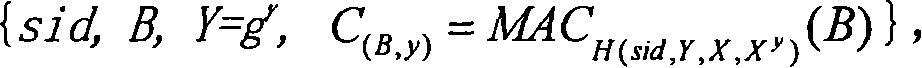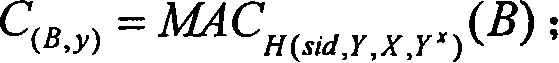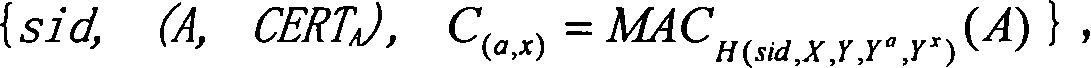Repudiation Internet key exchange protocol
A key exchange protocol and Internet technology, which is applied in the field of key exchange protocols, can solve the problems that user identities cannot be known or determined, danger, Stinson-Wu protocol cannot be repudiated, etc., to achieve privacy protection and complete security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0059] When the protocol-1 is implemented in the IKEv2 main mode, the session identifier sid is formed by the combined connection of two random strings sent by the two parties running the protocol before the protocol-1 runs. Thus, the specific implementation of the invention protocol in IKEv2 main mode runs six rounds. Note that the current IKEv2 standard also runs six rounds in main mode.
[0060] First round, from A to B: {R A}, where R A is a 32-bit random 0-1 string. B verifies R A The effectiveness of (ie: R A is a 32-bit 0-1 string).
[0061] Second round, from B to A: {R B},R B Yes with R A A random 0-1 string of the same length. B sets sid to R A ||R B (i.e. R A with R B Merge connection); A receives R B post-validation R B The effectiveness of (ie: R B is a 32-bit 0-1 string), and set the sid to R A ||R B .
[0062] Third round, from A to B: {R A ||R B , X=g x (mod p)}, where x is from Z q randomly selected from. X is called A's DH key componen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com