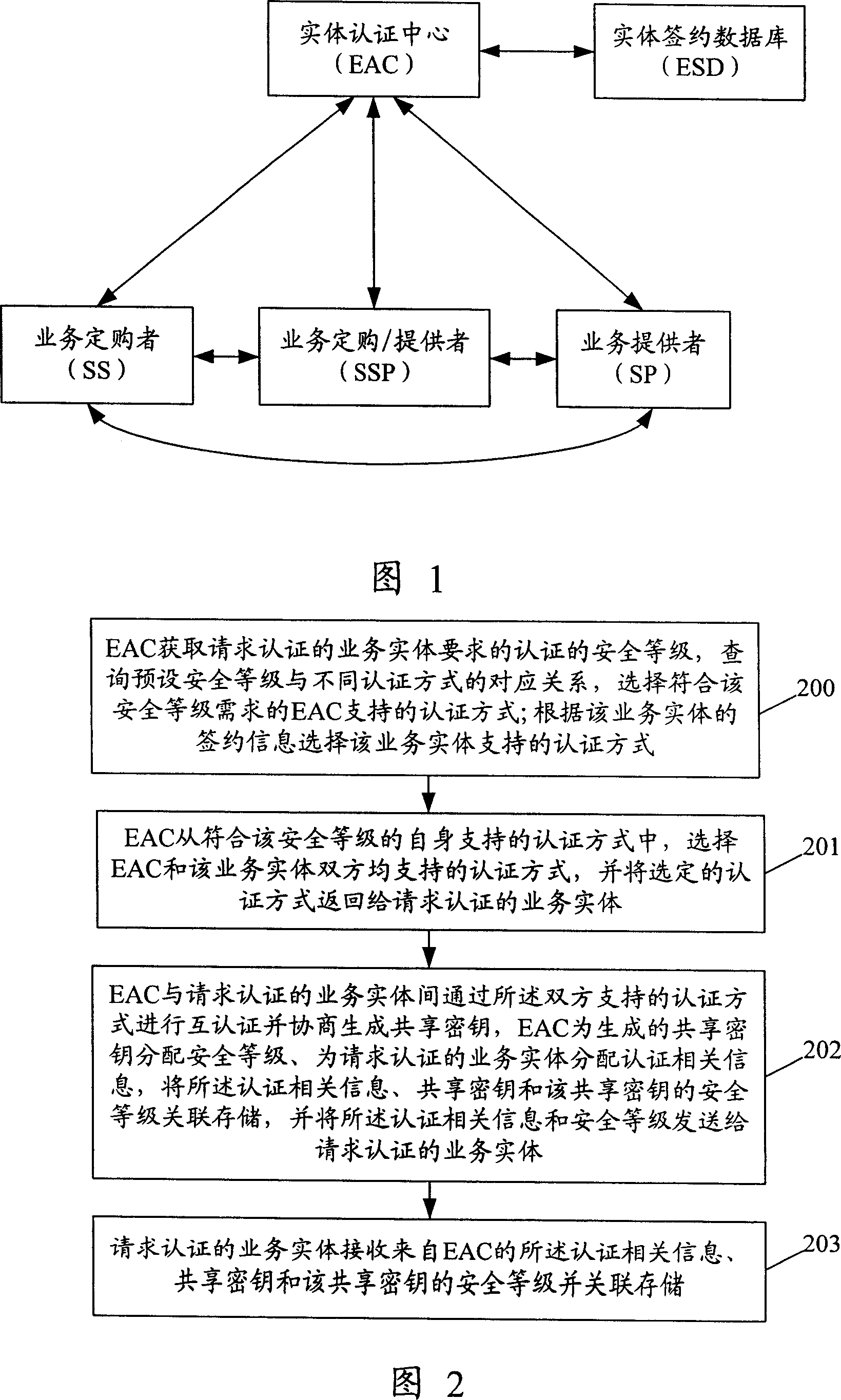
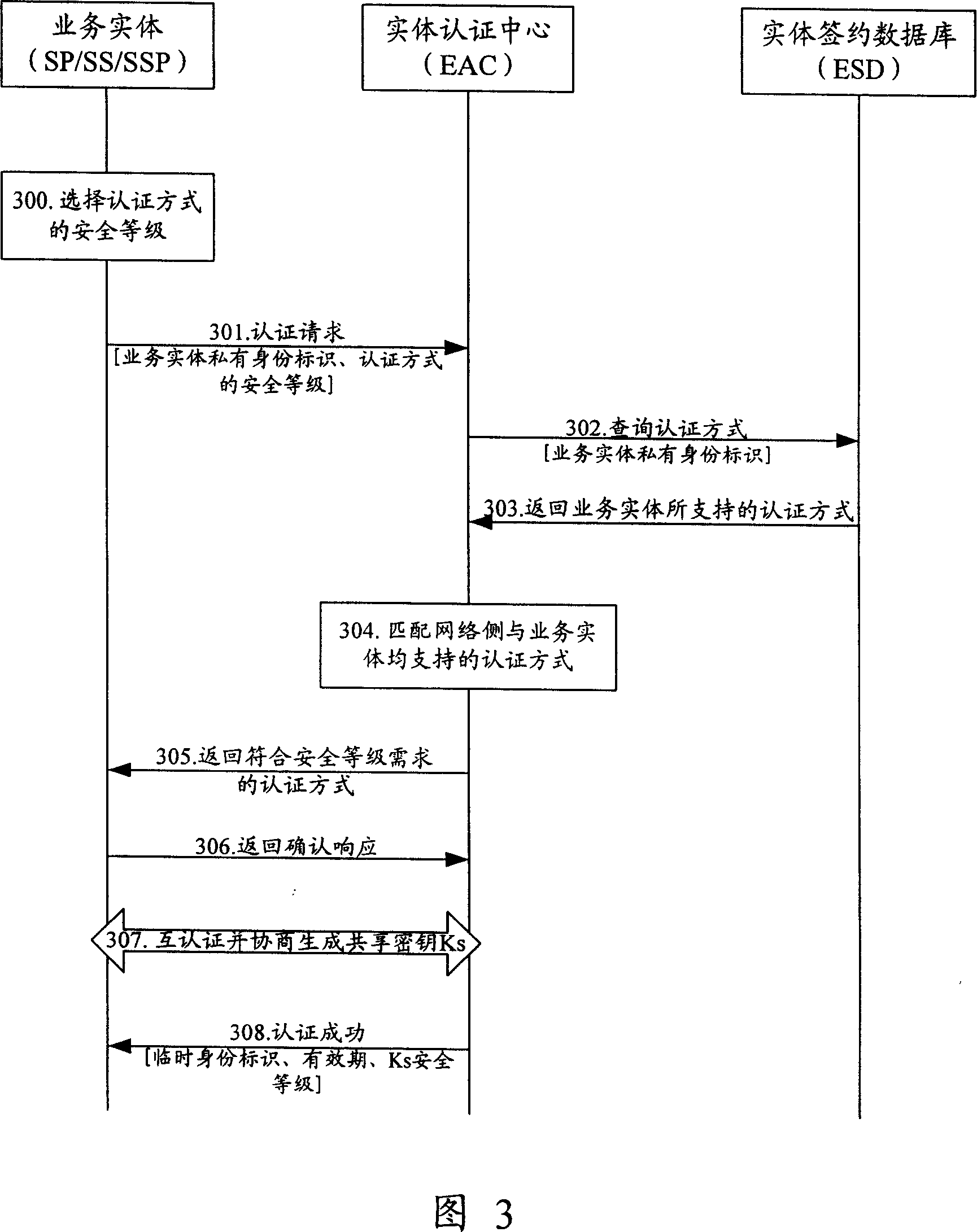
Method for implementing authentication by entity authentication centre
A technology of authentication center and authentication method, applied in user identity/authority verification and key distribution, which can solve the problems of not being able to adapt to business development, inconvenient for billing, and unable to obtain derived keys, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
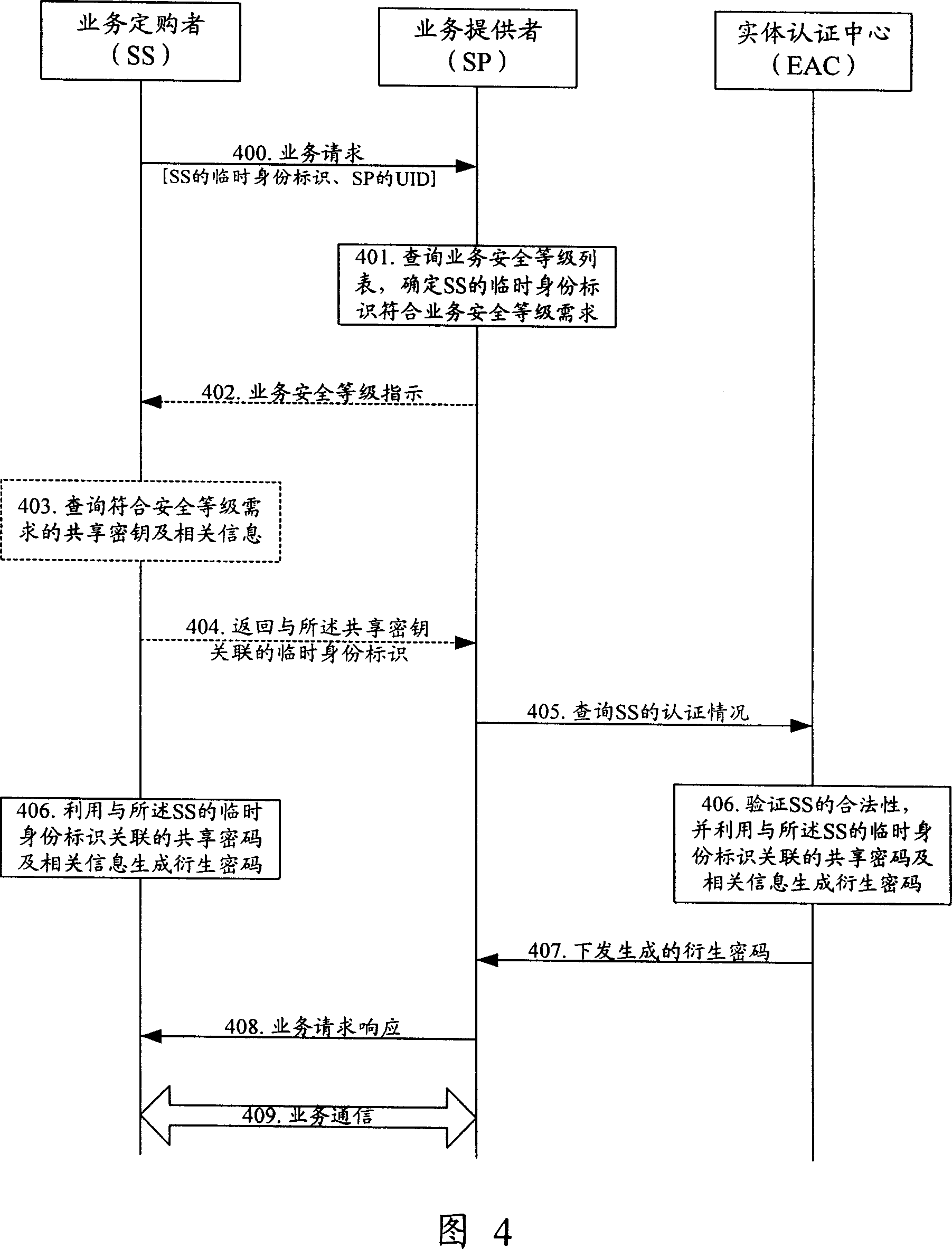
[0109]Embodiment 1, the service communication between SS and SP is realized by sending a service request message from SS to SP. FIG. 4 is a flow chart of Embodiment 1 of realizing service communication between SS and SP of the present invention, which specifically includes the following steps:
[0110] Step 400: the SS sends a service request message to the SP, and the service request message carries the temporary identity of the SS and the UID corresponding to the service applied by the SS.
[0111] In this step, assuming that the security level field storing the security level required by the SS is set in the temporary identity, the SS can search for the security level requirements corresponding to the requested service through the service security level list stored by itself, and find the security level that meets the security level. The temporary identity associated with the shared key Ks.
[0112] If the security level field is not set in the temporary identity, the secur...
Embodiment 2
[0127] Embodiment 2, the business communication between the SS and the SP is realized by sending an authentication request message to the EAC through the SS. FIG. 5 is a flow chart of the second embodiment of the business communication between the SS and the SP of the present invention, which specifically includes the following steps:
[0128] Step 500: When the SS sends an authentication request message to the EAC, the authentication request message also carries the PID of the SS and the UID corresponding to the applied service.
[0129] The authentication request message may also carry authentication capability information of the service entity, that is, supported authentication modes.
[0130] Step 501: After receiving the authentication request message, the EAC queries the preset service security level list to obtain the security level corresponding to the received UID. If the temporary identity of the SP can be obtained through the information stored in association with th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com