Method and system for certification
A technology of identity authentication and authentication center, which is applied in the direction of user identity/authority verification, public key for secure communication, etc., and can solve the problems of difficult discovery, complicated processing, and long certificate path of the mesh authentication center structure path
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
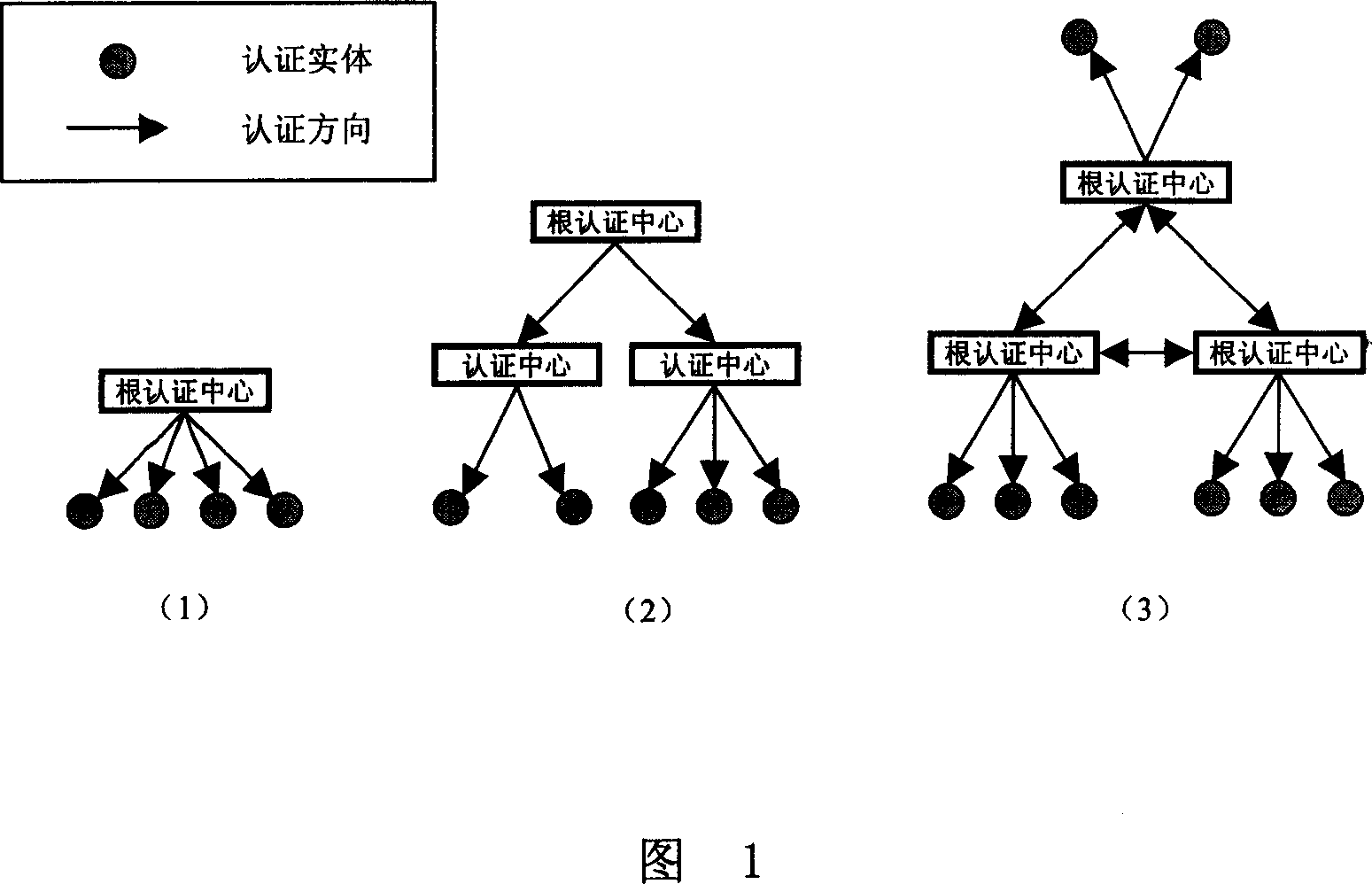
[0028] The authentication process of identity authentication between authentication centers in the extended PKI / CA system will be described in detail below.
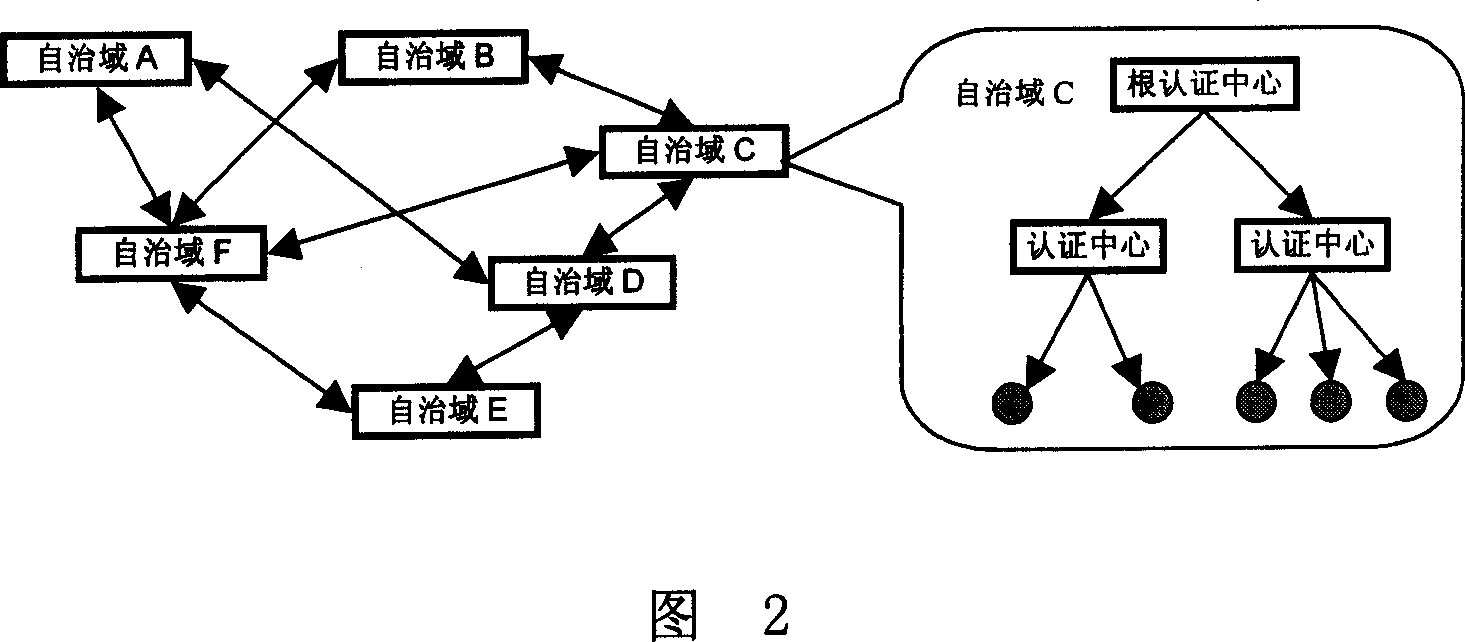
[0029] The architecture of this extended PKI / CA system is shown in Figure 2. It consists of six autonomous domains (autonomous domain A - autonomous domain F), and each domain has a unique root certification center. According to the size and application of the domain According to actual needs, multiple secondary certification centers can be dynamically configured to provide various types of certificate services for end users. As shown on the right side of the figure, the root certification center in autonomous domain C has two secondary certification centers.
[0030] certificate issuer
[0031] Table I
[0032] The structure of a domain certificate mainly includes eight basic elements, namely:
[0033] Certificate Issuer: The distinguished name of the issuer of the certificate.
[0034] Certi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com