Vehicle owner contacting method and system with function of protecting privacy of vehicle owner
A technology for protecting cars and car owners, applied in the field of communication, can solve the problems of high cost of phone calls, inconvenient car owners, complicated processes, etc., and achieve the effects of convenient and fast car owner contact, protection of privacy, and increased effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
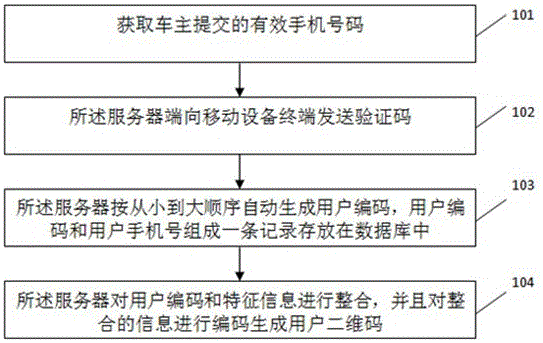
[0030] Such as figure 1 with figure 2 As shown, this embodiment provides a method for obtaining user information that protects the privacy of the car owner:
[0031] Step 101: obtain the valid mobile phone number submitted by the car owner;
[0032] Step 102: the server side sends a verification code to the mobile device terminal. In this step, the server sends a verification code to the mobile phone number submitted by the user. If the verification code submitted by the mobile device terminal of the car owner is correct, then perform step 103, otherwise reject;
[0033] Step 103: the server automatically generates user codes in ascending order, and user codes and user mobile phone numbers form a record and store them in the database. The user codes in this step are irrelevant to user information, that is, do not contain user information;
[0034] Step 104: The server integrates the user code and feature information, and encodes the integrated information to generate a use...
Embodiment 2
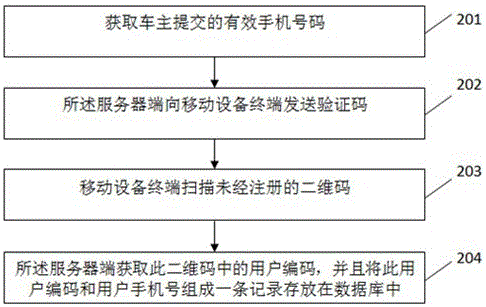
[0041] Such as image 3 with Figure 4 As shown, this embodiment provides a method for contacting a car owner that protects the privacy of the car owner.
[0042] Step 301: The mobile device terminal scans the QR code of the vehicle owner to obtain the QR code information. In this step, the user scans the QR code reserved by other users through the mobile device terminal, and the mobile device terminal analyzes the information contained in the QR code;
[0043] Step 302: After verifying that the characteristic information of the two-dimensional code is correct, submit the user code to the server. The purpose of verifying the characteristic information of the two-dimensional code in this step is to improve the efficiency of scanning the two-dimensional code. Through the identification of the characteristic information, confirm the two-dimensional The code is a dedicated QR code.
[0044] Step 303: the server receives the user code sent by the mobile device terminal;
[0045]...
Embodiment 3
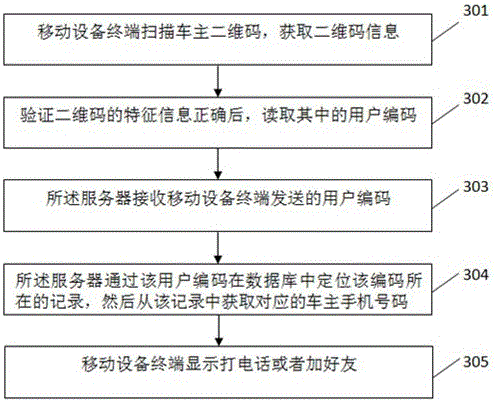
[0052] Such as image 3 and Figure 5 As shown, the present embodiment provides a method of contacting the car owner to protect the privacy of the car owner:
[0053] Steps 501 to 504 are consistent with steps 301 to 304, and will not be repeated here;
[0054] Step 505: The mobile device terminal chooses to add friends;
[0055] Step 506: After receiving the sender's request, the server sends the request to another mobile device terminal;
[0056] Step 507: Another mobile device terminal agrees to the request;
[0057] Step 508: The two mobile device terminals perform operations such as sending text, pictures, and audio between friends through the server;
[0058] Step 509: The mobile device end sets the operation of denying dial-in and moving into the blacklist. In this step, if a message from a certain mobile device terminal is rejected, it can be moved into the blacklist, or set to not allow dial-in.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com