Method and system for internal memory monitoring management
A technology of memory management and monitoring management, applied in the direction of multi-program device, resource allocation, etc., can solve problems such as difficulty in locating source code, achieve the effects of ensuring safe use, saving development and debugging time, and improving memory allocation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
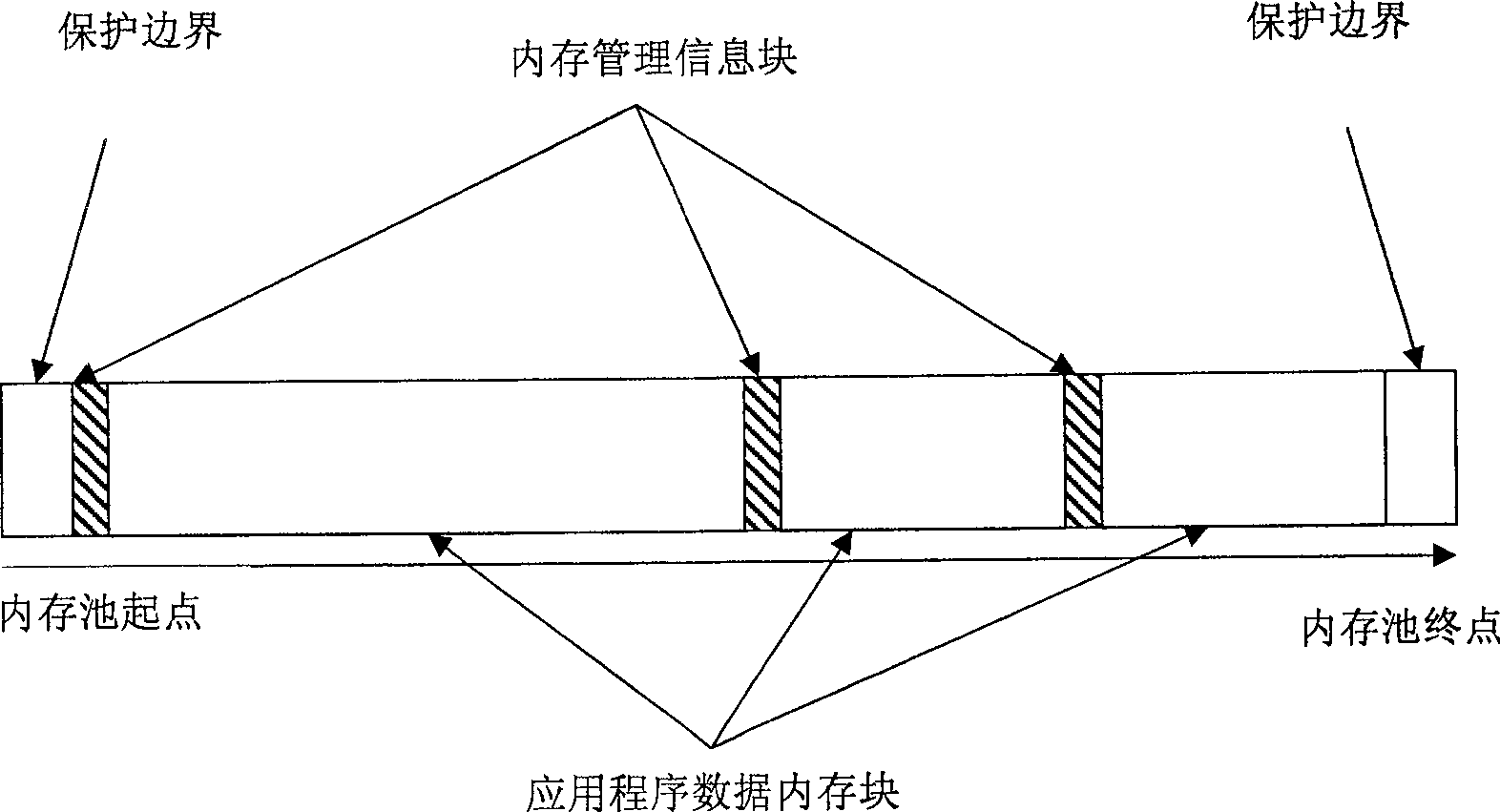
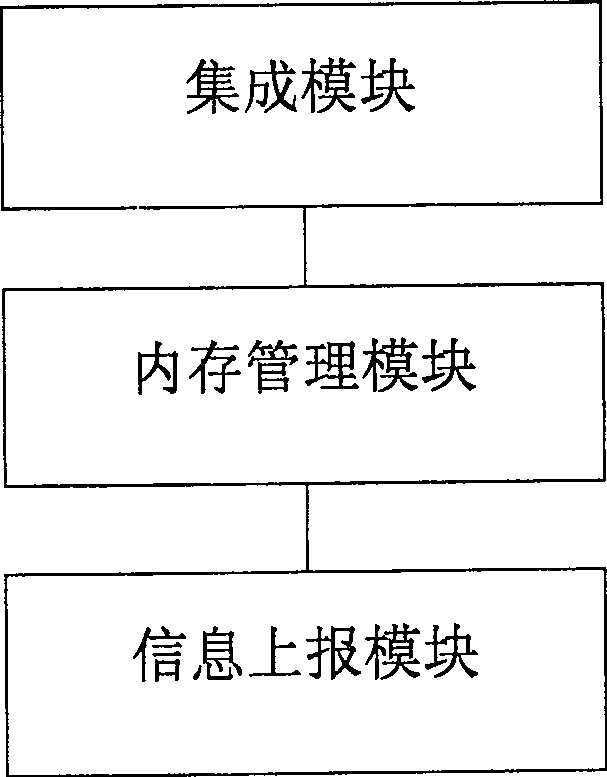
[0043] The purpose of the embodiment of the present invention is to provide an efficient memory monitoring and management module for C language (comprising VC, C++, etc.) Monitor and access, track and record memory leaks and illegal access information, and provide traceability basis for developers to quickly and accurately locate program problems.
[0044] The method described in the embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings.
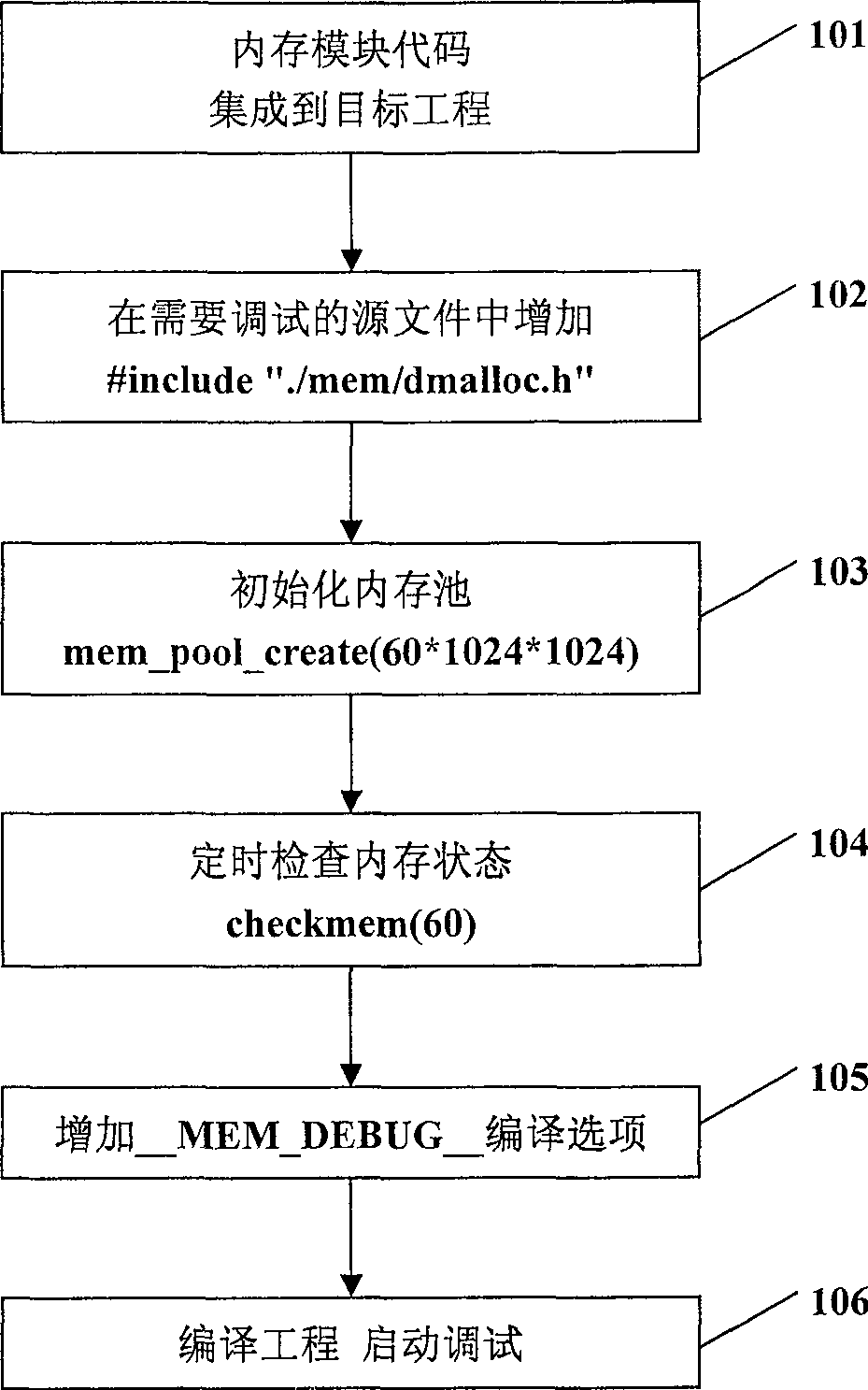
[0045] First, integrate the memory management module into the application; specifically, figure 1 as shown, figure 1 It is a schematic flow chart of integrating the memory management module into the application program, which specifically includes the following steps:
[0046] Step 101: Add the source code of the memory management module to the target project.
[0047] Step 102: Add #include ". / mem / dmalloc.h" reference in the target C file to introduce overloaded functions; spe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com