A biological key smart cryptographic key with security threat monitoring capability
A technology of intelligent password key and biological key, which is applied in the application field of biometrics, can solve the problems that biometric identification and encryption products cannot be quickly applied, and template attack behavior cannot be detected in real time, so as to achieve the effect of solving template attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so that the protection scope of the patent for the present invention can be defined more clearly.
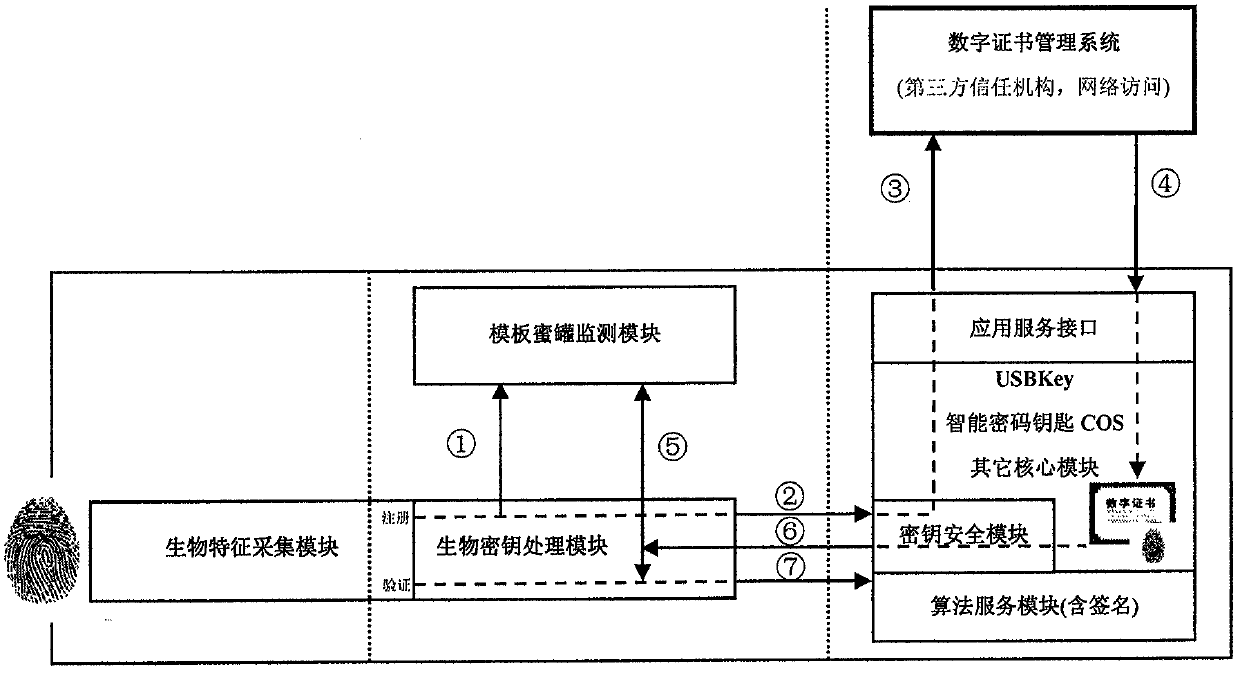
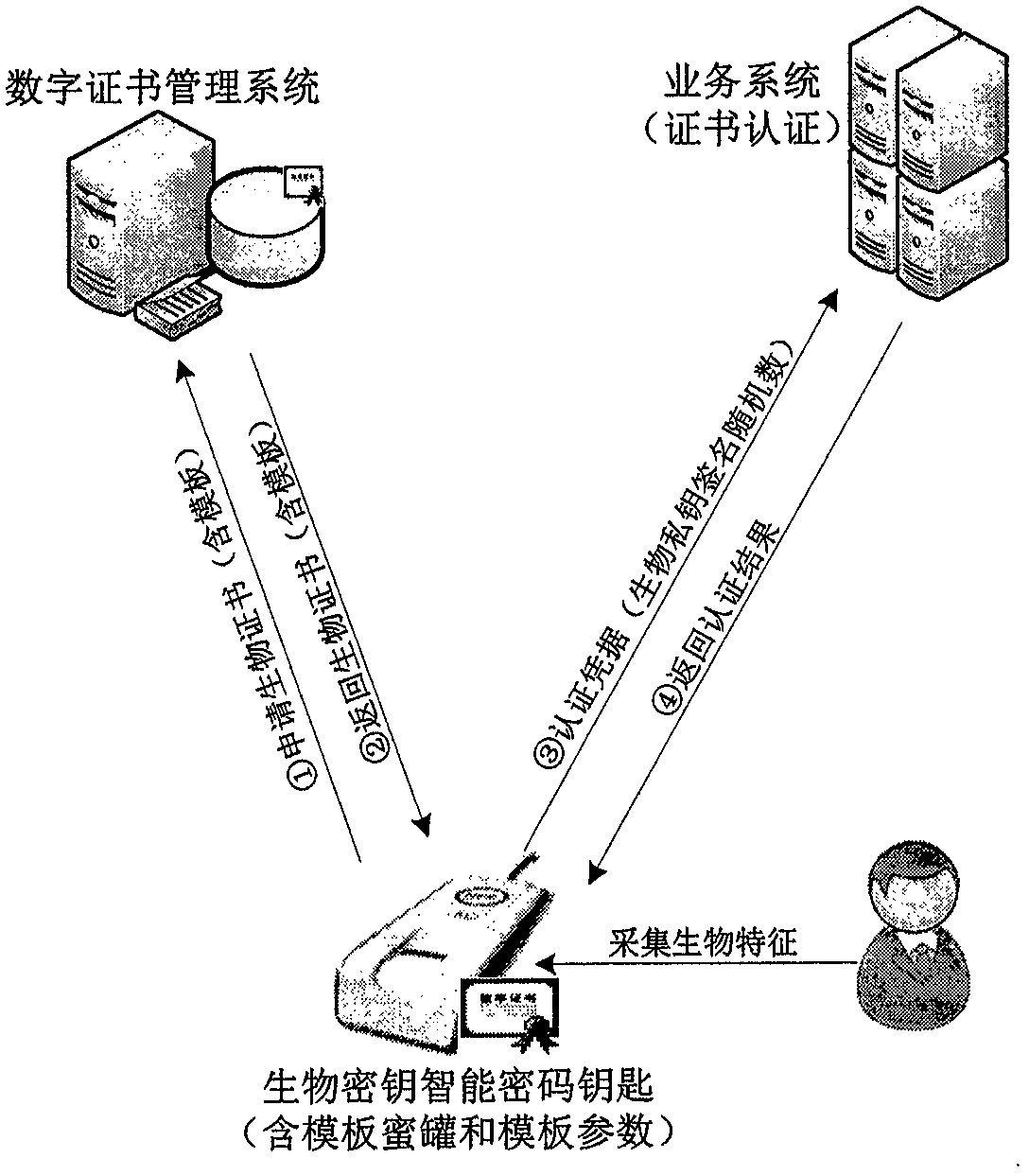
[0025] The main idea of the present invention is to replace the user signature public-private key pair involved in the USBKey smart cryptographic key with a biological public-private key pair generated in real time based on living fingerprints, and realize biological template security threat monitoring through certificate and honeypot technology.
[0026] The specific implementation steps are as follows:
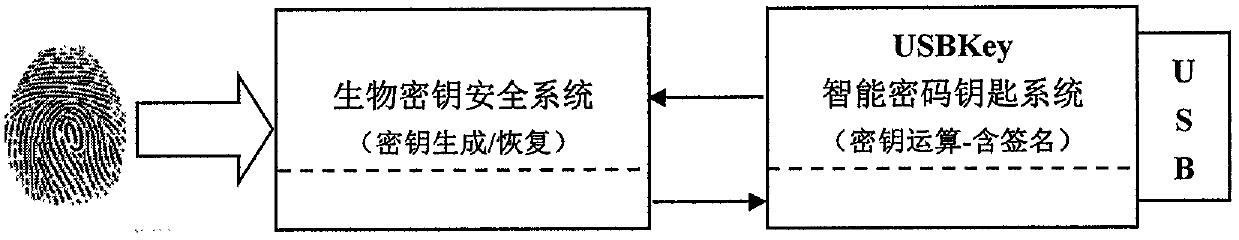
[0027] 1. The inventive method relates to the biological key intelligent password key and is made up of two parts, i.e. the USBKey intelligent password key system and the biological key security system (see figure 1 ). ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com