the comprehensiveness, the accuracy, the standardization and the computer recognition of the data can be guaranteed, later data statistics and mining can be facilitated, and the system is established on the gastroendoscope data acquisition mode based on the MST international standard.
Owner:青岛美迪康数字工程有限公司
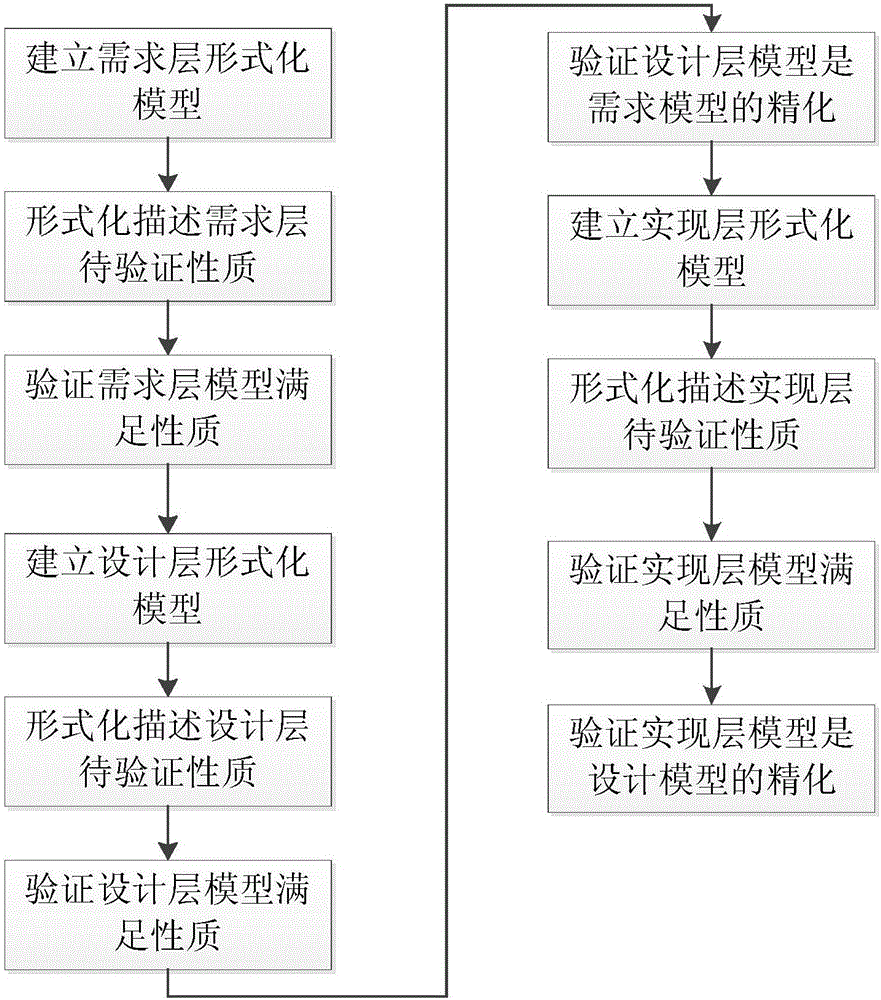
Formal verification method capable of aiming at embedded real-time operating system
ActiveCN106708730AGuaranteed correctnessSolve the problem that the correctness of requirements cannot be guaranteedSoftware testing/debuggingMathematical definitionOperational system
The invention discloses a formal verification method capable of aiming at an embedded real-time operating system, and adopts a phased thought to carry out formal verification on the embedded real-time operating system. firstly, according to three stages of requirement, design and implementation, formal modeling and verification is carried out, and grammar and semantics languages with a strict mathematical definition are used for describing the operating system; then, a formal model of the operating system is established, properties to be verified are extracted, and whether the formal model meets an expected property or not is analyzed and verified through a mathematical method; and through repeated iteration, the formal model which meets the expected property is obtained. Compared with the prior art, the problem that a traditional testing method can not guarantee the requirement correctness of the operating system and the requirement consistency of codes is solved, and the method has a good use value.
Owner:BEIJING INST OF CONTROL ENG
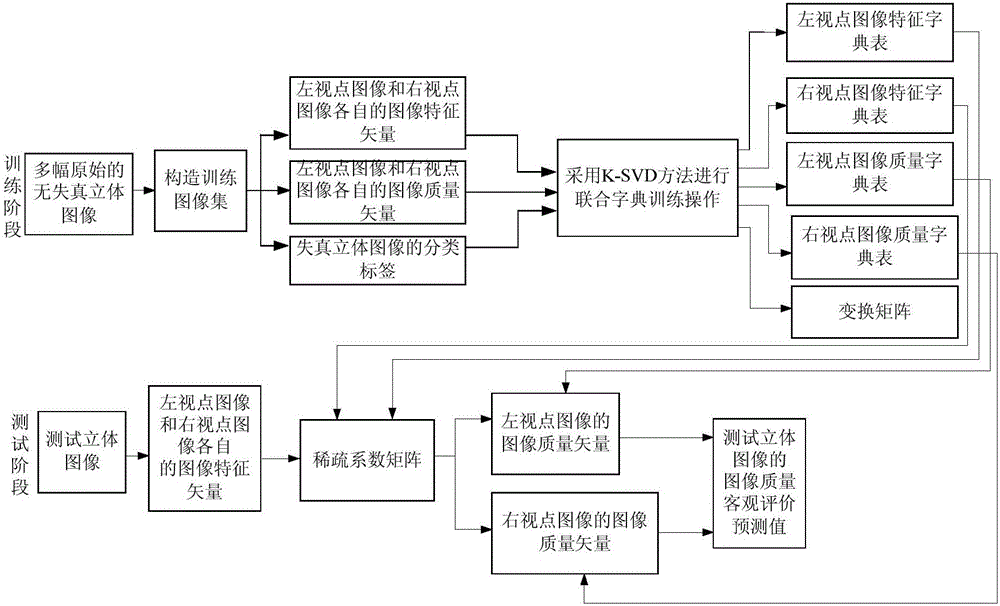
No-reference stereo image quality assessment method
ActiveCN106210711AIdentifiableNo need to predict the subjective evaluation valueTelevision systemsSteroscopic systemsStereo imageNo reference
The invention discloses a no-reference stereo image quality assessment method. The no-reference three-dimensional image quality assessment method comprises the following steps: in a training phase, obtaining classification labels of distorted stereo images by subjective experiments, constituting a training image set through all undistorted stereo images, all distorted stereo images and respective corresponding classification labels, and obtaining left and right viewpoint image feature dictionary tables and left and right viewpoint image quality dictionary tables of the training image set, and a transformation matrix by joint dictionary training, wherein the left and right viewpoint image feature dictionary tables and the left and right viewpoint image quality dictionary tables have discernibility; and in a test phase, obtaining a sparse coefficient matrix by optimization according to the left and right viewpoint image feature dictionary tables, and calculating a predicted value of objective assessment of image quality through the sparse coefficient matrix and the left and right viewpoint image quality dictionary tables. Since the left and right viewpoint image feature dictionary tables and the left and right viewpoint image quality dictionary tables have discernibility, the predicted value of objective assessment of image quality and a subjective assessment value keep relatively good consistency.
Owner:泰安泰山智慧科技有限公司
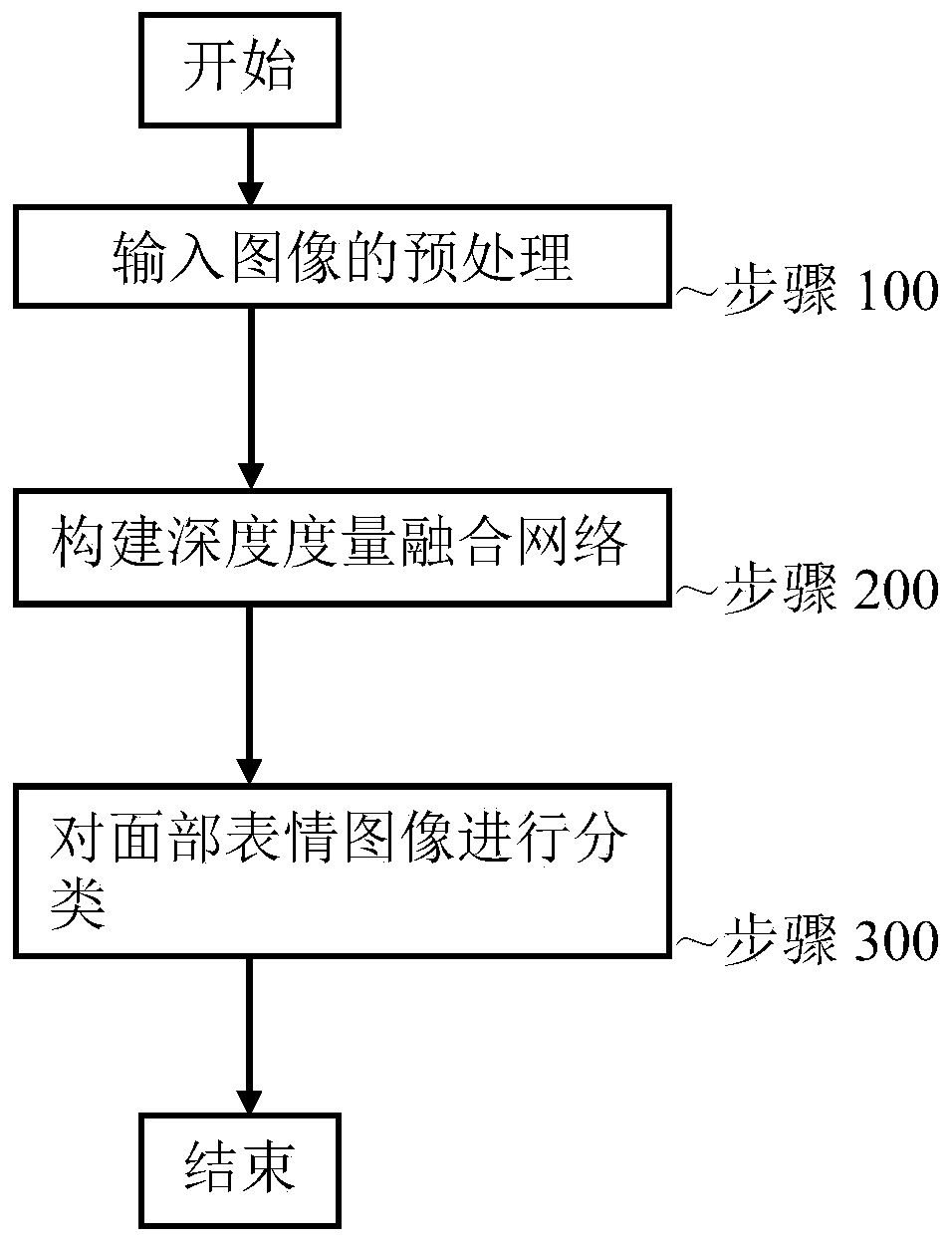
Facial expression recognition method based on depth measurement fusion network
ActiveCN110378237AFast convergenceImprove learning effectAcquiring/recognising facial featuresPattern recognitionAnchor point
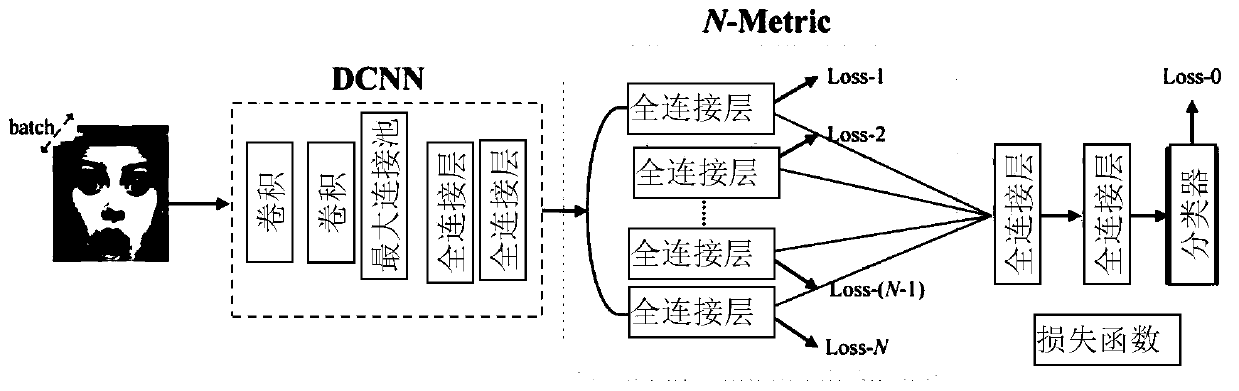
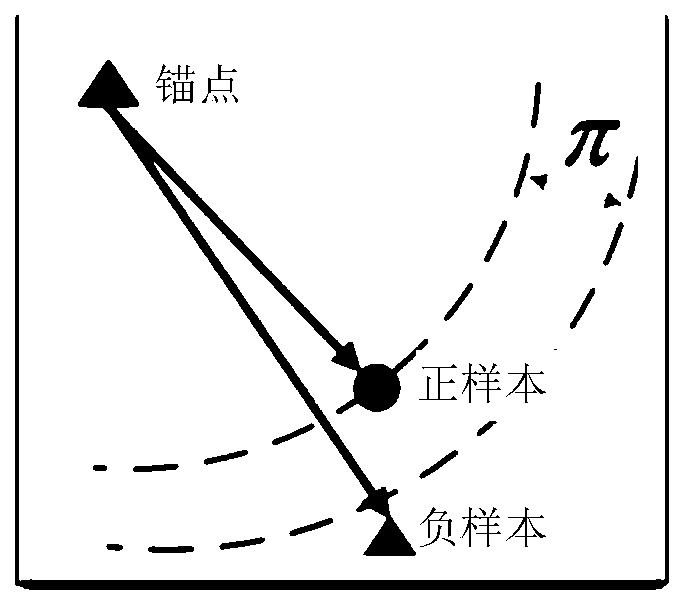
The invention discloses a facial expression recognition method based on a depth measurement fusion network, and the method comprises the following steps: firstly carrying out the preprocessing of an input image; secondly, constructing a depth measurement fusion network combined with various expression feature representations, and finally, training the depth measurement fusion network by utilizingthe training sample; and during testing, inputting a to-be-detected facial expression image into the trained depth measurement fusion network to obtain classification categories of expressions. The method has the following beneficial effects that different expression distributions are learned by using multiple pieces of threshold information, so that the learned features are more robust and distinguishable; a symmetric triple loss function is used, the problems of incomplete judgment and anchor point selection sensitivity can be avoided, convergence of the deep metric fusion network is accelerated, and the learning ability is improved; the accuracy of facial expression recognition can be improved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Digital certificate and electronic seal system and implementation method for electricity trading system
ActiveCN106790106AEasy to manageEasy to useBuying/selling/leasing transactionsTransmissionElectricityConfidentiality
The invention discloses a digital certificate and electronic seal system and an implementation method for an electricity trading system. Core confidential data in the electricity trading quotation process are electronically signed and encrypted by a centralized price competition trading encryption implementation method, safety protection measures are provided for the core data, and data safety, confidentiality and undeniable and anti-tamper properties are ensured. Declared prices of users in price competition need to be encrypted by a certificate in the system. The system solves the problems that the price competition data of the users are easily leaked and tampered in a traditional digital environment, bidding data in the digital environment are easily leaked and decrypted in advance, and integration and synchronization are needed in an internal and external net isolation environment.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
Biological characteristic template protection method with safety threat monitoring capability
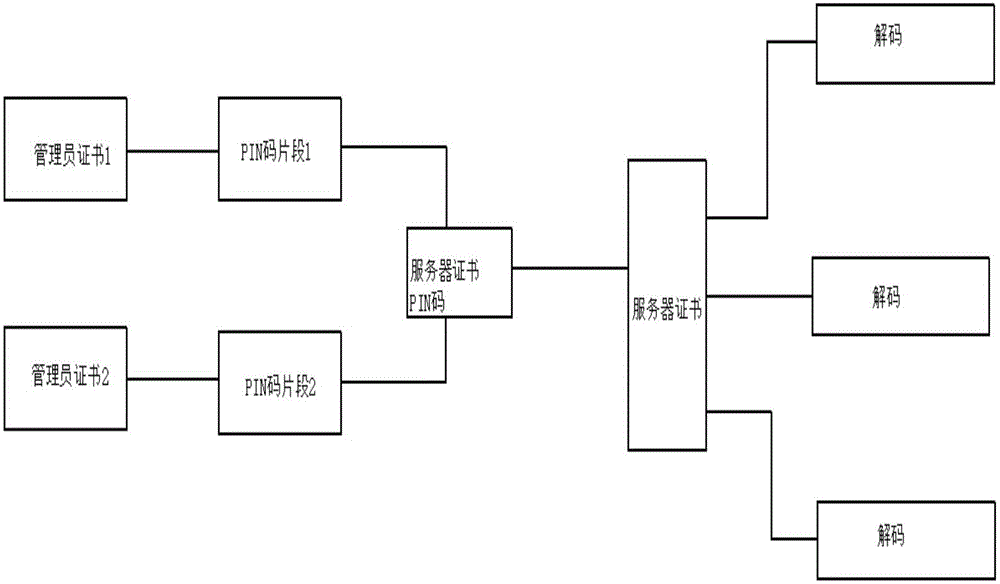
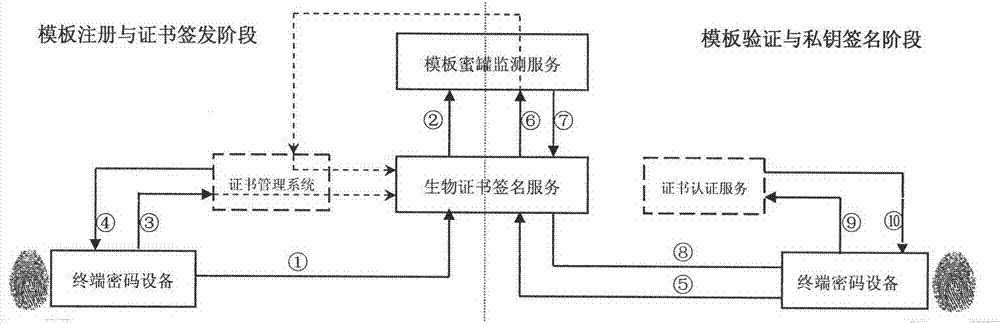
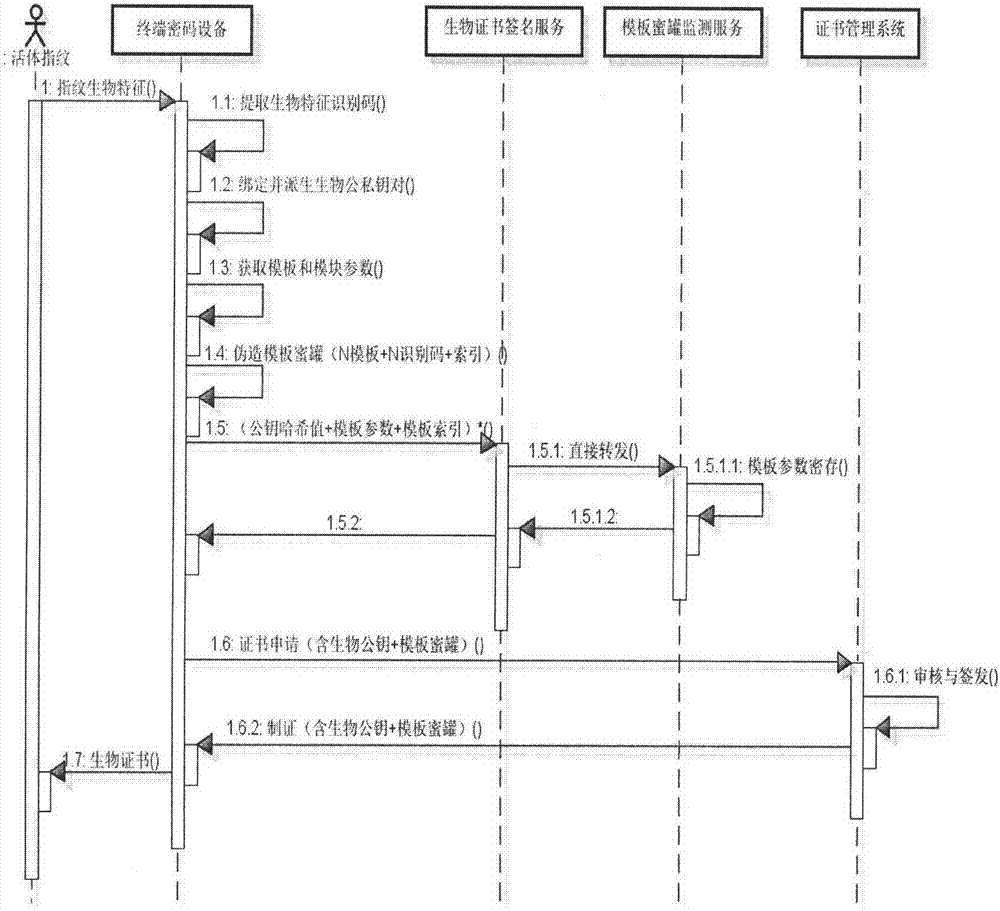
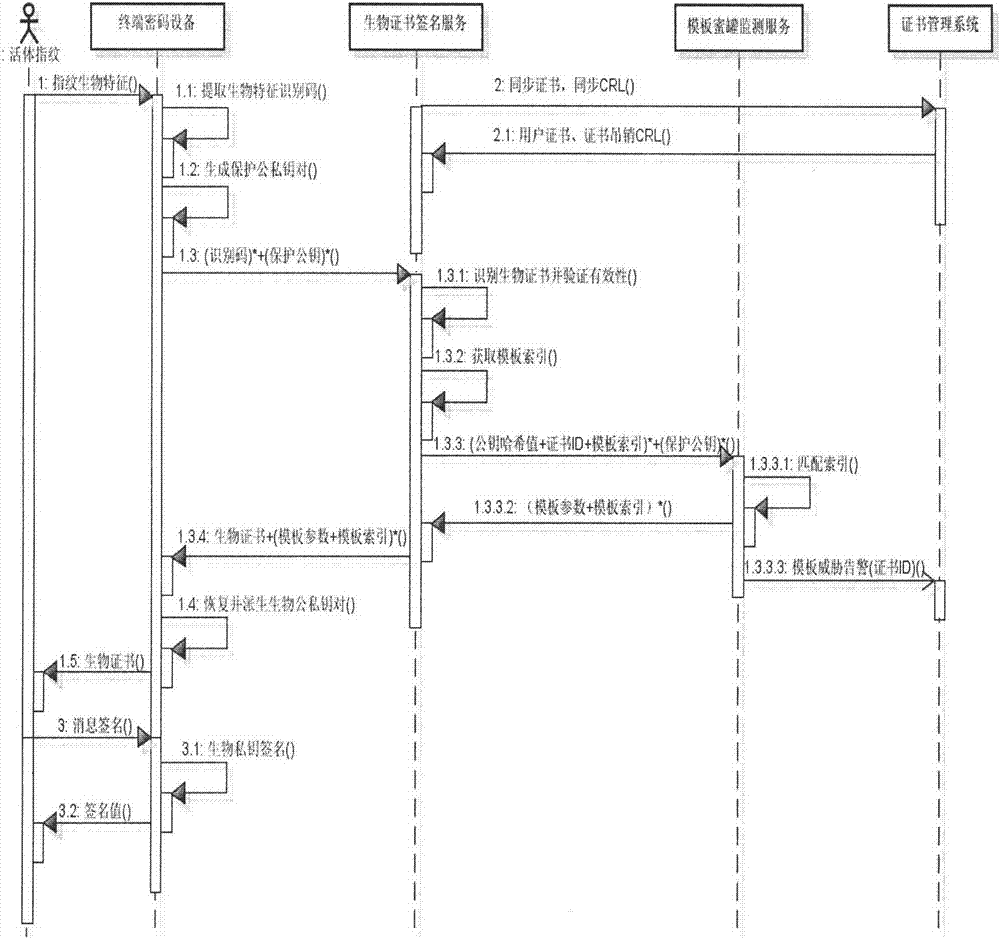
InactiveCN107294943AReal-time monitoring of security threatsSolve template attack problemUser identity/authority verificationKey generationKey recovery
The invention discloses a biological characteristic template protection method with the safety threat monitoring capability and relates to terminal password equipment, a certificate management system, a biological certificate signing service, a template honey pot monitoring service and a certificate certification service. The method is characterized by comprising a biological secret key generation and template honey pot forging, a template parameter secret storage and template honey pot publicity, a feature rapid matching and recognition of a biological certificate, a template parameter retrieval and template threat detection, a biological secret key recovery and on-line signature application. Based on the above manner, the safety threat of the biological template can be monitored in real time based on a honey pot and a certificate. Therefore, the template attack problem of the biological template based on the publicity of the digital certificate is effectively solved. As a result, the novel characteristic of the biological characteristic encryption application of the online signature and offline verification is realized. Meanwhile, safety targets, such as identifiable identity of the biological characteristic application, the non-repudiation of the signature, the non-tampering of data and the like, are achieved.
Owner:TIANJIN POLYTECHNIC UNIV
Transgene crop pollen competitive agent and method for cotten seed preparation
InactiveCN1823579AImprove visibilitySolve the problem of direct pollination without emasculationPlant genotype modificationSelect agentPollen
An application of the transgenic crop's pollen competitor in culturing the hybrid cotton includes such steps as choosing the non-resistant cotton as female parent, choosing transgenic cotton as male parent, spraying the pollen competitor onto the flower of female parent and pollinating with the pollen of male parent or mixing the pollen of male parent with the pollen competitor liquid and spraying the mixture onto the flower of female parent, hybridizing, and coating the obtained seeds with the seed or seedling purity selecting agent.
Owner:朱安灿
Specific molecular target containing staphylococcus aureus standard strains as well as detection and application thereof
ActiveCN112592993AIdentifiableTypical biochemical reactionsBacteriaMicrobiological testing/measurementStaphyloccocus aureusHigh survival rate
The invention relates to the technical field of bioengineering, in particular to four staphylococcus aureus standard strains which have independent intellectual property rights in China and meet the domestic propagation rule. The staphylococcus aureus standard strains can be used as standard reference strains in different fields of foods, medicines, clinical examination and the like. The preservation numbers of the strains are GDMCC 60841, GDMCC 60843, GDMCC 60844 and GDMCC 60845 respectively. The four staphylococcus aureus strains have standard staphylococcus microscopic morphology and physiological and biochemical characteristics, the genetic background is clear, and information of drug resistance, virulence genes and molecular detection targets is clear. The invention also relates to agroup of specific target genes for detecting and identifying the four staphylococcus aureus standard strains and corresponding PCR primers. Finally, the invention further provides a staphylococcus aureus freeze-drying protective agent with high survival rate and specificity, and the staphylococcus aureus freeze-drying protective agent can be used for long-term storage of the standard strains.
Owner:GUANGDONG INST OF MICROBIOLOGY GUANGDONG DETECTION CENT OF MICROBIOLOGY +1
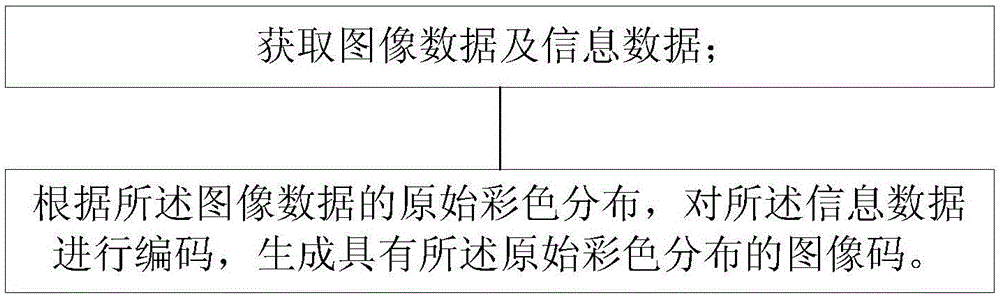
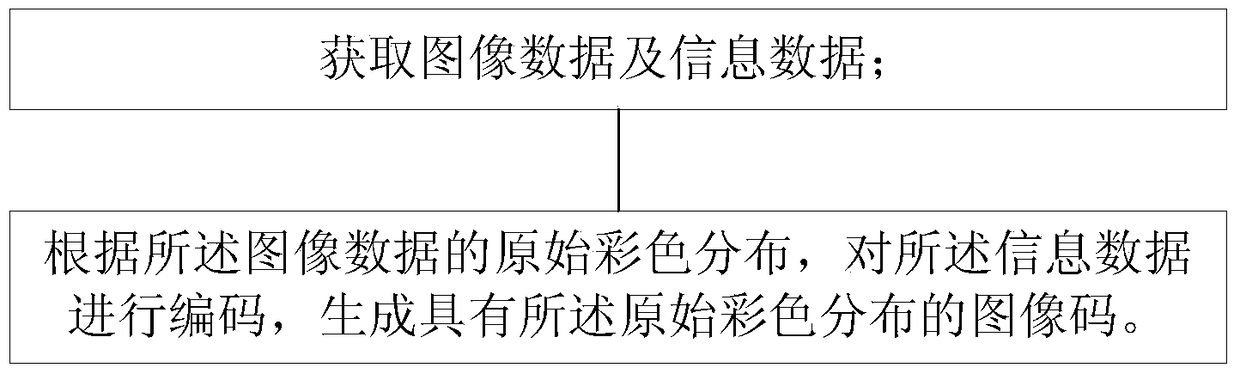
Method for generating color multi-order invisible image code
ActiveCN105095938AIdentifiableLarge amount of information storageRecord carriers used with machinesPattern recognitionIdentifiability
The invention provides a method for generating a color multi-order invisible image code. The method comprises the following steps: acquiring image data and information data; and coding the information data according to the original color distribution of the image data to generate an image code with the original color distribution. By adopting the scheme, the image code with the original color distribution is generated according to the original color distribution of the image data, so that a two-dimensional code can display an image and bear more information, has large information storage volume, can be used as a character or image carrier and has the advantage of naked eye identifiability, the representation form of the two-dimensional code is fitter for the practice, instead of various existing small grids or mosaic, and the ornamental value is higher.
Owner:矽图(厦门)科技有限公司
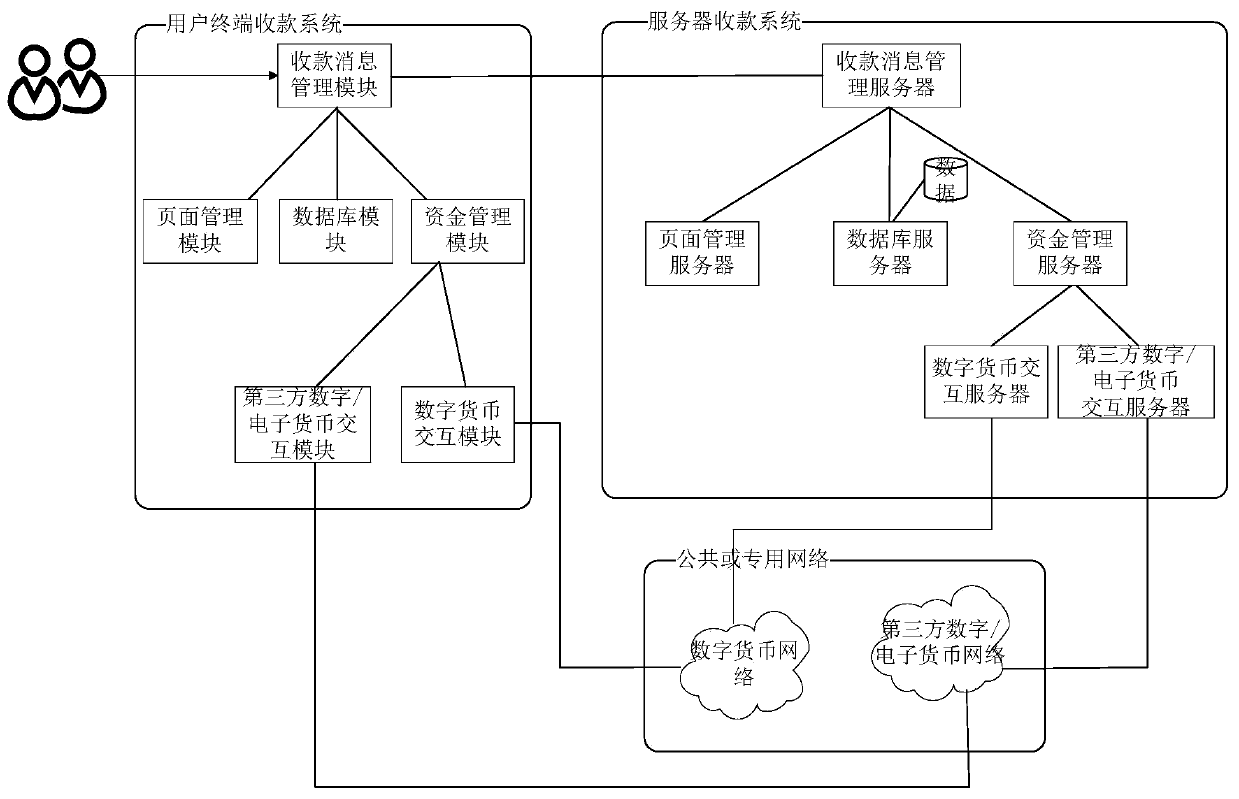
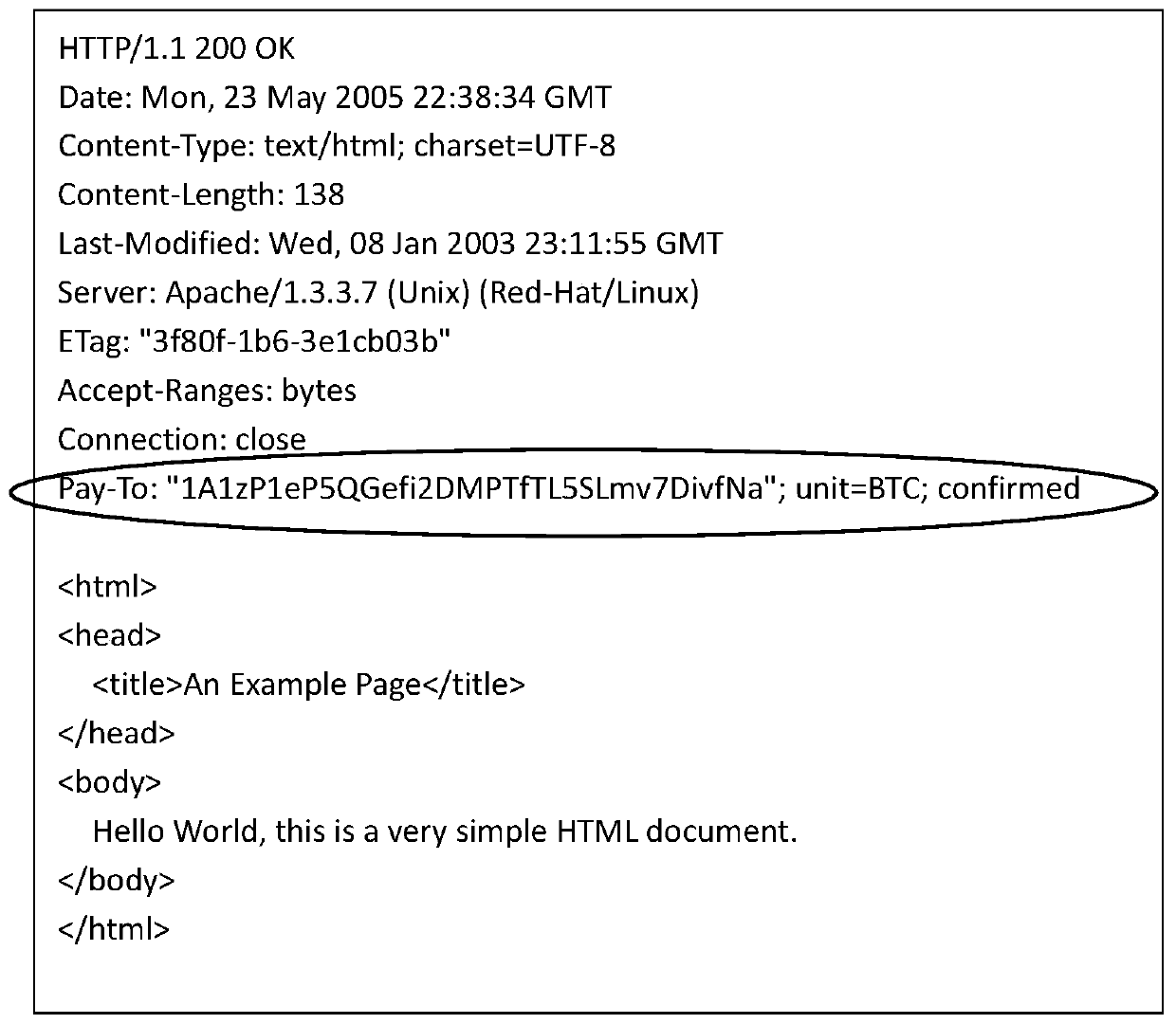
Server based on HTTP protocol, user terminal collection system and collection method
PendingCN109858902AImprove the application of financial functionsAchieve deliveryPayment circuitsTransmissionDigital currencyTime efficient
The invention discloses a server based on an HTTP protocol, a user terminal collection system and a collection method. A head field with collection information is added on the basis of a traditional HTTP protocol; the HTTP protocol is combined with the digital currency / electronic currency; a traditional HTTP protocol has financial functions of collection, remittance and the like; according to theinvention, the collection between the user and the page content provider is realized while the HTTP protocol transmits the information, so that the value is transmitted, and the collection system andthe collection method can be widely applied to servers and user terminals such as browsers, media players and readers, so as to realize the synchronous transmission of the information and the value ofthe HTTP protocol. The invention has the technical characteristics that the value and the information are synchronously transmitted and do not influence each other, account registration is not neededin value transmission, convenience and high efficiency are achieved, and time and cost are saved.
Owner:SHANGHAI FINMAIL NETWORK TECH CO LTD
Robust efficient distributed face image steganography method
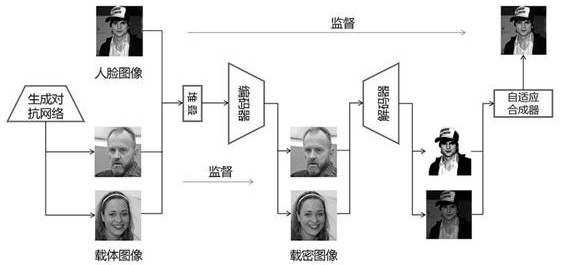
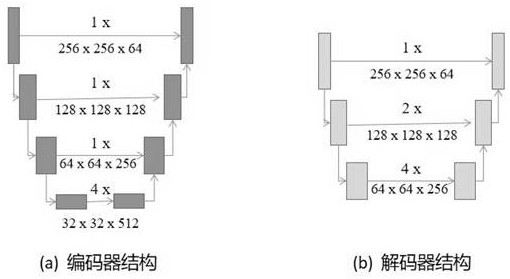
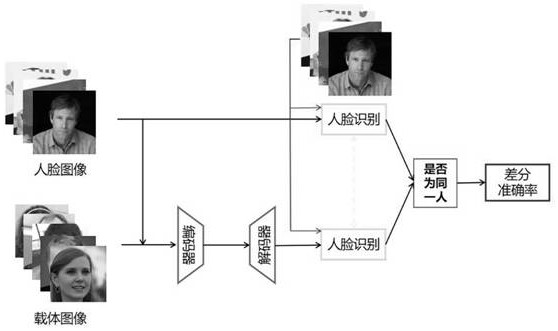
ActiveCN113326531AIdentifiableImprove robustnessImage codingDigital data protectionPrivacy protectionGenerative adversarial network
The invention discloses a robust efficient distributed face image steganography method, which comprises the following steps of: for a given secret face image, encoding the given secret face image and a plurality of carrier face images generated by a generative adversarial network into a plurality of secret-carrying images in a distributed manner by an encoder, and decoding the secret-carrying images into a plurality of secret images by a decoder, and adopting an adaptive synthesizer to synthesize the secret images into a final restored secret face image. The encoder and the decoder provided by the invention are excellent in performance, efficient in calculation and low in consumption of calculation resources. The distributed steganography method provided by the invention is higher in robustness and safer. And a standard of steganography performance of the first human face image is established. Therefore, the method has important application value in the fields of face image privacy protection and the like.
Owner:湖南汇视威智能科技有限公司
Heart rate detection method and device, computer equipment and readable storage medium
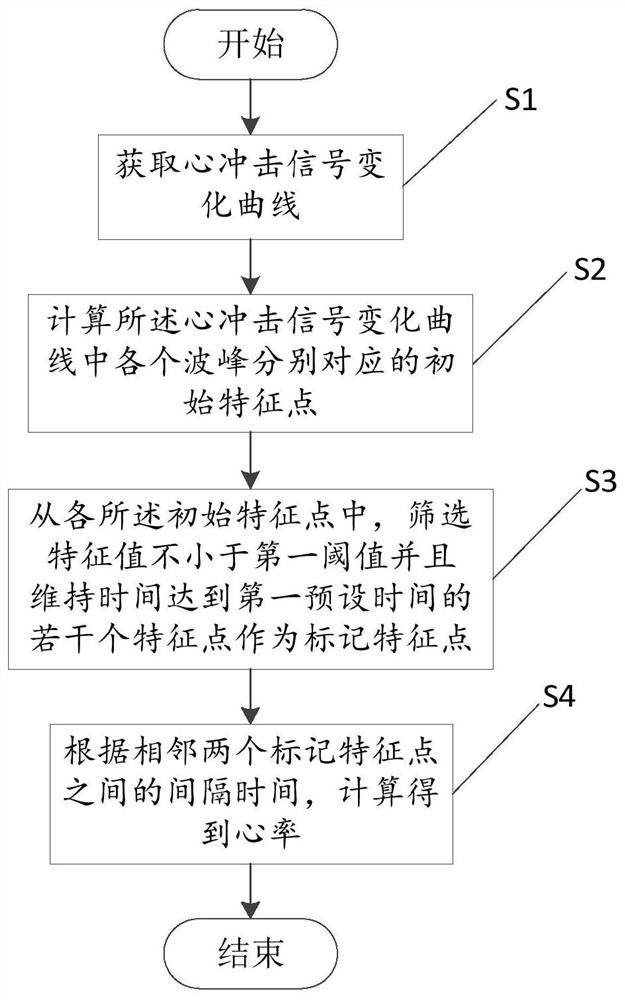
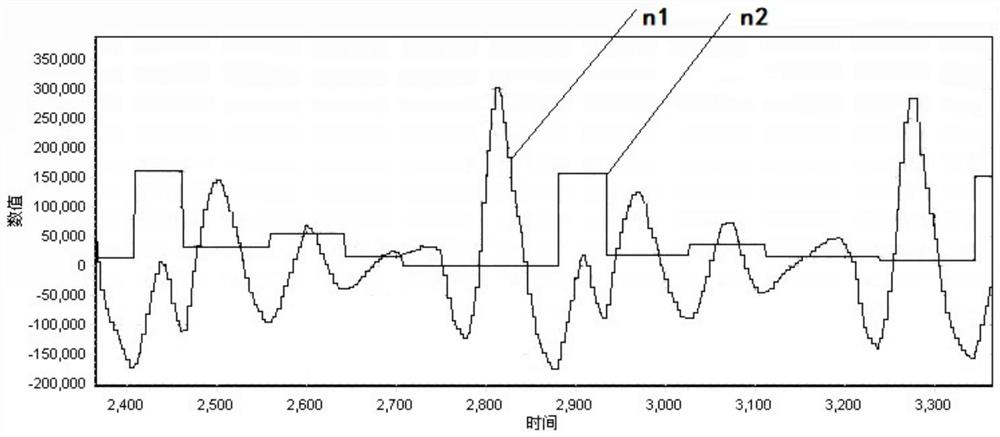
ActiveCN111938621ASignificant rangeStrong specificityMeasuring/recording heart/pulse rateAlgorithmComputation process
The application provides a heart rate detection method and device, computer equipment and a readable storage medium. The method comprises the steps of firstly, obtaining a ballistocardiogram signal change curve, and then calculating an initial feature point corresponding to each wave crest in the ballistocardiogram signal change curve; screening a plurality of feature points as marked feature points from initial feature points, wherein the feature values of the screened feature points are not less than a first threshold value and the time for which the feature values are maintained not to be exceeded reaches a first preset time; and finally, calculating the heart rate according to the interval time between two adjacent marked feature points. In the calculation process, the calculated feature points represent the line length change and consistency of an ascending curve and a descending curve of the wave crest. Compared with an existing algorithm which directly calculates the crest valueof the ballistocardiogram signal change, the amplitude of the feature points is more obvious and more identified. The algorithm provided by the invention aims at 'surface extraction ', so that the specificity of the feature position in periodic signals is remarkably improved, and the accuracy of obtaining the heart rate from the ballistocardiogram signals is greatly increased.
Owner:杨铭轲
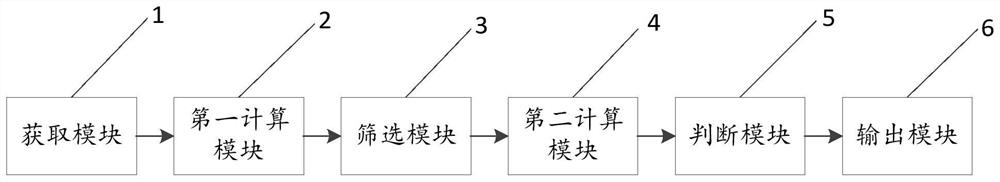
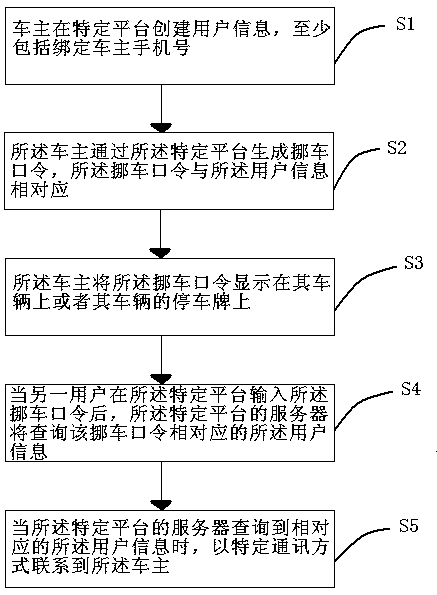
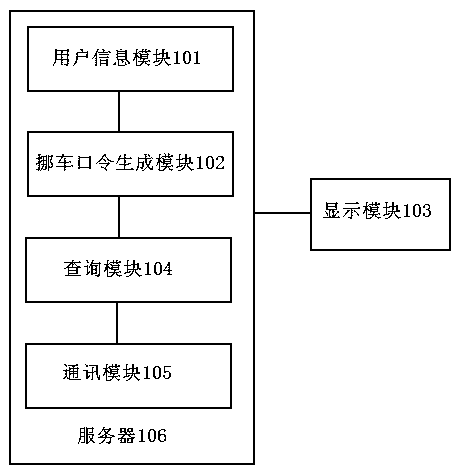
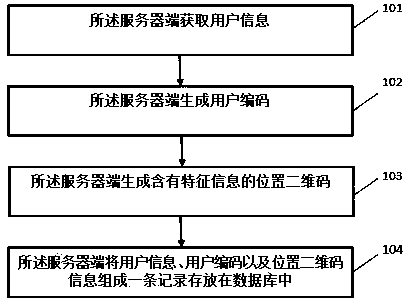
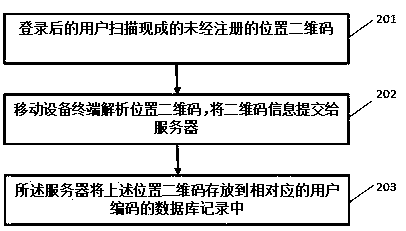
Method and system for contacting vehicle owner to protect privacy of vehicle owner
InactiveCN109639920AProtect personal privacyPersonal privacy hasTelephonic communicationMessaging/mailboxes/announcementsUser inputMobile phone
The invention discloses a method and system for contacting a vehicle owner to protect the privacy of the vehicle owner. The method comprises the following steps: step S1: the vehicle owner creates user information on a specific platform, at least comprising binding a mobile phone number of the vehicle owner; step S2, the vehicle owner generates a vehicle moving command through the specific platform, wherein the vehicle moving command corresponds to the user information; step S3, the vehicle owner displays the vehicle moving command on his vehicle or on stop boards of other vehicles; step S4, after another user inputs the vehicle moving command on the specific platform, a server of the specific platform queries the user information corresponding to the vehicle moving command; and step S5, when the server of the specific platform queries the corresponding user information, the server contacts the vehicle owner in a specific communication manner. By adoption of the method disclosed by theinvention, the personal privacy of the vehicle owner is effectively protected, and a variety of communication manners increase the effectiveness of the contact.
Owner:王恩惠
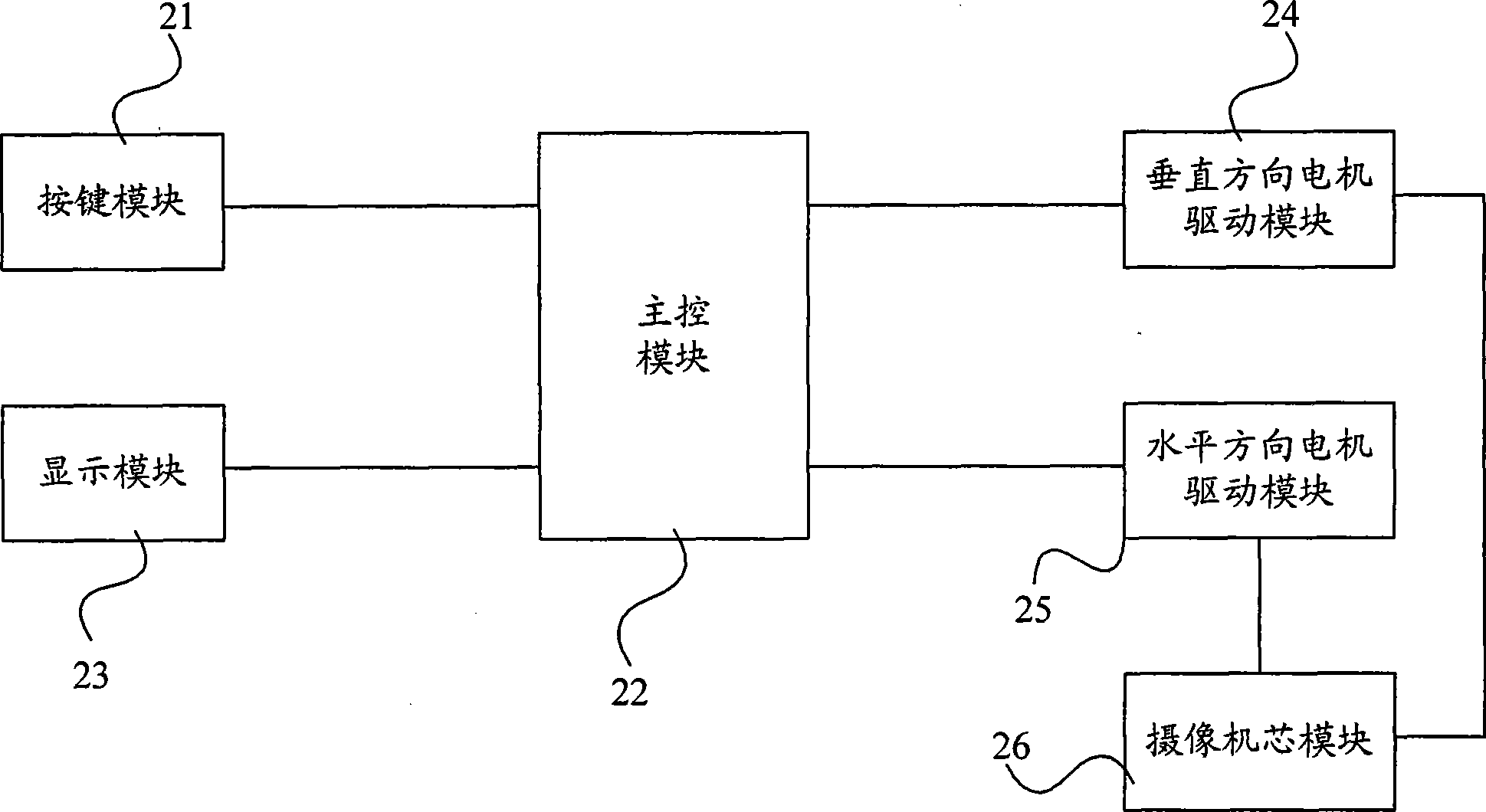
High-speed image missile-borne data recording device
ActiveCN107135365AImplement serial-to-parallel conversionRealize the recording functionTelevision system detailsRegistering/indicating working of vehiclesGate arrayComputer module
The invention discloses a high-speed image missile-boron data recording device. The device comprises a field programmable logic gate array; an LVDS image data interface module, a first storage module and a second storage which are respectively connected with the field programmable logic gate array; the LVDS image data interface module is used for performing series- parallel conversion on high-speed seeker image data in the flight process of an aircraft, and performing visible light / infrared image class judgment on the high-speed seeker image under the control of the field programmable logic gate array; the high-speed seeker image at different image classes is stored in the first storage module and the second storage module through the field programmable logic gate array; the data recording device is recycled after the aircraft is grounded so as to read out the image data in the flight experiment. The data recording device disclosed by the invention has the advantages of being simple in module, small in volume, light in weight, recognizable in visible light / infrared image, strong in large-overload resistance, and simple in data recording and controlling flow, and is especially suitable for the data storage of a missile-borne seeker image.
Owner:湖北三江航天红林探控有限公司
A method for generating color multi-level invisible image codes
ActiveCN105095938BIdentifiableLarge amount of information storageRecord carriers used with machinesIdentifiabilityImage code
The invention provides a method for generating a color multi-order invisible image code. The method comprises the following steps: acquiring image data and information data; and coding the information data according to the original color distribution of the image data to generate an image code with the original color distribution. By adopting the scheme, the image code with the original color distribution is generated according to the original color distribution of the image data, so that a two-dimensional code can display an image and bear more information, has large information storage volume, can be used as a character or image carrier and has the advantage of naked eye identifiability, the representation form of the two-dimensional code is fitter for the practice, instead of various existing small grids or mosaic, and the ornamental value is higher.
Owner:矽图(厦门)科技有限公司
Twin classifier certainty maximization method for cross-domain complex vision task
PendingCN112801179AGuaranteed mobilityIdentifiableCharacter and pattern recognitionNeural architecturesAlgorithmIdentifiability
The invention relates to a twin classifier certainty maximization method for a cross-domain complex visual task; the method comprises the following steps: 1, constructing a neural network frame, and initializing the neural network frame; 2, inputting the source domain sample into a feature generator G to obtain a corresponding feature representation; and 3, under the supervision of the label information of the source domain sample, calculating an empirical risk error between a model prediction output p and a real label y on the source domain sample by using a standard cross entropy loss function. The method has the advantages that a novel classifier deterministic difference measurement CDD is designed, wherein the difference of the classifiers is measured by means of category correlation between target prediction of the twin classifiers, and implicit constraints are applied to the identifiability of target features at the same time.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
A kind of anti-counterfeiting ink
The invention provides an anti-counterfeiting ink which comprises a Raman mark material having Raman activity. The ink can detect an obvious Raman characteristic scattering peak of a marker material under stimulation of a 514.5 nm light source. The characteristic peak has uniqueness, can be identified and marked, can be distinguished from other components in the ink, and is not interfered by other components, so that the anti-counterfeiting ink can be used for identifying the true and false of paper money and negotiable securities, and has a certain anti-counterfeiting function.
Owner:CHINA BANKNOTE SECURITY PRINTING TECH RES INST CO LTD +1
A method and system for contacting a car owner to protect the privacy of the car owner
ActiveCN105049406BPrivacy protectionImprove effectivenessCo-operative working arrangementsData switching networksMobile Telephone NumberMobile device
The invention discloses a method and system for contacting a car owner to protect the privacy of the car owner. The method includes: a server obtains the information of the car owner, and sends a verification code to the mobile phone number submitted by the car owner, and the mobile device terminal receives the verification code and submits it to the server; the server automatically generates User code; the server stores the user code and mobile phone number in a record in the database; the server encodes and generates the user QR code; the mobile device terminal scans the user QR code, verifies the information, and submits the user code to the server; the server passes the user code Locate in the database, obtain the corresponding car owner's mobile phone number, and the mobile device terminal calls the mobile phone dial-up function to establish a call connection with the car owner. The present invention can conveniently contact the car owner without revealing the phone number of the car owner, and protects the privacy of the car owner; the car owner can print the generated two-dimensional code by himself, which is convenient and fast, and can also use the beautiful two-dimensional code that has been made, which is easy to attract people's attention.
Owner:OCEAN UNIV OF CHINA
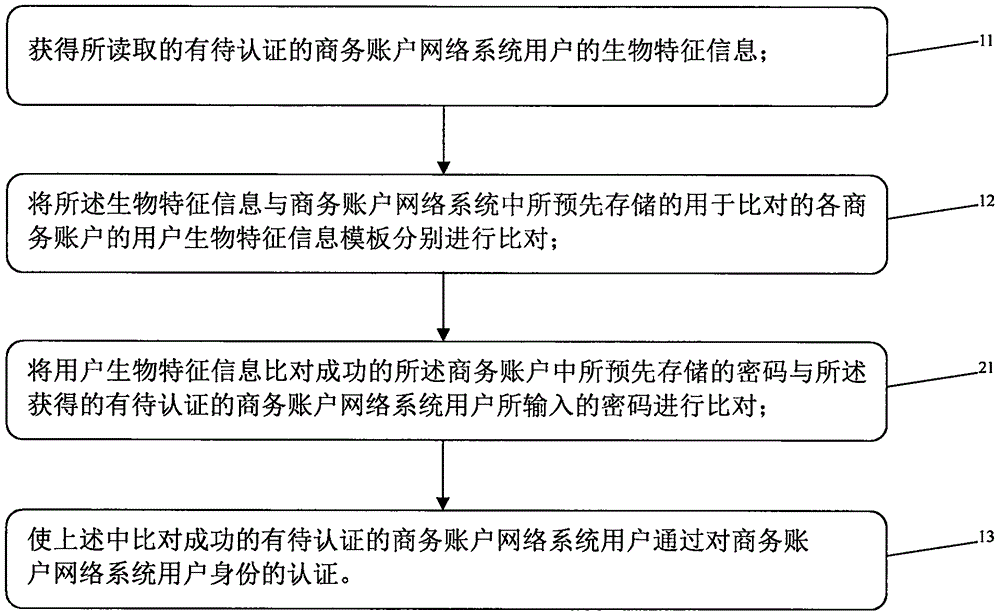
User identity authentication method and systems of business account network system, and apparatuses
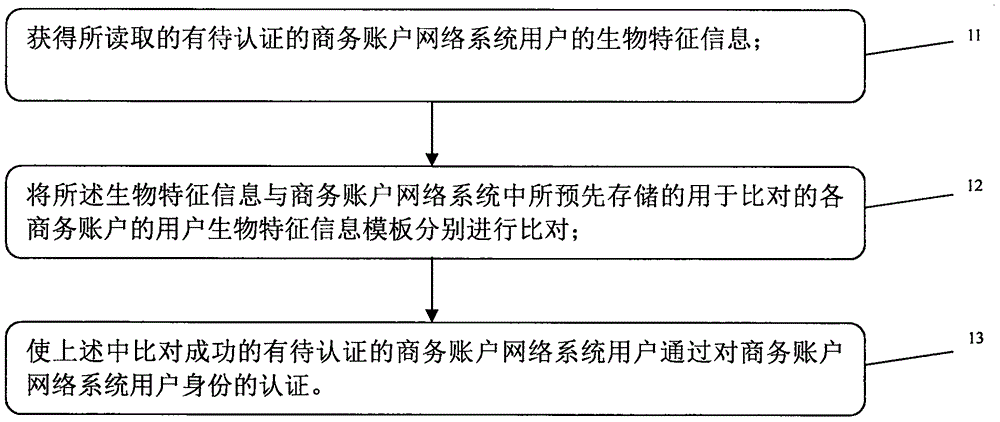
InactiveCN106656983AAccurate authenticationThere is no problem of lossTransmissionInternet privacyNetworked system
The present invention provides a user identity authentication method and system of a business account network system, and an apparatus, relating to the field of business account network systems. The method comprises the steps of acquiring read to-be-authenticated biometric information of a user of the business account network system; comparing the biometric information with a user biometric information template of each business account that is used for comparison and is prestored in the business account network system; and approving the authentication of the user identity of the successfully compared business account in the business account network system. The present invention further provides a user identity authentication apparatus and system of a business account network system. Through adoption of the method, system and apparatus, dependence on the account number and the account card is eliminated, and an era in which various business accounts can be used at any time without using the account number and account card is ushered in.
Owner:李国兴
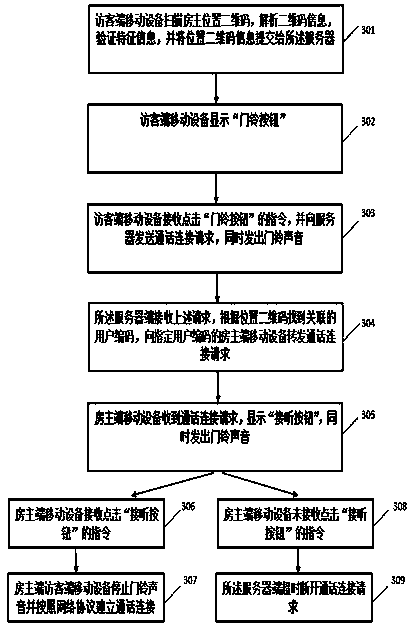
Mobile phone software doorbell system and its implementation method
ActiveCN105761392BReduce installation costsInstant contactSensing by electromagnetic radiationElectric/electromagnetic audible signallingDoorbellSpeech sound
Owner:OCEAN UNIV OF CHINA
A method for realizing two-dimensional and three-dimensional interactive correlation based on KKS coding
ActiveCN109241581AIdentifiableSolve the basic problems of classificationDesign optimisation/simulationSpecial data processing applicationsSimulationHandover
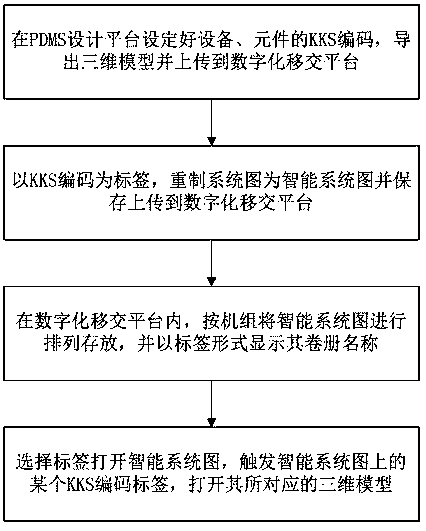
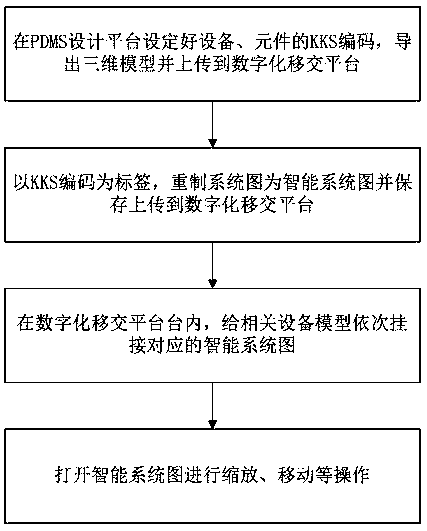
The invention relates to a method for realizing two-dimensional and three-dimensional interactive correlation based on KKS coding, belonging to the technical field of digital handover of power plants.The method comprises the following steps: setting KKS coding of equipment and components on a PDMS design platform, importing a three-dimensional model and uploading it to the digital handover platform; by taking KKS code as label, redrawing system diagram as intelligent system diagram and saving and uploading it to digital handover platform; In the digitized handover platform, arranging and storing the intelligent system diagrams according to the units, and displaying the volume names in the form of labels; Selecting a label to open the intelligent system diagram, triggering a certain KKS coding label on the intelligent system diagram, and opening its corresponding three-dimensional model. The method for realizing two-dimensional and three-dimensional interactive correlation based on KKScode provided by the invention solves the problem that the fast correlation is not possible in the digital handover process of the power plant at present, improves the efficiency and accuracy of thedigital handover, and improves the convenience of the digital handover work.
Owner:POWERCHINA HEBEI ELECTRIC POWER SURVEY & DESIGN INST CO LTD +2
Gait recognition method and device based on spatial-temporal feature fusion and storage medium
PendingCN114387670AReduce the amount of parametersImprove recognition accuracyCharacter and pattern recognitionNeural architecturesEffect of gait parameters on energetic costRecognition algorithm
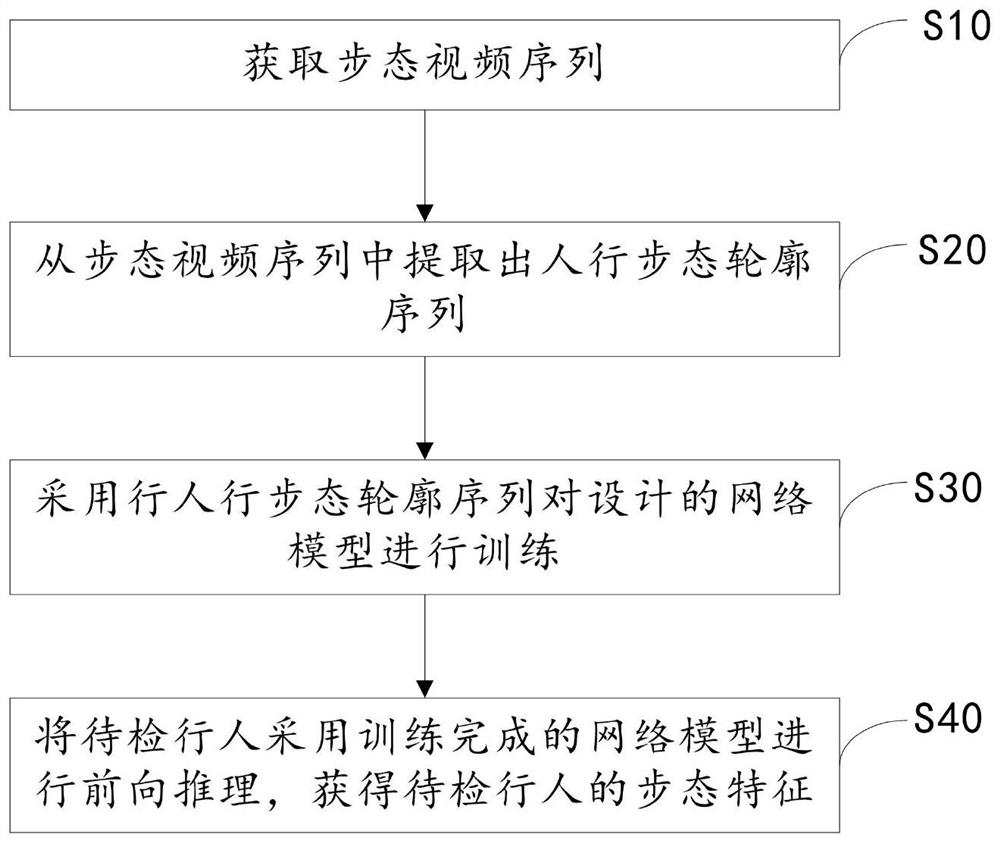
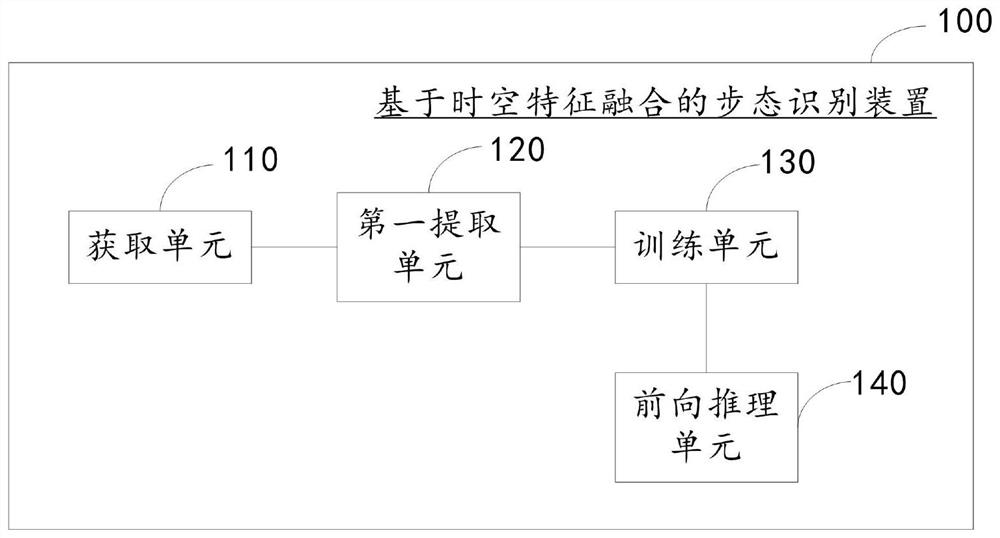
The embodiment of the invention discloses a gait recognition method and device based on spatio-temporal feature fusion and a storage medium. The method comprises the following steps: acquiring a gait video sequence; extracting a pedestrian gait contour sequence from the gait video sequence; training the designed network model by adopting a pedestrian walking gait contour sequence; and performing forward reasoning on a to-be-detected pedestrian by adopting the trained network model to obtain gait features of the to-be-detected pedestrian. According to the method, the time sequence of the gait video sequence can be reserved, the parameter quantity of the network is further reduced, that is, the better effect is achieved on the aspects of the effect and the model complexity, in addition, the time and space characteristics of the gait sequence are fused, and the algorithm is more efficient. A gait recognition algorithm which is smaller in model and higher in recognition precision is realized.
Owner:深圳市同为数码科技股份有限公司
A certificate-free combined key generation and application method
ActiveCN105450396BSolve the sum collision problemGuaranteed logo effectKey distribution for secure communicationKey generationNon-repudiation
The invention discloses a certificate-free combined secret key generation and application method. The method comprises the following steps: S1, a server end generating an elliptical curve, skm and pkm, and issuing parameters of the elliptical curve and the pkm; S2, a client generating ID, xID and PKuk, and uploading the ID and the PKuk to the server end; S3, the server end generating SKID, PKID, rID and PKrID; S4, the server end generating PKE, SKE and PKS; S5, the service end issuing the SKE to the client, and broadcasting the ID, the PKE and the PKS; S6, the client generating SKS through the xID and the SKE, and decrypting encryption information through the SKE, and signing verification information through the SKS; and S7, a general client encrypting decryption information and verifying signature information through the PKS. The method provided by the invention solves the problems of non-repudiation of sum bumps, linear collusion and individual signature of a combination public key technology and the like.
Owner:鄂尔多斯市迪曼森密码科技有限公司
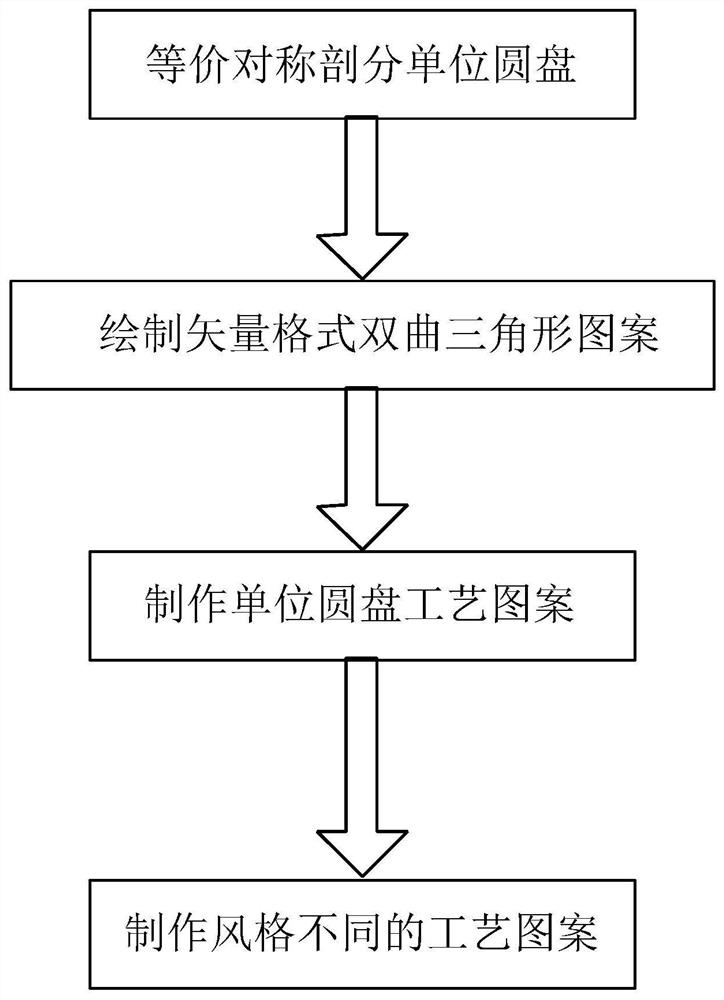
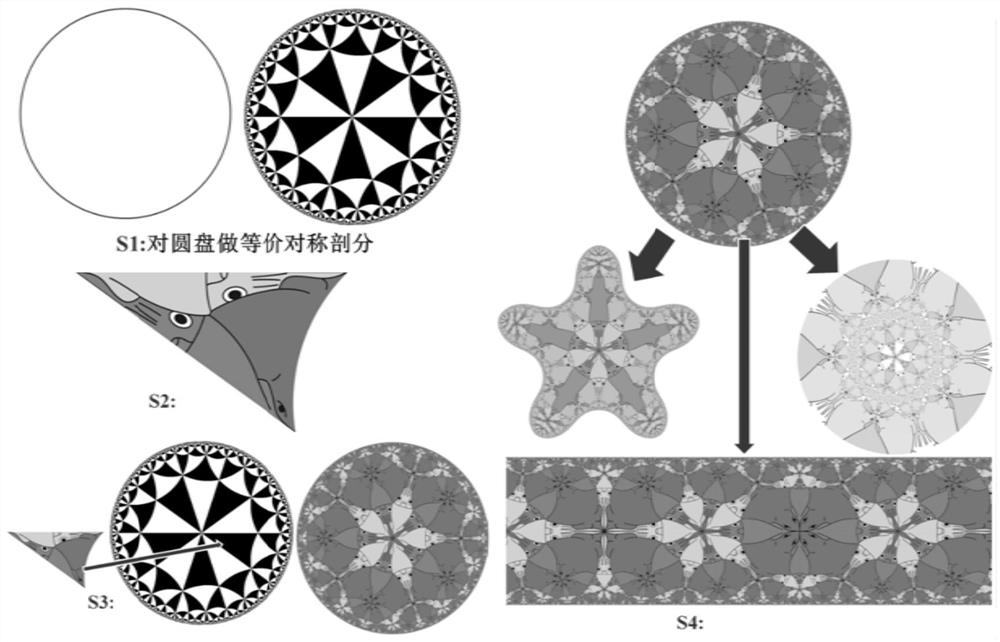
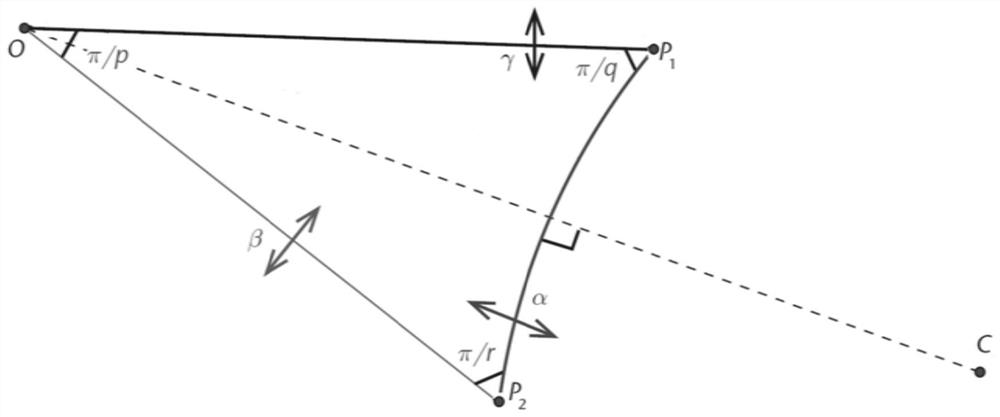
A digital art pattern drawing method with infinite symmetrical structure
ActiveCN107862725BIdentifiableEasy to storeDrawing from basic elementsDesign optimisation/simulationTextile printerMaterial Design
The invention discloses an infinite-symmetrical-structure digital art pattern drawing method. The infinite-symmetrical-structure digital art pattern drawing method is implemented through the followingsteps of, firstly, according to the principles of symmetric hyperbolic groups and base domain in hyperbolic geometry, performing symmetric equivalent subdivision on a unit disk; secondly, drawing a hyperbolic triangle pattern in a vector format through vector software; thirdly, through hyperbolic geometry transformation technology, manufacturing a unit disc technical pattern; fourthly, through the conformal technology, manufacturing technical patterns in different styles. The patterns drawn through the infinite-symmetrical-structure digital art pattern drawing method is attractive in style and rich in variety, presents an infinite symmetrical structure within a finite domain and can be widely applied to the decoration fields such as textile printing, porcelain and packing material design.
Owner:JINGGANGSHAN UNIVERSITY
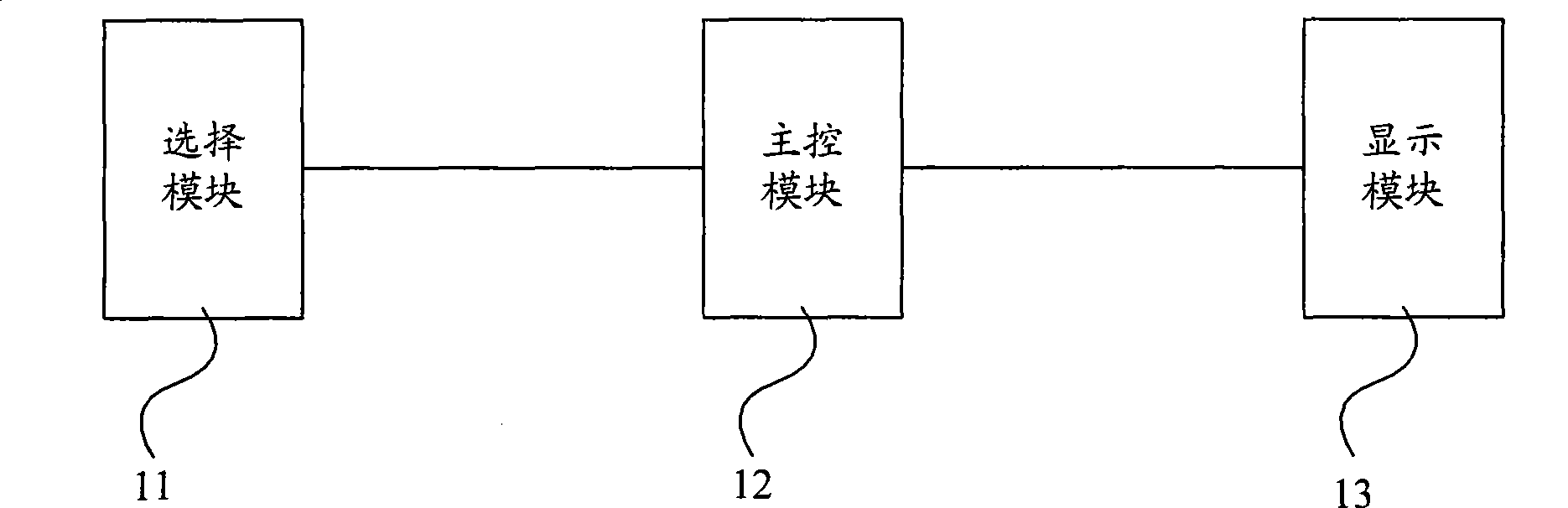
Meeting type camera and implementing method thereof
InactiveCN101500087AIdentifiableEasy to operateTelevision system detailsNon-electrical signal transmission systemsControl modeImage resolution
The invention discloses a convention camera and a realization method thereof. The camera comprises a selection module used for selecting and transmitting an output mode, a video resolution factor and a control mode to a main control module; the main control module used for configuring video output to be consistent with the output mode, the video resolution factor and the control mode selected by the selection module and transmitting the output mode, the video resolution factor and the control mode to a display module; and the display module connected with the main control module and used for displaying the output mode, the video resolution factor and the control mode obtained by the main control module. The embodiment of the invention can simplify the operation, avoid misoperation as much as possible, and lead the output mode, the video resolution factor and the control mode to have identifiability.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com