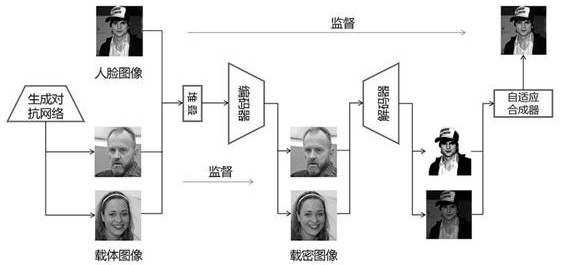
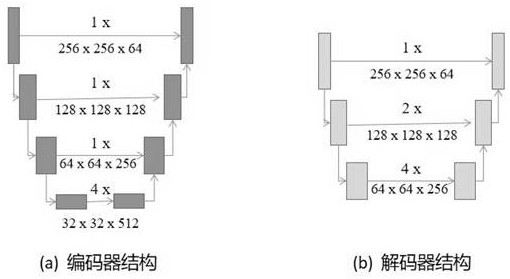
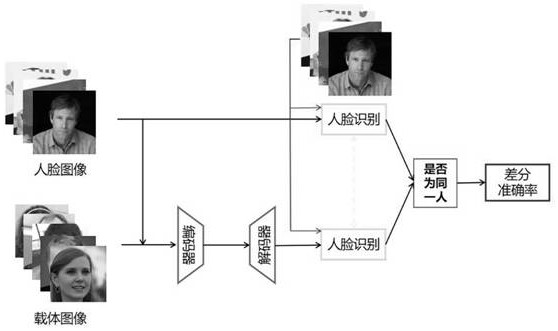
Robust efficient distributed face image steganography method
A face image, distributed technology, applied in the field of image steganography and computer vision, can solve the problem of not being able to fit the task of face image steganography well, achieve real-time high-resolution image decoding, improve robustness and safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0061] 1. Dataset
[0062] For the secret image, the LFW data set is selected. LFW is a commonly used data set for face recognition at present. The face pictures provided are all from natural scenes in life, so the recognition difficulty will increase, especially due to multiple poses, lighting, and expressions. Due to factors such as age, occlusion, etc., even the photos of the same person are very different, so it is very consistent with the face image in the real scene. The LFW data set has a total of 13,233 face images, and each image has a corresponding name. There are 5,749 people in total, and most of them have only one picture, and the size of each picture is 250×250. But it will be scaled to 256×256 for training or testing. When training, select 10,000 of them as the training set and 3,232 as the test set, and there is no intersection between the training set and the test set pictures.
[0063] The carrier image is not suitable for using existing face images due to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com