Safety communication method
A technology for secure communication and called users, applied in the field of secure communication, can solve the problems of host monitoring and hidden dangers, and achieve the effect of ensuring user communication security and avoiding short messages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
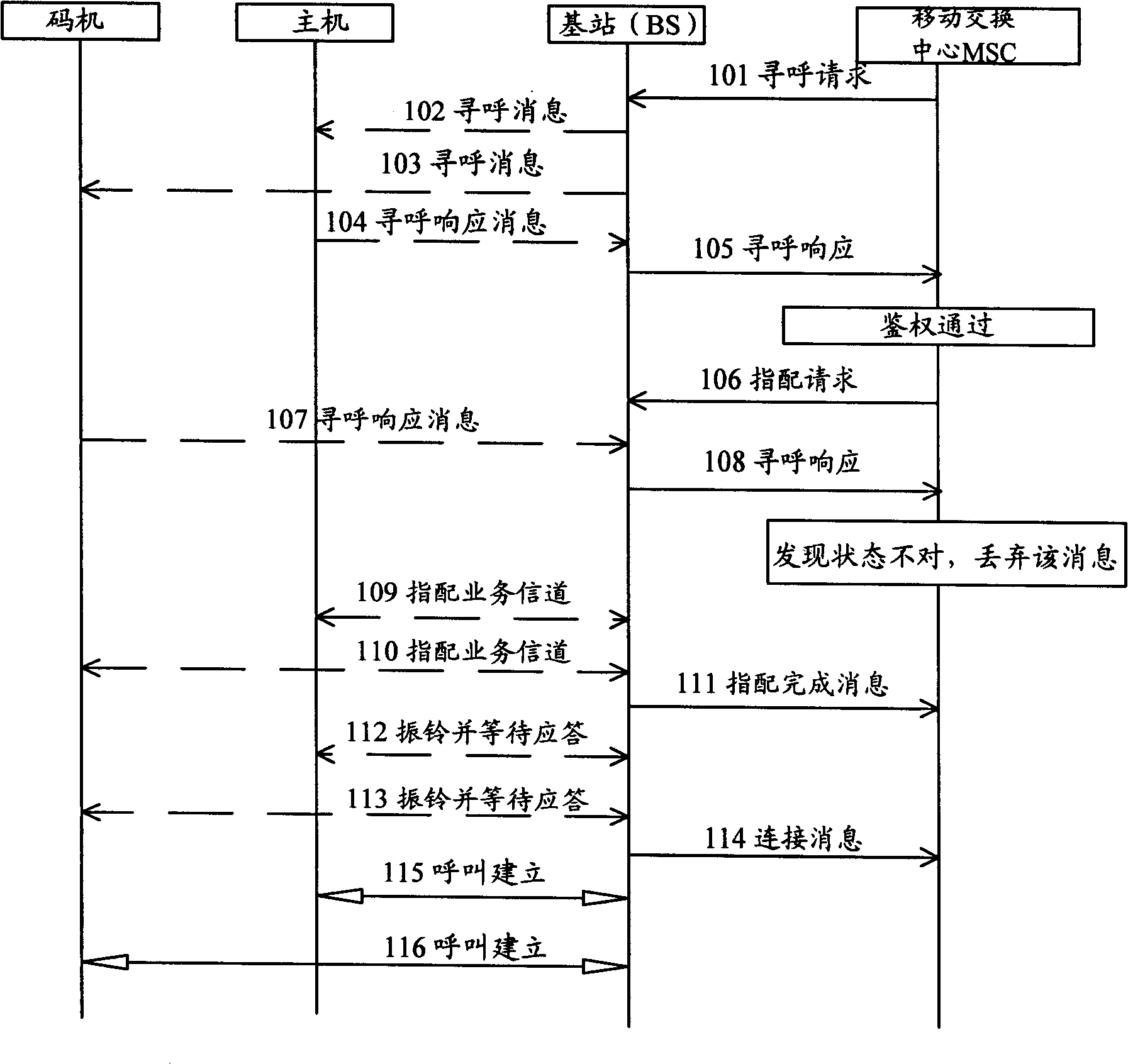
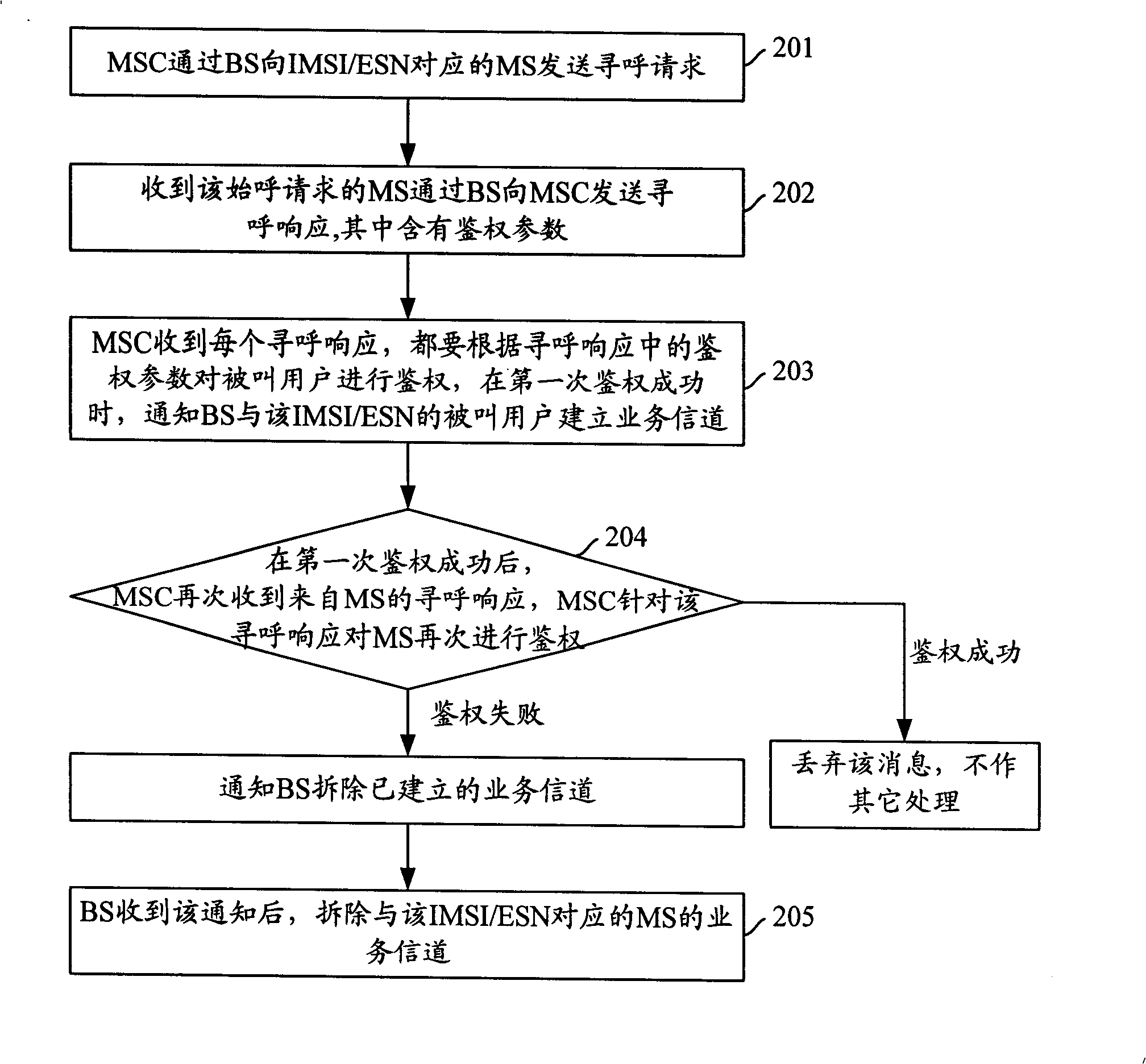
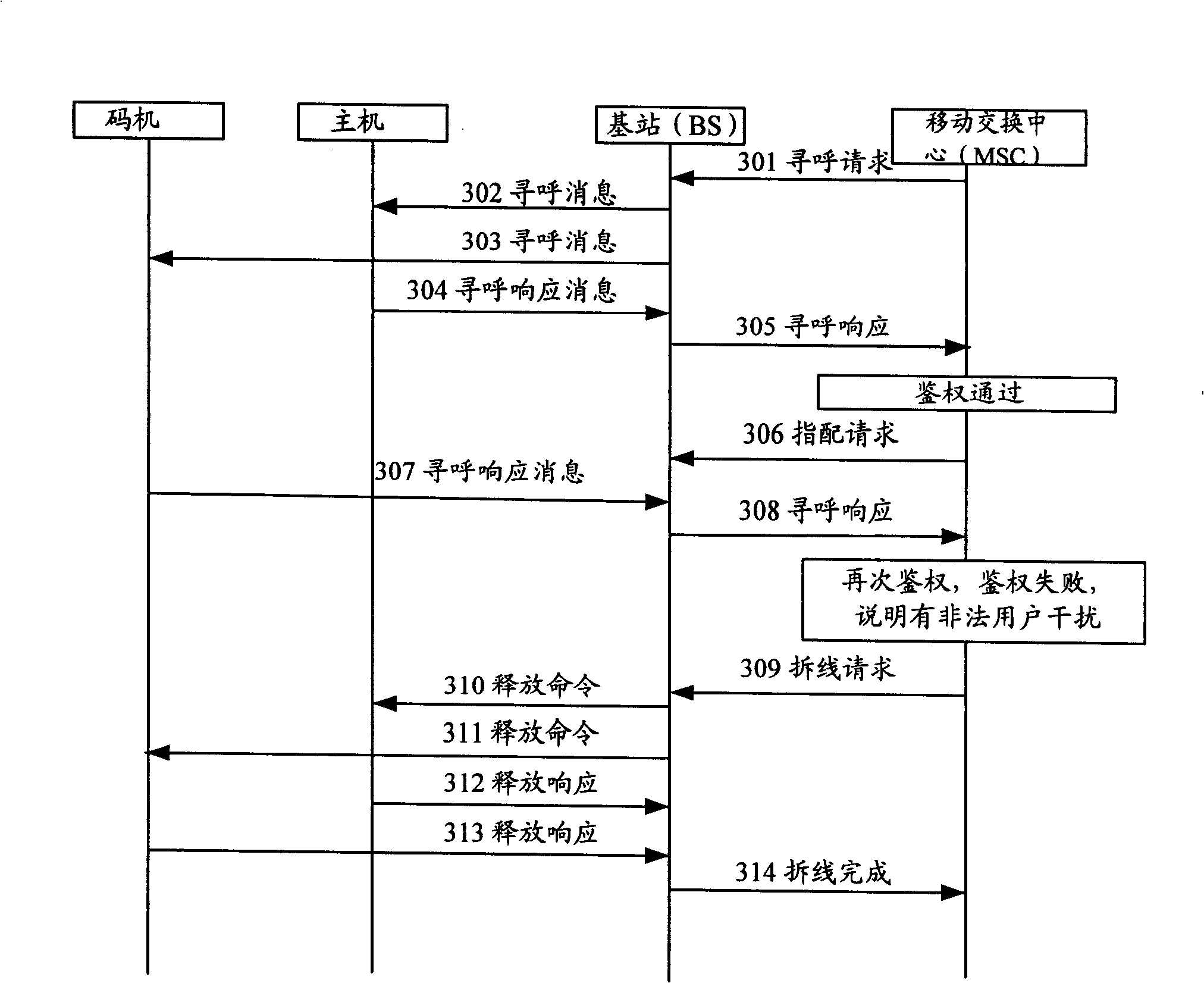
[0035] The main method of the present invention is: the MSC sends a paging request to the MS corresponding to the IMSI / ESN through the BS; when the MSC receives the paging response from the MS forwarded by the BS, it authenticates the MS; In the service channel between the BS and the MS, if the authentication fails, the called user is considered to be an illegal user, and the MSC continues to wait. After the MSC authentication passes, if the MSC receives the paging response from the MS forwarded by the BS again, it will authenticate the called user again. There is a code machine MS, which notifies the BS to tear down the service channel between the called users corresponding to the IMSI / ESN, and stop the communication.
[0036] see figure 2 Shown, the concrete steps that realize the inventive method are as follows:
[0037] Step 201: The MSC sends a paging request to the MS corresponding to the IMSI / ESN through the BS.
[0038] Step 202: The MS receiving the paging request...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com