Computer I/O port control program
A port control, computer technology, used in computing, user identity/authority verification, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described in detail below in conjunction with the accompanying drawings.
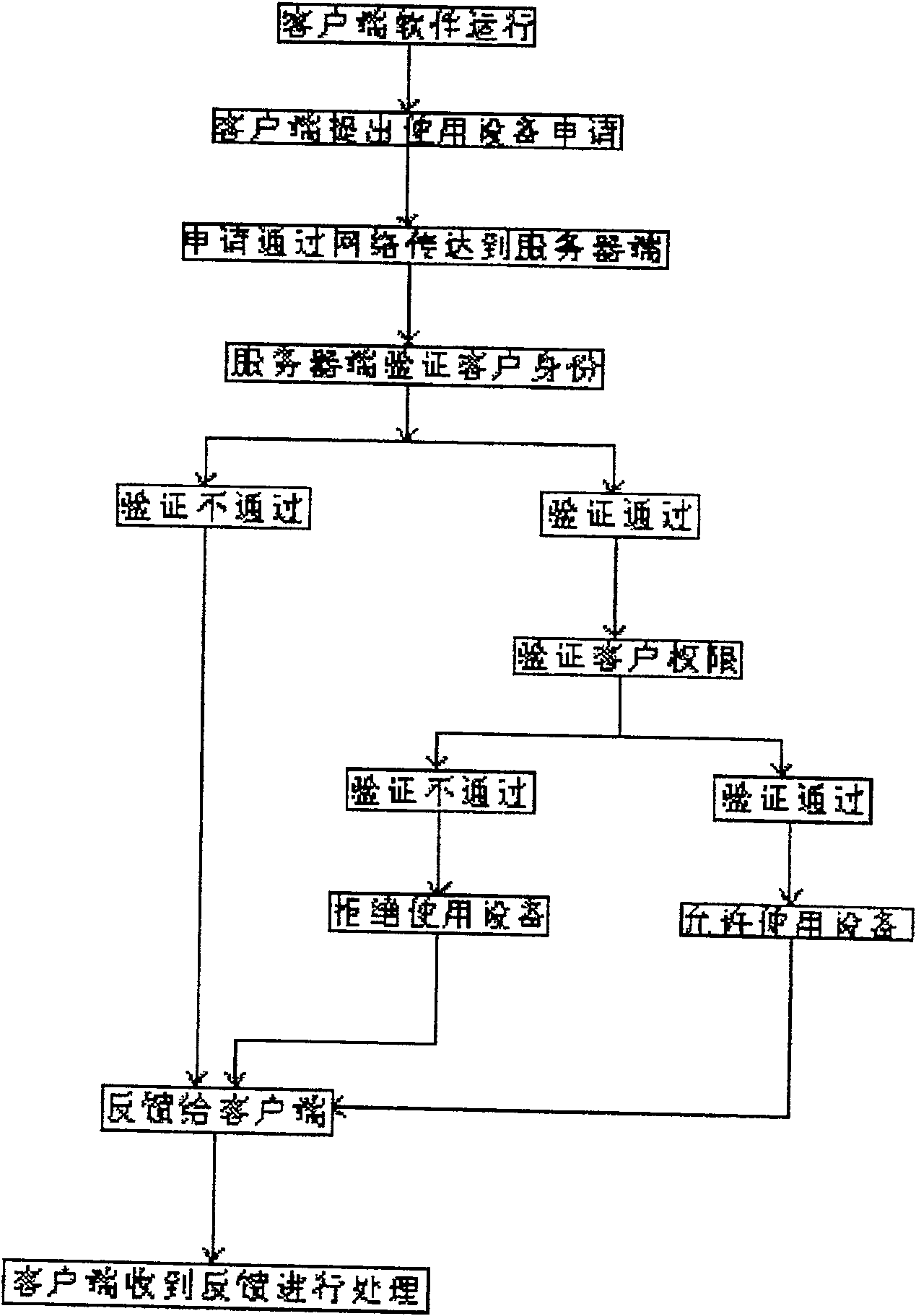
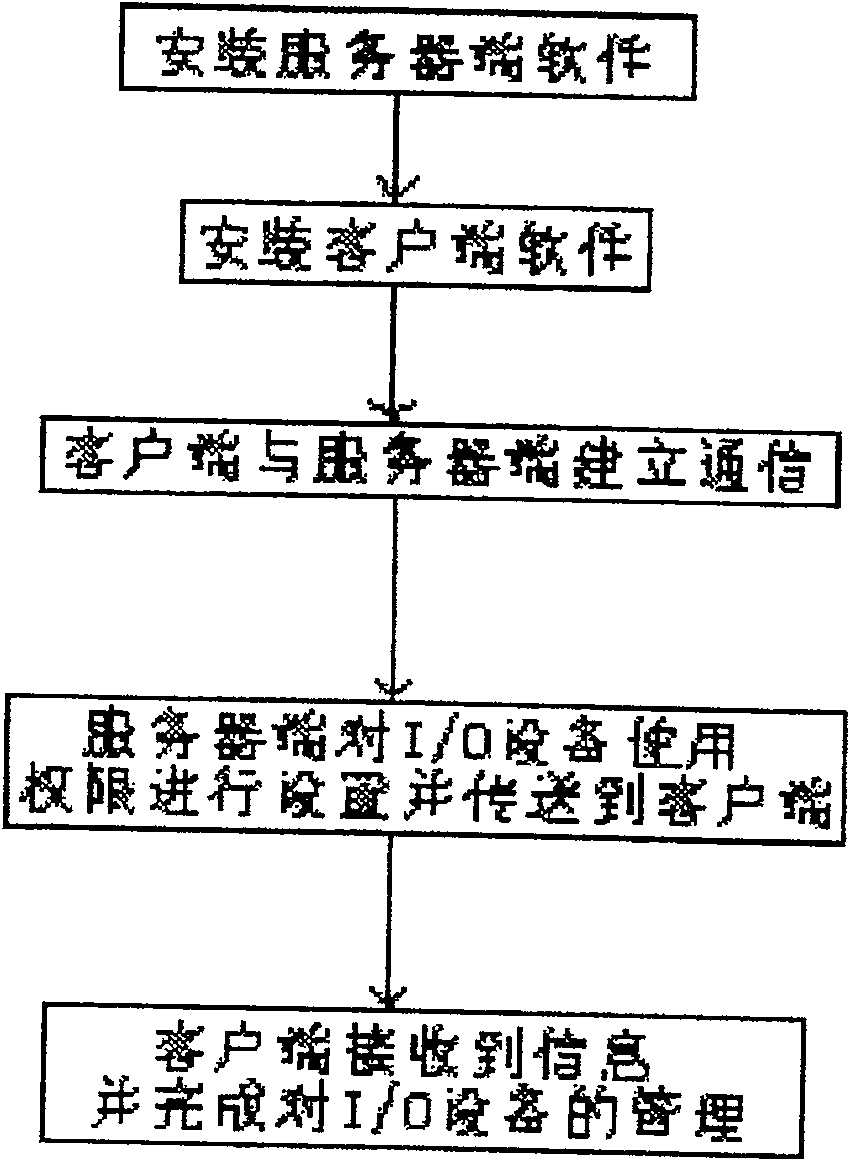
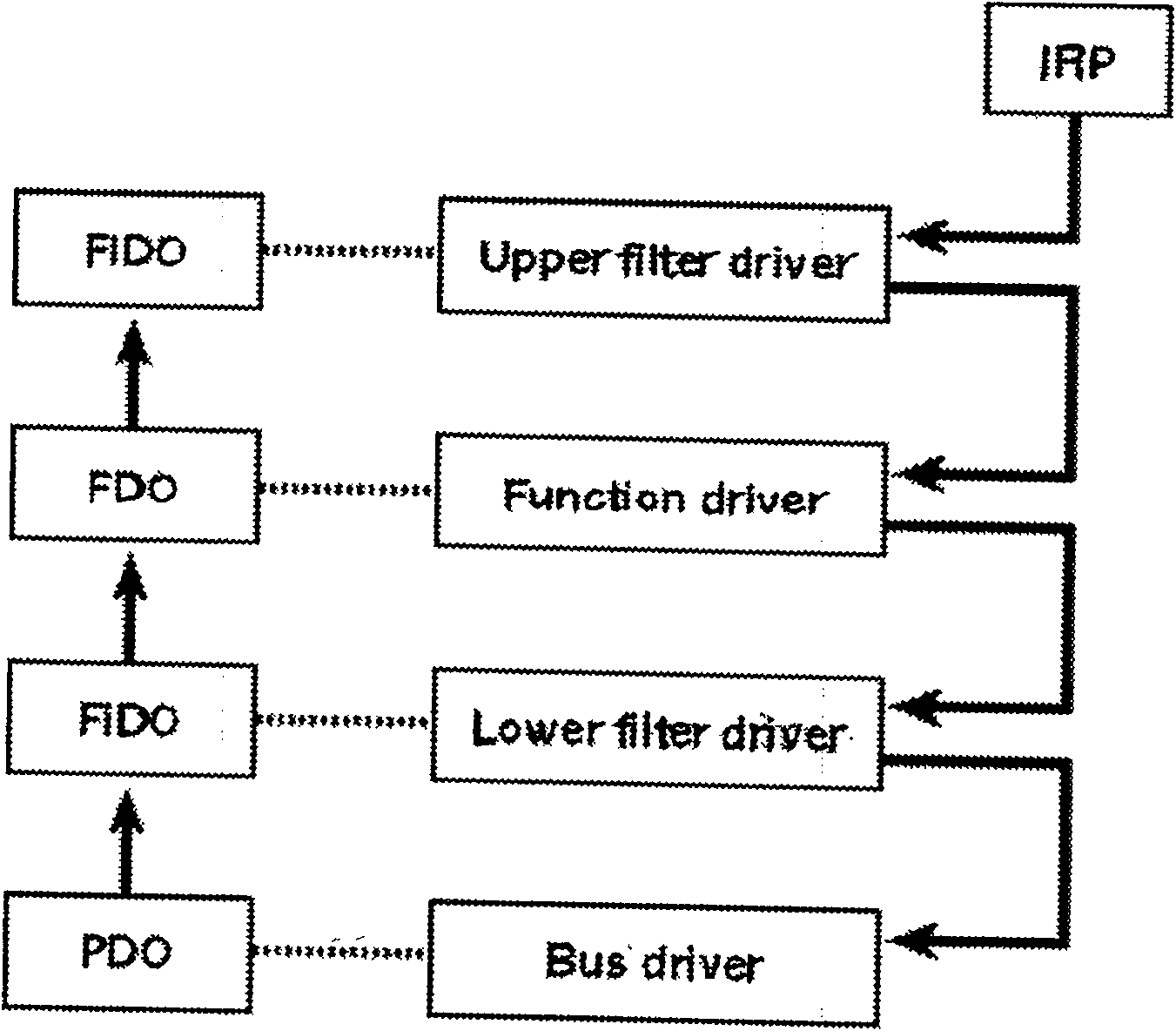
[0030] Such as figure 1 As shown, the computer I / O port control method of the present invention directly controls the I / O port resources of the computer through the management terminal software of the server and the corresponding client software, including the following steps:
[0031] Step 1, the client software runs;
[0032] Step 2, the client submits an application for using the device;
[0033] Step 3, the application is transmitted to the server through the network;
[0034] Step 4, the server verifies the identity of the client;
[0035] Step 5, if the verification fails, feed back to the client, and the client will process it after receiving the feedback; if the verification passes, execute step 6;
[0036] Step 6, verify customer authority;
[0037] Step 7, if the verification fails, refuse to use the device and give feedback to the client, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com