Malevolence code automatic recognition method
A technology for automatic identification and malicious code, applied in the field of automatic analysis of malicious code, it can solve the problem that it is difficult to establish a robust and differentiated model, and achieve the effect of speeding up the analysis process and covering a wide range of analysis.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
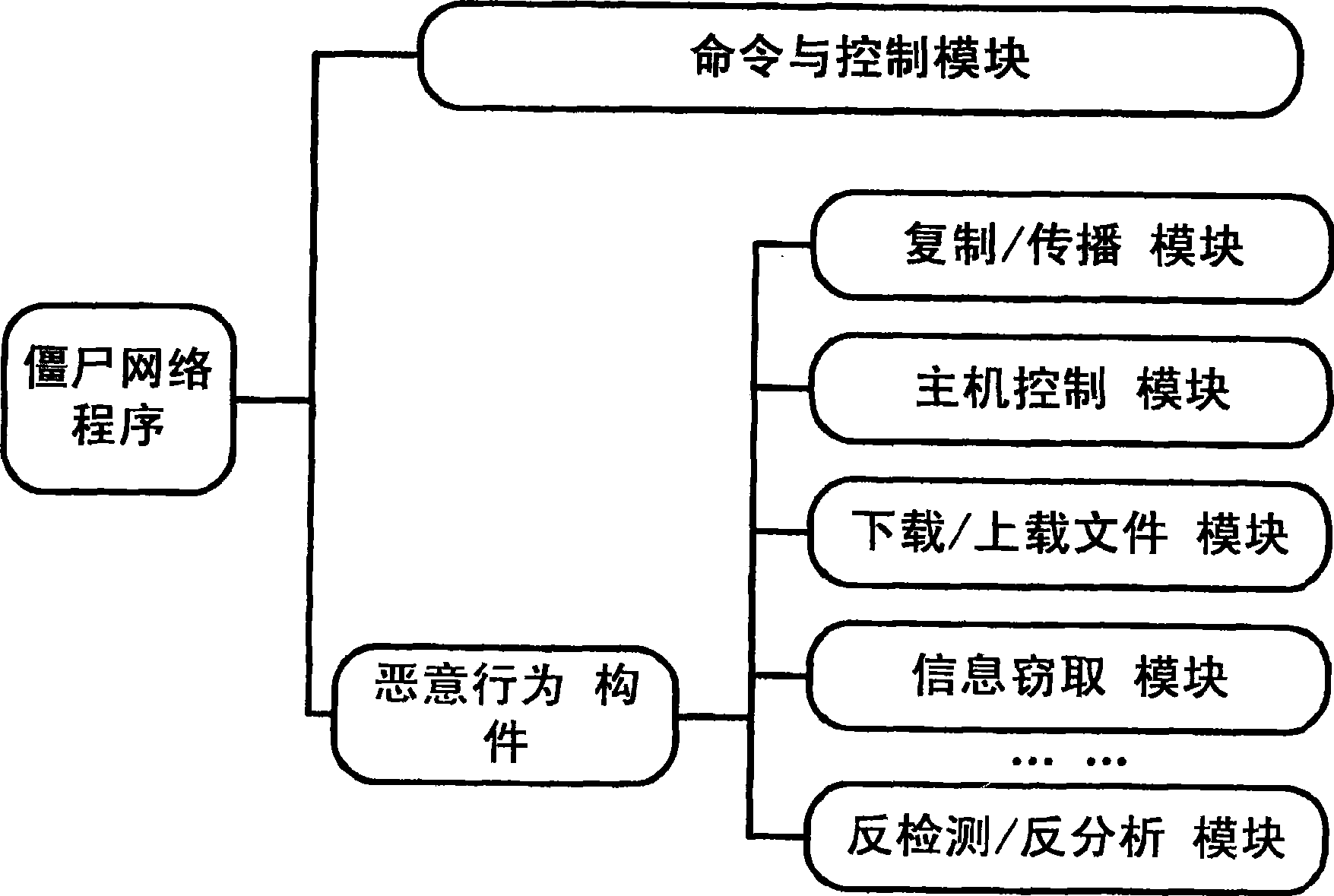
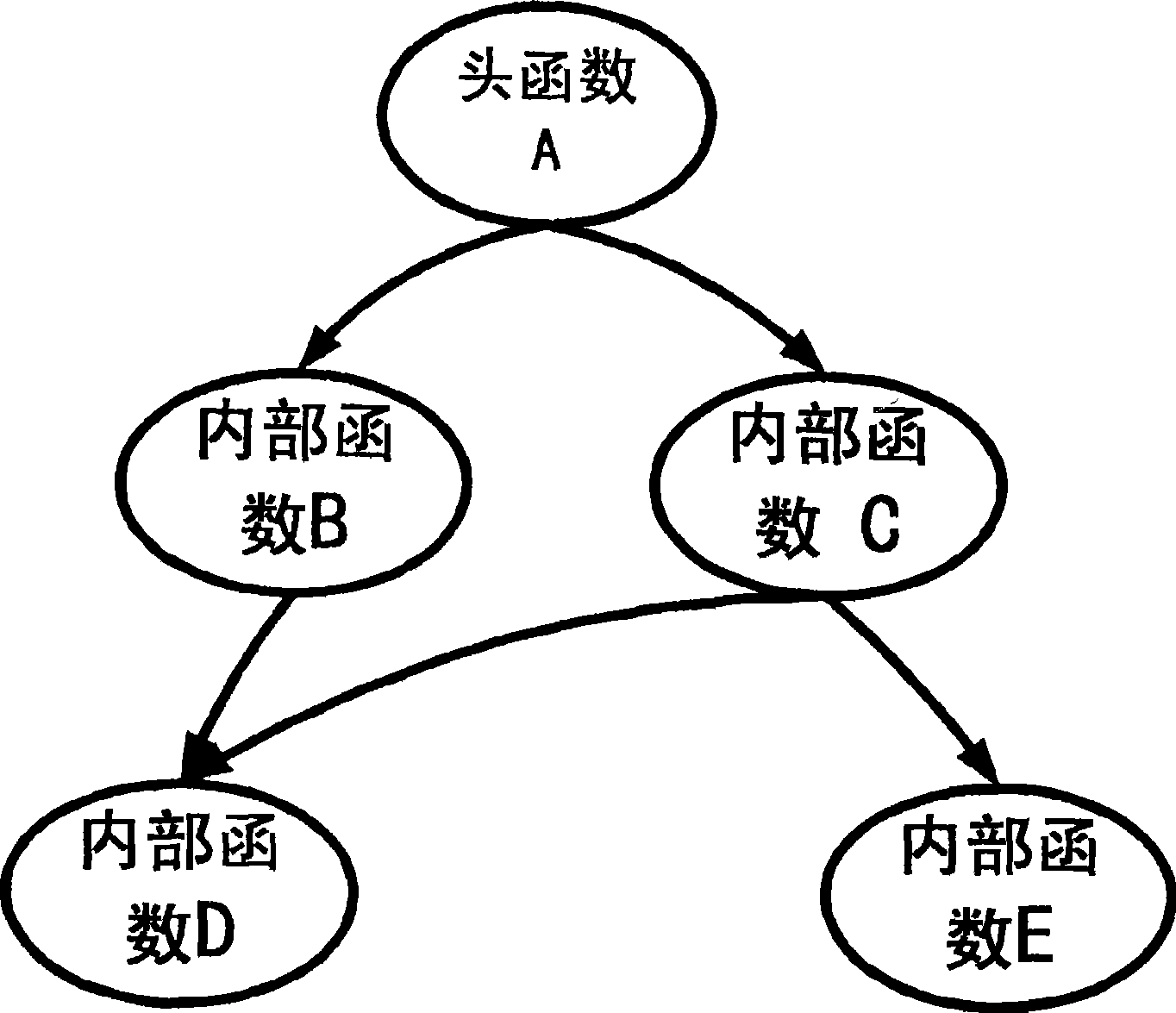
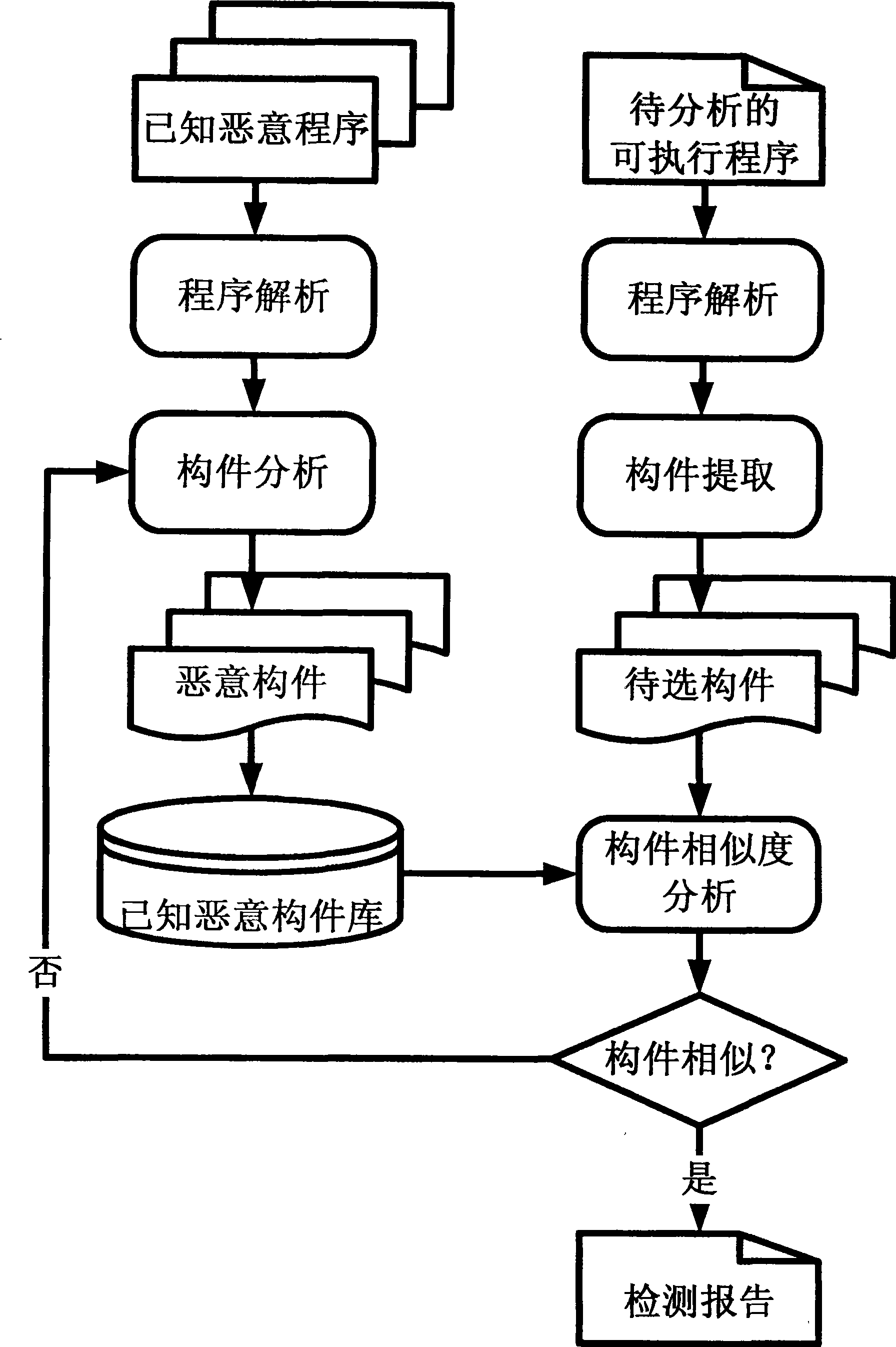
[0034] In the present invention, a component is defined as a program module composed of a group of related functions to complete a specific function. This function cluster contains a header function, that is, the construction header, which directly or indirectly calls all other functions in the cluster. figure 2 Shown is a schematic diagram of the components defined in the present invention.
[0035]The invention uses component extraction technology and binary code similarity comparison technology in the field of reverse engineering. Component extraction technology is an important research topic in the field of software engineering, and its main goal is to identify reusable components from legacy code. The method of component extraction and evaluation (see literature: Luo Jing, Zhang Lu, Sun Jiasu "Review of Component Extraction Technology", Computer Science, Volume 32, December 2005), including domain knowledge, structure and component measurement, etc., this kind of The m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com