Method for implementing reinforced authentication by binding access account number and business account number
A technology of account binding and access mode, applied in the field of user authentication and authentication technology, it can solve the problems of one-number access, multi-machine sharing, easy account theft, etc., and achieve the effect of enhancing security and reducing operating costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The specific implementation of the technical solution of the present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
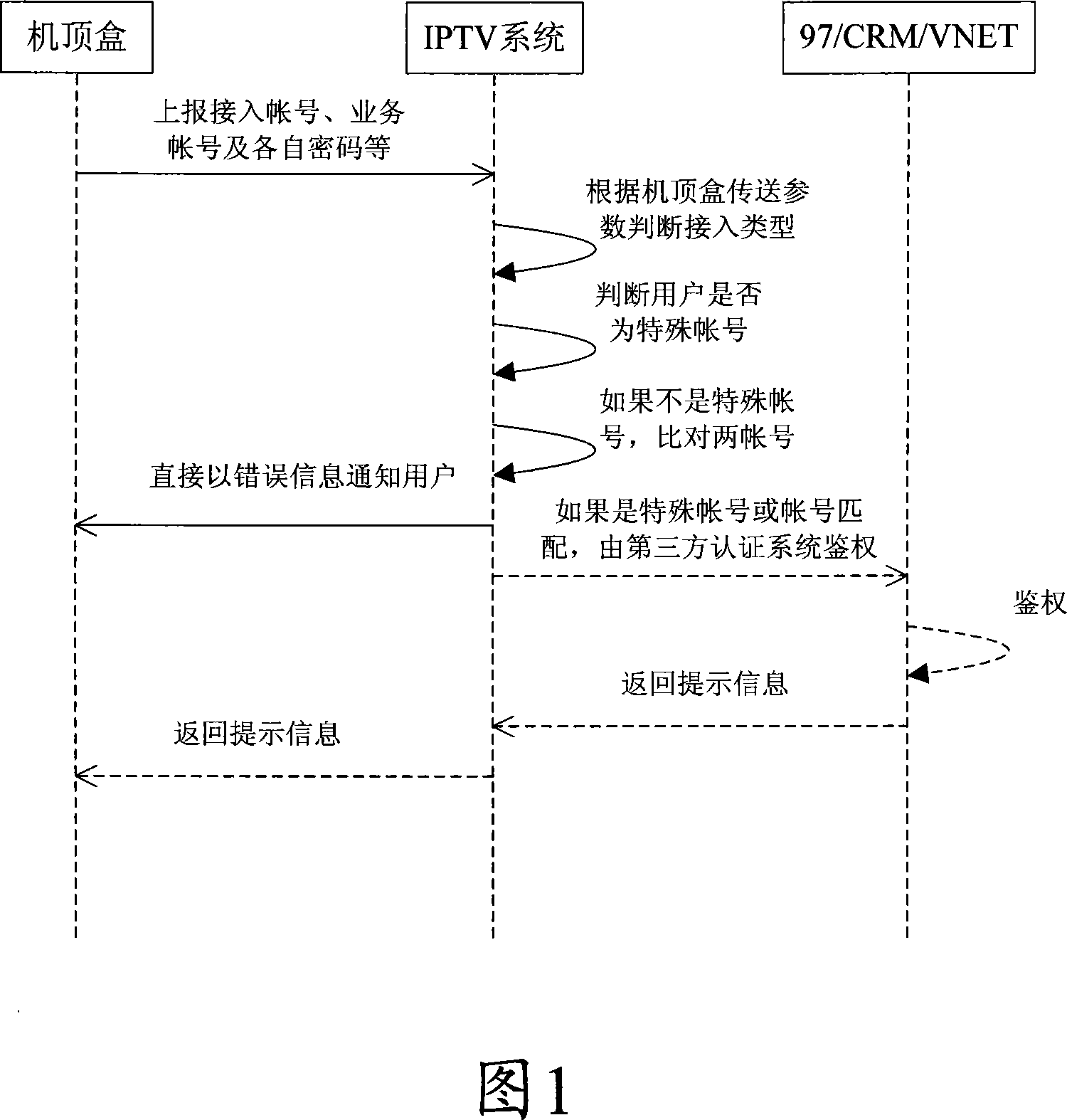
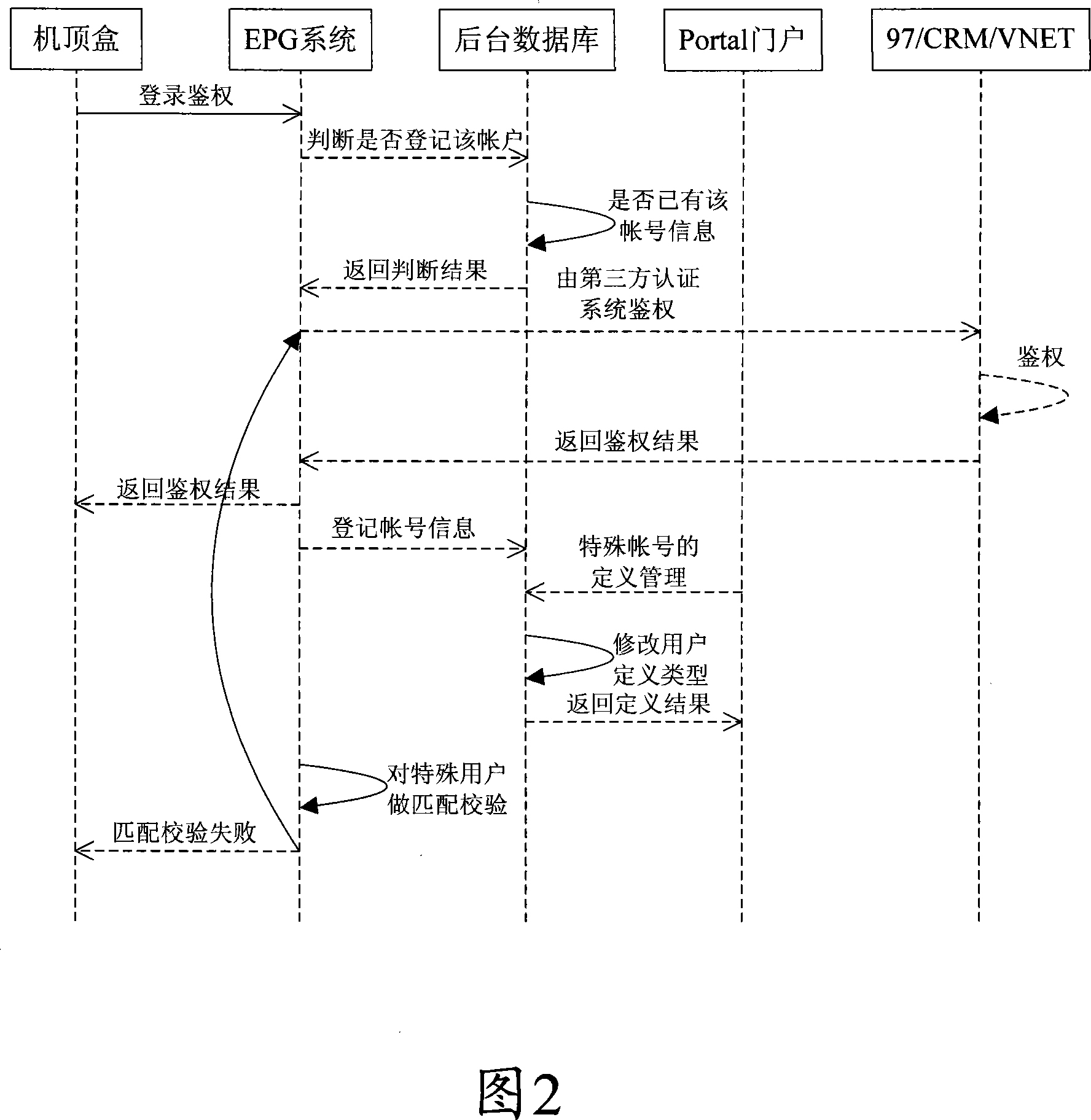
[0043] In order to prevent IPTV service accounts from being stolen; in order to prevent one service account from being shared by multiple addresses and set-top boxes; in order to avoid that service accounts marked as special users still need to be compared. It is proposed to increase the binding comparison process, and realize the solution of security authentication and authentication according to the comparison of the binding account when the user accesses the authentication.
[0044] When the user logs in and authenticates, the user's broadband user is compared with the business account, and only the same name or match is sent to the background or a third-party system for business authentication, and the uniqueness of the business account login is guaranteed. At the same time,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com