Mobile Privacy Information Proxy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
examples
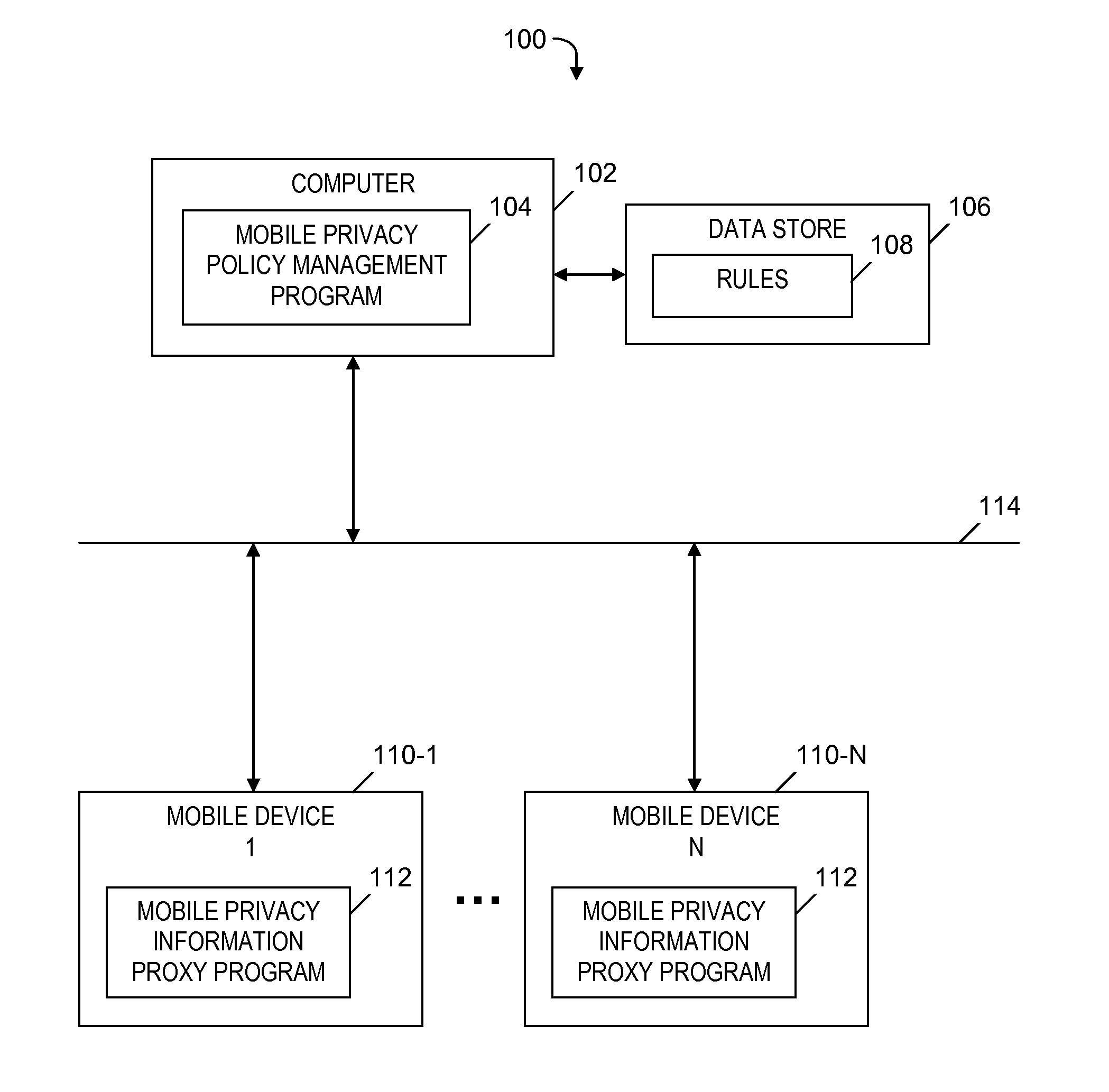
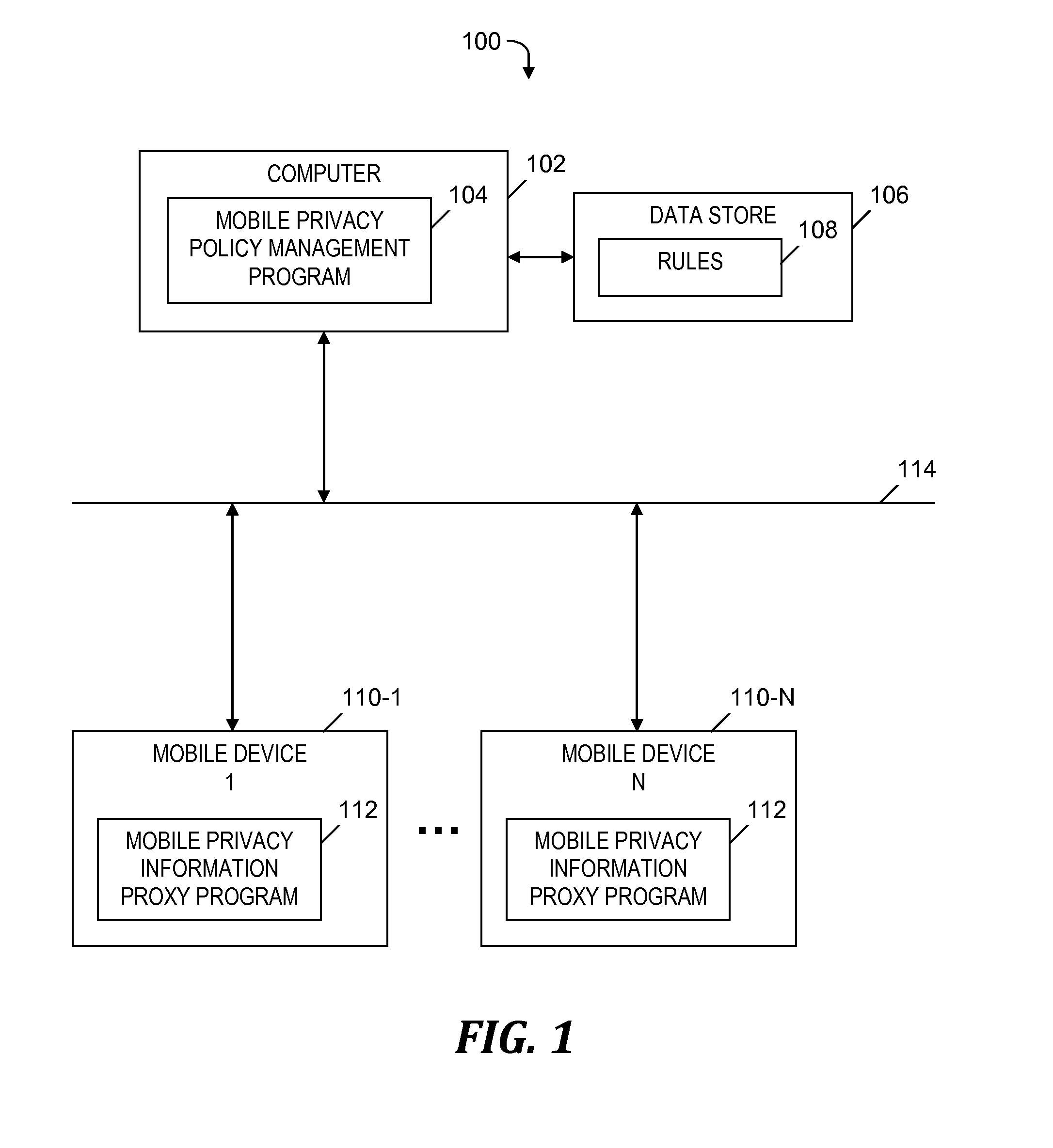
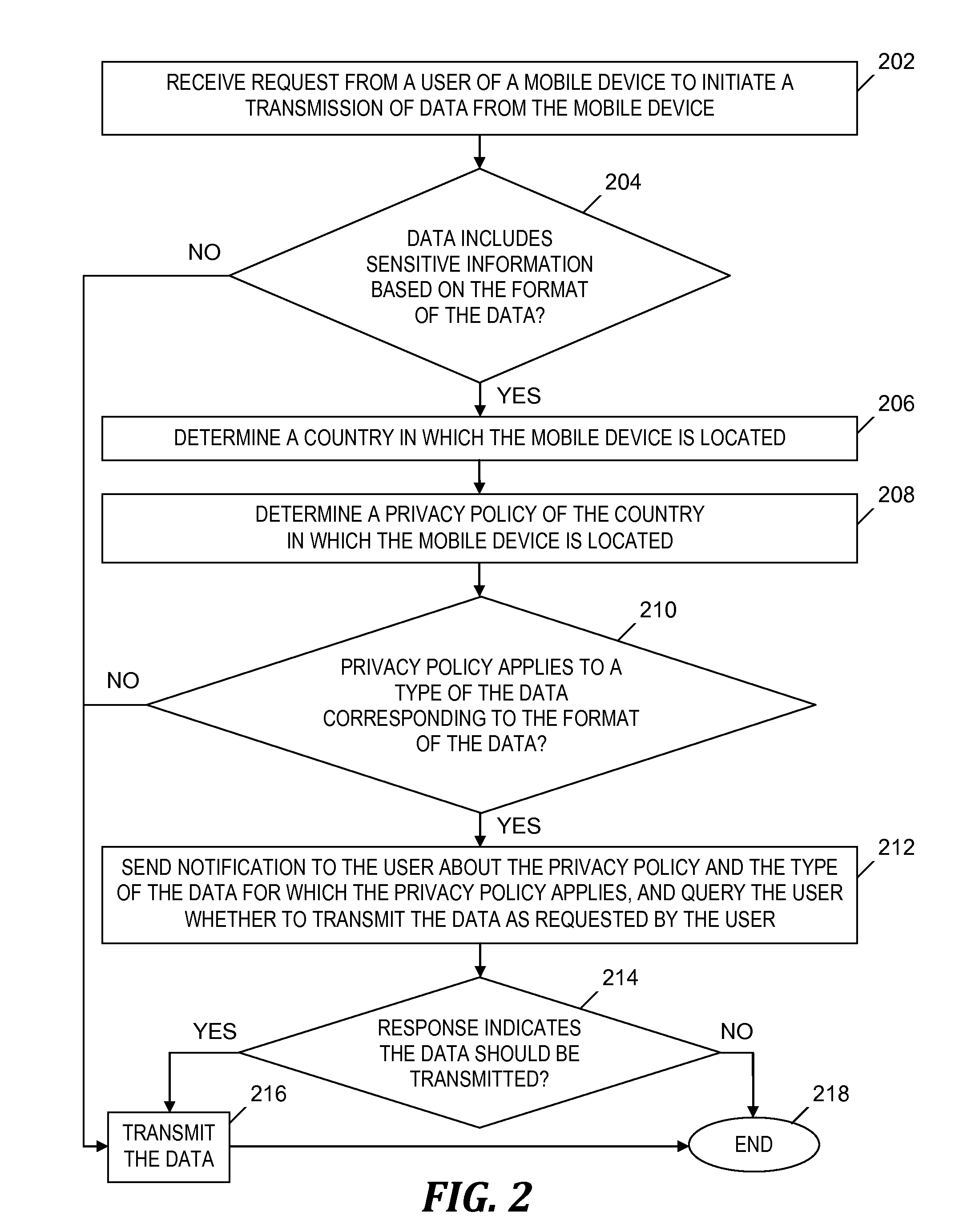
[0050]An example of privacy rule 108 (see FIG. 1) is stored in the form of an Extensible Markup Language (XML) document, which includes the following tags:[0051] is the root tag of the privacy rule 108 (see FIG. 1)[0052] is a tag that includes the name of the privacy rule 108 (see FIG. 1)[0053] is a tag that includes a regular expression to be used while applying the privacy rule 108 (see FIG. 1) to data (see step 210, described below), which verifies that the data includes sensitive information based on the location of the mobile device 110-1 (see FIG. 1)[0054] is a tag that includes a category to which the privacy rule 108 (see FIG. 1) belongs, which specifies the type of the data to which the privacy rule 108 (see FIG. 1) is applied, and which has an attribute ‘policy-type’, which specifies the type of the category. For example, ‘email’ is a category which has the ‘policy-type’ of “sensitive private information.”[0055] is a tag that specifies a locale of users for whom the privac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com