Biological characteristic template protection method with safety threat monitoring capability
A biometric and template technology, applied in secure communication devices, user identity/authority verification, digital transmission systems, etc., can solve problems such as real-time detection of attack behaviors that cannot be templated, and rapid application of biometric identification and encryption products.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
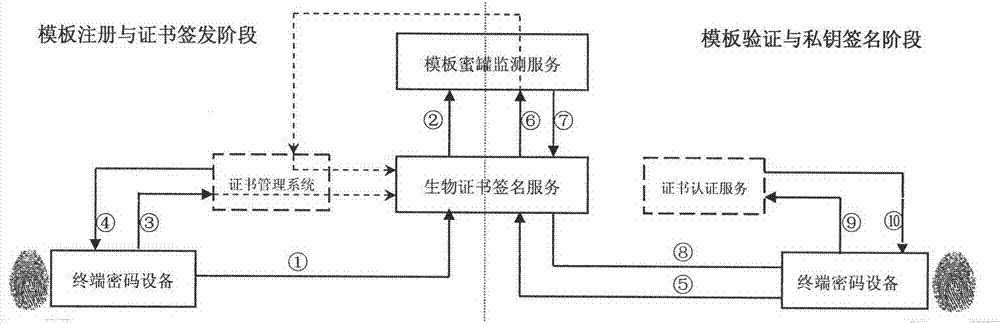
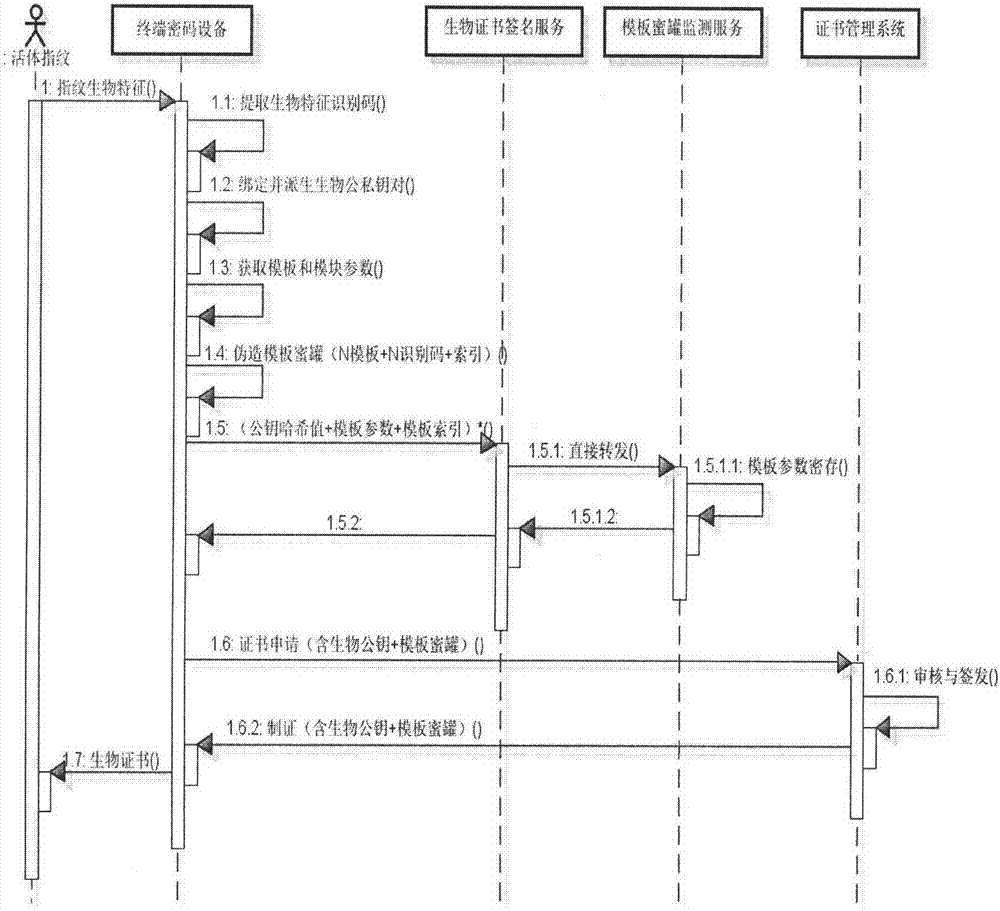
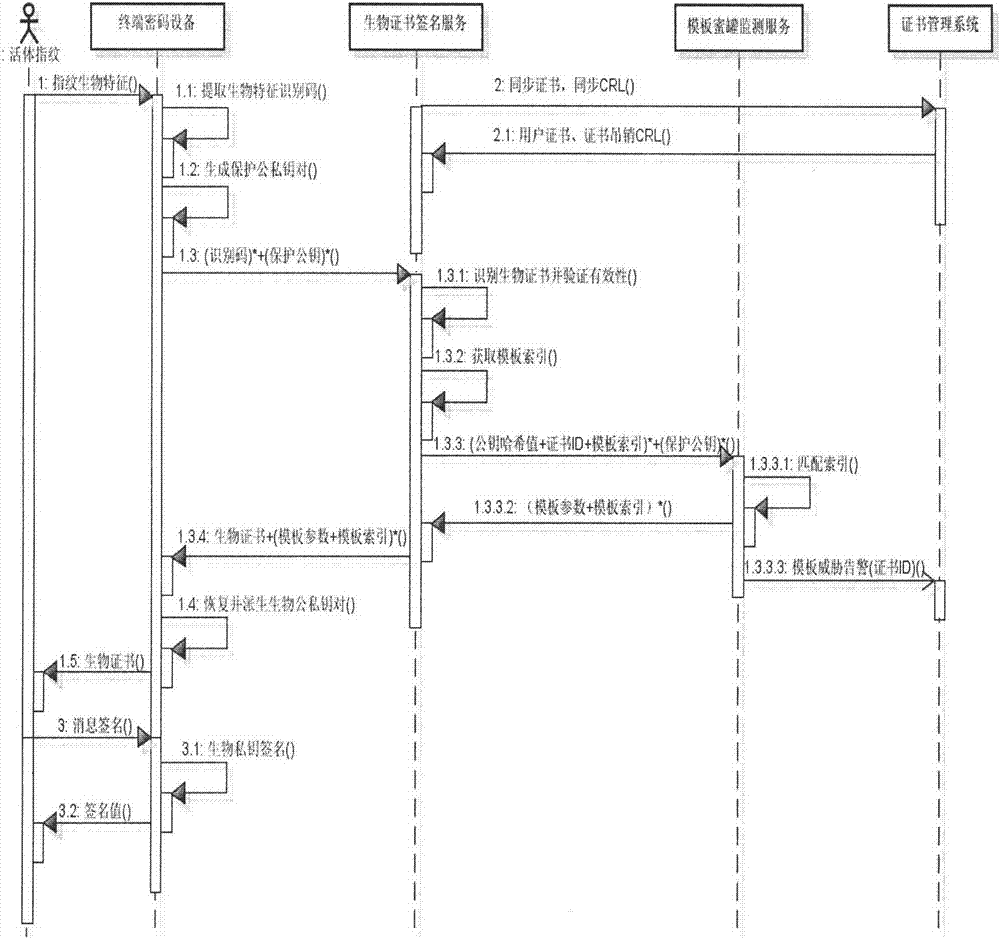
[0026] The main idea of this patent is, aiming at the template attack behavior problems that may exist in biometric templates, combined with digital certificates and using the principle of network honeypots to monitor template security threats in real time, to achieve online signature cryptographic operations based on biometric keys, such as figure 1 It includes two stages, namely template registration and certificate issuance stage, template verification and private key signature stage, which are described as follows:
[0027] 1) Template registration and certificate issuance stage (registration stage for short): Extract biometric identificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com