Patents
Literature
51 results about "Domain level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Domain level indicates that server is capable of doing certain operations. Domain levels allows to migrate to a never version of freeIPA and activate new features when all servers are migrated and compatible with that particular feature. The domain level has to be increased manually, it is not raised during upgrade.
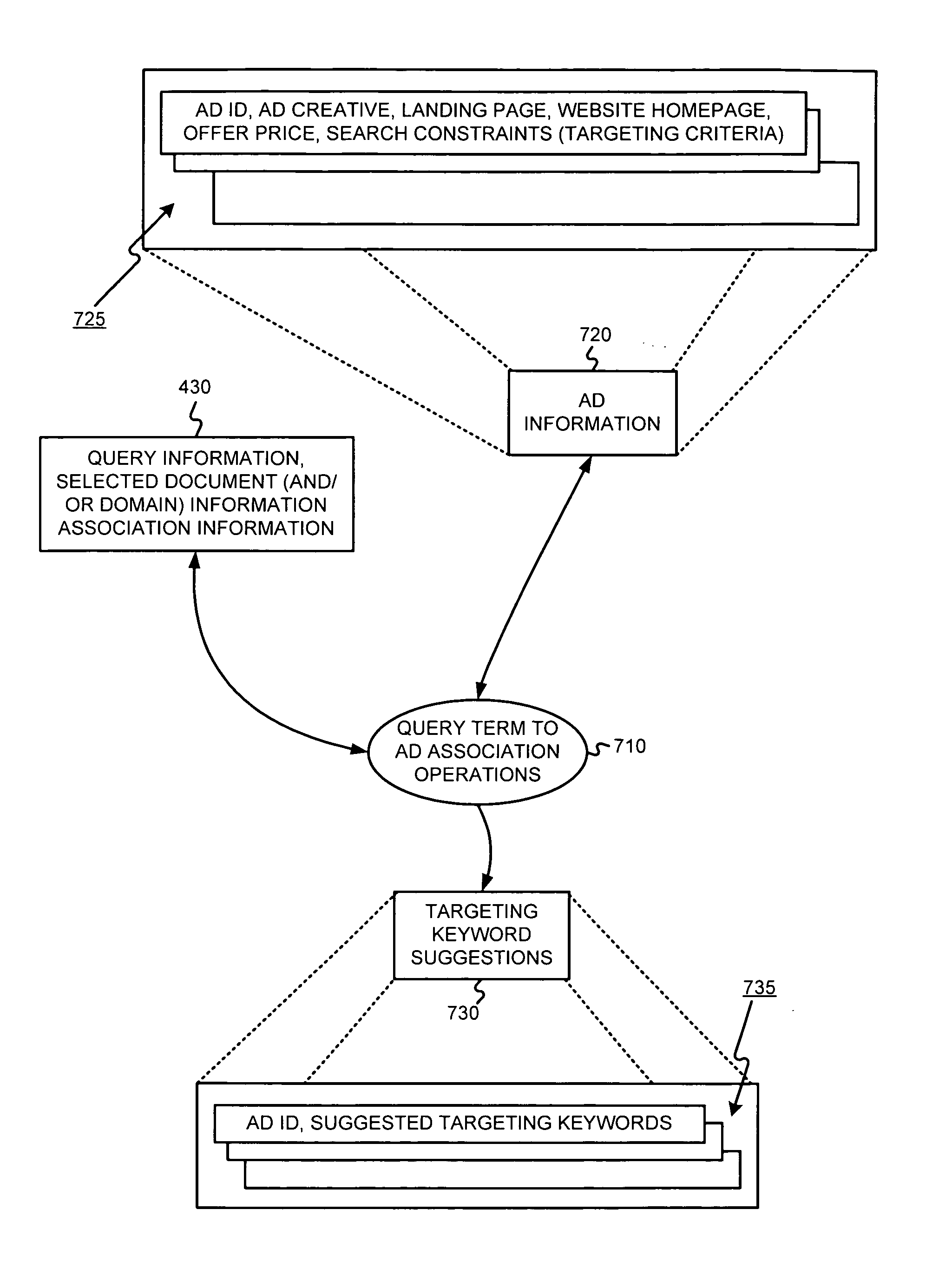
Determining ad targeting information and/or ad creative information using past search queries
InactiveUS20050222901A1Web data indexingUnstructured textual data retrievalDomain levelPaper document
Ad information, such as ad targeting keywords and / or ad creative content for example, may be determined using aggregated selected document-to-query information associations. For example, popular terms and / or phrases also associated with a selected document may be used as ad targeting keywords and / or ad creative content for an ad having the document as a landing page. Query information may be tracked on a per document level, a per domain level, etc. The determined ad information may be used to automatically populate an ad record, or may be provided to an advertiser as suggested or recommended ad information.
Owner:GOOGLE LLC
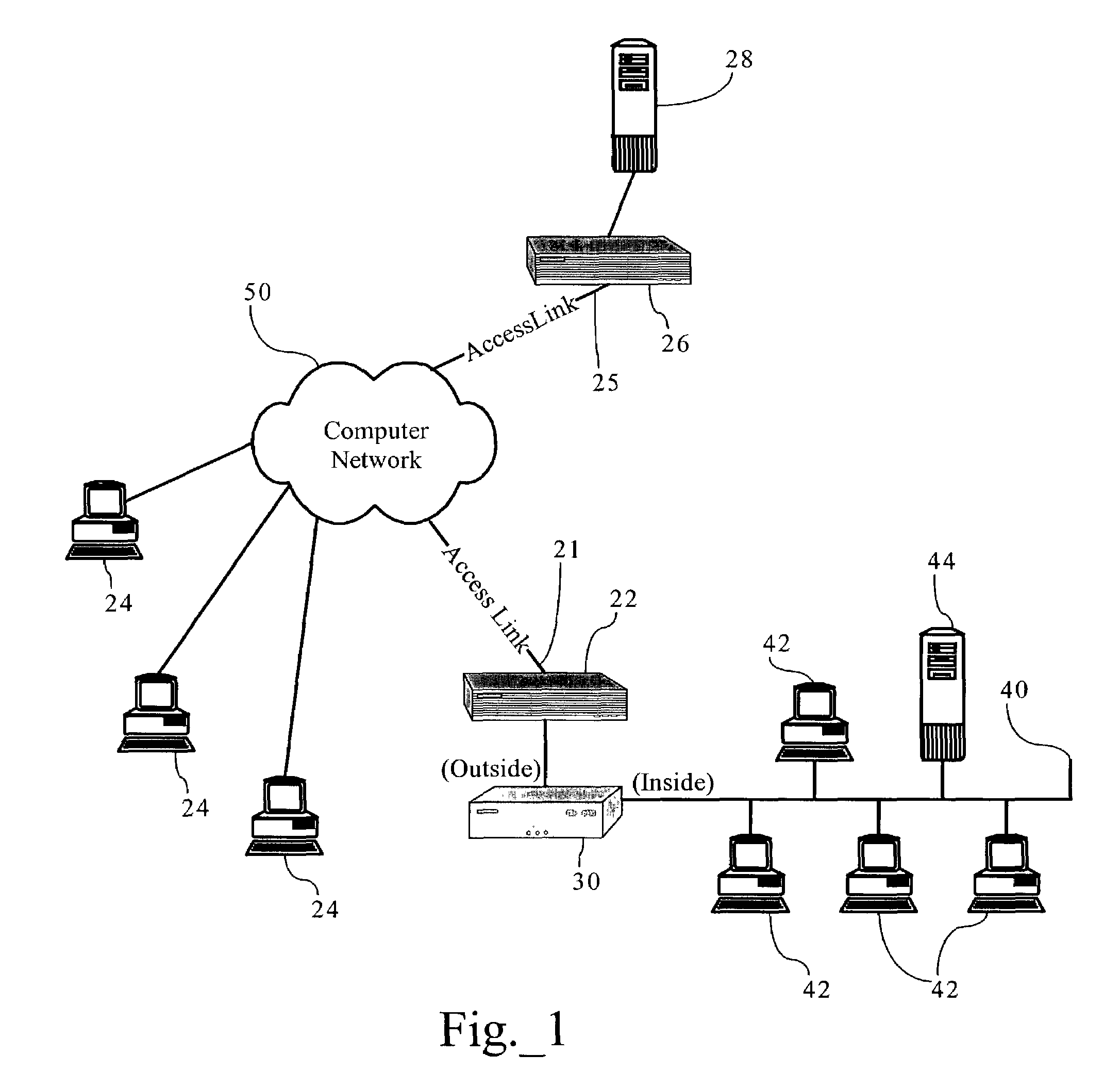
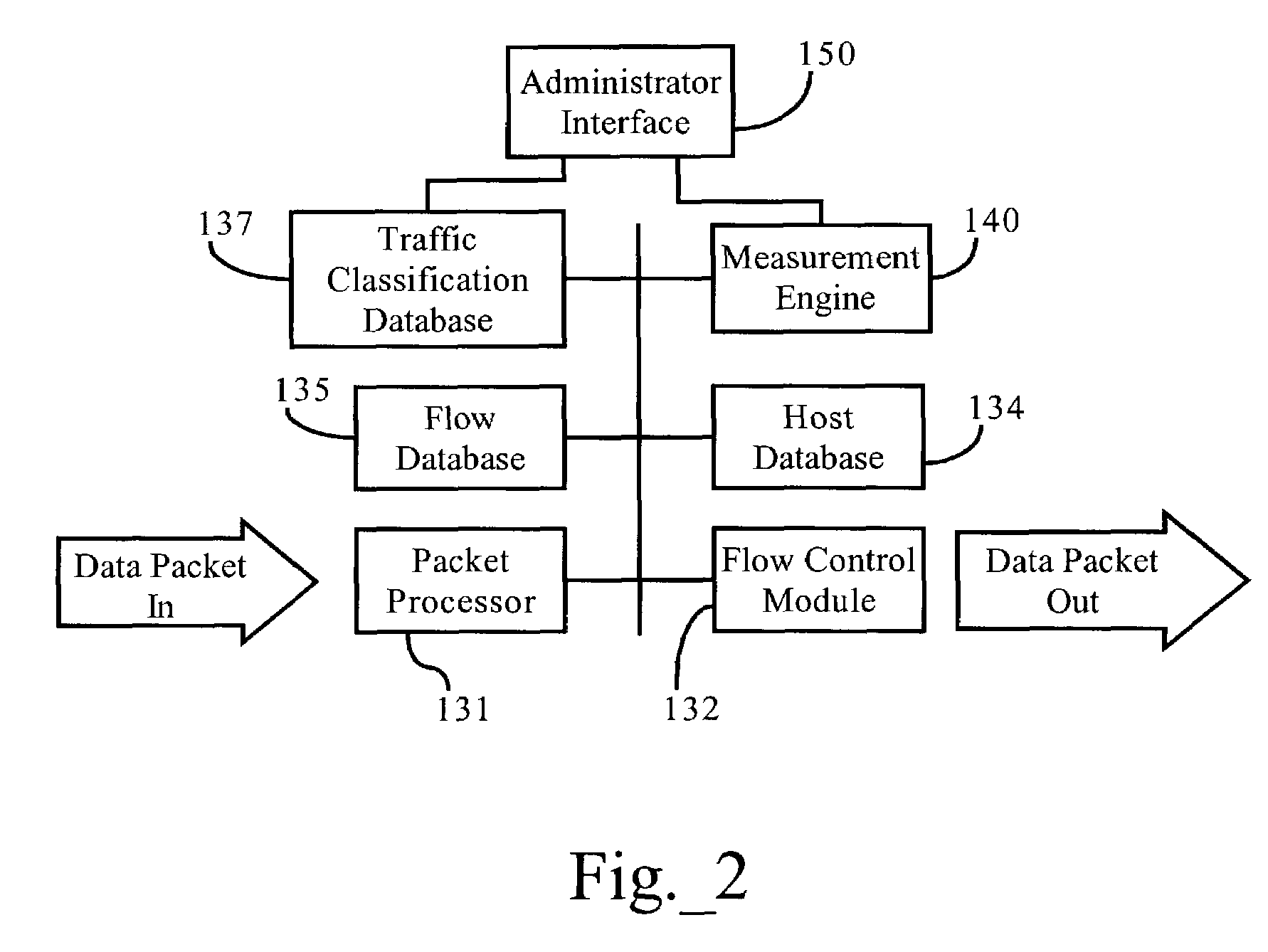
Classification data structure enabling multi-dimensional network traffic classification and control schemes
ActiveUS7433304B1OptimizationEasy to transportError preventionTransmission systemsTraffic capacityDomain level
Methods, apparatuses and systems facilitating hierarchical network traffic classification and resource allocation schemes. In one embodiment, the present invention provides traffic classification data structure facilitating creation and configuration of multi-dimensional, hierarchical network resource allocation schemes. The present invention features a hierarchical network traffic classification scheme that allows users to logically embed (or otherwise associate) one or more reference trees within selected traffic class nodes of a given traffic classification tree. In one embodiment, an administrator can create a pool of referenceable traffic classification trees and select such trees or sub-trees from the pool to achieve a variety of different traffic classification configurations. The present invention, in one embodiment, also facilitates the implementation of a system or domain-level workflow interface that features managed access links as configurable objects as opposed to the network devices operating on the access links.
Owner:CA TECH INC
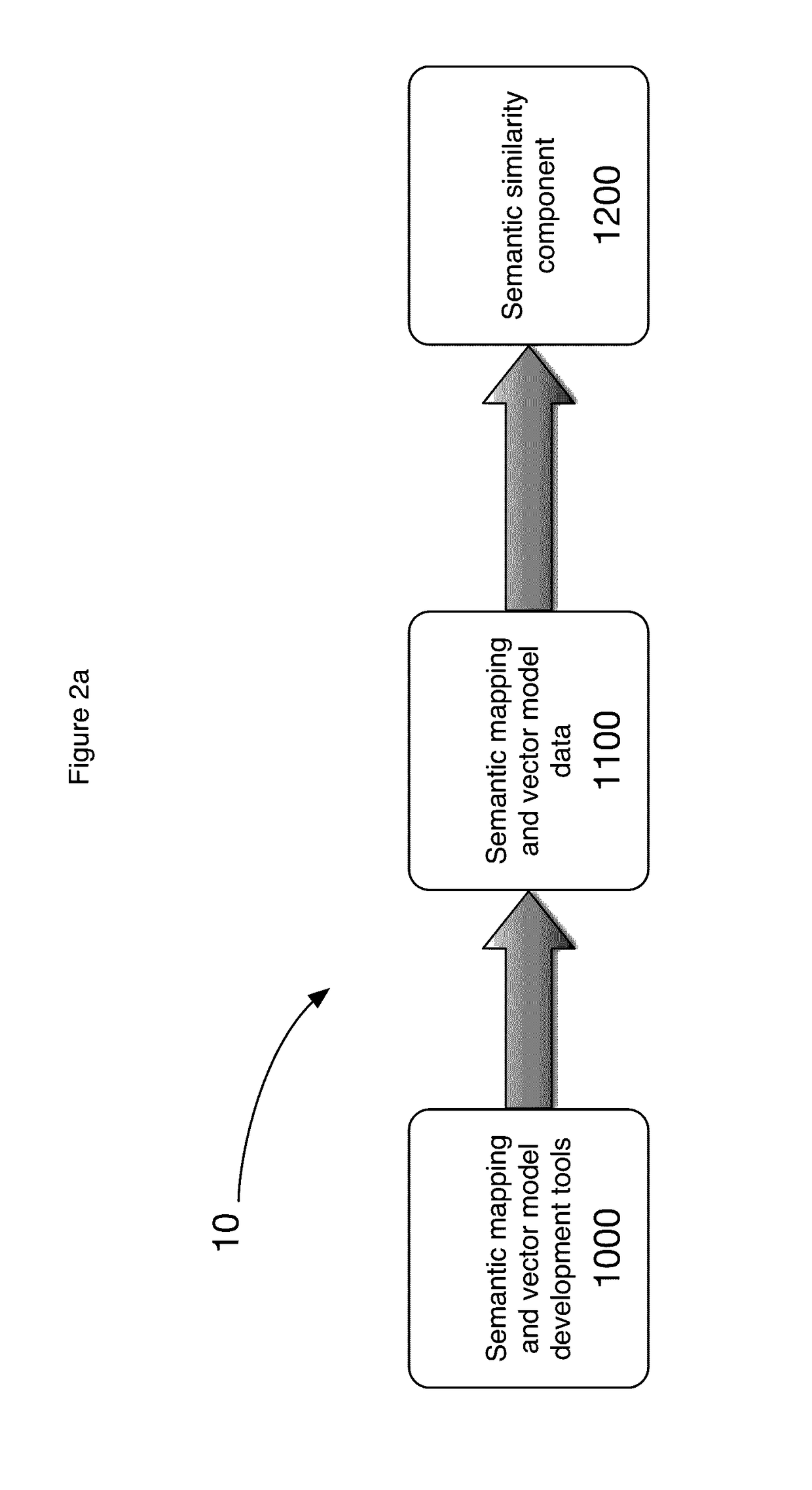
Apparatus, system and method for application-specific and customizable semantic similarity measurement
ActiveUS20160350283A1Semantic analysisSpecial data processing applicationsDocumentation procedureDomain level
The present invention relates to an apparatus system and method for creating a customizable and application-specific semantic similarity utility that uses a single similarity measuring algorithm with data from broad-coverage structured lexical knowledge bases (dictionaries and thesauri) and corpora (document collections). More specifically the invention includes the use of data from custom or application-specific structured lexical knowledge bases and corpora and semantic mappings from variant expressions to their canonical forms. The invention uses a combination of technologies to simplify the development of a generic semantic similarity utility; and minimize the effort and complexity of customizing the generic utility for a domain- or topic-dependent application. The invention makes customization modular and data-driven, allowing developers to create implementations at varying degrees of customization (e.g., generic, domain-level, company-level, application-level) and also as changes occur over time (e.g., when product and service mixes change).
Owner:INFORMATION EXTRACTION SYST
Hierarchy for characterizing interactions with an application
InactiveUS7805510B2Improve rendering capabilitiesIncrease capacityError detection/correctionDigital computer detailsTraffic capacityMonitoring system
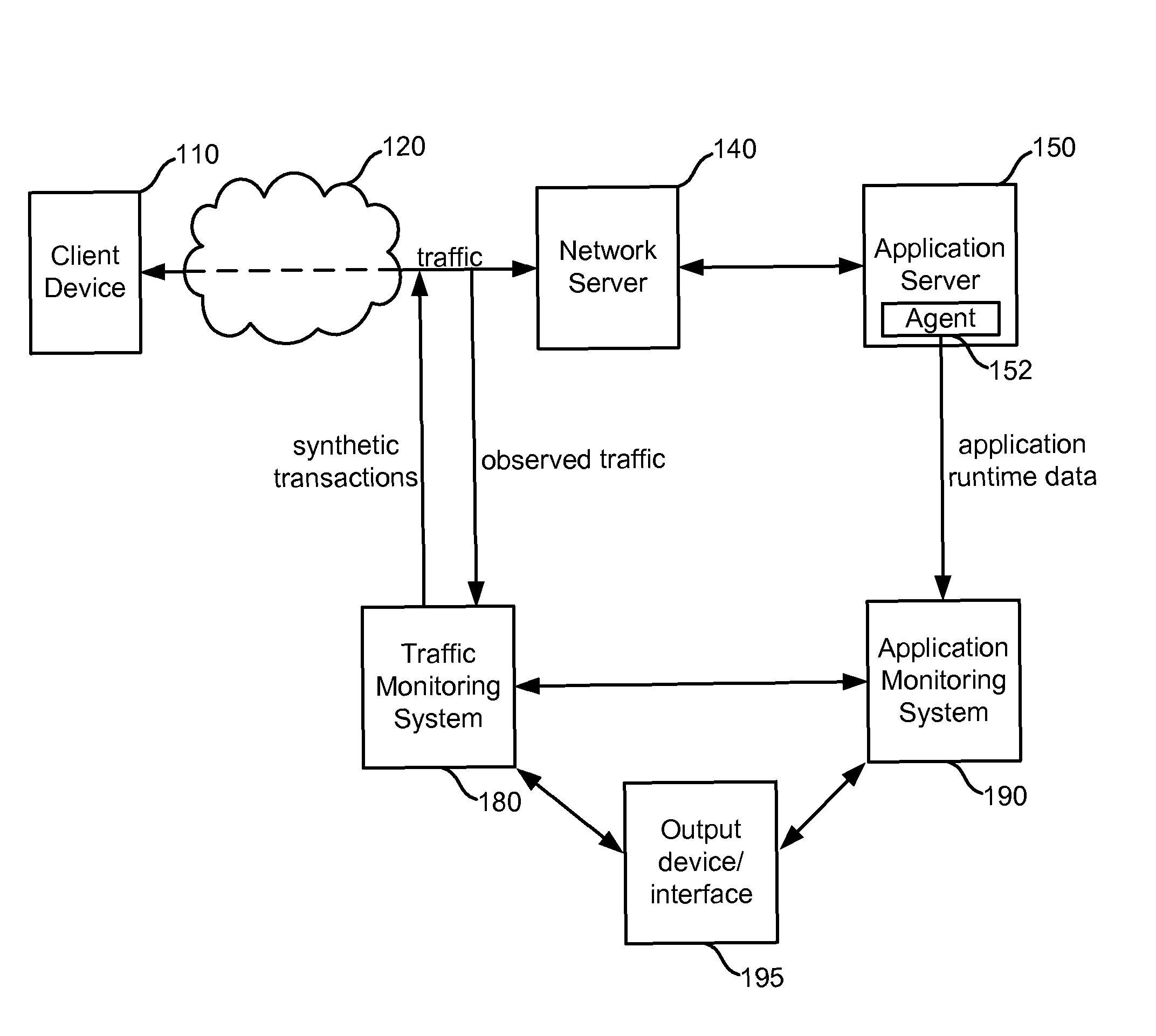
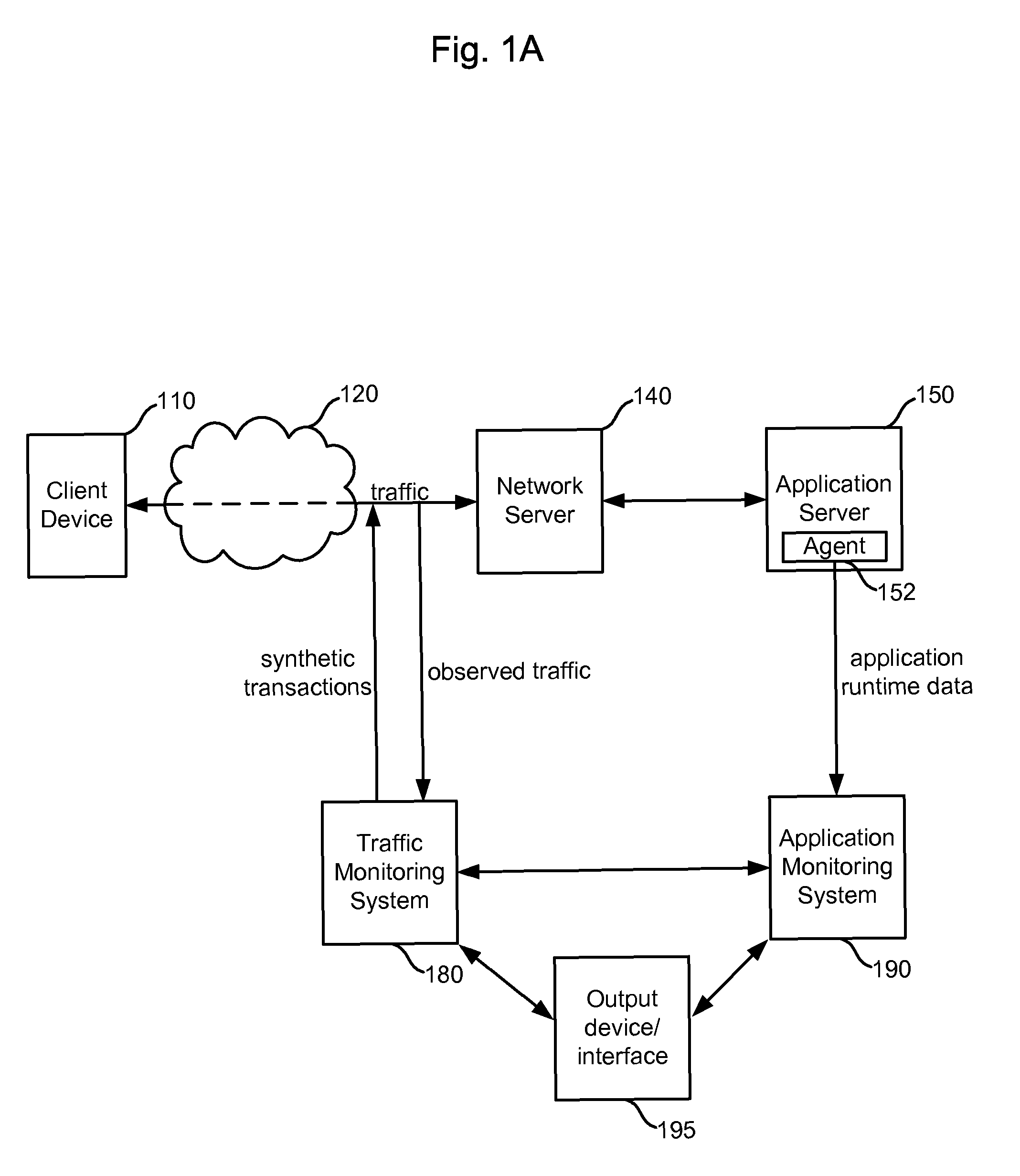
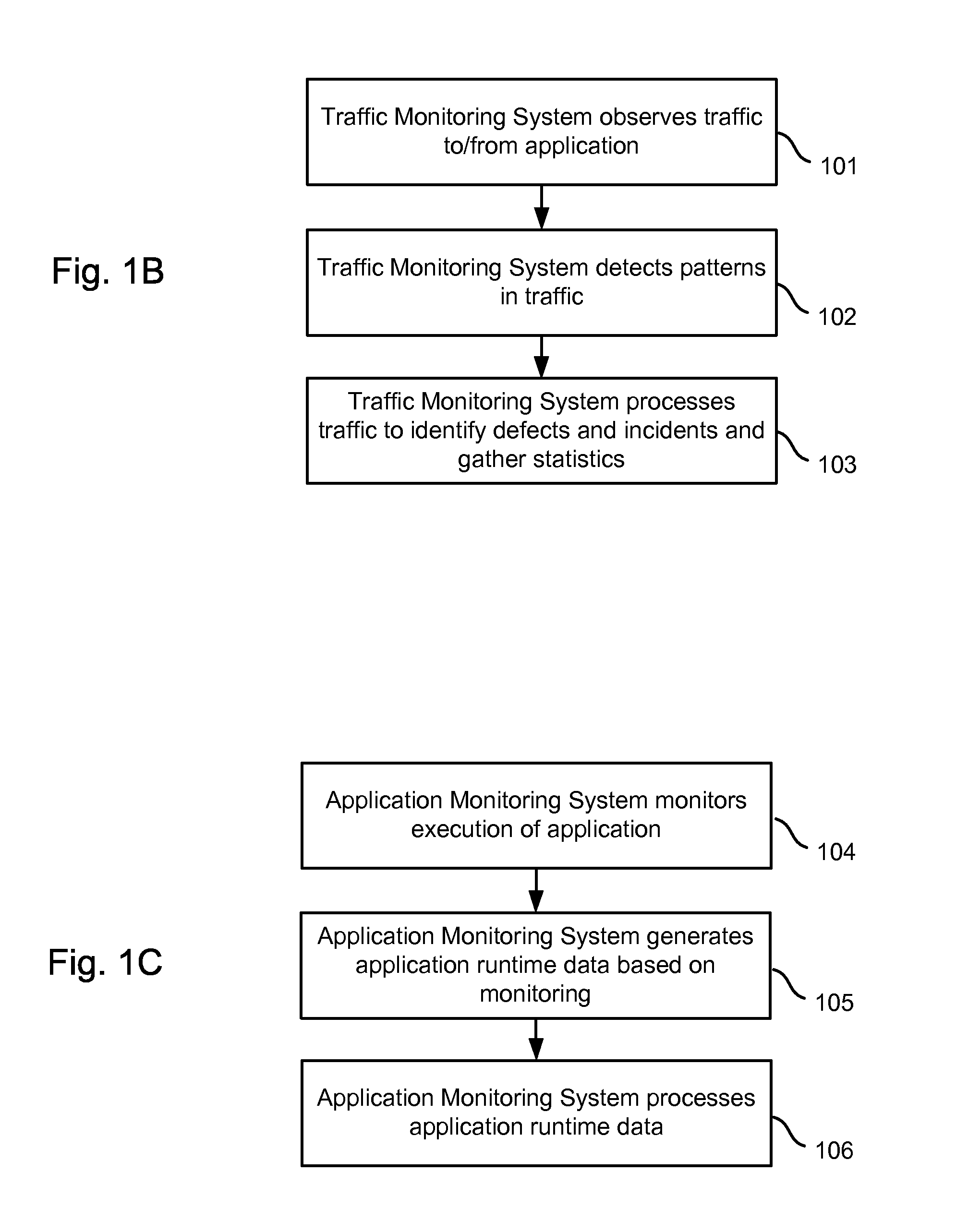
Application runtime data is obtained from an application monitoring system which monitors execution of an application, and traffic monitoring data is obtained from a traffic monitoring system which monitors traffic to / from the application as the clients interact with the application. Corresponding application runtime data and traffic monitoring data can be selectively output to assist an operator in investigating an anomalous condition. The data can be classified and selectively output according to one or more hierarchies which characterize the interactions. The hierarchies can include a domain level, a business process level (where a domain is made up of a number of business processes), a business transaction level (where a business process is made up of different business transactions), an individual transaction level (where a business transaction is made up of different transactions), and a transaction component level (where a transaction is made up of one or more transaction components).
Owner:CA TECH INC
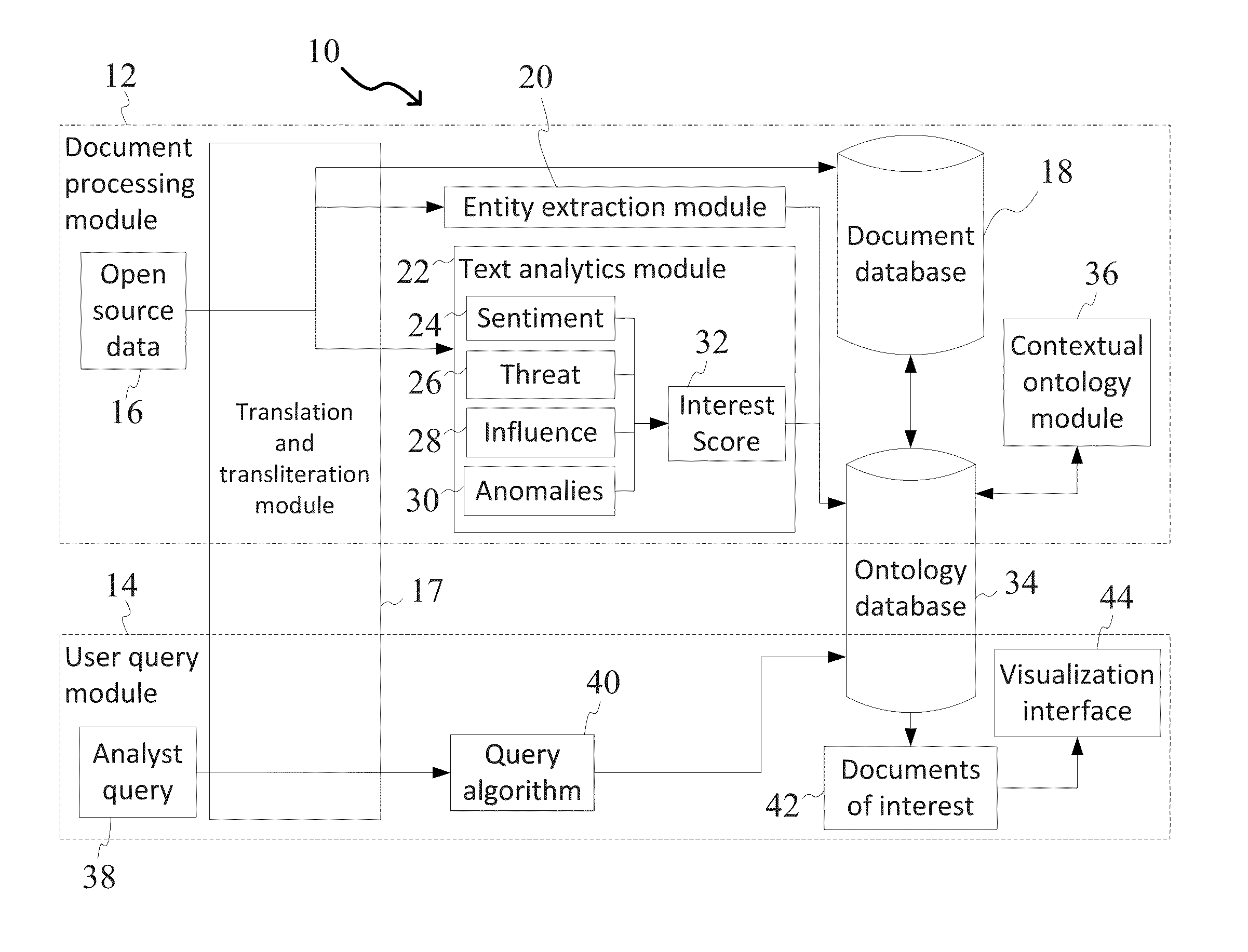
System and Method for Data Mining Using Domain-Level Context
InactiveUS20140195518A1Quick navigationQuickly find documentsDigital data information retrievalDigital data processing detailsGraphicsDomain level
A system and method for data mining using domain-level context is provided. The system includes a computer system and a contextual data mining engine executed by the computer system. The system mines and analyzes large volumes of open-source documents / data for analysts to quickly find documents of interest. Documents / data are encoded into an ontological database and represented as a graph in the database linking contextual entities to find patterns and anomalies in context. Documents are separately analyzed by the system and scored on several different scales. The resulting information could be presented to the user via a visualization interface which allows the user to explore the data and quickly navigate to documents of interest.
Owner:OPERA SOLUTIONS
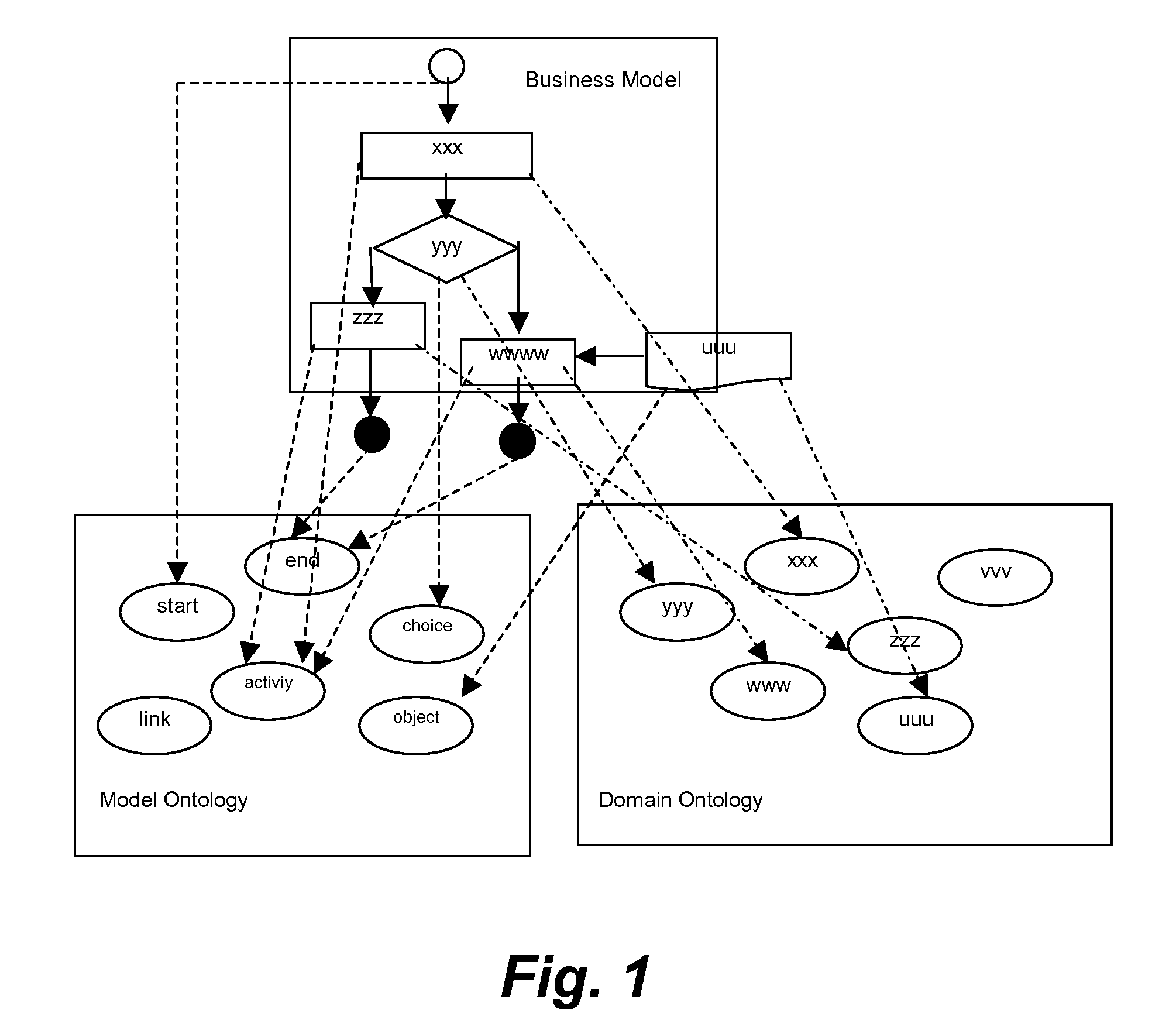
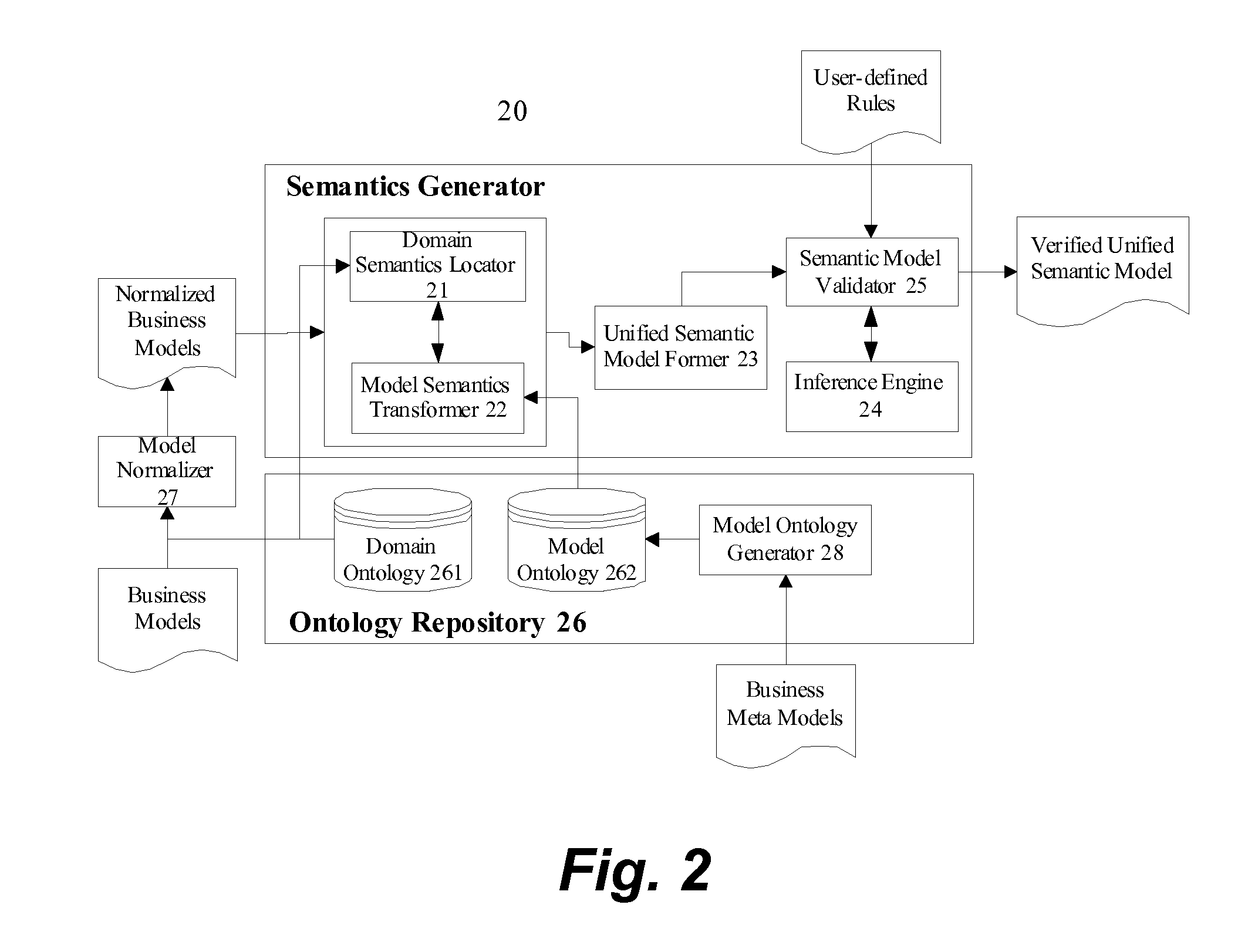
Method and apparatus to enable integrated computation of model-level and domain-level business semantics
InactiveUS20070112718A1Business value is tremendousKnowledge representationSpecial data processing applicationsDomain modelDomain level
A method is provided for integrating model and domain semantics in business models. The method includes a business model inputting step for inputting the business model to be realized; a domain semantics locating step for locating the domain semantics of the modeling element of the business model within the domain ontology and outputting the corresponding domain model semantics; a model semantics transforming step for transforming the modeling element of the business model into business model semantics that are represented by a model ontology; and a unified semantic model forming step for combining the aforesaid business model semantics and domain model semantics and then outputting a unified semantic model. The teachings disclosed are directed to facilitate the integration and utilization of the semantics embedded in business models.
Owner:IBM CORP
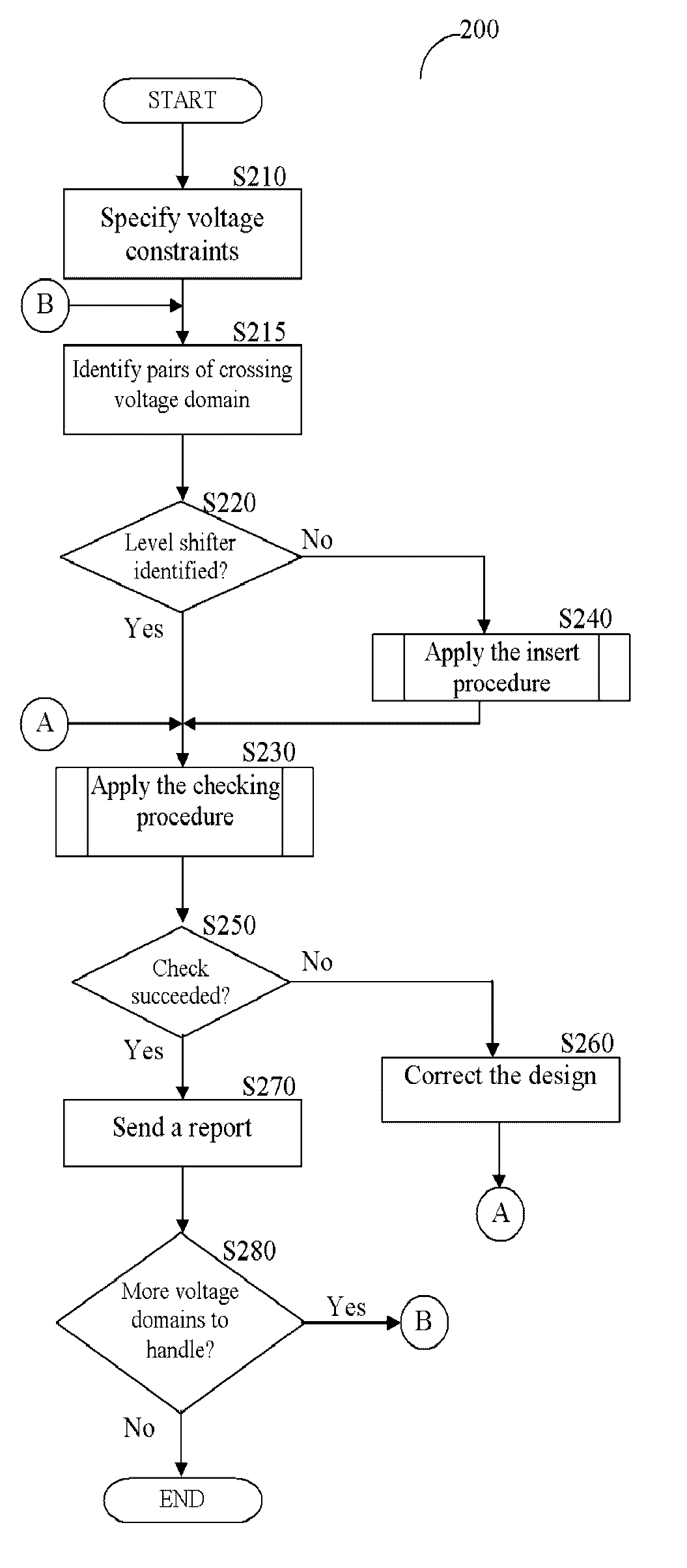
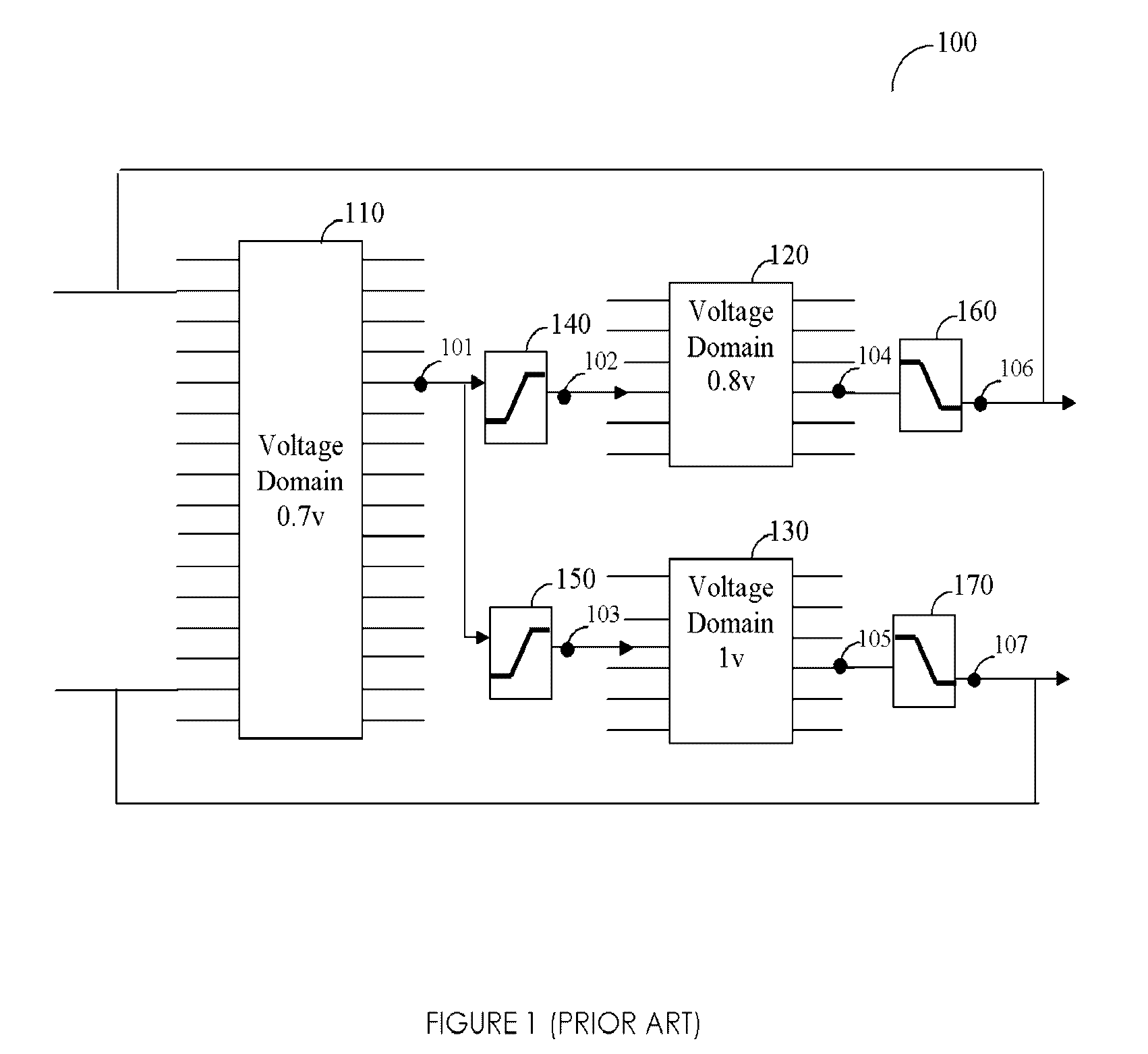
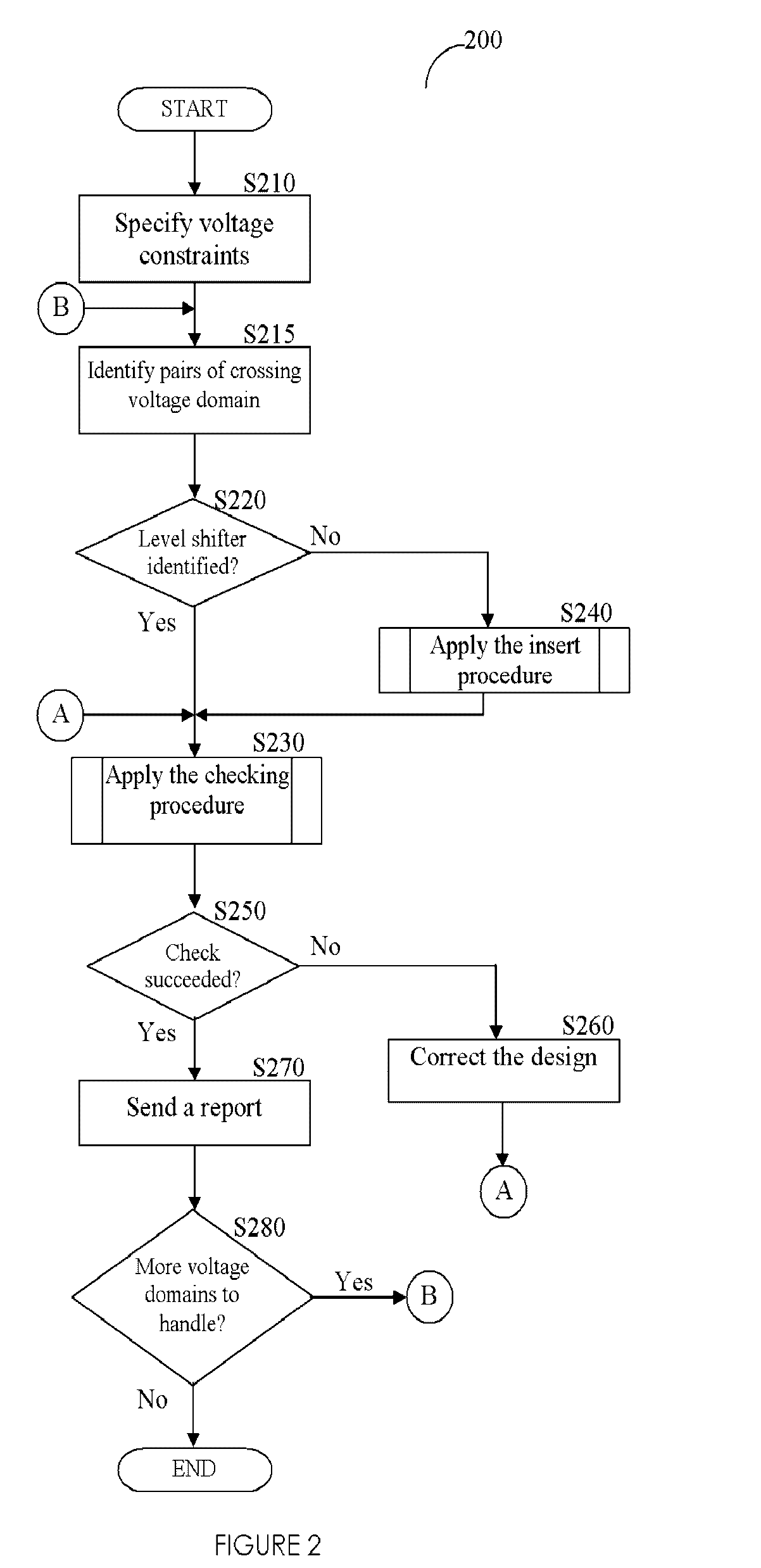
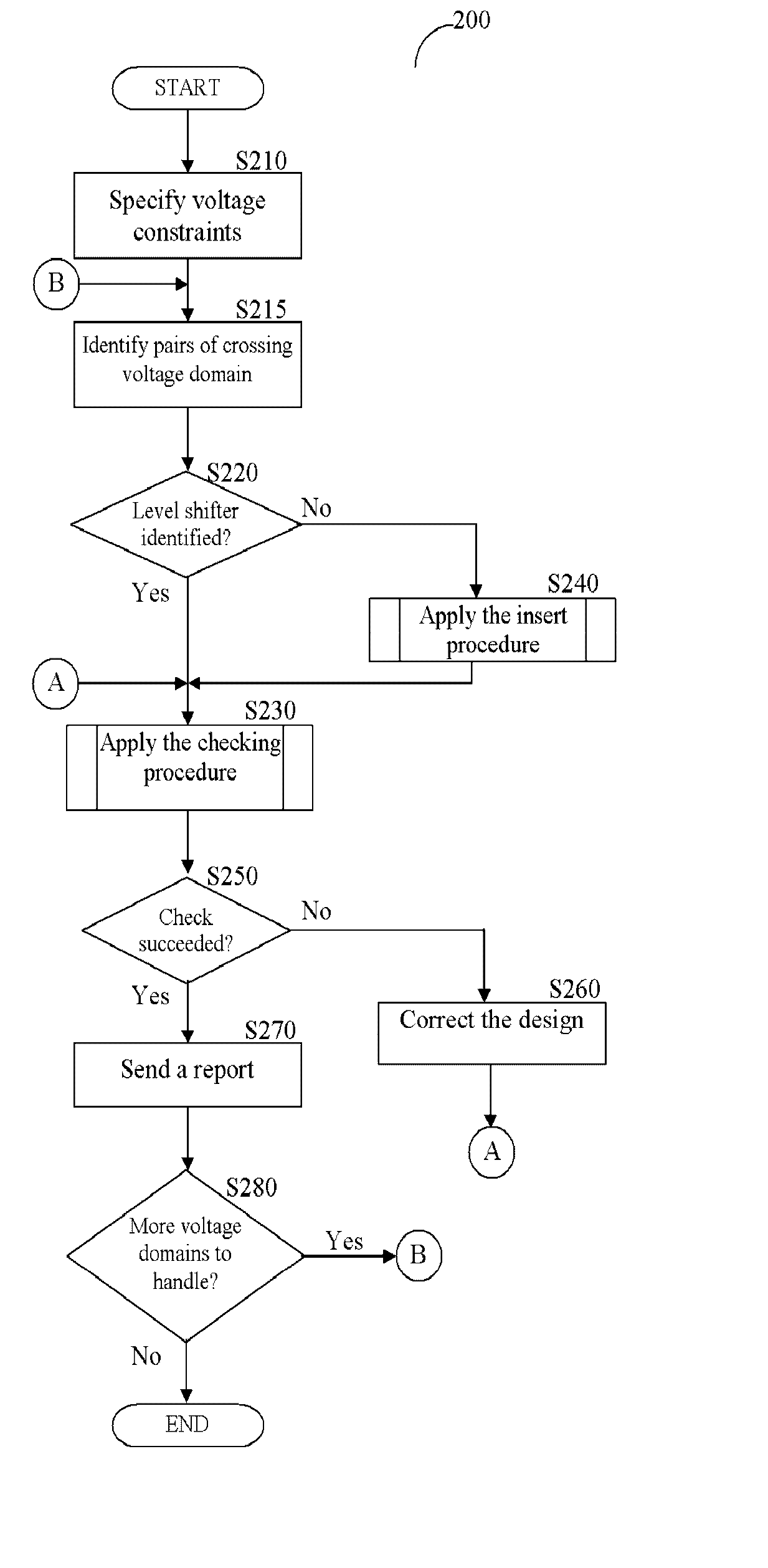
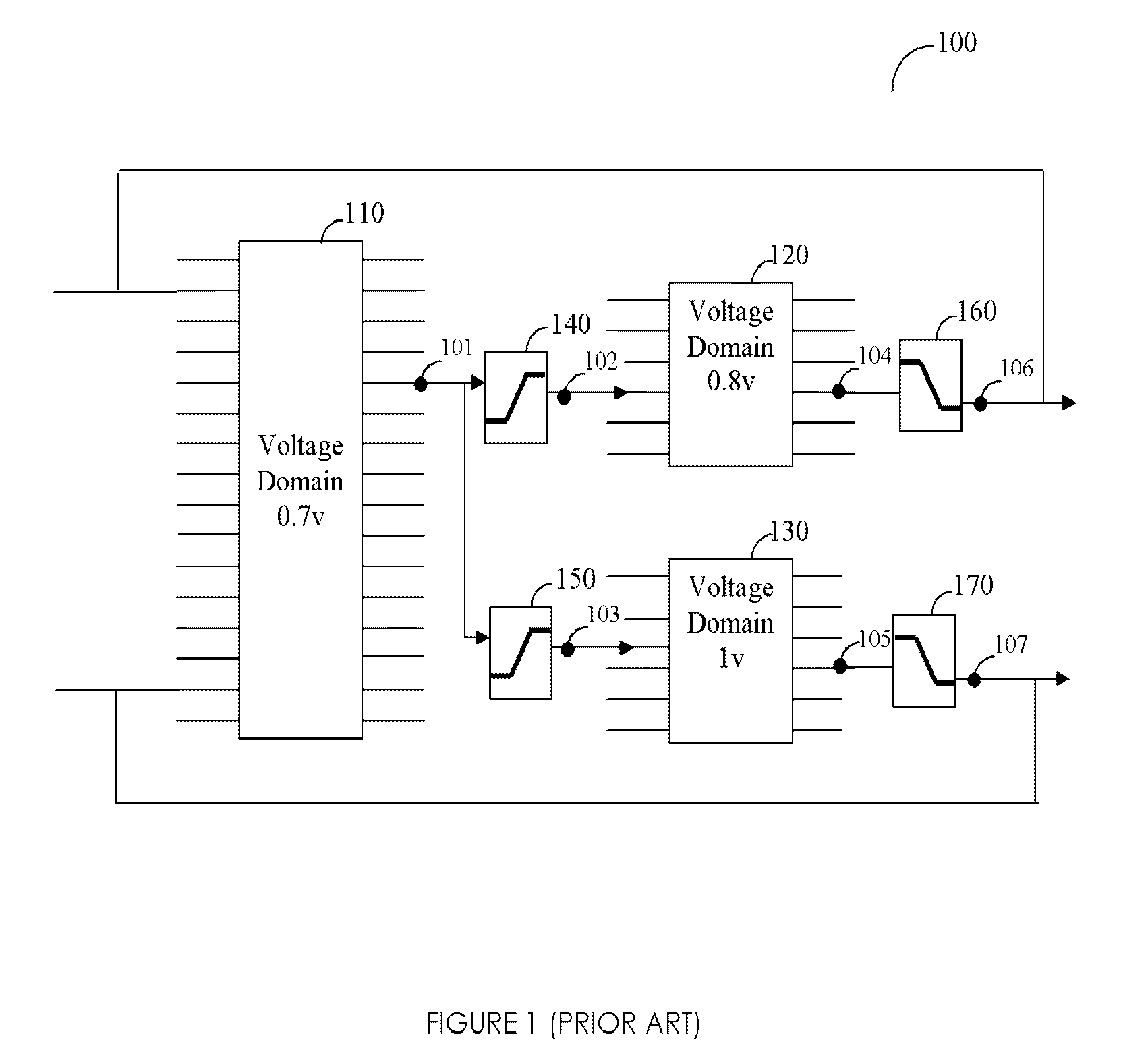
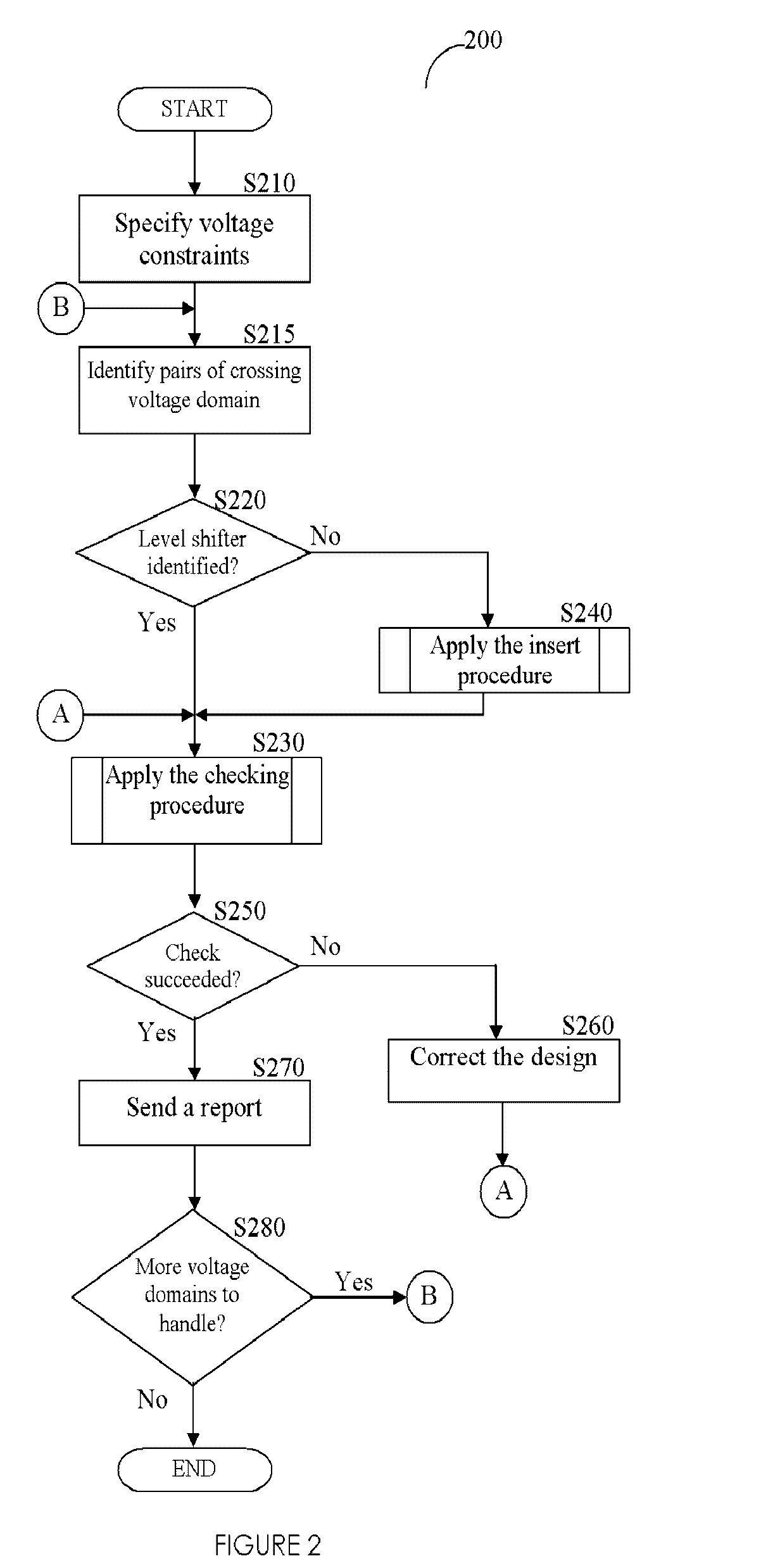
Method, system, and computer program product for automatic insertion and correctness verification of level shifters in integrated circuits with multiple voltage domains
ActiveUS7152216B2Automatic detectionCAD circuit designSoftware simulation/interpretation/emulationDomain levelIntegrated circuit layout
Level shifter modules, used in integrated circuits (ICs), are automatically inserter and their correctness verified. A level shifter module for signals crossing voltage domains is generated, and instances thereof are inserted in a pre-determined voltage domain. Several checks ensure the correctness of the inserted level shifter module. The level shifter modules are instantiated based on user-defined voltage constraints.
Owner:SYNOPSYS INC
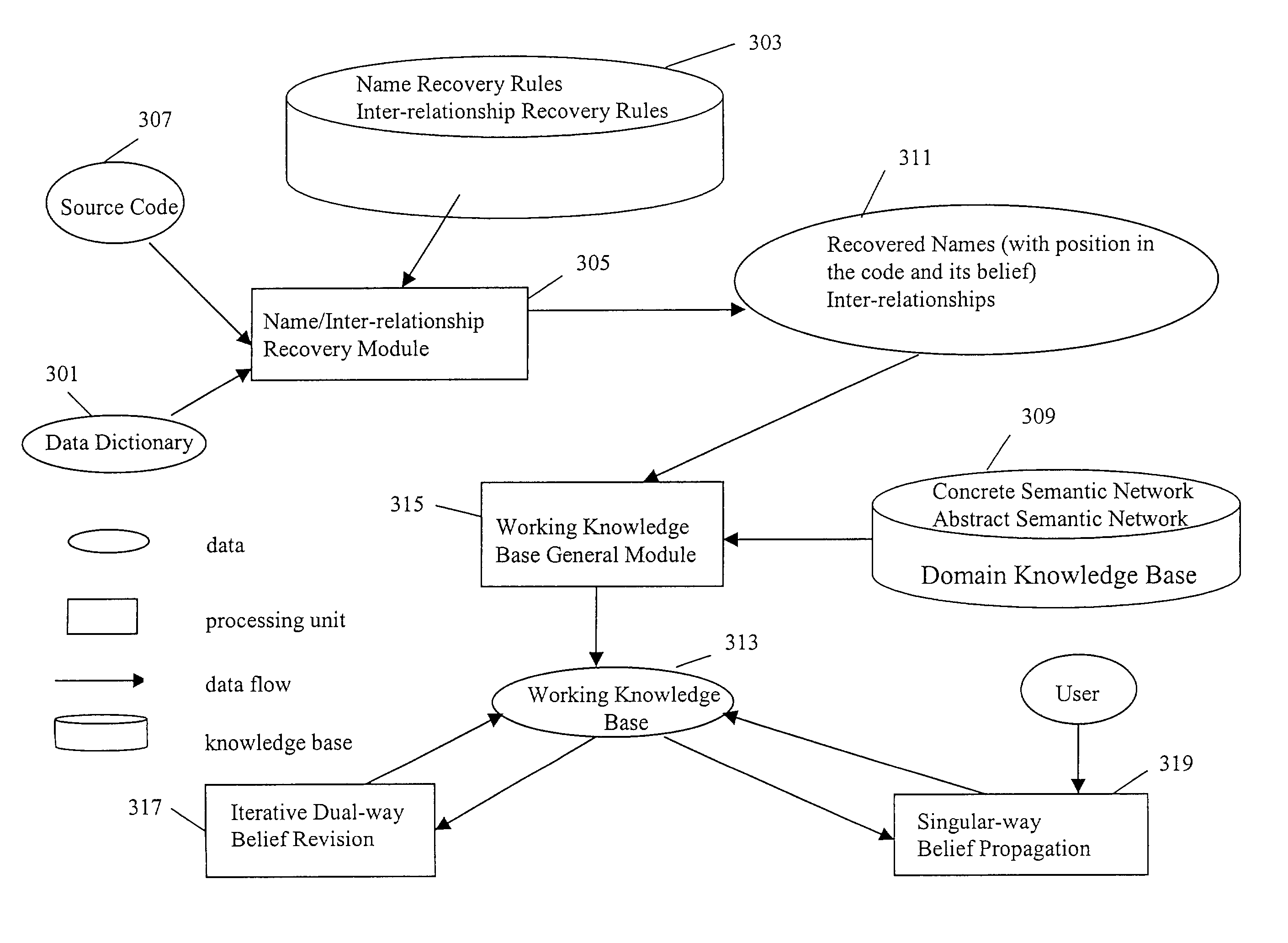
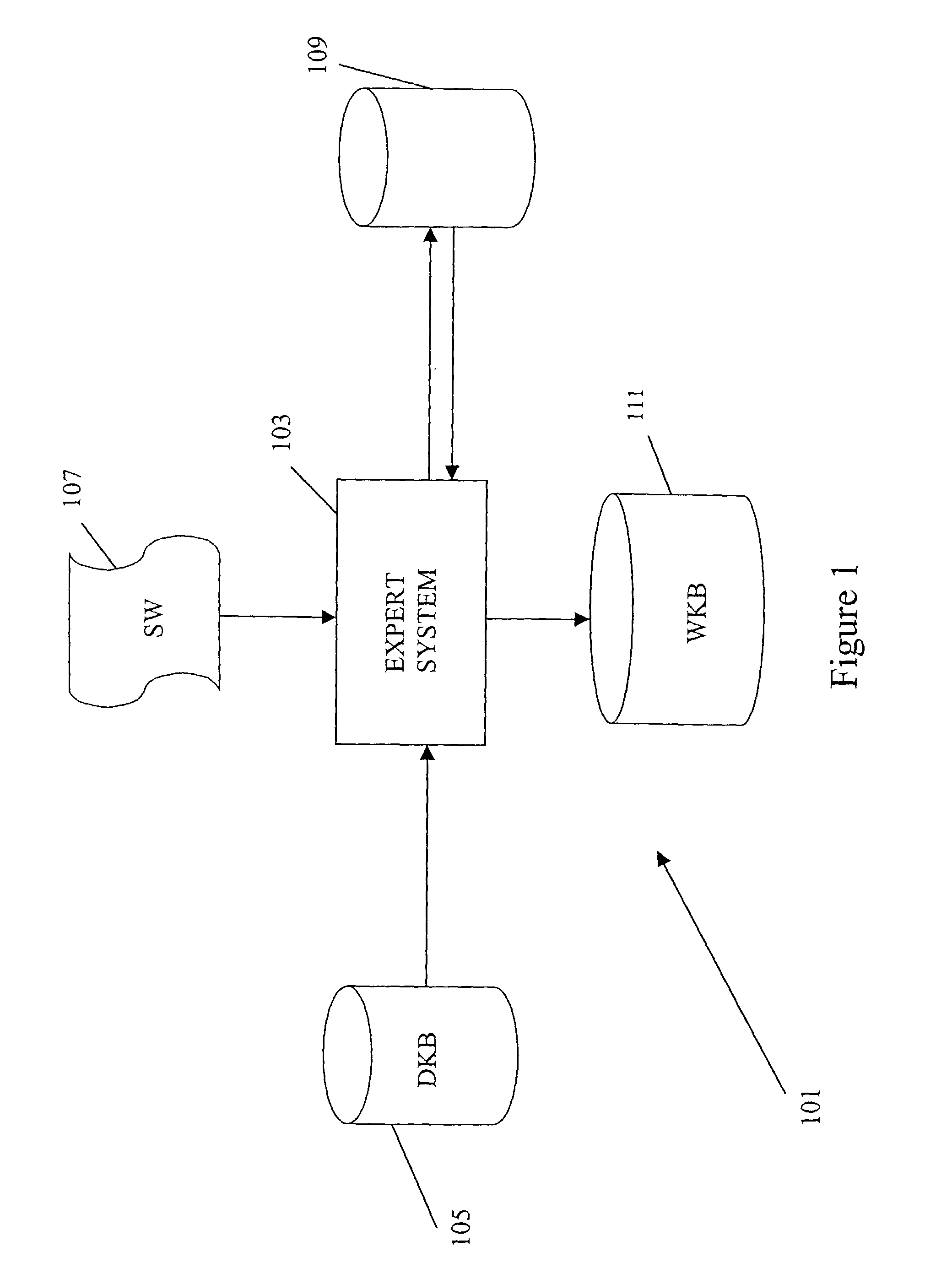
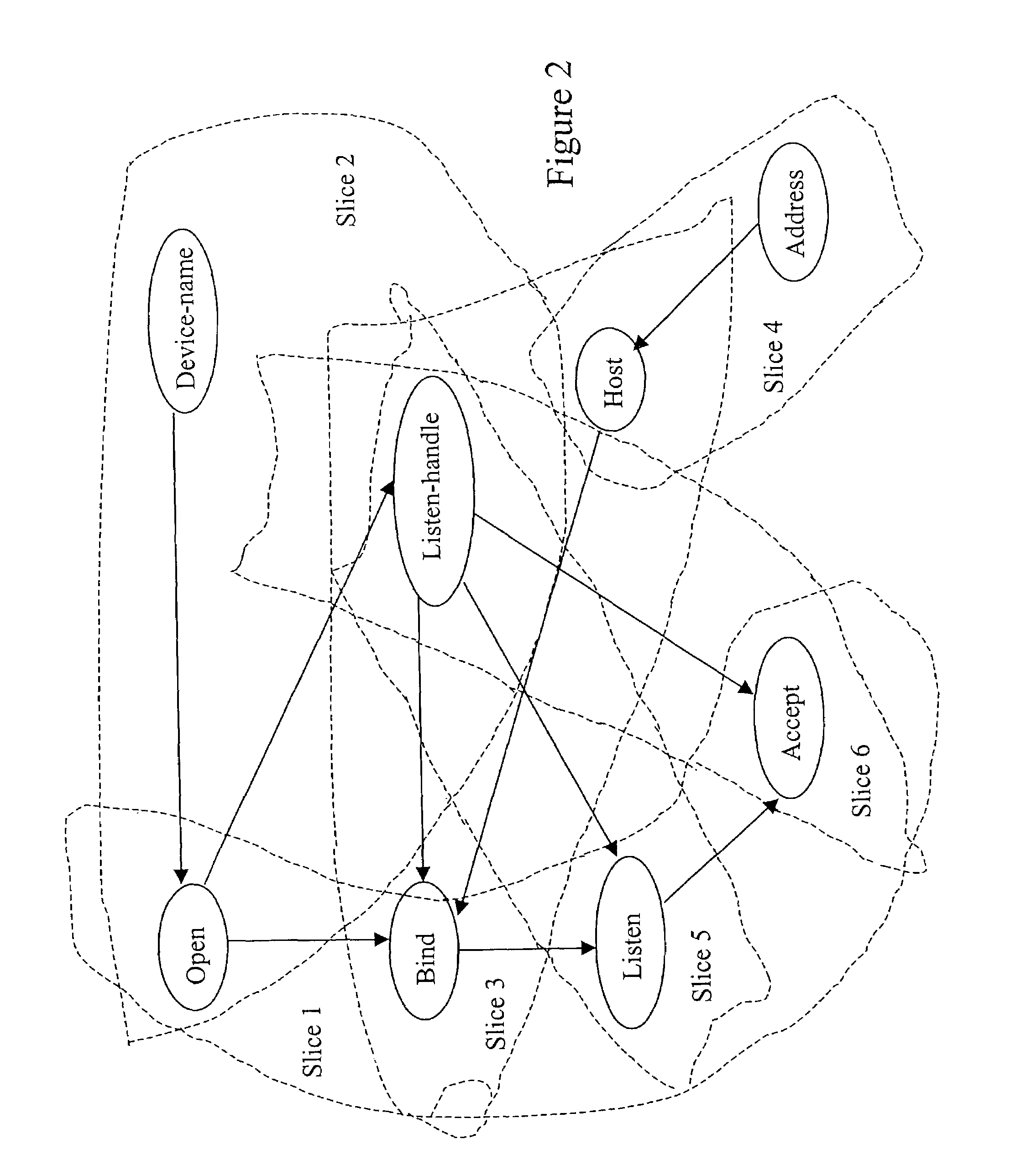
Method and apparatus for extracting knowledge from software code or other structured data
InactiveUS7177852B2Easy can be completely matchedIncrease weightKnowledge representationSpecial data processing applicationsDomain levelComputer-aided
A method for knowledge representation and management is disclosed which has particular but not exclusive application in knowledge recovery techniques. To help with program understanding, software maintainers use computer aided reverse engineering (CARE) tools which utilize techniques such as syntax analysis, structural analysis, and domain knowledge base analysis (DKBA). Known DKBA methods are complex since the domain knowledge recovery relies on the use of knowledge at different layers while some elements of the knowledge at domain level is not used at all. In the disclosed method for representing knowledge in a knowledge base, the knowledge is represented by a set of one or more concepts and by one or more first type of relationships between two or more or said concepts. The method comprises dividing the set of concepts into a plurality of sub-sets, each sub-set comprising a set of concepts related to a sub-set of the knowledge; dividing the relationships among the sub-sets of concepts; and providing a further set comprising all the concepts along with a second type of relationship that provides an association between each concept in the further set of concepts and one or more of the sub-sets of concepts and relationships.
Owner:BRITISH TELECOMM PLC
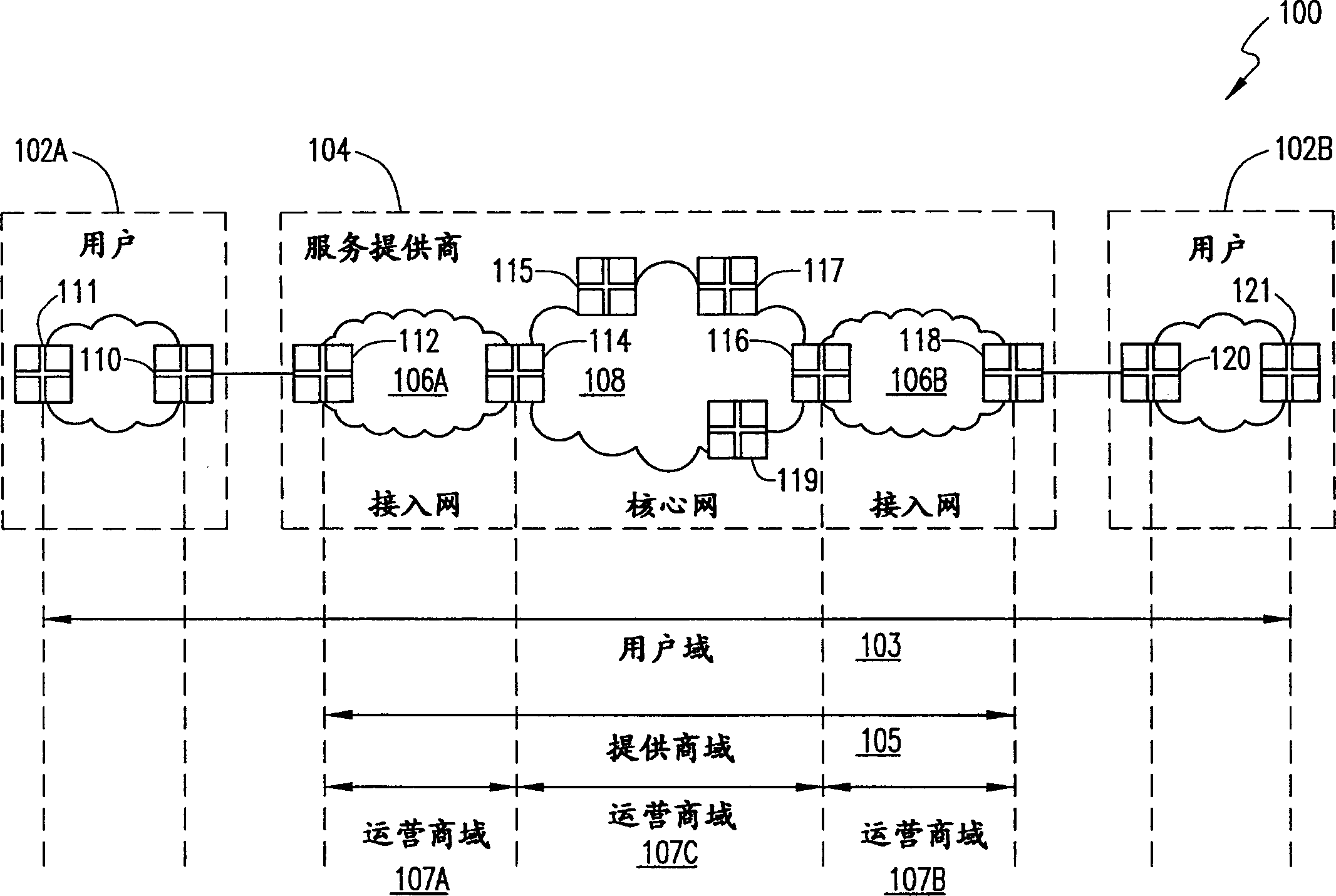
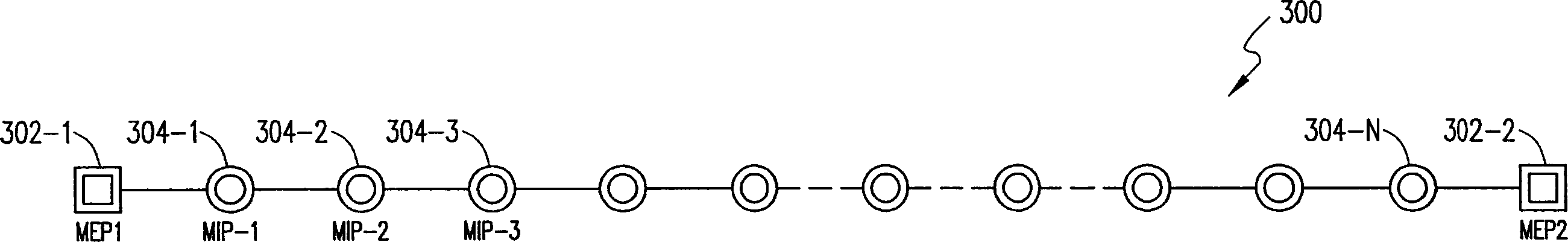
System and method for reducing OAM frame leakage in an Ethernet OAM domain
A system and method for reducing frame leakage in a VLAN defined in an Ethernet OAM network. Upon receiving a unicast OAM frame at a Maintenance Intermediate Point (MIP) entity, a first database is queried to verify it the frame's destination address (DA) is provided therein. If not, a second database is queried to verify the frame's source address (SA) is associated with a Maintenance End Point (MEP) entity provided therein. If so, OAM domain level information corresponding to the MEP entity is obtained and a multicast MAC address associated with the OAM domain level is determined. The incoming OAM frame's DA is then replaced with the multicast MAC address for forwarding the frame to a set of port addresses restricted to the OAM domain level.
Owner:ALCATEL LUCENT SAS
Method and system for managing and securing subsets of data in a large distributed data store
ActiveUS20140304243A1Digital data processing detailsSpecial data processing applicationsDomain levelDistributed data store
A system groups multiple entities in a large distributed data store (DDS), such as directories and files, into a subset called a domain. The domain is treated as a unit for defining policies to detect and treat sensitive data. Sensitive data can be defined by enterprise or industry. Treatment of sensitive data may include quarantining, masking, and encrypting, of the data or the entity containing the data. Data in a domain can be copied as a unit, with or without the same structure, and with transformations such as masking or encryption, into parts of the same DDS or to a different DDS. Domains can be the unit of access control for organizations, and assigned tags useful for identifying their purpose, ownership, location, or other characteristics. Policies and operations, assigned at the domain level, may vary from domain to domain, but within a domain are uniform, except for specific exclusions.
Owner:DATAGUISE
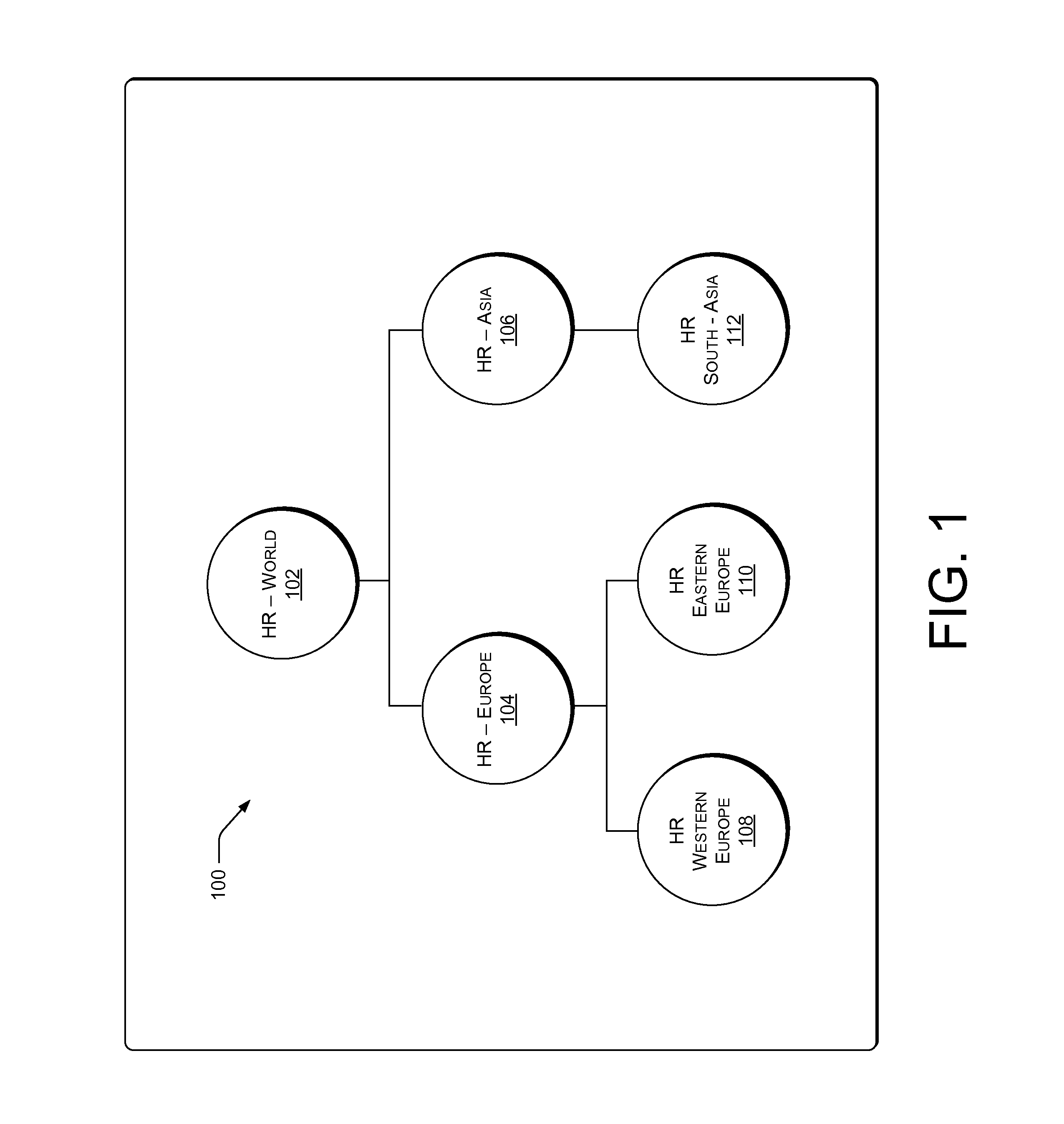
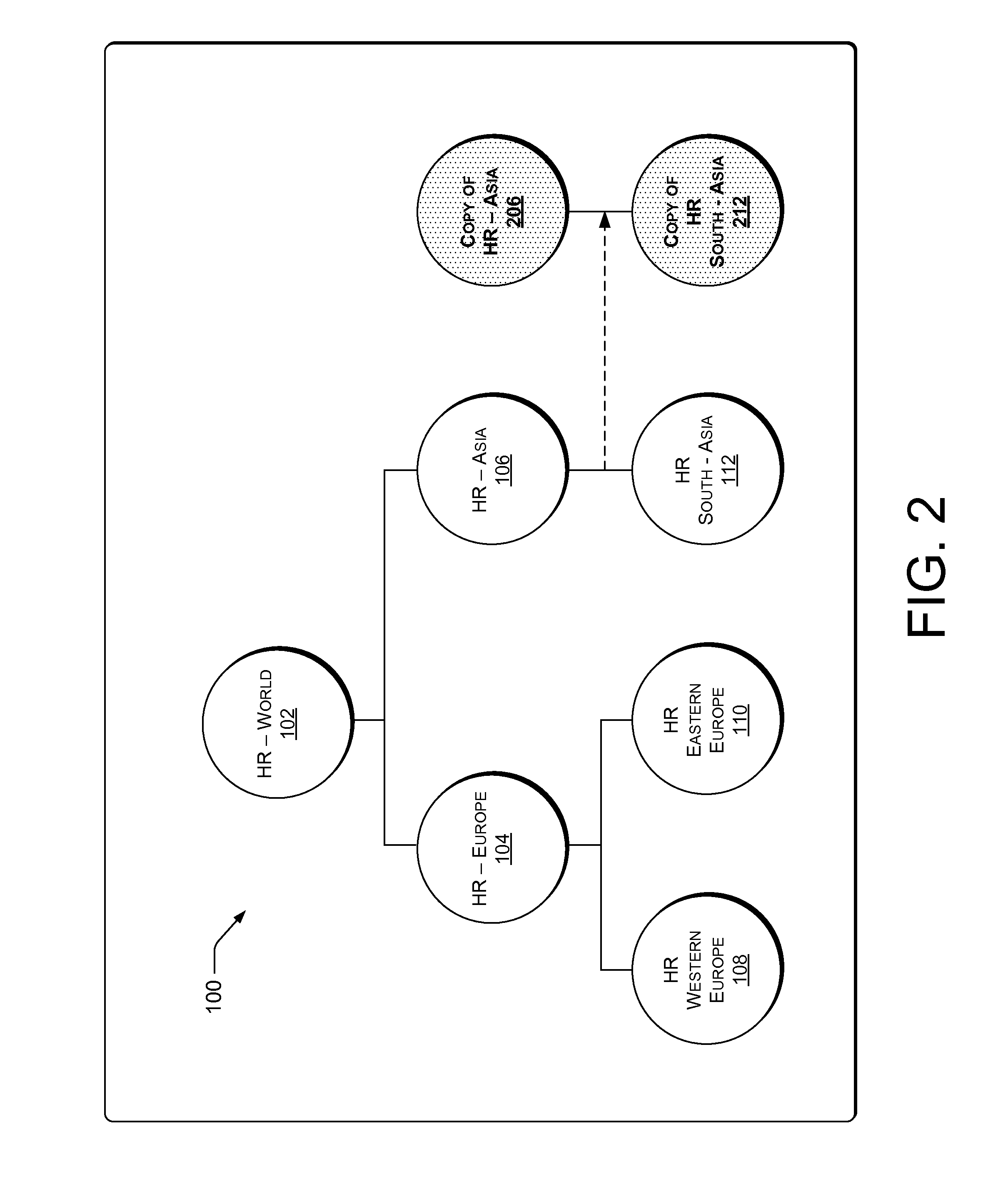
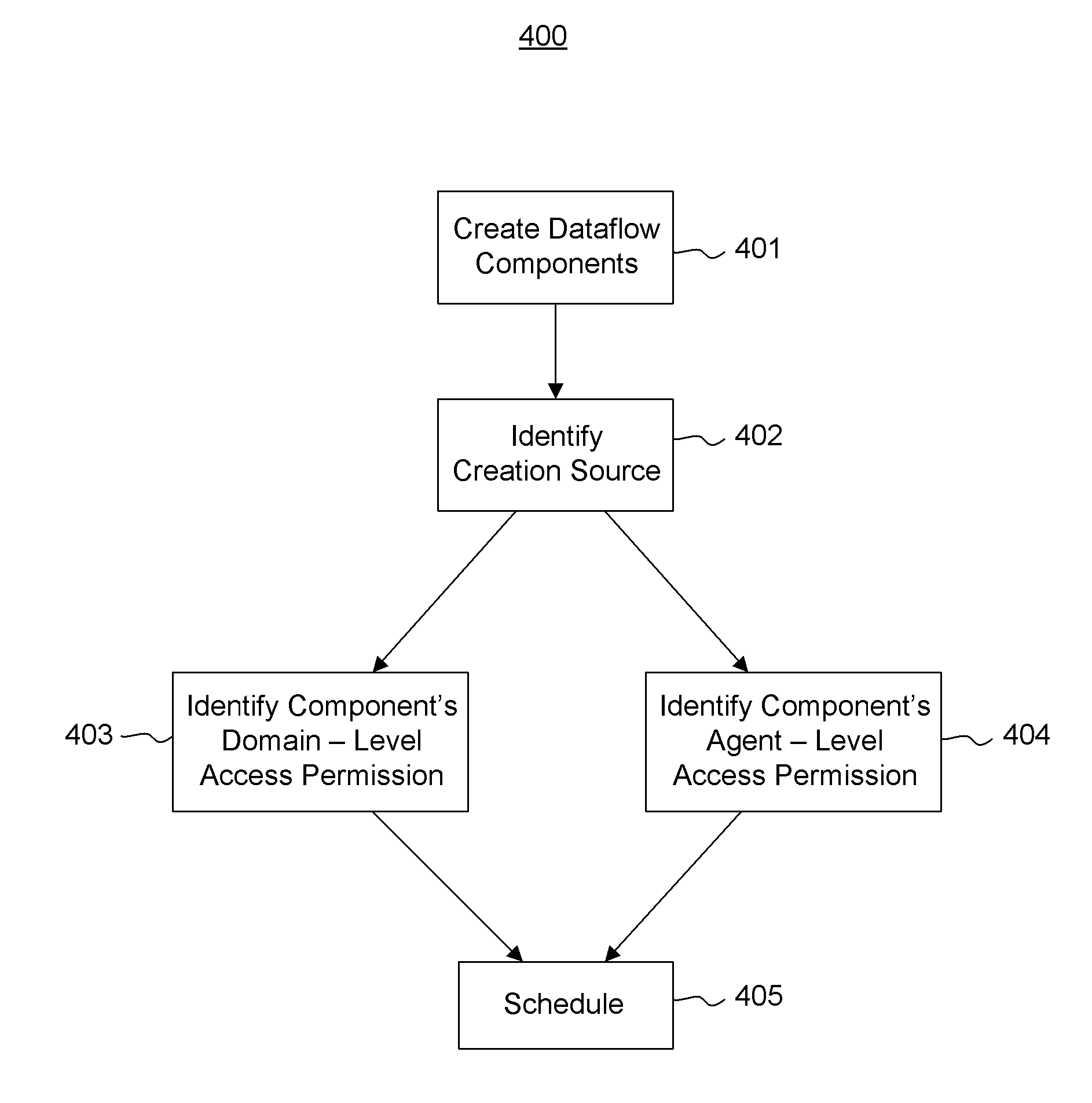
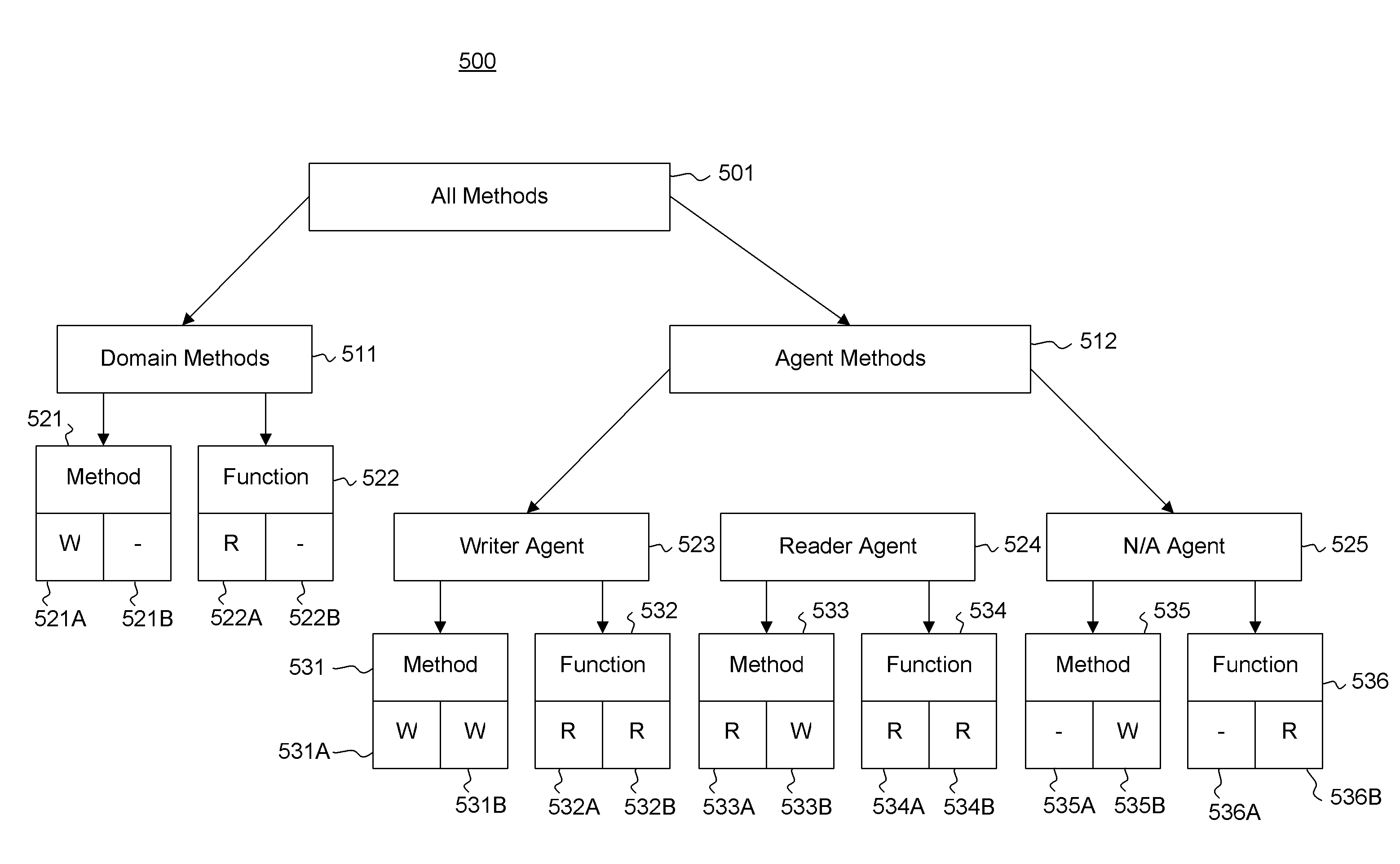
Dataflow component scheduling using reader/writer semantics
The scheduling of dataflow components in a dataflow network. A number, if not all, of the dataflow components are created using a domain / agent model. A scheduler identifies, for a number of the components, a creation source for the given component. The scheduler also identifies an appropriate domain-level access permission (and potentially also an appropriate agent-level access permission) for the given component based on the creation source of the given component. Tokens may be used at the domain or agent level to control access.
Owner:MICROSOFT TECH LICENSING LLC
Universal keyboard
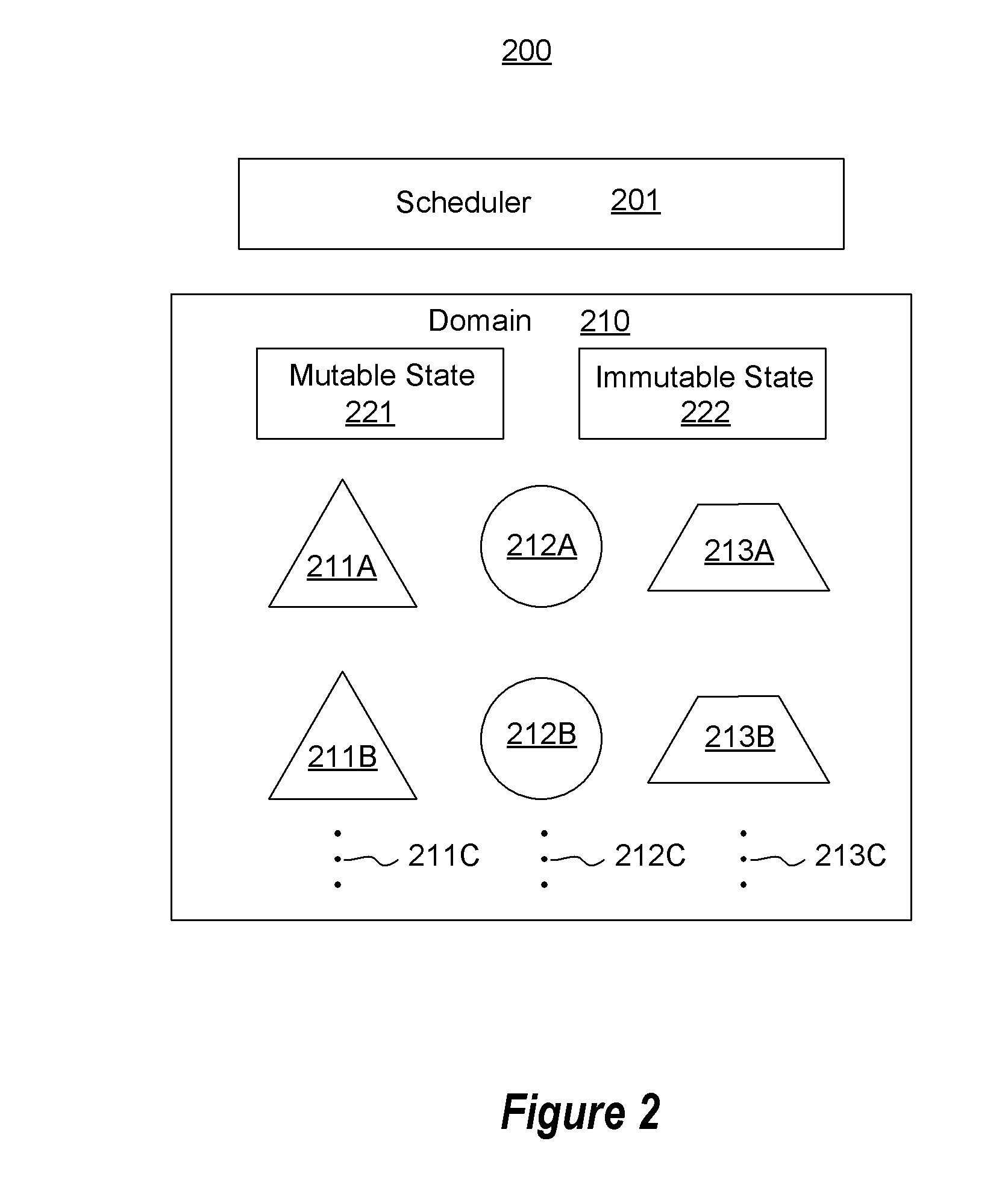
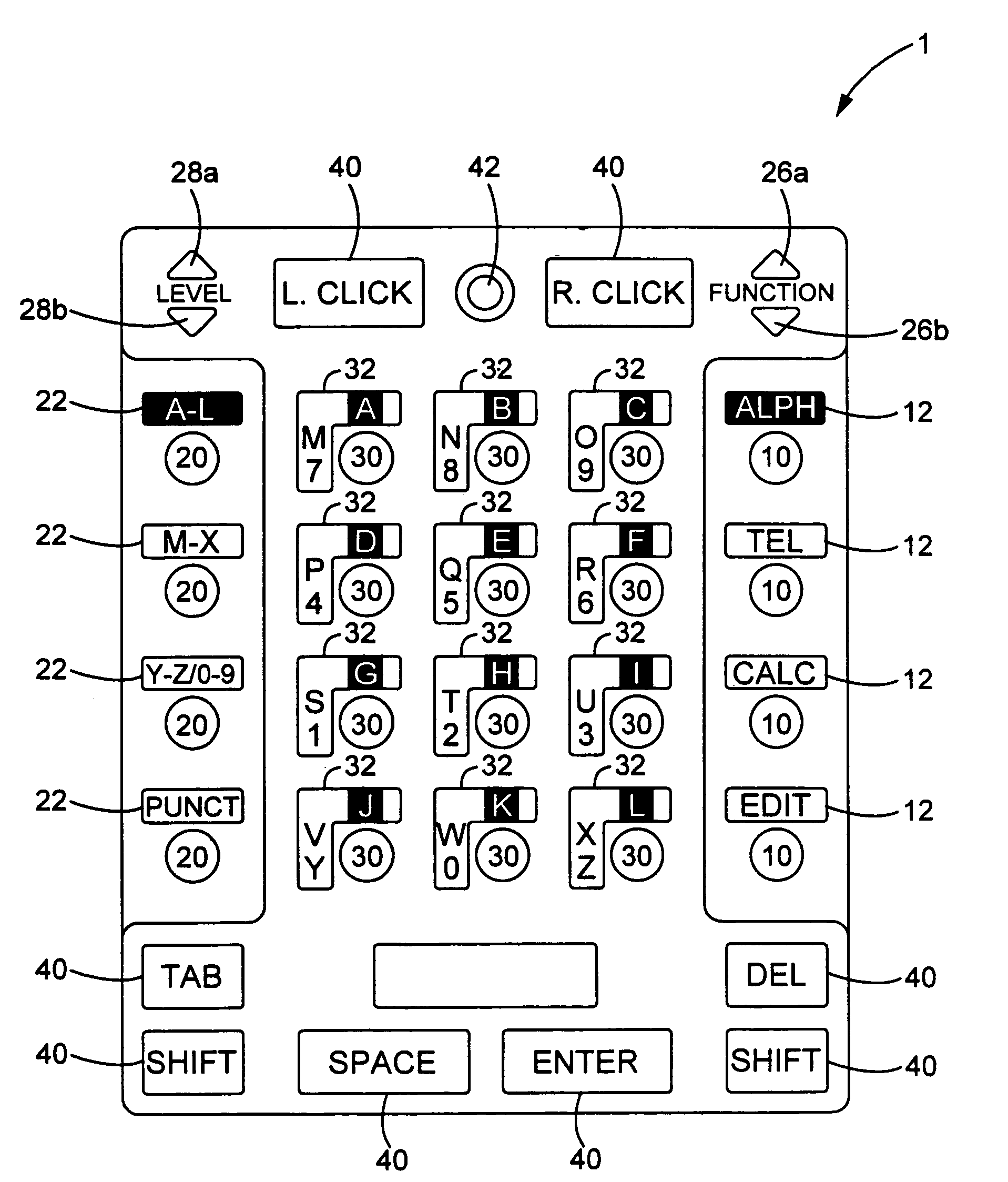
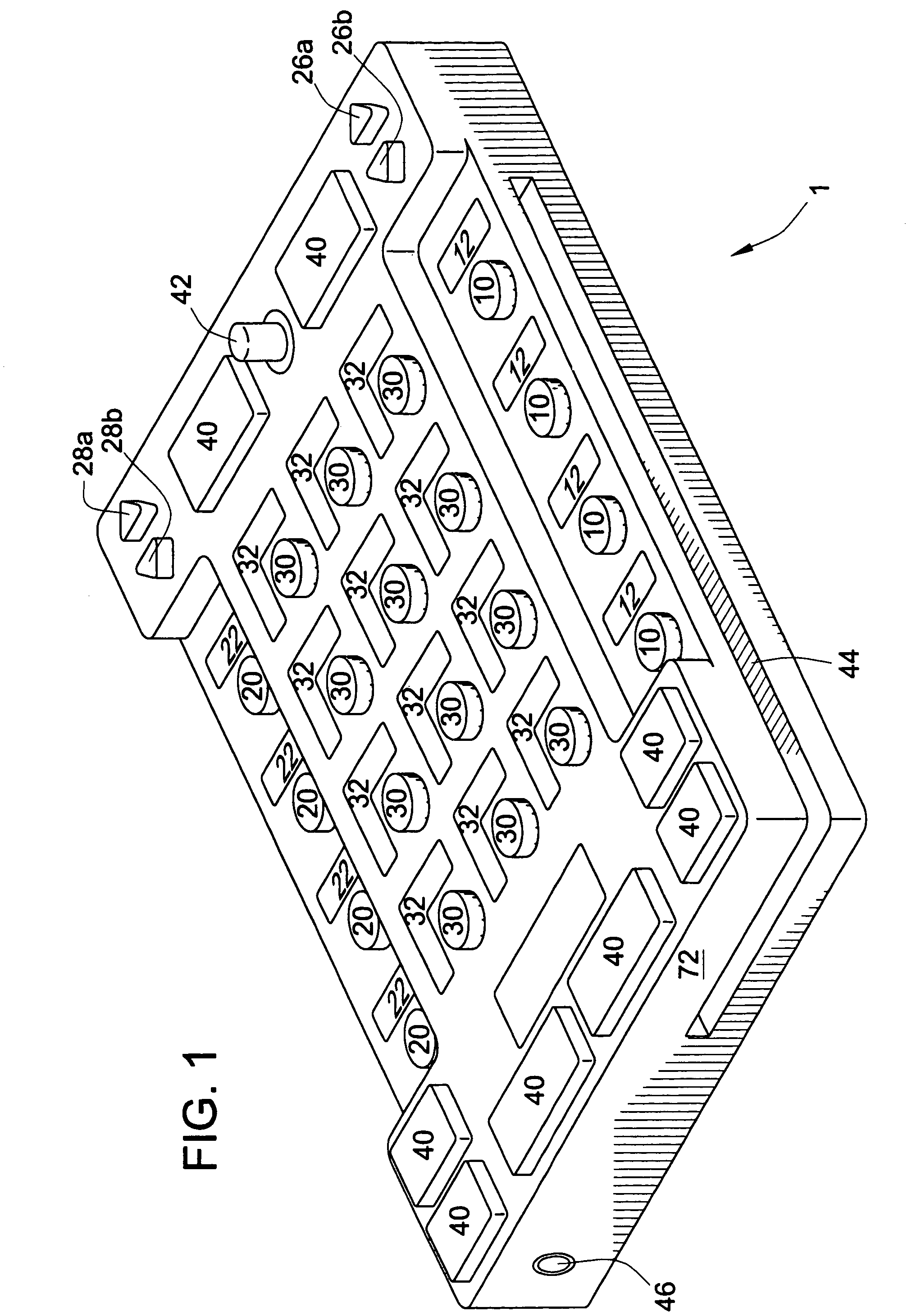
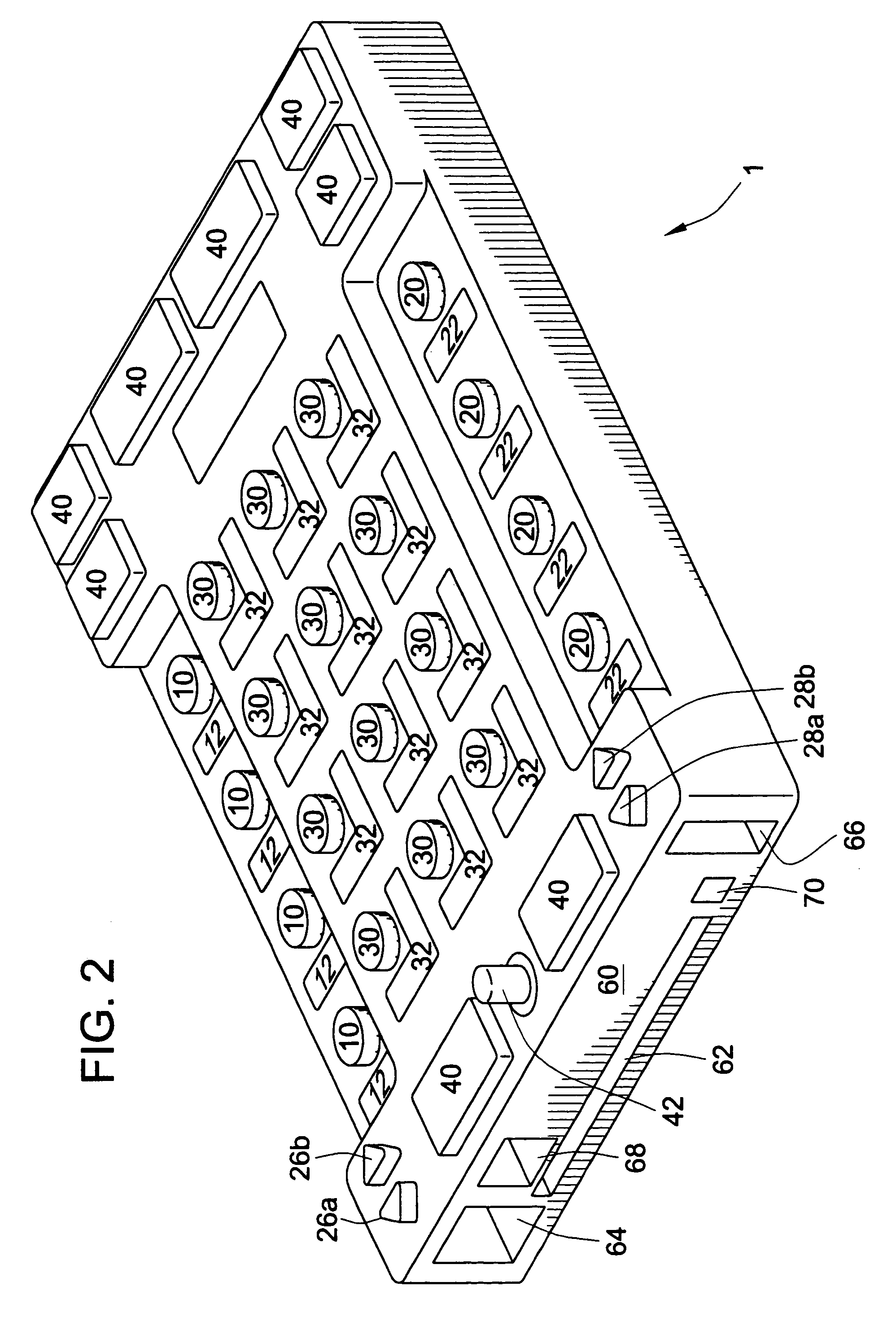
InactiveUS7250898B2Input/output for user-computer interactionElectric signal transmission systemsDomain levelDisplay device
The present invention provides a multifunctional input device. The input device includes a functional mode which defines the mode of operation of the input device. Each functional mode includes one or more domain levels with each domain level containing one or more domain-level values. Each domain level-value within each functional mode is assigned to one of a plurality of programmable input keys. The domain-level value assigned to each programmable input key controls the function of that programmable input key within a given functionality and domain level. The present invention also includes a display to indicate the domain-level value associated with each of the programmable input keys within a given functionality.
Owner:PRINCEPS INTERFACE TECH LLC
Support for domain level business object keys in EJB
InactiveUS6999964B2Enable reusable business componentsDigital data processing detailsSpecific program execution arrangementsPublic interfaceDomain level
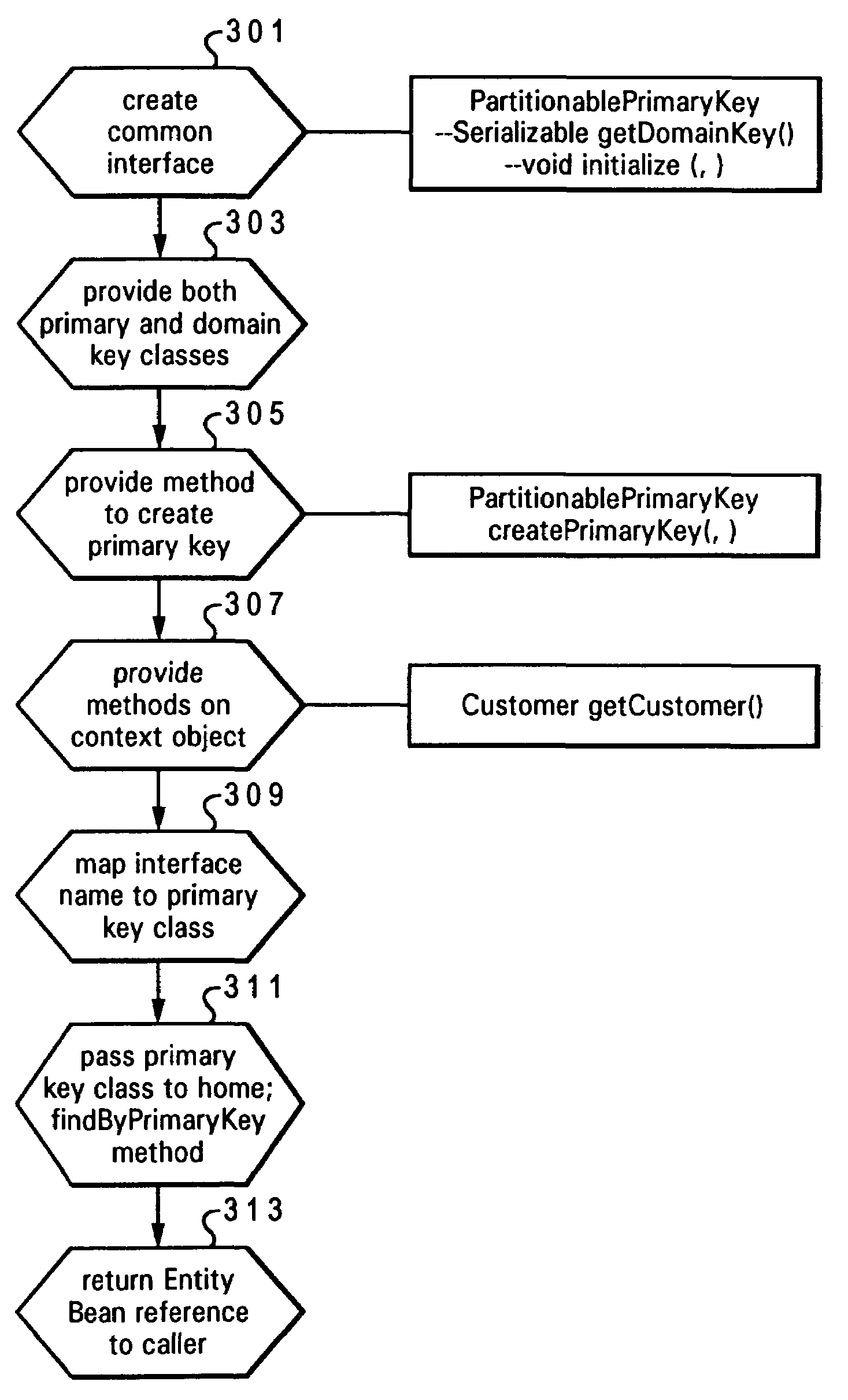
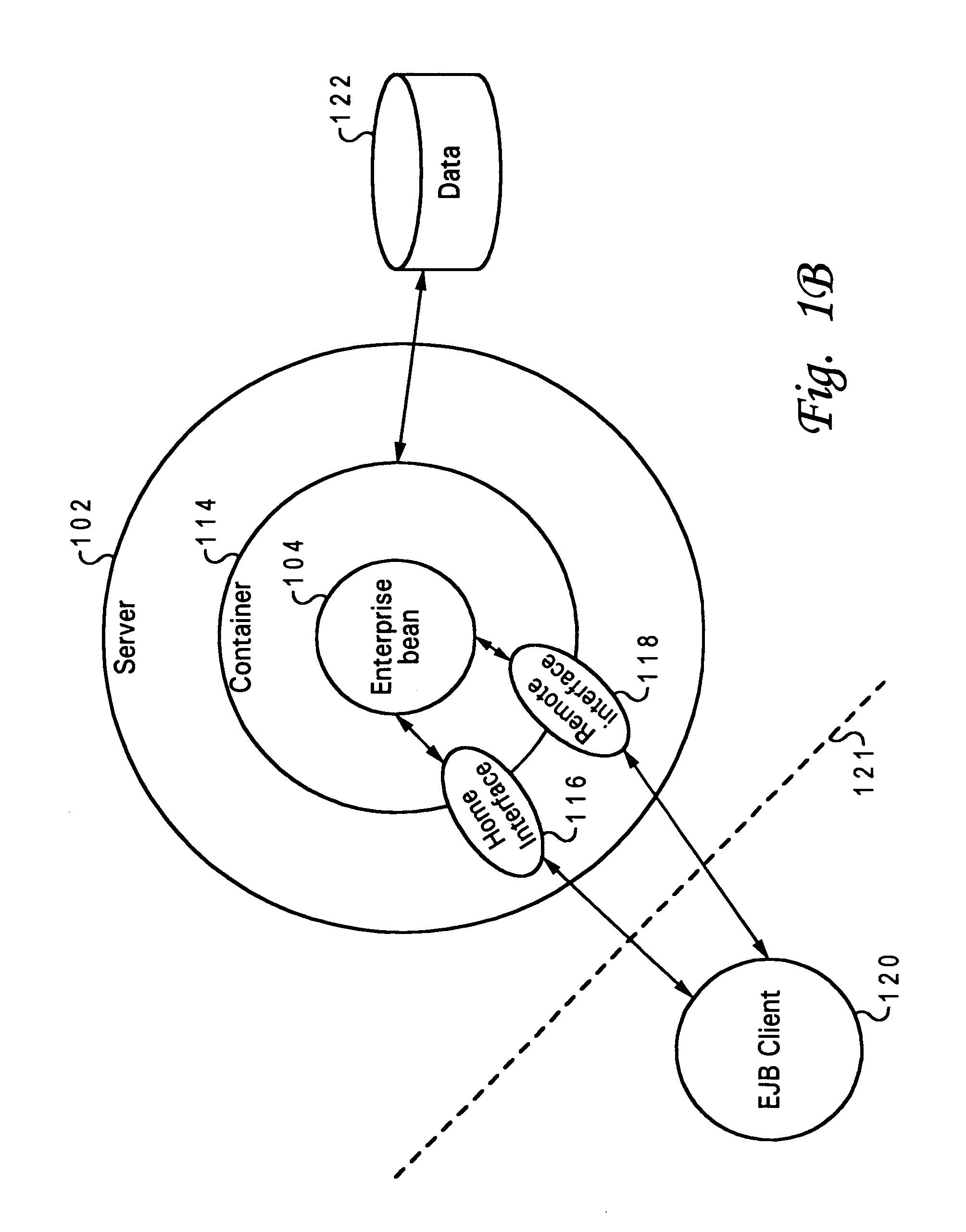
A method, system and program product for providing domain level business object keys in Enterprise JavaBeans (EJB) applications. An instance of an EntityBean object is provided with both a primary key and a domain key class. The primary key class is associated with a home selected for the EntityBean object, and the domain key class is associated with a particular business application within which the EntityBean object is being utilized. The EntityBean and associated home is utilized across different business applications, while ensuring uniqueness across the different applications. Also, a common interface for the primary key is introduced that has methods, which (1) provide an initialized instance of associated domain key classes from a concrete primary key subclass, wherein a concrete primary key subclass knows its associated domain key and is able to initialize the domain key from a subset of attributes of the primary key, and (2) creates an initialized instance of a primary key subclass from a given domain key and a context object.
Owner:INTERMATIONAL MACHINERY CORPORATIO
Production process control method for prebaked anode
InactiveCN102364404AQuality productionHomogeneous productionTotal factory controlProgramme total factory controlElectrolysisDomain level
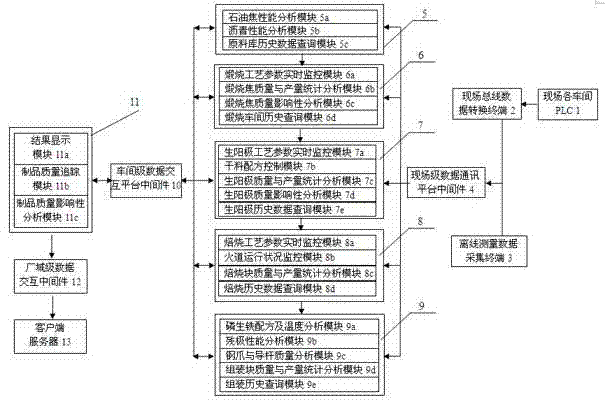
The invention relates to a production process control method for a prebaked anode used for aluminum electrolysis. The production process control method comprises the following steps of: automatically importing and storing the data in a data analysis server in a classified way by utilizing field level data communication platform middleware, wherein the data is obtained by processing prebaked anode production process field computer programmable logical controller (PLC) data by using a field bus data conversion terminal and an offline measurement data acquisition terminal; finishing the real-time monitoring and the rapid response of raw material petroleum coke, asphalt performance parameters, calcination process technical parameters, anode preparation process technical parameters, roasting process technical parameters and assembly technical parameters of the overall prebaked anode production by using the data analysis server; and transmitting data analysis server data analysis results of each workshop and quality tracking and impact analysis results of each workshop to a client server through a plant domain level data exchange middleware by using a carbon plant data analysis server. By the method, the production efficiency and the anode quality of the overall prebaked anode are improved, and production process energy consumption and operation cost are reduced.
Owner:SHENYANG ALUMINIUM MAGNESIUM INSTITUTE
A method, system, and computer program product for automatic insertion and correctness verification of level shifters in integrated circuits with multiple voltage domains
ActiveUS20060085770A1Automatic detectionCAD circuit designSoftware simulation/interpretation/emulationDomain levelLevel converter
Level shifter modules, used in integrated circuits (ICs), are automatically inserter and their correctness verified. A level shifter module for signals crossing voltage domains is generated, and instances thereof are inserted in a pre-determined voltage domain. Several checks ensure the correctness of the inserted level shifter module. The level shifter modules are instantiated based on user-defined voltage constraints.
Owner:SYNOPSYS INC
Mail transmission agent primary anti-deny method based on domain hierarchy identifying mechanism
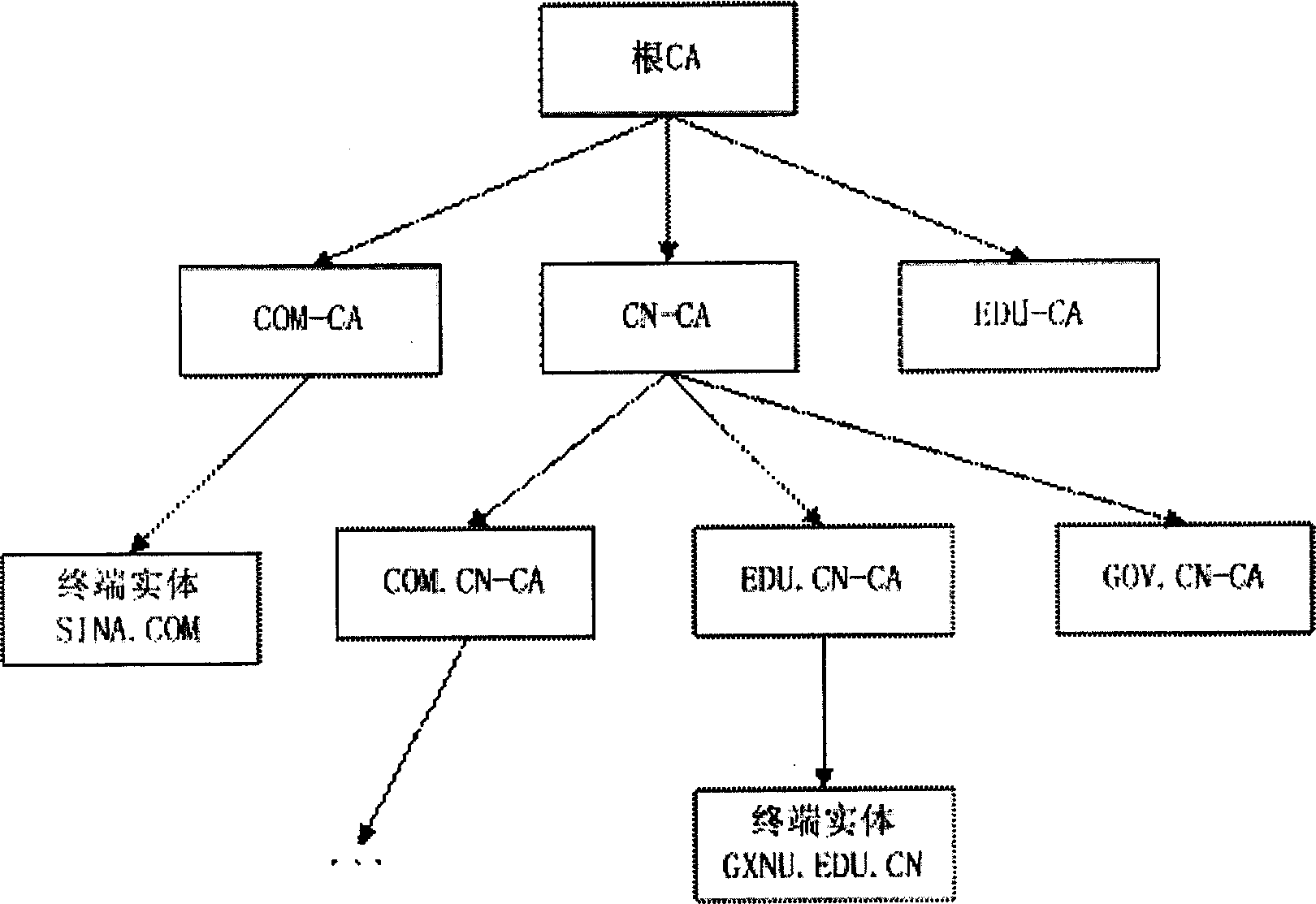
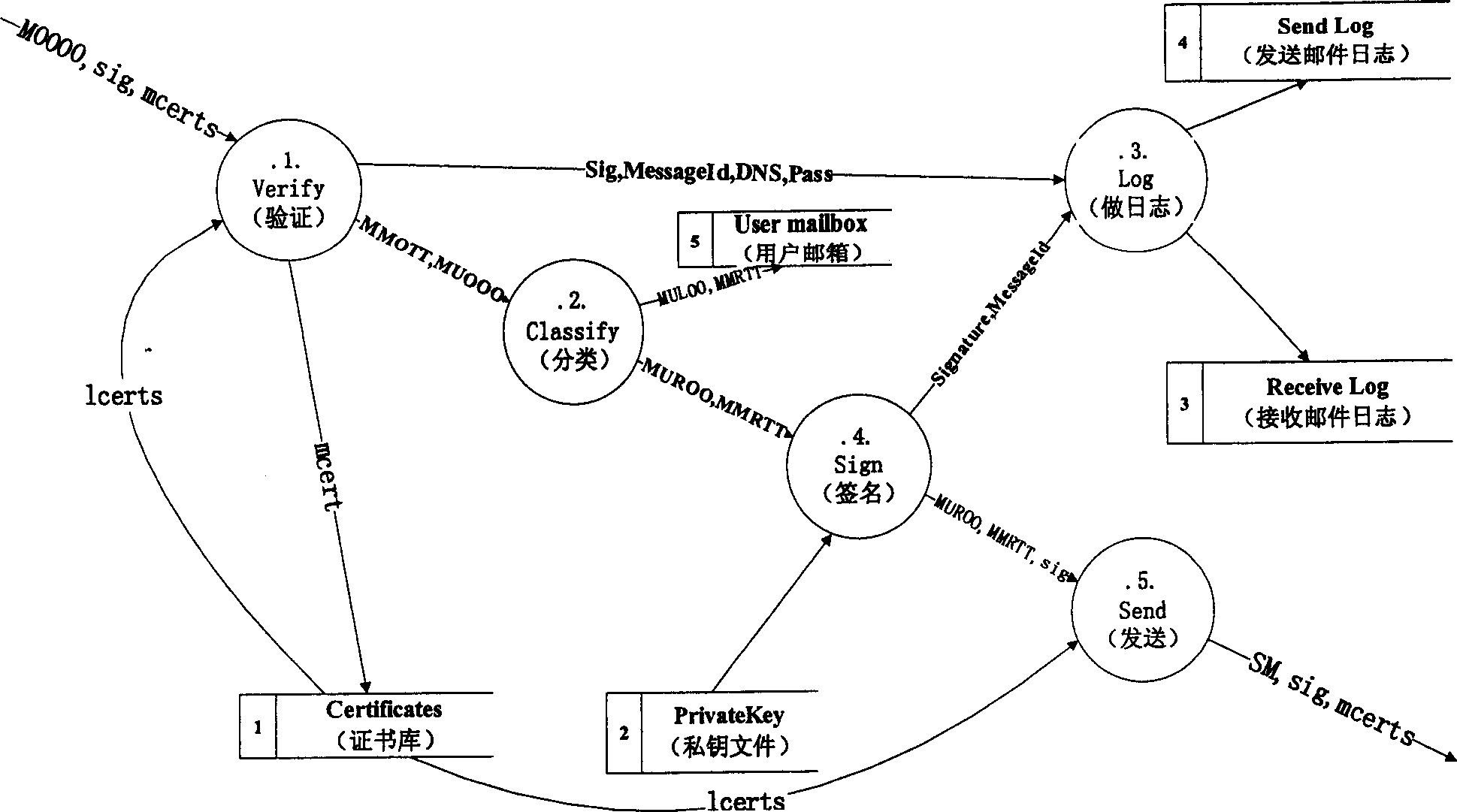
InactiveCN1783848AEnforcing non-repudiationEasy to implementPublic key for secure communicationData switching networksDomain nameLevel structure
This invention relates to non-repudiation of origin method for mail proxy based on DNS domain level certification authority. It contains 1, establishing CA, 2, establishing level structure CA corresponded with all DNS domain level structure, 3, generating and distributing MTA certificate, 4, source MTA calculating Hash value H to mail to be send, making digital signature to H by private key, said signature information is sig, 5, forming certificate chain mcerts to certificate from said field to root field, 5, sending {M, sig, mcerts} to next MTA, 7, identifying MTA certificate as being received by receiver MTA, 8, taking public key from identified source certificate, identifying the digital signature of source MTA to M by public key, 9, directly writing user mail box or sending to next MTA. Said invention realizes the forced non-repudiation of origin between MTA to MTA with convergent divergent level CA structure.
Owner:BEIHANG UNIV
Use of iterative learning for resolving scalability issues of bandwidth broker
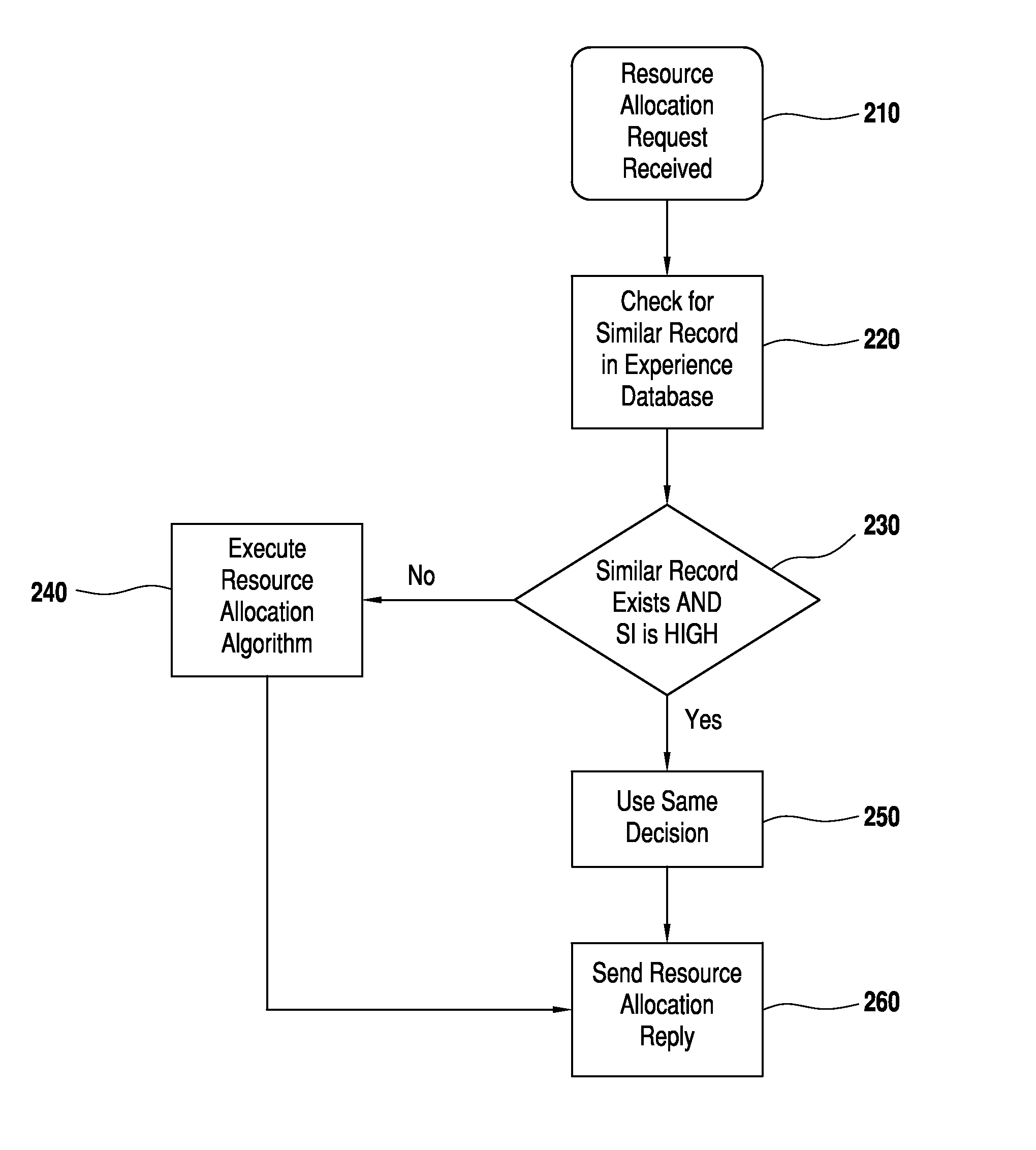
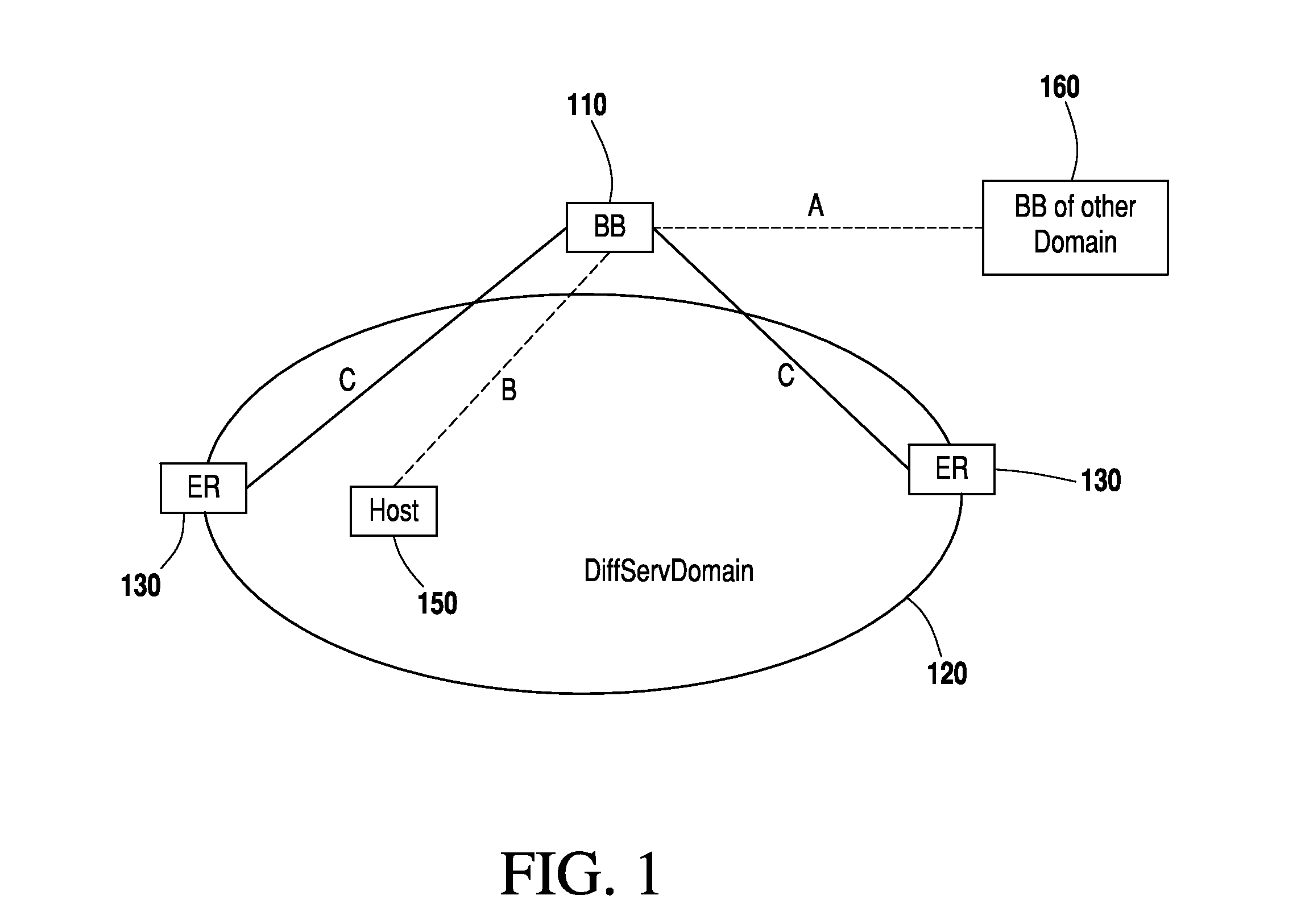
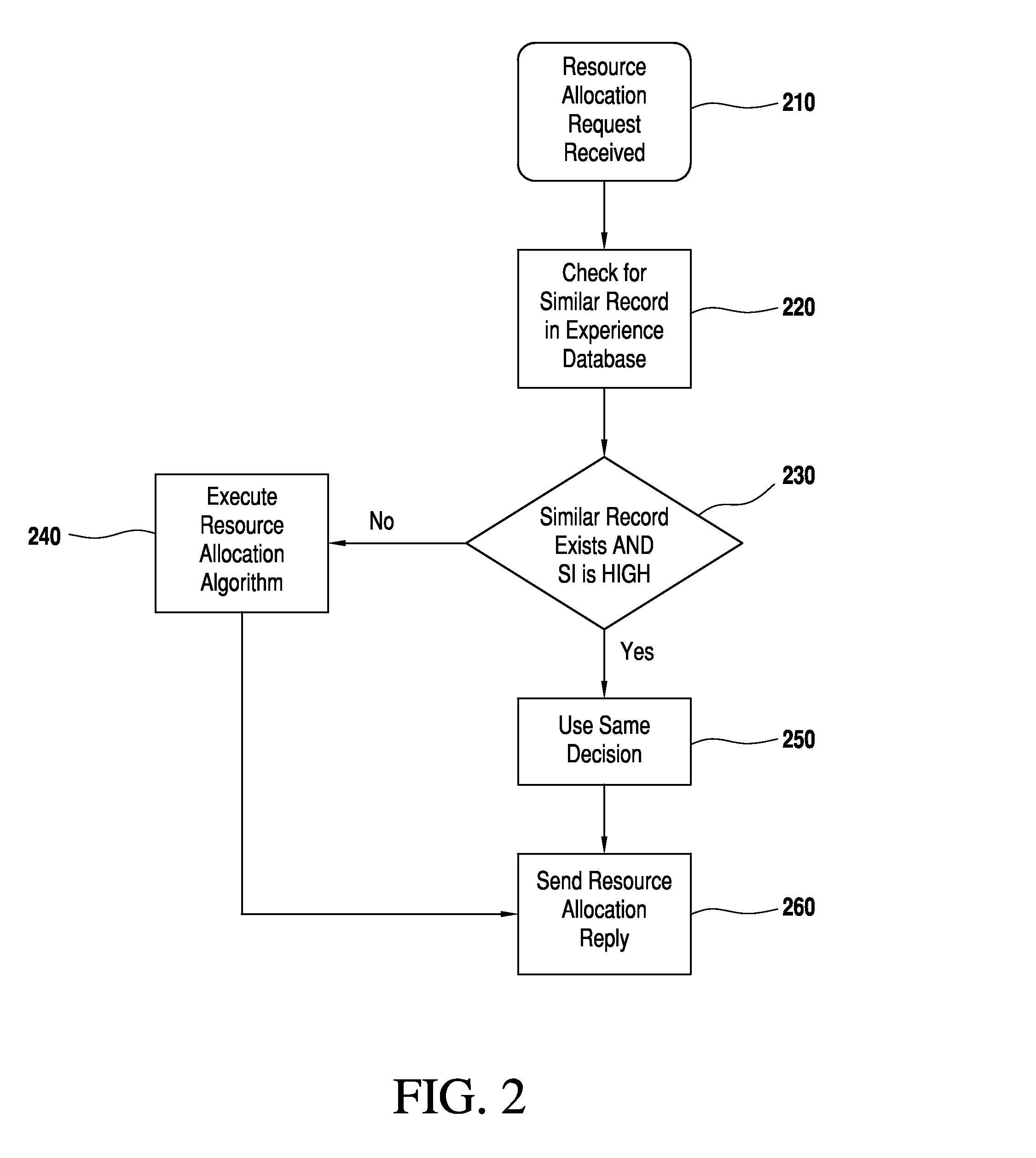
InactiveUS20150100694A1Improve optimalImprove quickDigital computer detailsData switching networksExtensibilityInternet network
A centralized bandwidth broker (a special network server) functioning as a domain manager in an internet network having differentiated services architecture is responsible for receiving and replying to a large number of requests and for performing huge numbers of resource management tasks at the inter- and intra-domain level. Consequently, it can have scalability issues. According to the invention the bandwidth broker maintains an experience database in addition to information about other aspects of the network, and uses iterative learning for solving scalability issues by using information of previous good experiences to take future resource management decisions. Based on similarity with previous network and request conditions, the new decision can be taken without executing resource intensive algorithms. The database of experience is continuously updated for optimized iterative learning. Processing overhead is reduced, enabling a single bandwidth broker to manage big networks with large numbers of users.
Owner:UMM AL QURA UNIVERISTY
Apparatus, system and method for application-specific and customizable semantic similarity measurement
Owner:INFORMATION EXTRACTION SYST
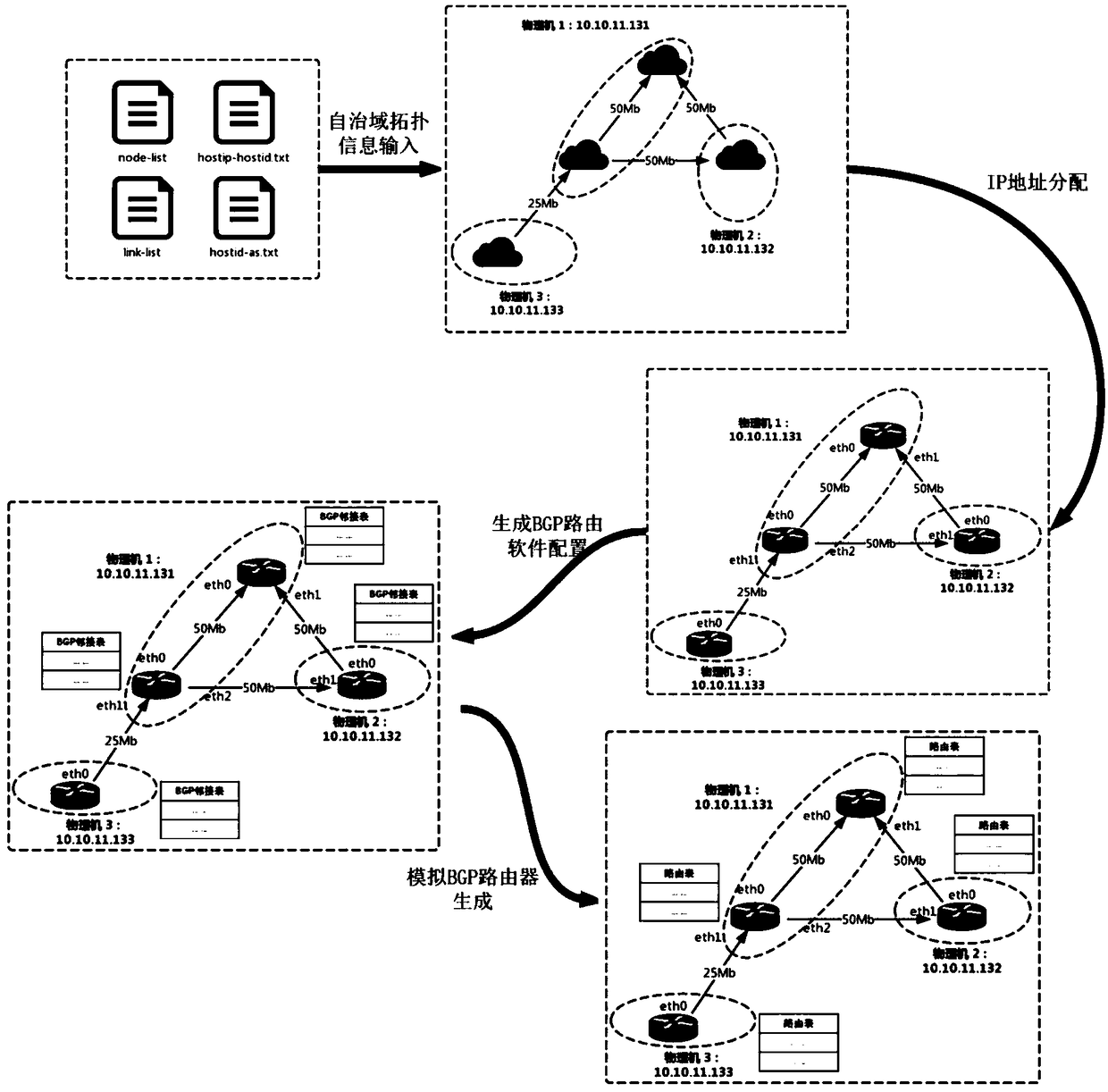
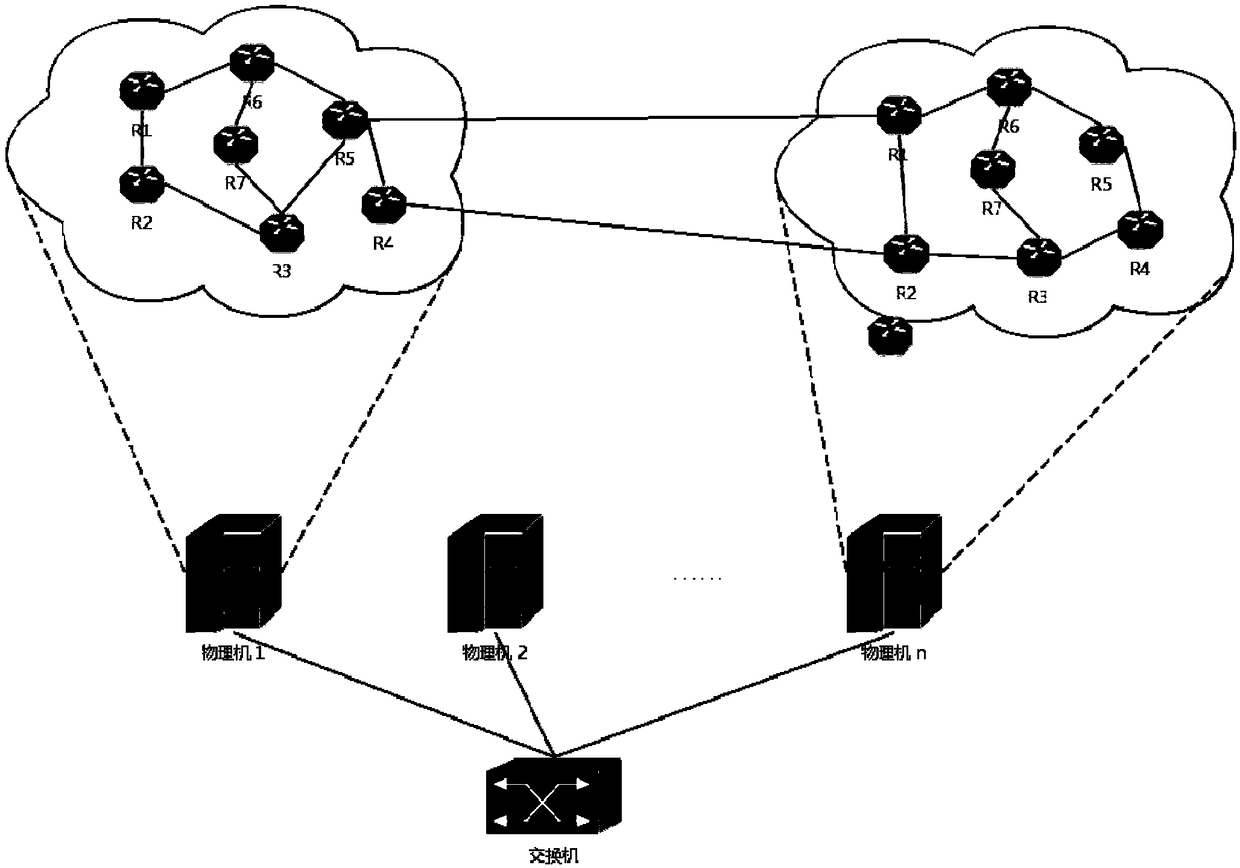
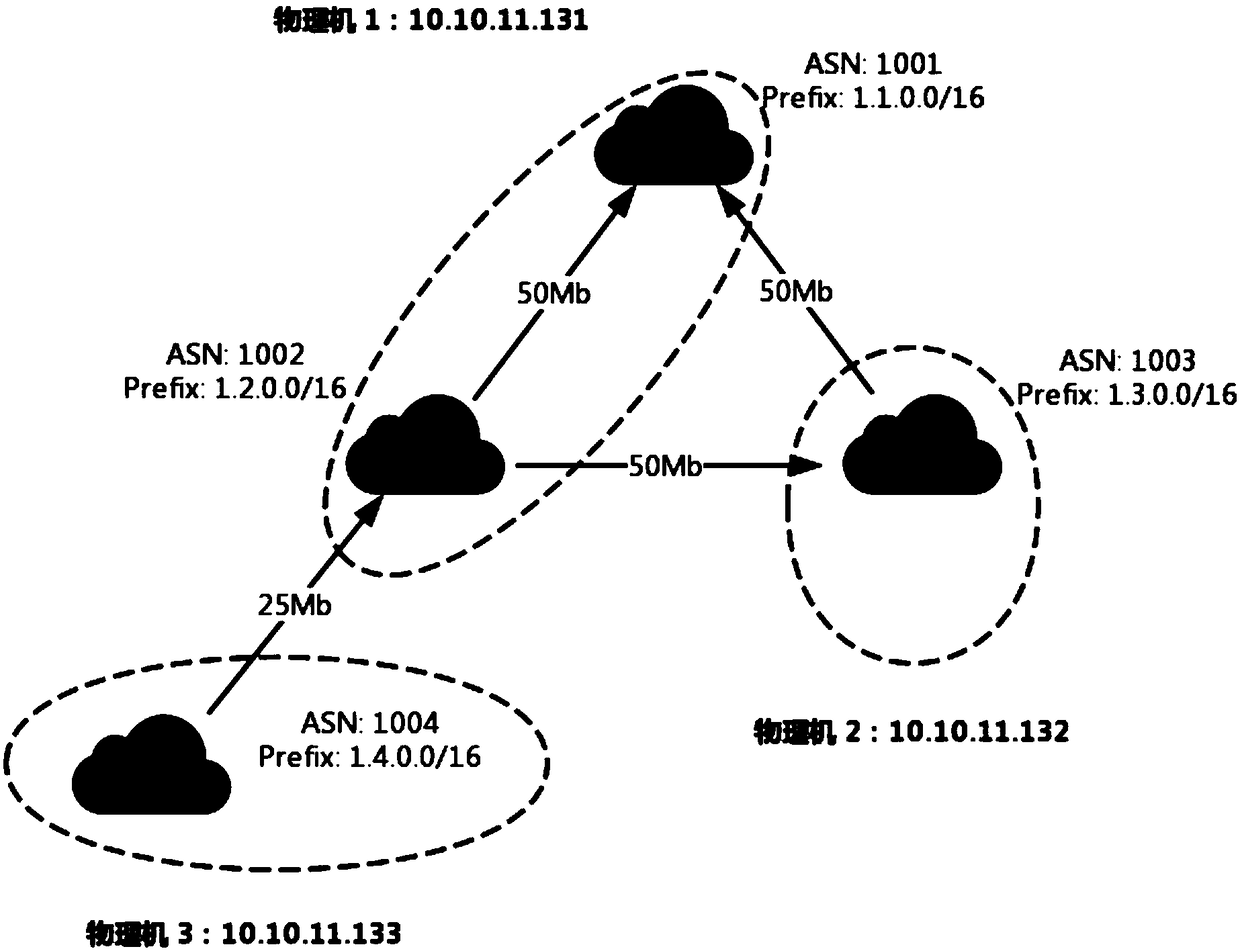
Autonomous-domain-level network simulation method based on virtualization technology
The invention discloses an autonomous-domain-level network simulation method based on a virtualization technology, and relates to the field of network simulation and algorithm design. The method aimsat achieving the purpose that by utilizing a server cluster and the virtualization technology, a host in a network is created and simulated to construct autonomous-domain-level network routing topology. According to the method, one BGP router is simulated for each autonomous domain on one or more physical machines by adopting a virtualization means, BGP sessions among the BGP routers are created,and the simulated network topology is formed. According to collected autonomous domain numbers, prefixes declared by the autonomous domains, adjacency relationships of the autonomous domains and business relationships of the autonomous domains, the autonomous-domain-level network routing topology formed by the BGP routers on a certain scale is simulated on a limited number of physical machines. The simulated BGP router topology can truly reflect the collected adjacency relationships of the autonomous domains and attributes of links among the autonomous domains; each simulated BGP router conducts routing selecting according to BGP routing protocols, and the routing behaviors of the simulated BGP routers are identical to the behaviors of real BGP routers.
Owner:HARBIN INST OF TECH
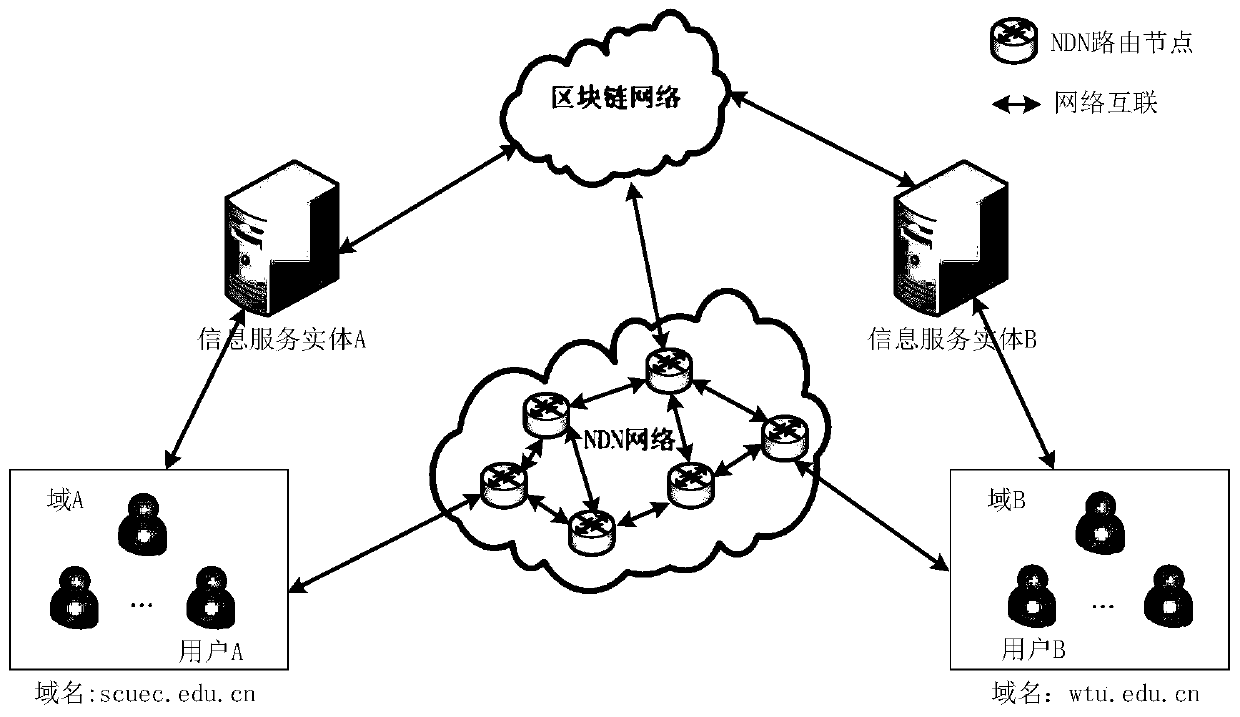
Name-based trust method in named data network
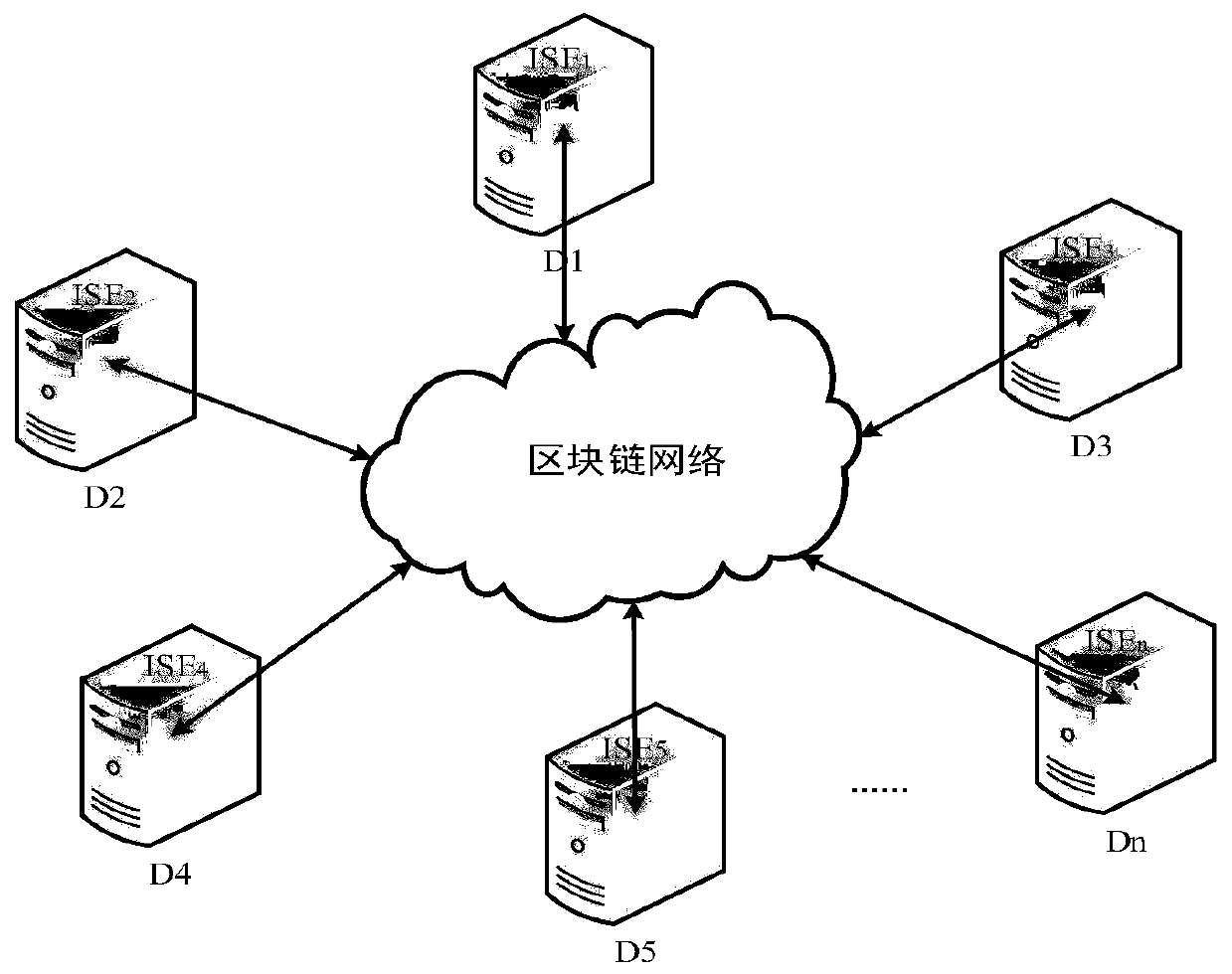
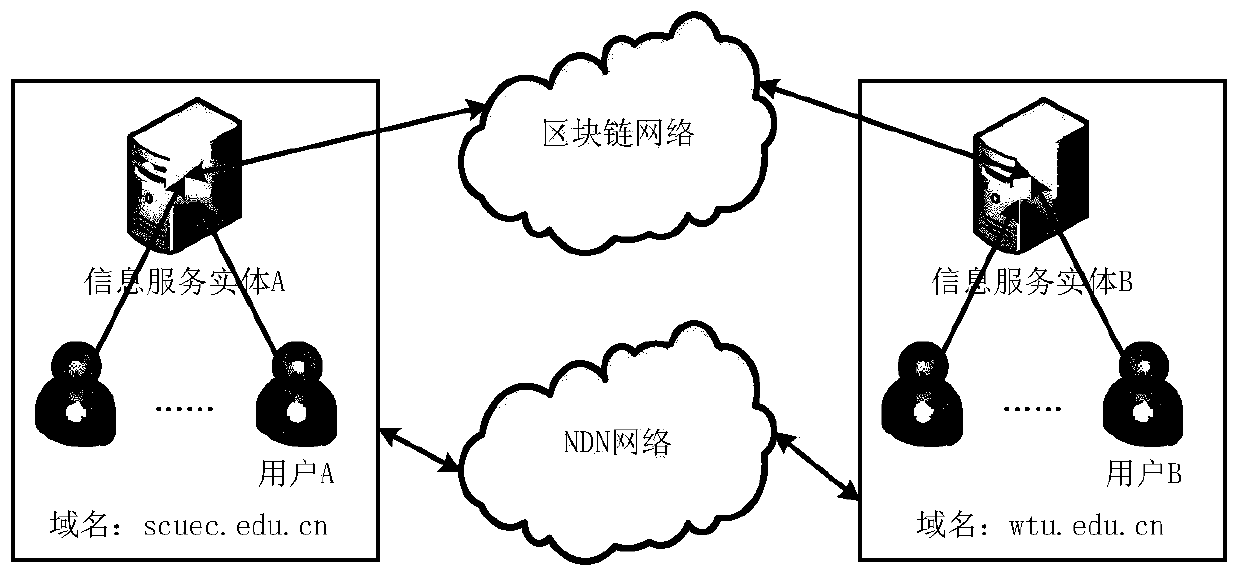
ActiveCN110401637AAuthentication is efficient and accurateUser identity/authority verificationDomain nameDomain level
The invention discloses a name-based trust method in a named data network. The method comprises the following steps: identity authentication based on a block chain technology: a domain-level information service entity applying for registration to a block chain and creates a block, and the block comprising a domain name, a public key of the domain and public parameter information of the domain; after receiving the data packet, the user verifying the identity of the domain where the producer of the data packet is located by adopting a domain-level identity authentication method, the data packetbeing credible if the verification succeeds, and otherwise, discarding the data packet; judging data credibility: signing each data packet, and a receiver judging the integrity of the data packet by verifying the data signature; according to the domain-level identity authentication method, determining the identity of a producer, and if the data packet has integrity and is generated by the producerwith legal identity, a receiver trusting the data packet. The domain-level identity is authenticated by adopting the block chain technology, the authentication efficiency is high and accurate, and the credibility of the data packet is judged by utilizing the identity authentication scheme.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
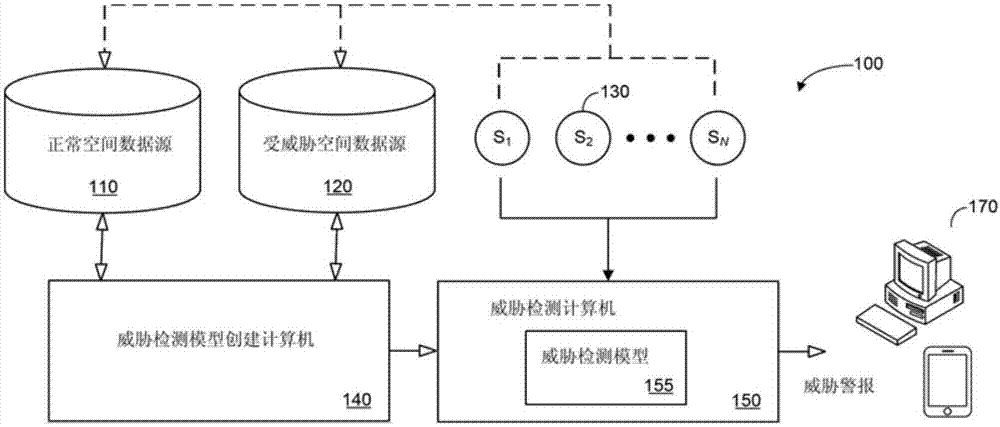
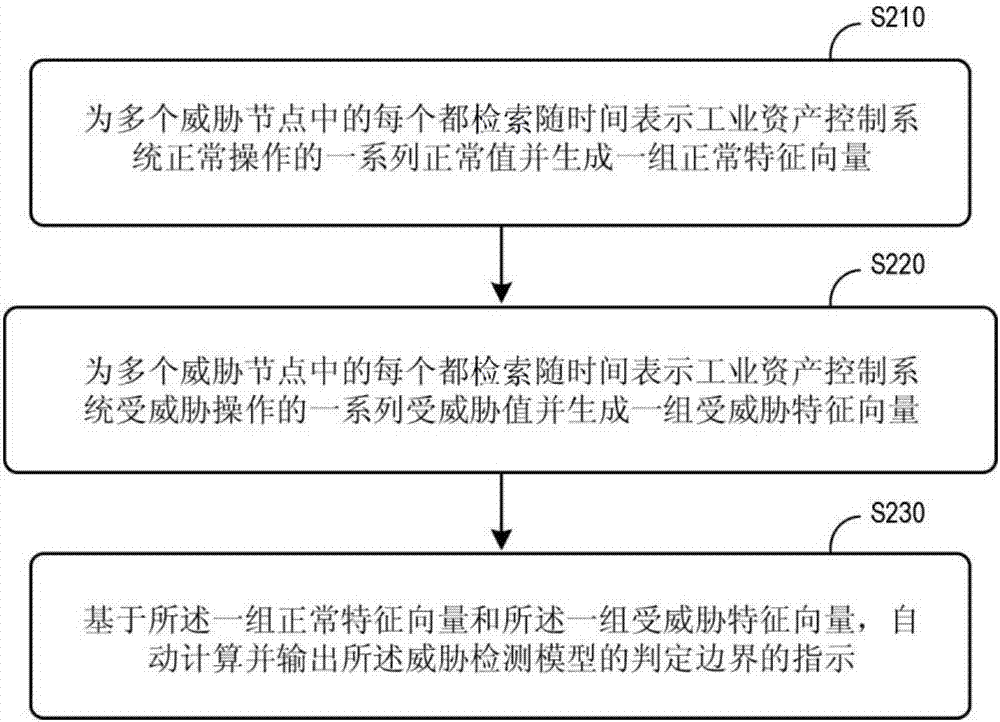
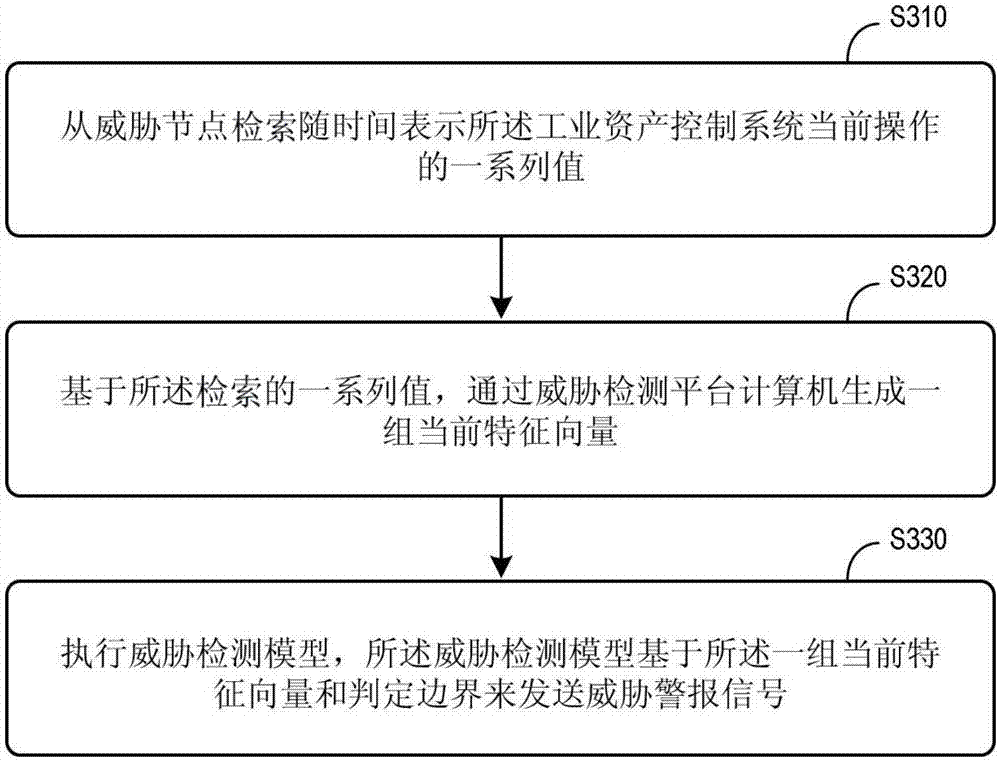
Domain level threat detection for industrial asset control system
ActiveCN107390567AProtection from cyber threatsProgramme controlComputer controlFeature vectorDecision boundary
A normal space data source 110 stores, for each of a plurality of threat nodes 130, a series of normal values that represent normal operation of an industrial asset control system, and a threatened space data source 120 stores a series of threatened values. A model creation computer 140 may generate sets of normal and threatened feature vectors. The computer 140 may also calculate and output at least one decision boundary for a threat detection model 155 based on the normal and threatened feature vectors. The plurality of threat nodes 130 may then generate a series of current values from threat nodes that represent a current operation of the asset control system. A threat detection computer 150 may receive the series of current values from threat nodes 130, generate a set of current feature vectors, execute the threat detection model 155, and transmit a threat alert signal based on the current feature vectors and at the least one decision boundary.
Owner:GENERAL ELECTRIC CO
Remote sensing image sequence moving target detection method based on improved ViBe background model
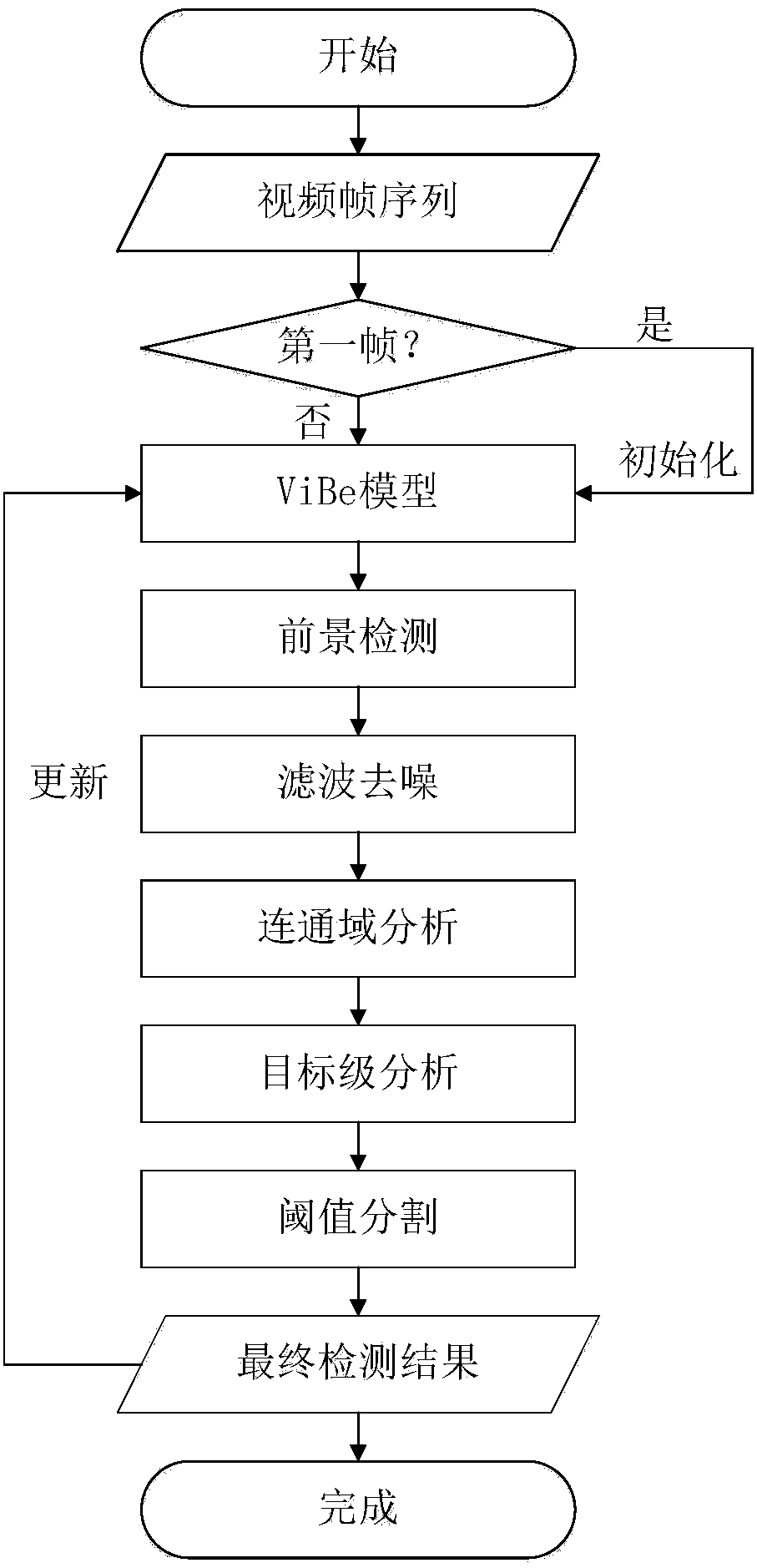
InactiveCN107767404AEasy to detectGuaranteed integrityImage enhancementImage analysisPattern recognitionDomain level
The invention provides a remote sensing image sequence moving target detection method based on an improved ViBe background model. The method comprises the following steps: adding random noise in a setrange to a first frame image in a remote sensing image sequence to construct and initialize a ViBe background model; starting from a second frame image, carrying out moving target detection: based oncurrent frame and the background model difference, obtaining an initial foreground detection result; carrying out median filtering and Gaussian filtering on the initial foreground detection result toremove noise jamming; carrying out connected domain analysis on the filtering results, that is, converting pixel level processing into connected domain level processing, and carrying out preliminaryscreening on the detection result based on connected domain attributes; carrying out target level analysis: serving each connected domain in the result obtained after preliminary screening as a target, and carrying out further optimization on the detection result through ghost judgment and saliency detection; and carrying out threshold segmentation based on an Otsu method to obtain a final movingtarget detection result. The method takes detection result accuracy and calculating efficiency into both considerations, and can meet real-time processing requirements.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
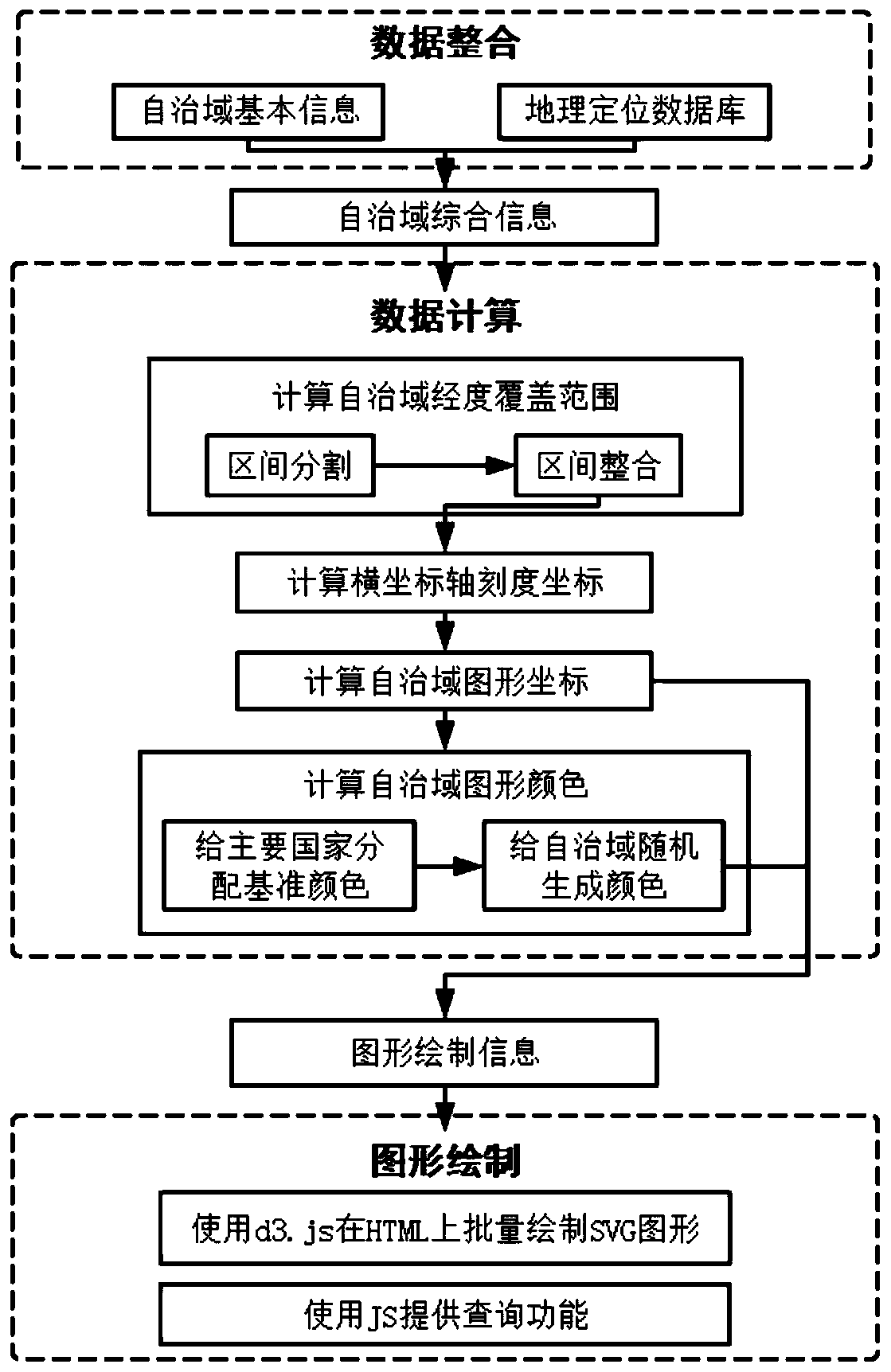
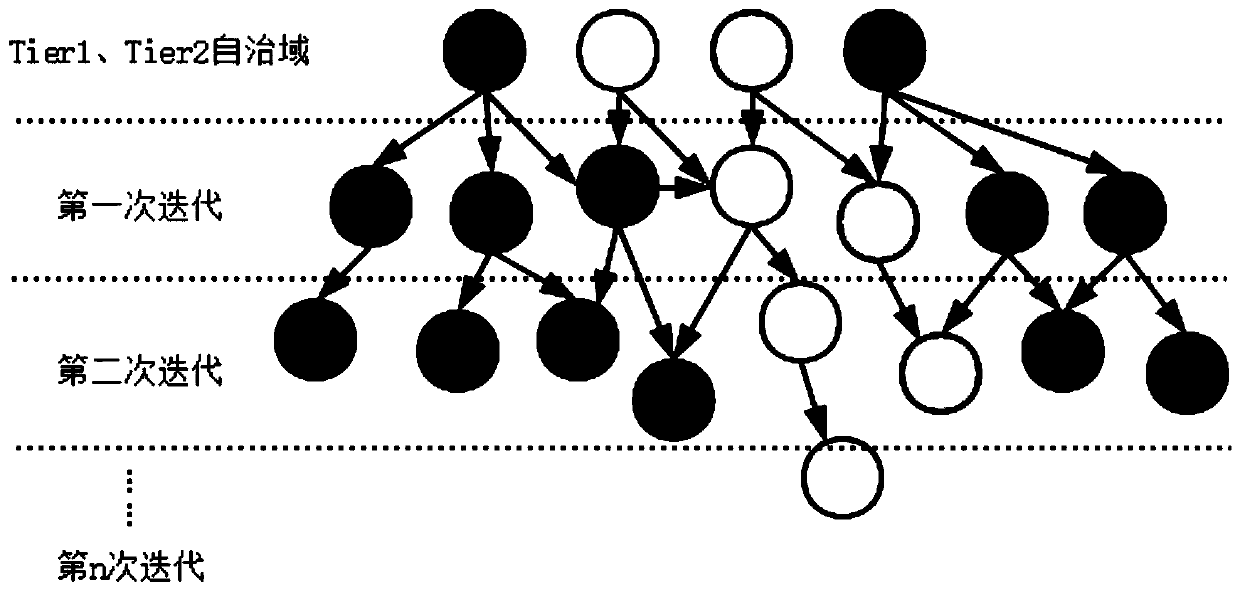
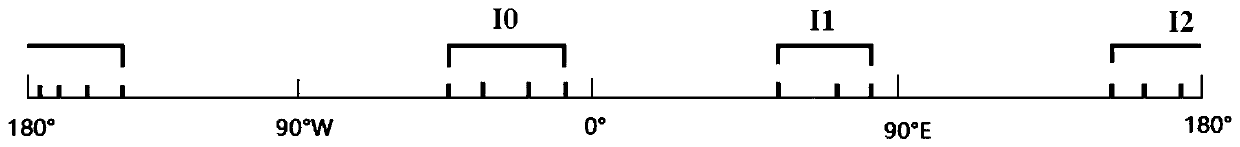
Autonomous domain level internet topology visualization method
InactiveCN109889396AEasy to observeGuaranteed stabilityData switching networksTwo-dimensional graphGraphics
The invention discloses an autonomous domain level internet topology visualization method, and relates to the technical field of network topology visualization. The objective of the invention is to solve the problem that an existing internet topology visualization method cannot reflect the characteristics of an autonomous domain-level topology. The method comprises: dividing the autonomous domaininto a Tier1 domain, a Tier2 domain and other autonomous domains according to the hierarchical information; wherein all the autonomous domains in the Tier1 are expressed by one graphic symbol respectively, all the autonomous domains in the Tier2 are expressed by the same or different graphic symbols as the Tier1 respectively, and the rest autonomous domains are expressed by the graphic symbols different from the Tier1 and the Tier2 respectively; carrying out statistics on the longitude in the geographic information to obtain a longitude coverage range of the autonomous domain, and taking the longitude coverage range of the autonomous domain as abscissa data of the autonomous domain-level internet topological graph; and generating a two-dimensional graph by using a graph drawing tool, the longitude of which is taken as an abscissa and the topology level of which is taken as an ordinate, and reflecting the basic information and the adjacent information of the autonomous domain in the two-dimensional graph, thereby finishing the visualization of the autonomous domain-level internet topology.
Owner:HARBIN INST OF TECH
Dataflow component scheduling using reader/writer semantics
The scheduling of dataflow components in a dataflow network. A number, if not all, of the dataflow components are created using a domain / agent model. A scheduler identifies, for a number of the components, a creation source for the given component. The scheduler also identifies an appropriate domain-level access permission (and potentially also an appropriate agent-level access permission) for the given component based on the creation source of the given component. Tokens may be used at the domain or agent level to control access.
Owner:MICROSOFT TECH LICENSING LLC
Unsupervised cross-domain action recognition method based on channel fusion and classifier confrontation
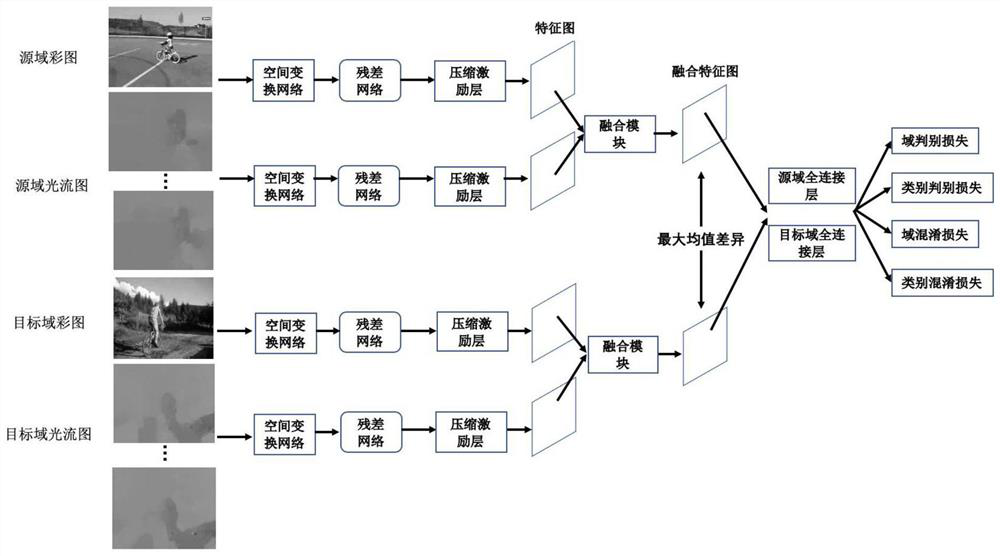
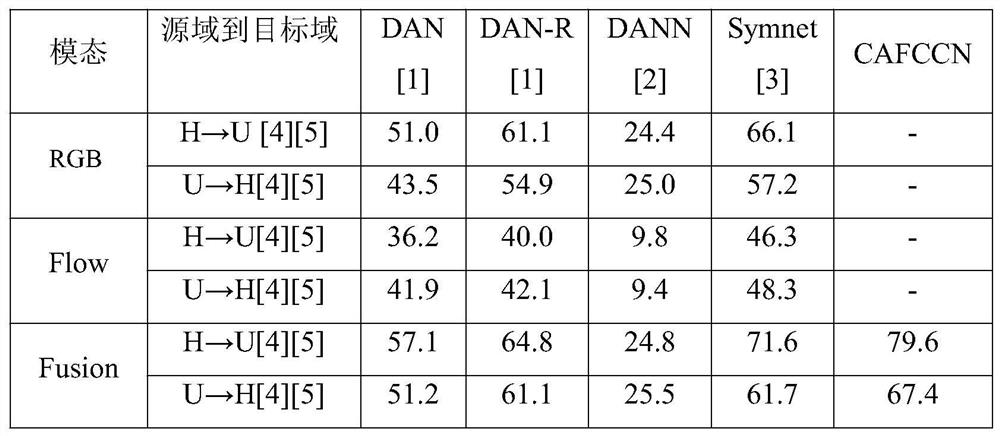
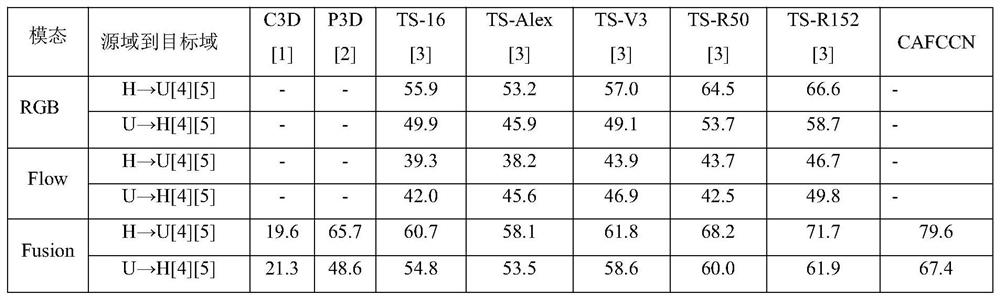
PendingCN111797814ASpace invariantFast convergenceCharacter and pattern recognitionNeural architecturesData setDomain testing
The invention discloses an unsupervised cross-domain action recognition method (CAFCCN) based on channel fusion and classifier confrontation. Efficient action recognition of a target domain test set based on a source domain labeled data set and a target domain unlabeled training set is achieved. The method comprises the following specific steps of: (1) selecting an action recognition model; (2) optimizing a double-flow deep network structure; (3) constructing an objective function based on the double-flow network; (4) building an unsupervised cross-domain action recognition model based on thedouble-flow network; and (5) constructing a data set. The method has the advantages that unlabeled data sets of other training sets can be subjected to efficient action recognition on the basis of theknown data set, and the problem of unlabeled data of the training set of the target data set can be effectively solved. By applying the confrontation method, confusion of categories and domains can be achieved at the same time, domain-level and class-level invariant features are obtained, the convergence speed of the method is high, and efficient recognition of actions can be achieved.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Crush creation method and system for deploying Ceph based on Rook
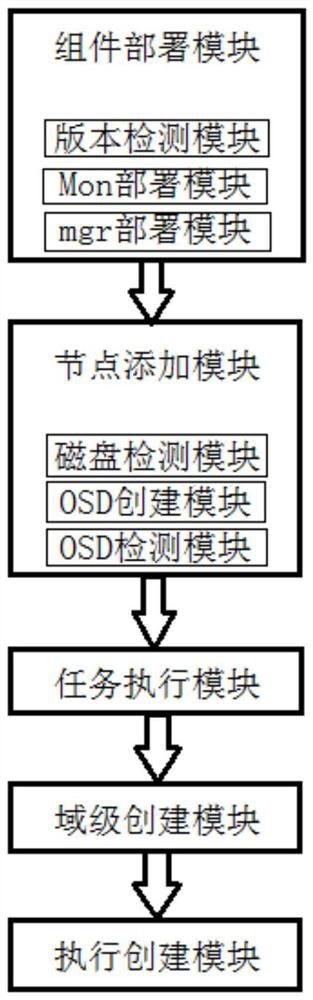
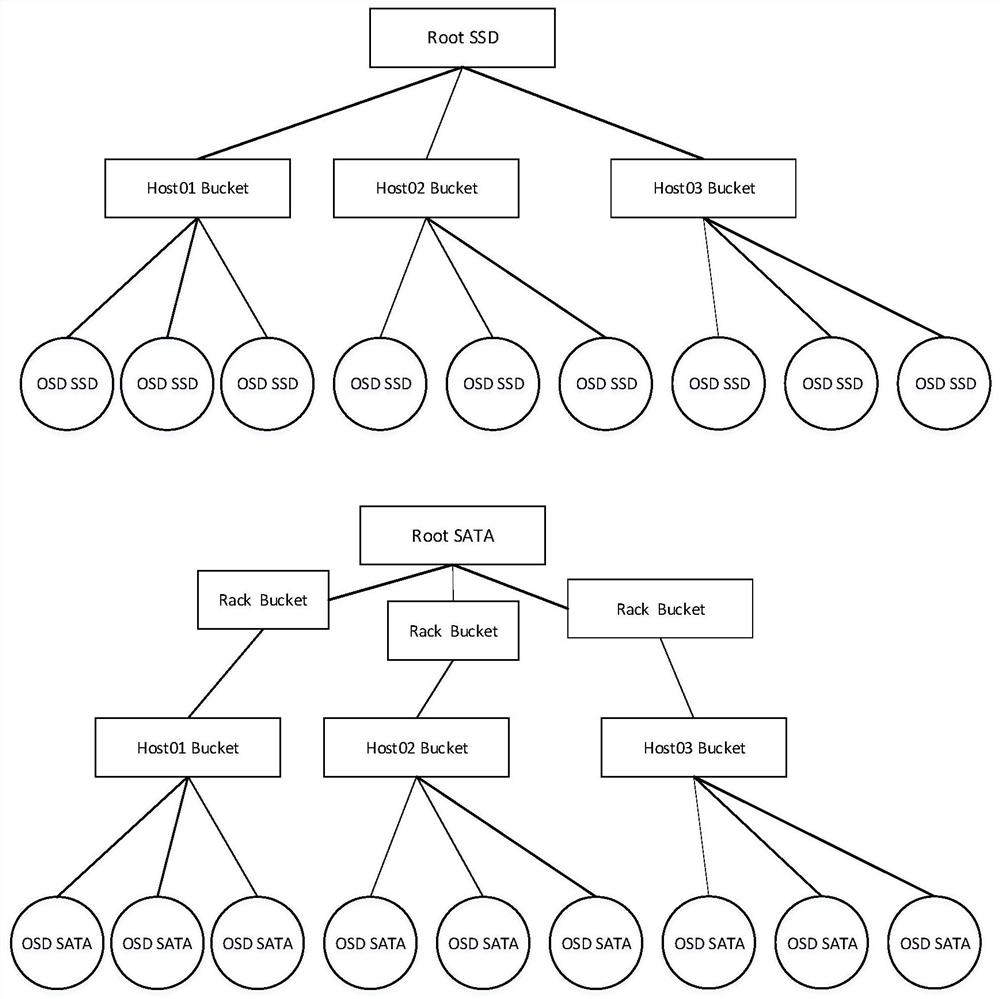
PendingCN111857735AMeet the requirements for resource partitioningImprove efficiencyVersion controlSoftware deploymentDomain levelPool
The invention discloses a Crush creation method and system for deploying Ceph based on Rook, and belongs to the technical field of cloud computing. The method comprises the following specific steps: S1, detecting a Ceph version, and deploying a Ceph cluster component service; S2, deploying and adding OSD nodes; S3, setting task execution by utilizing CrushRoot; S4, executing a Crush Rules task, and carrying out the creation according to the Crush Root fault domain level of the Ceph cluster; S5, executing the CepBlock Pool user-defined resource, and creating Pool according to the selected CephCrush Rule and the number of pg. According to the method and the device, the Crush Root and the Crush Rules are automatically created after the Ceph cluster is deployed by the Rook; the defect that the Crush Root and the Crush Rules cannot be automatically created after the Ceph cluster is quickly deployed by the Rook is overcome; the requirement that the Ceph cluster performs resource division ondifferent storage type nodes in an actual use scene is met; the deployment efficiency is improved through automatic creation, the efficiency of implementation personnel is improved, and the risk thaterrors are prone to occurring due to manual intervention is avoided.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
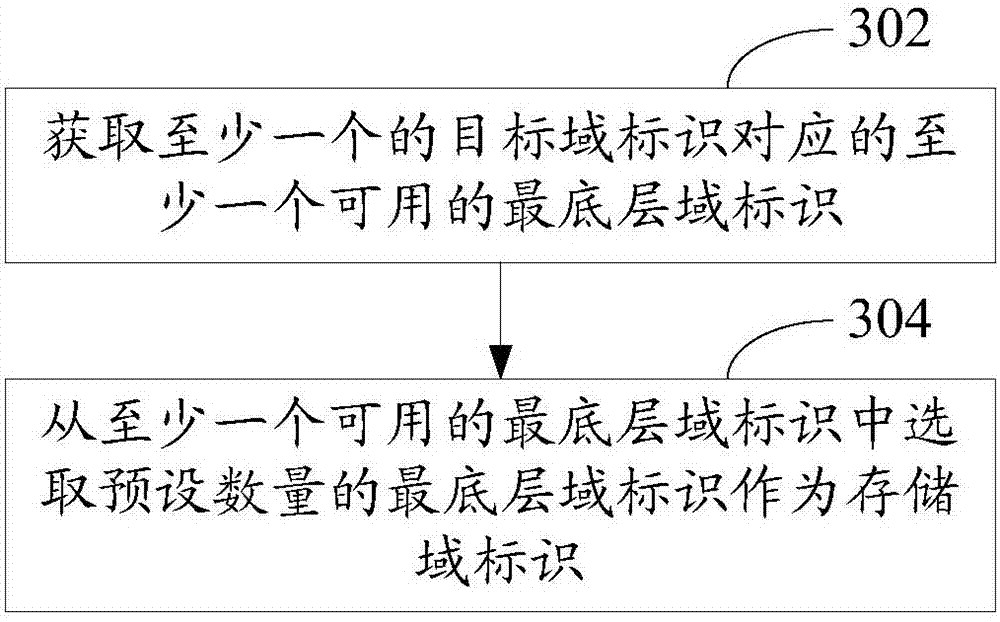
Fault domain technology-based data management method and apparatus
ActiveCN107085546AEasy to controlTake advantage ofRedundant operation error correctionDomain levelData management
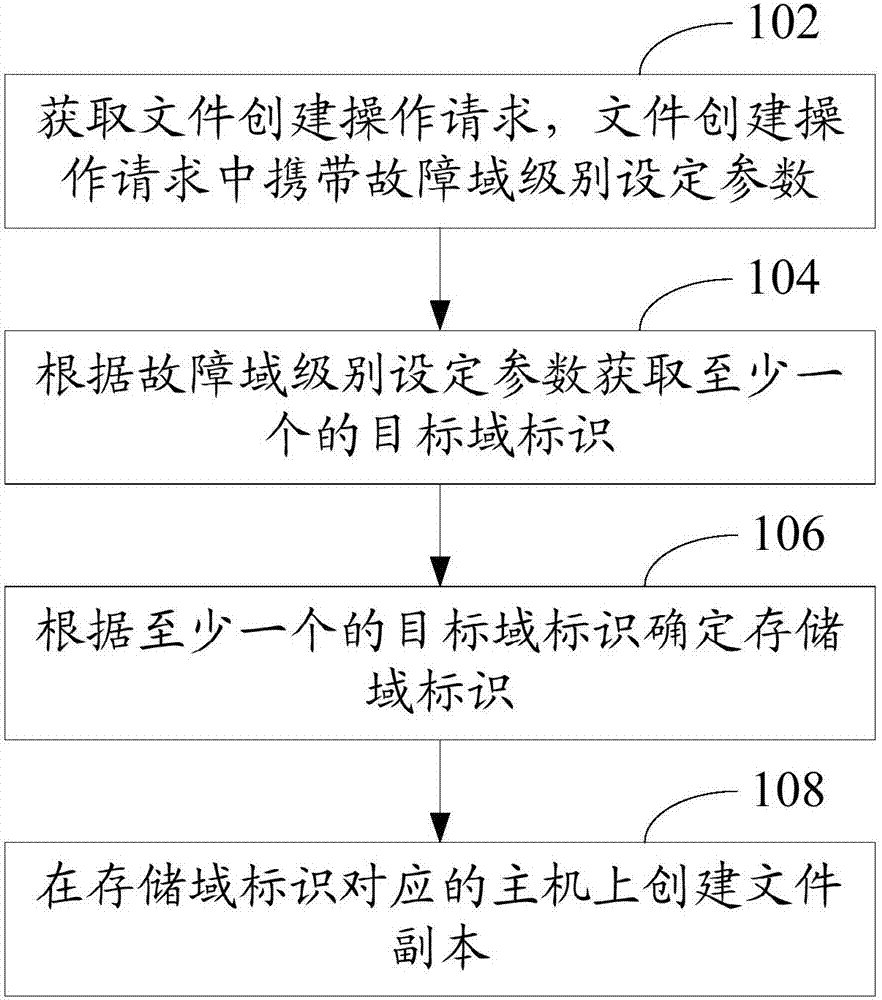
The invention relates to a fault domain technology-based data management method. The method comprises the steps of obtaining a file creation operation request, wherein the file creation operation request carries a fault domain level setting parameter; obtaining at least one target domain identifier according to the fault domain level setting parameter; determining a storage domain identifier according to the at least one target domain identifier; and creating a file copy on a host corresponding to the storage domain identifier. According to the method, a user can set a fault domain level of file copy creation according to the need, so that the user can control storage position and range of the file copy creation and the data management is more flexible; and meanwhile, the user controls different file copies to be created in different fault domain levels, so that storage resources of a distributed storage system can be utilized more efficiently and effectively, and the waste of the storage resources is avoided. In addition, the invention provides a fault domain technology-based data management apparatus.
Owner:SANGFOR TECH INC
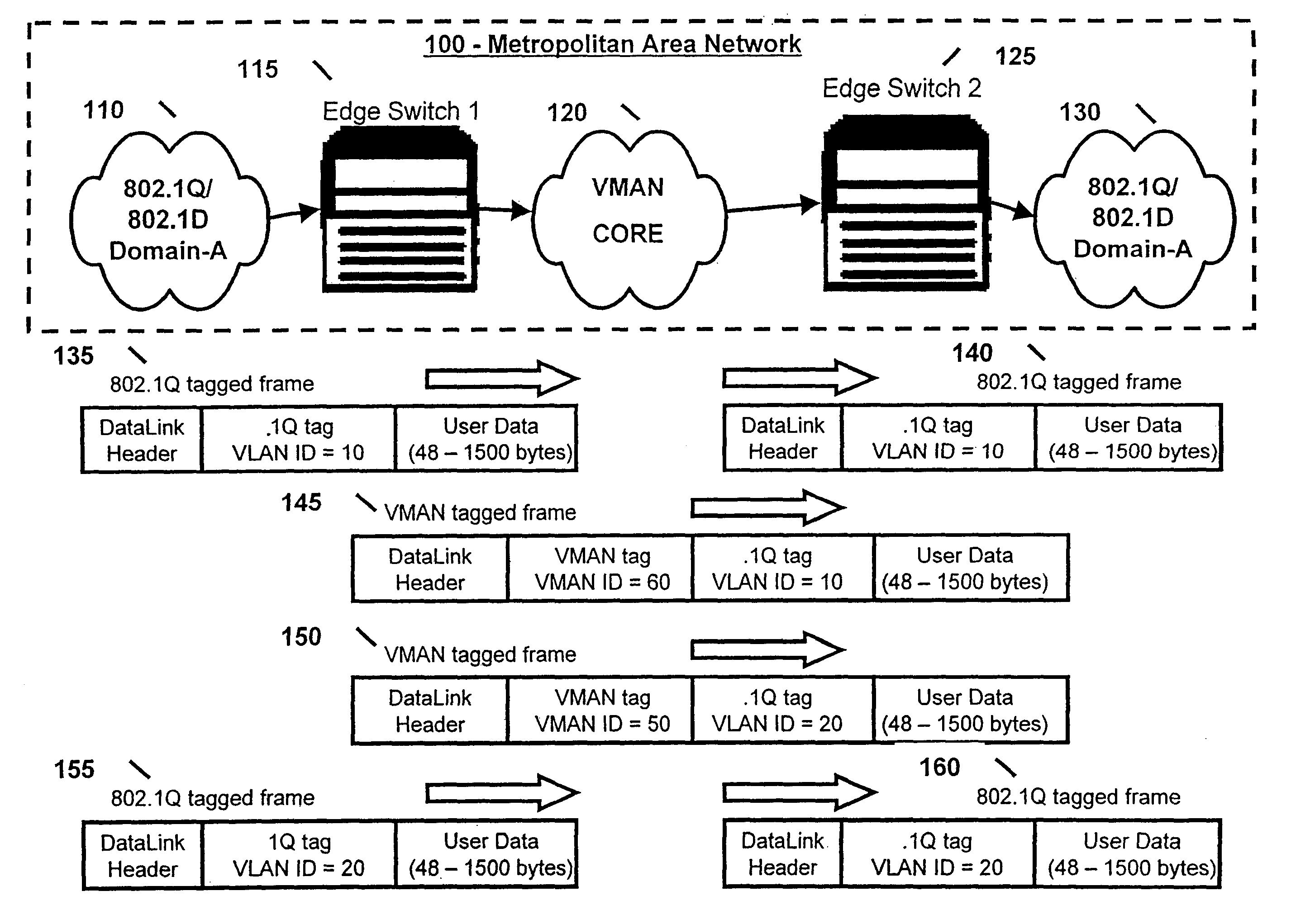
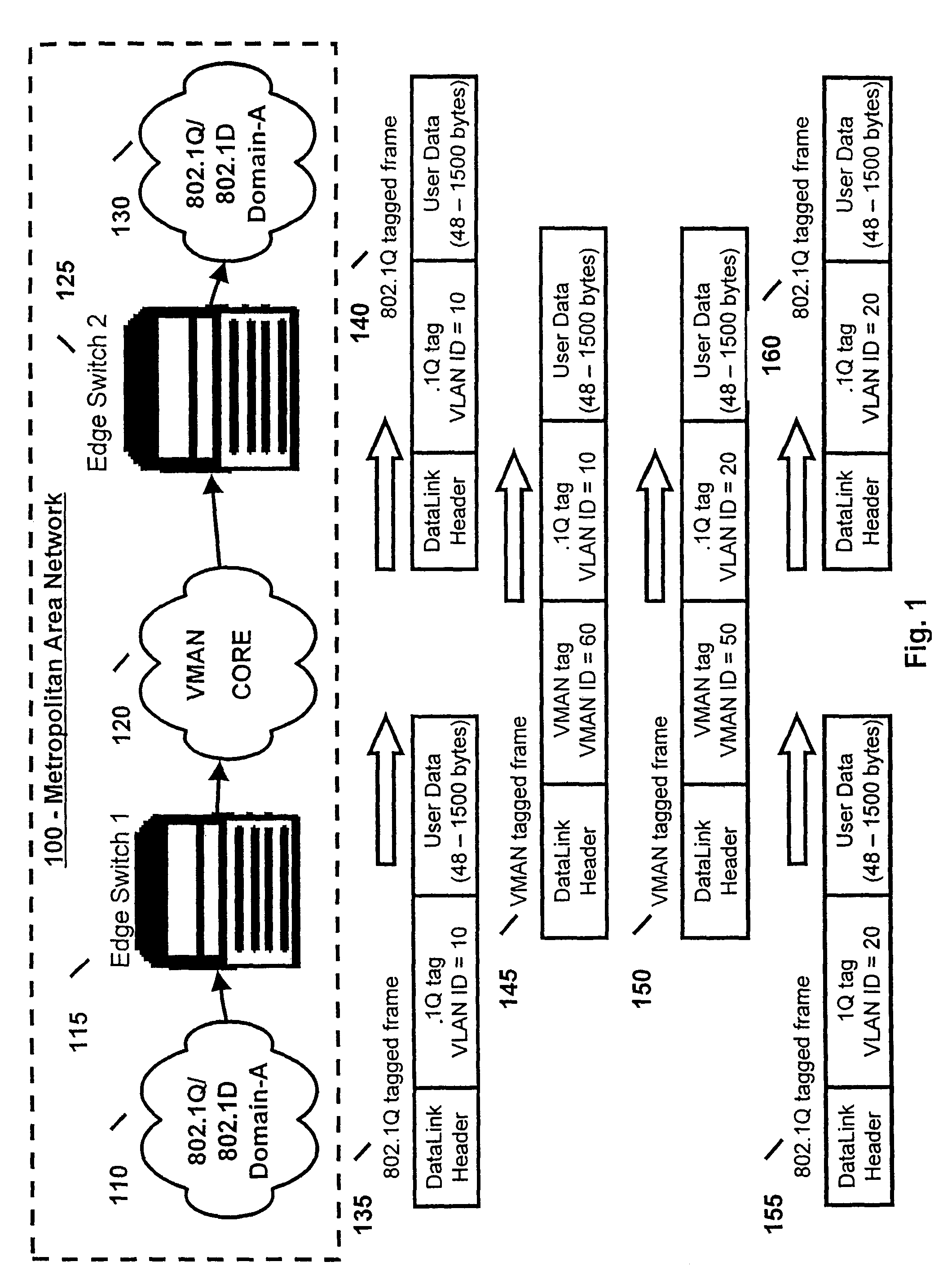
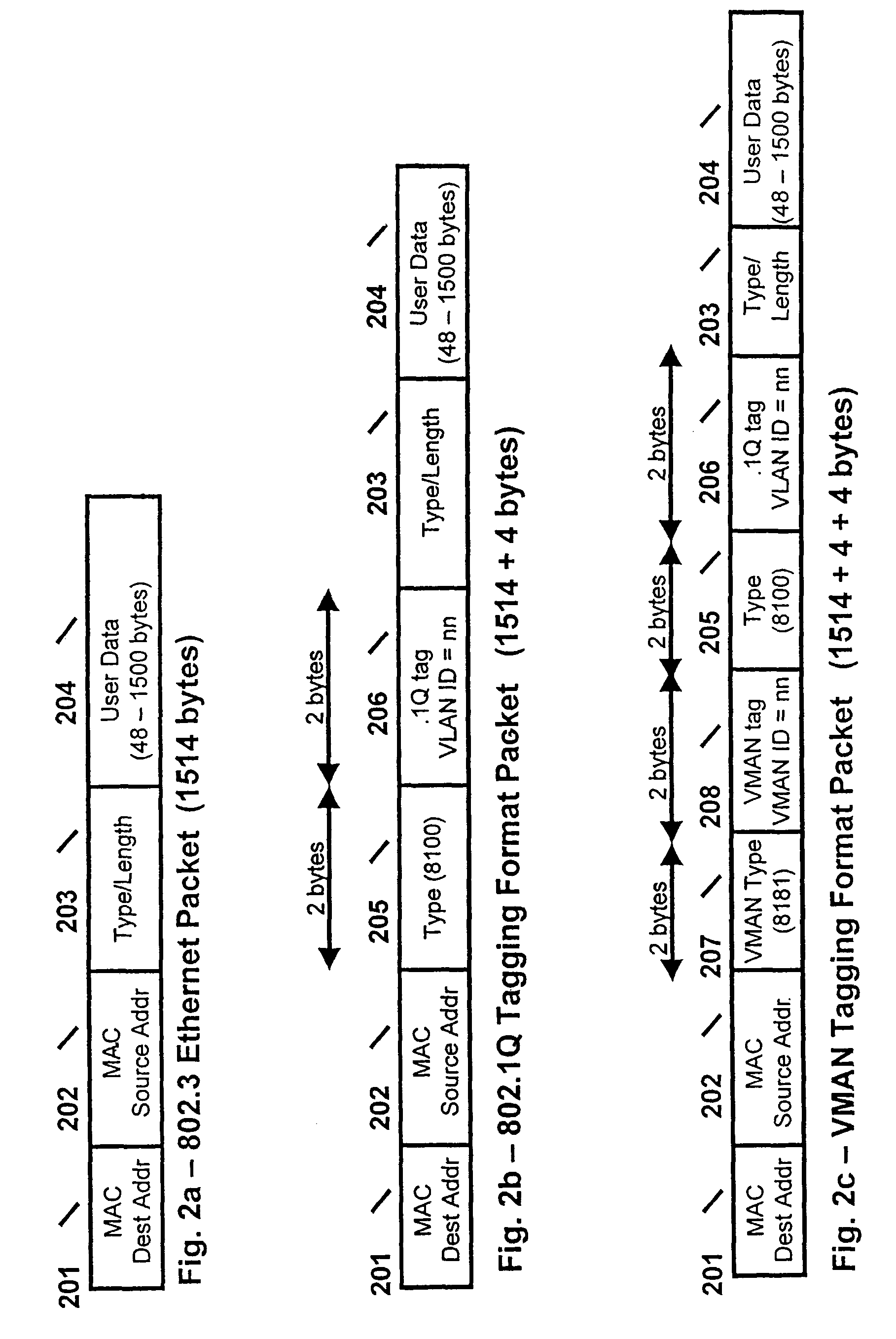
Method and system for VMAN protocol Layer-2 packet nested encapsulation
A method and system is provided in which MAN traffic is segregated at a customer and a provider domain level. A switch at the edge of the MAN encapsulates a data packet in a new header, which is used to specify the customer domain tags. The data packet is encapsulated further in another new header, which is used to specify new VMAN tags. The nested encapsulation is repeated as necessary until the data packet is forwarded to a remote switch at the edge of the MAN in accordance with the VMAN configuration or the source and destination address in the original data packet. The remote switch strips the VMAN tags from the data packet, and forwards the stripped data packet to the receiving customer domain as specified in the customer domain tag.
Owner:ARISTA NETWORKS
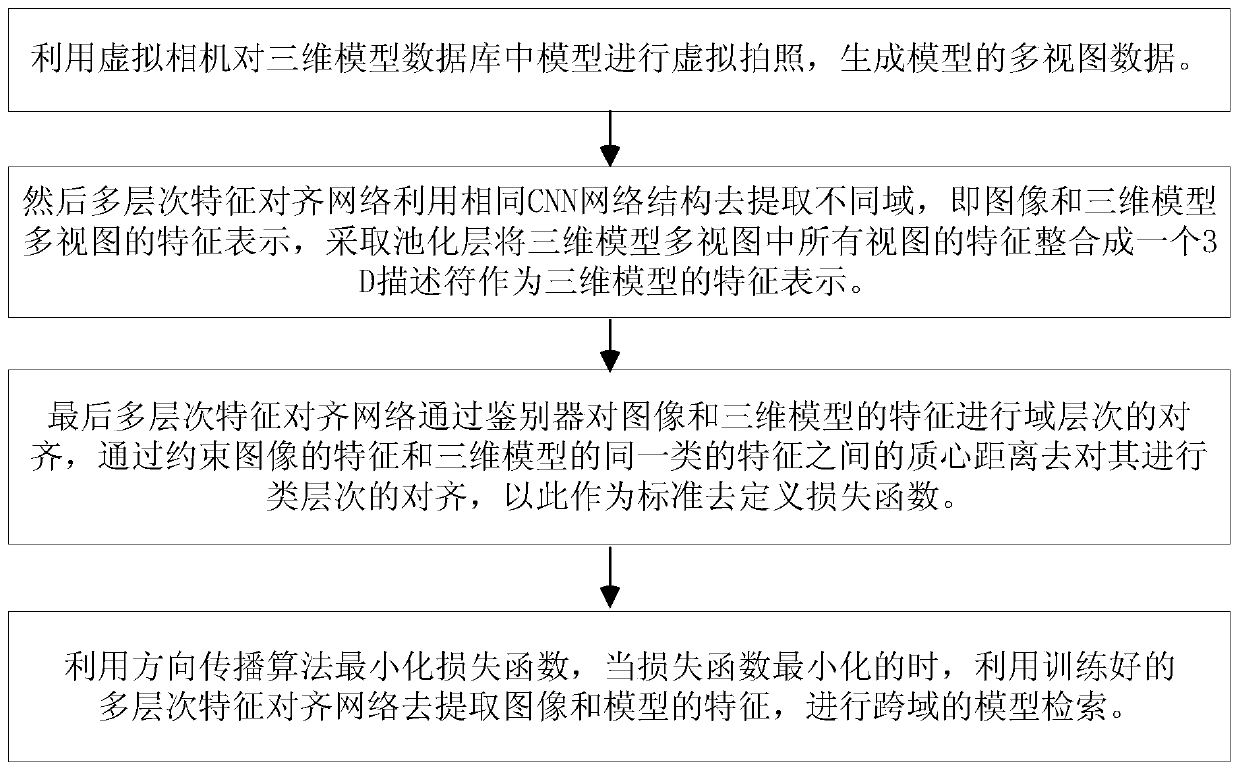
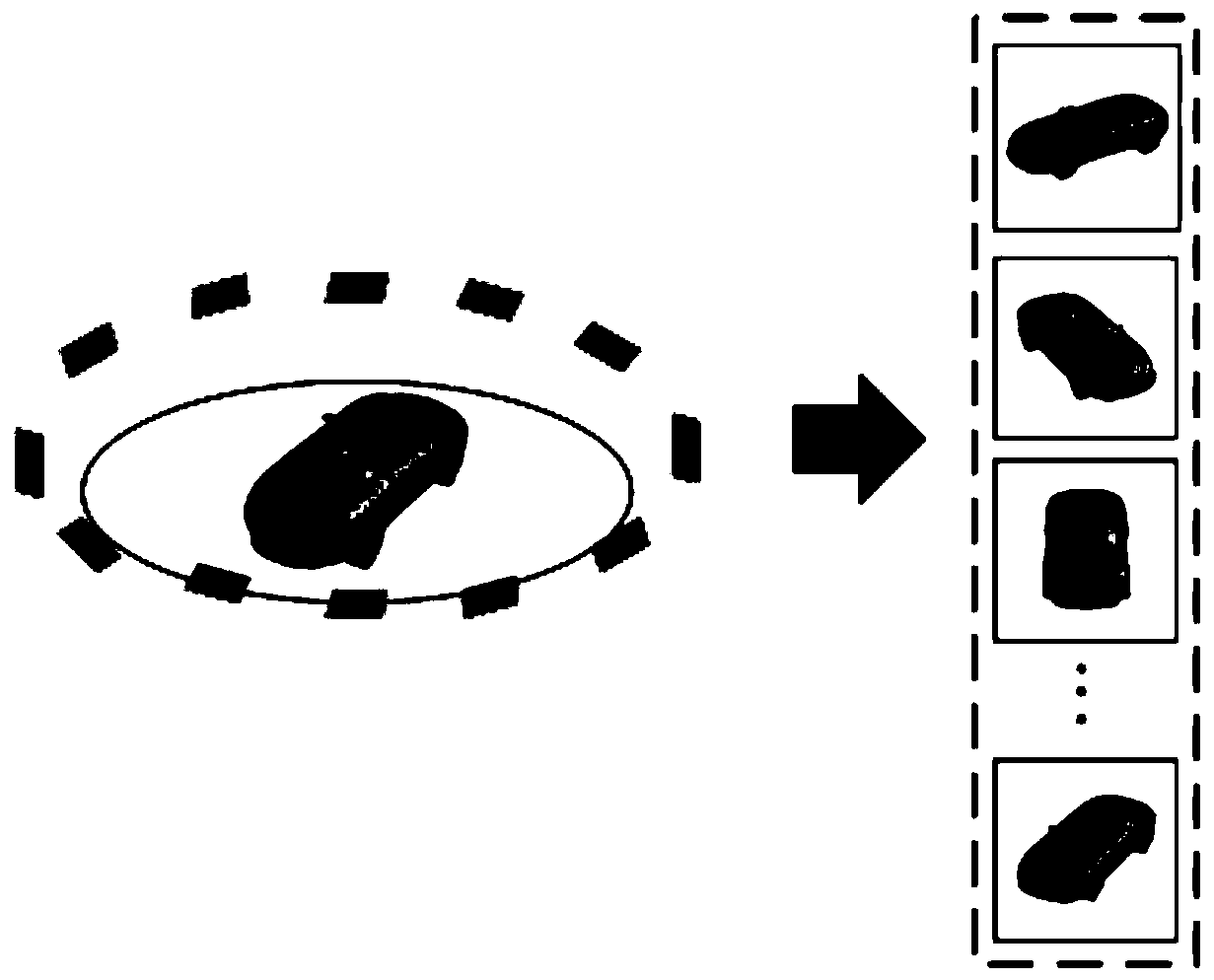
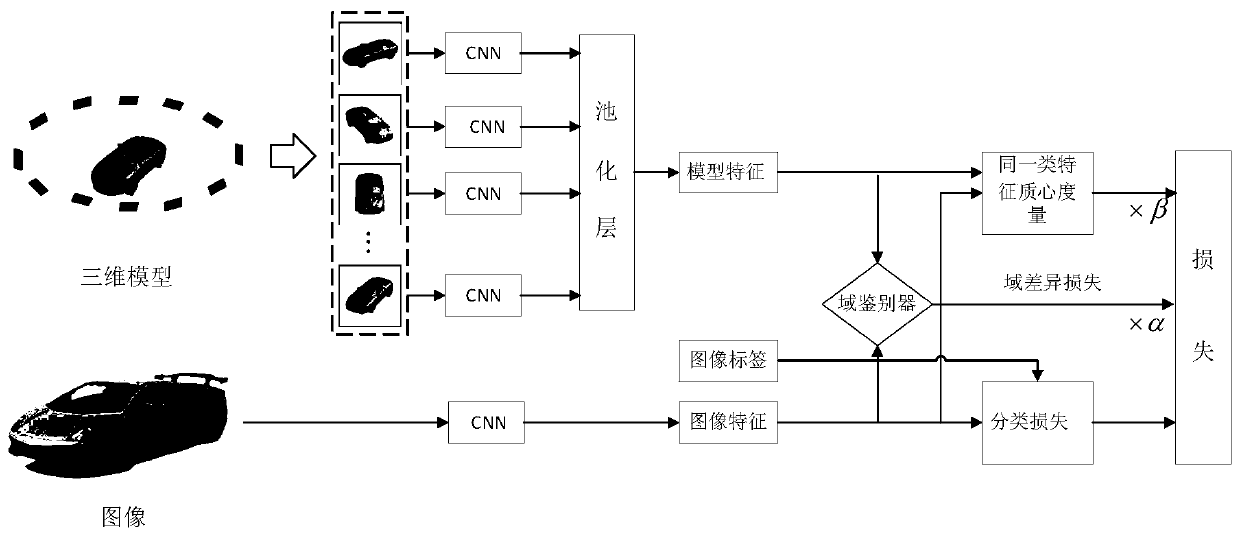
Cross-domain three-dimensional model retrieval method based on multi-level feature alignment network
PendingCN111078916AHigh precisionIdentifiableImage analysisDigital data information retrievalDomain levelVirtual camera
Owner:TIANJIN UNIV
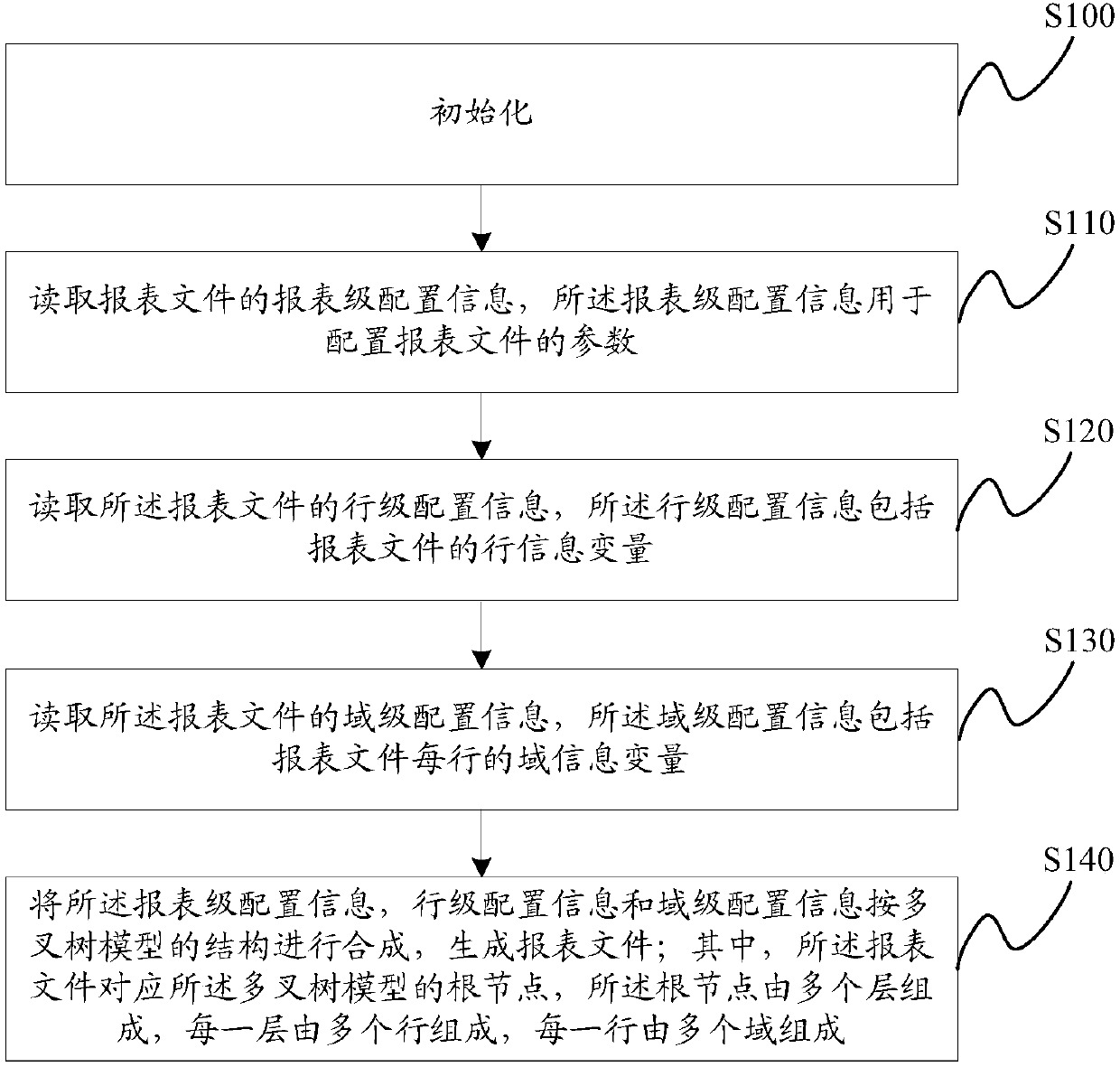
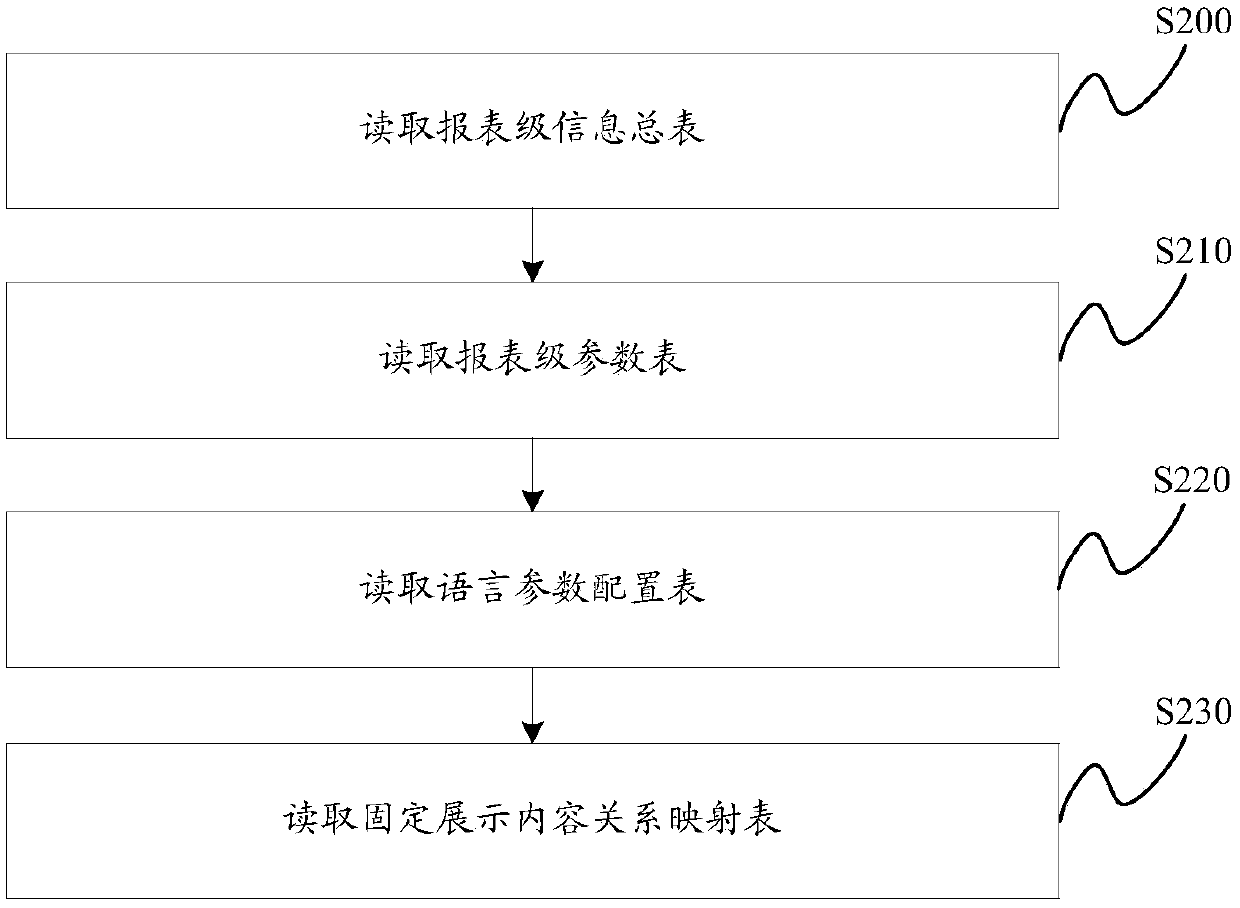
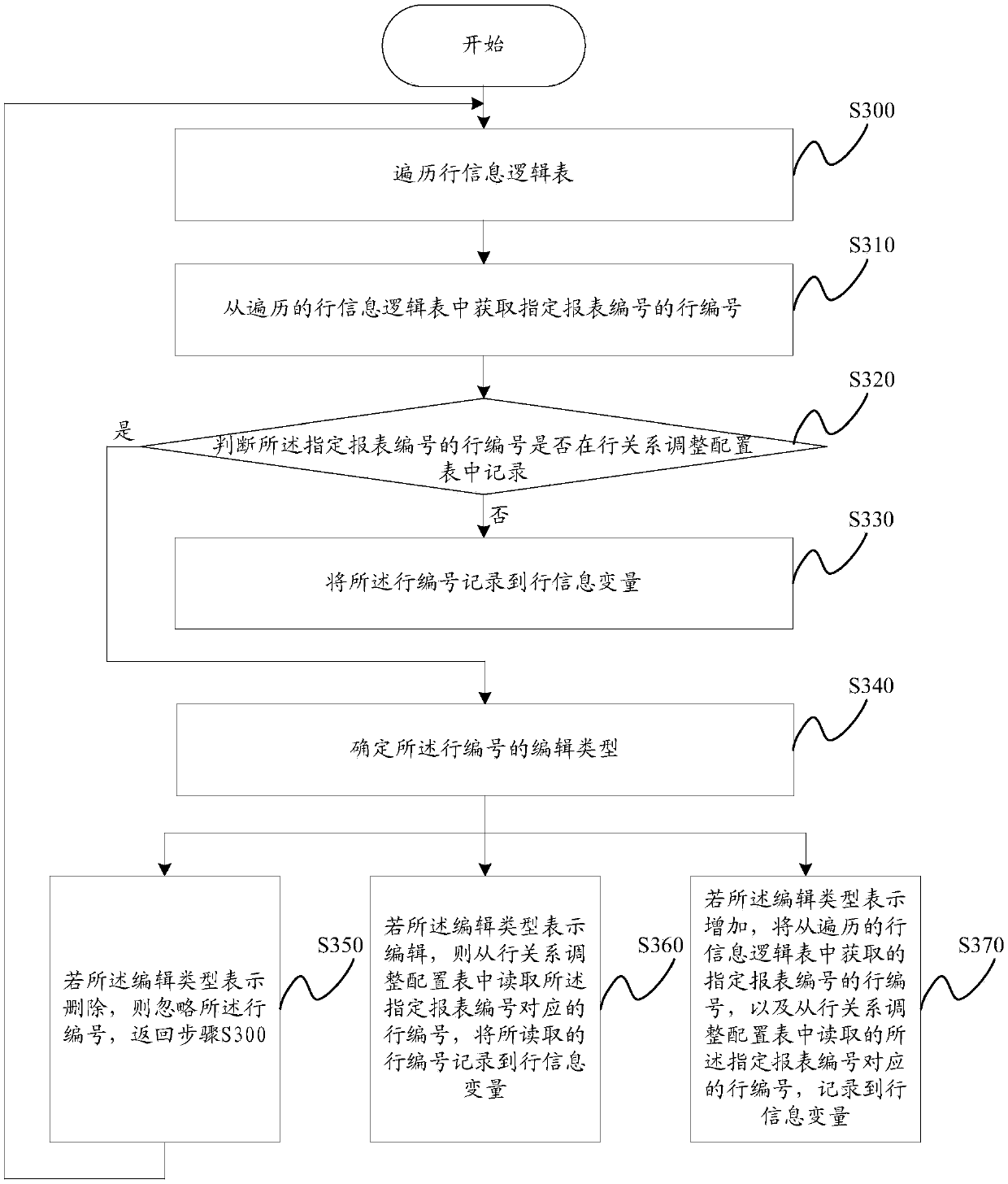
Report file generation method and apparatus
ActiveCN107609131ARealize generationReduce generation costSpecial data processing applicationsDomain levelStructure of Management Information
Embodiments of the invention provide a report file generation method and apparatus. The method comprises the steps of performing initialization; reading report level configuration information, whereinthe report level configuration information is used for configuring parameters of a report file; reading row level configuration information, wherein the row level configuration information comprisesa row information variable of the report file; reading domain level configuration information, wherein the domain level configuration information comprises a domain information variable of each row ofthe report file; and synthesizing the report level configuration information, the row level configuration information and the domain level configuration information according to the structure of a multi-way tree model to generate the report file, wherein the report file corresponds to a root node of the multi-way tree model, the root node consists of multiple layers, each layer consists of multiple rows, and each row consists of multiple domains. The cost of generating the report file is reduced and the maintenance convenience is improved.
Owner:BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com