Method for analysing large scale network safety
A security analysis and security technology, applied in the field of network security, can solve problems that affect the normal operation of the network, security issues, and manual analysis difficulties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
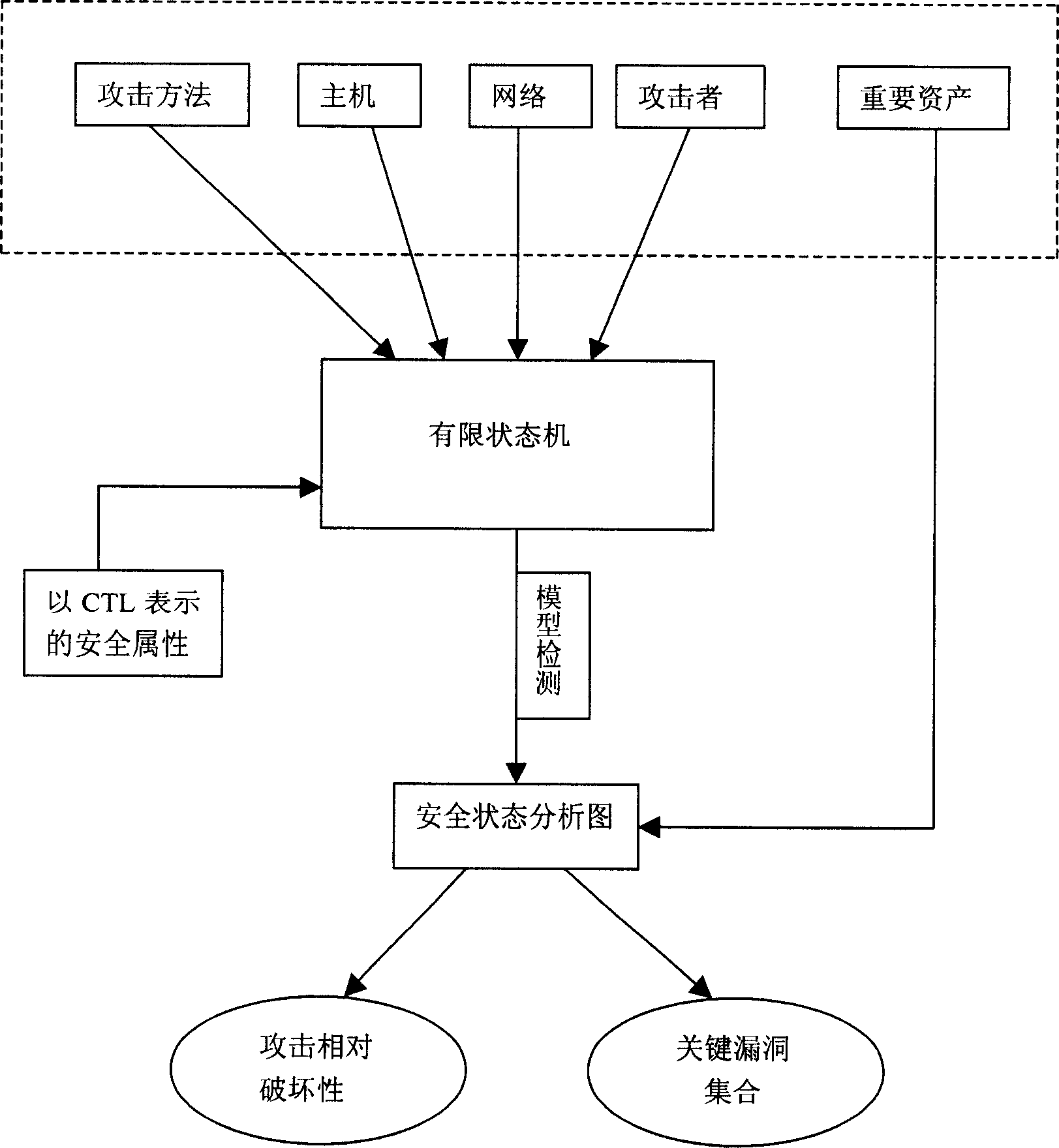
[0024] First, collect host, network, attacker, attack method and important asset information, organize and store them in the form of xml set, so as to structure the overall information of the network; then, use the above information as input to construct a finite state machine as a network model, and use The defined system security attributes are used as detection conditions, and model detection technology is used to simulate attacks on the basis of network models, and further combine the application environment to analyze and process the results of simulated attacks, and obtain targeted results such as the relative destructiveness of attacks and the set of key vulnerabilities. in conclusion.
[0025] Referring to the accompanying drawings, the detailed process is given below.
[0026] Step 1: Gather information and organize that information; information is divided into five categories: hosts, networks, attackers, attack methods, and critical assets.
[0027] 1. The host (Hos...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com