Method for access to control address through media and learning control equipment access to Ethernet
A technology for controlling equipment and Ethernet, applied in the field of Ethernet communication, it can solve the problems of complex configuration, adding new equipment and management complexity, and high cost, and achieve the effect of preventing private access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
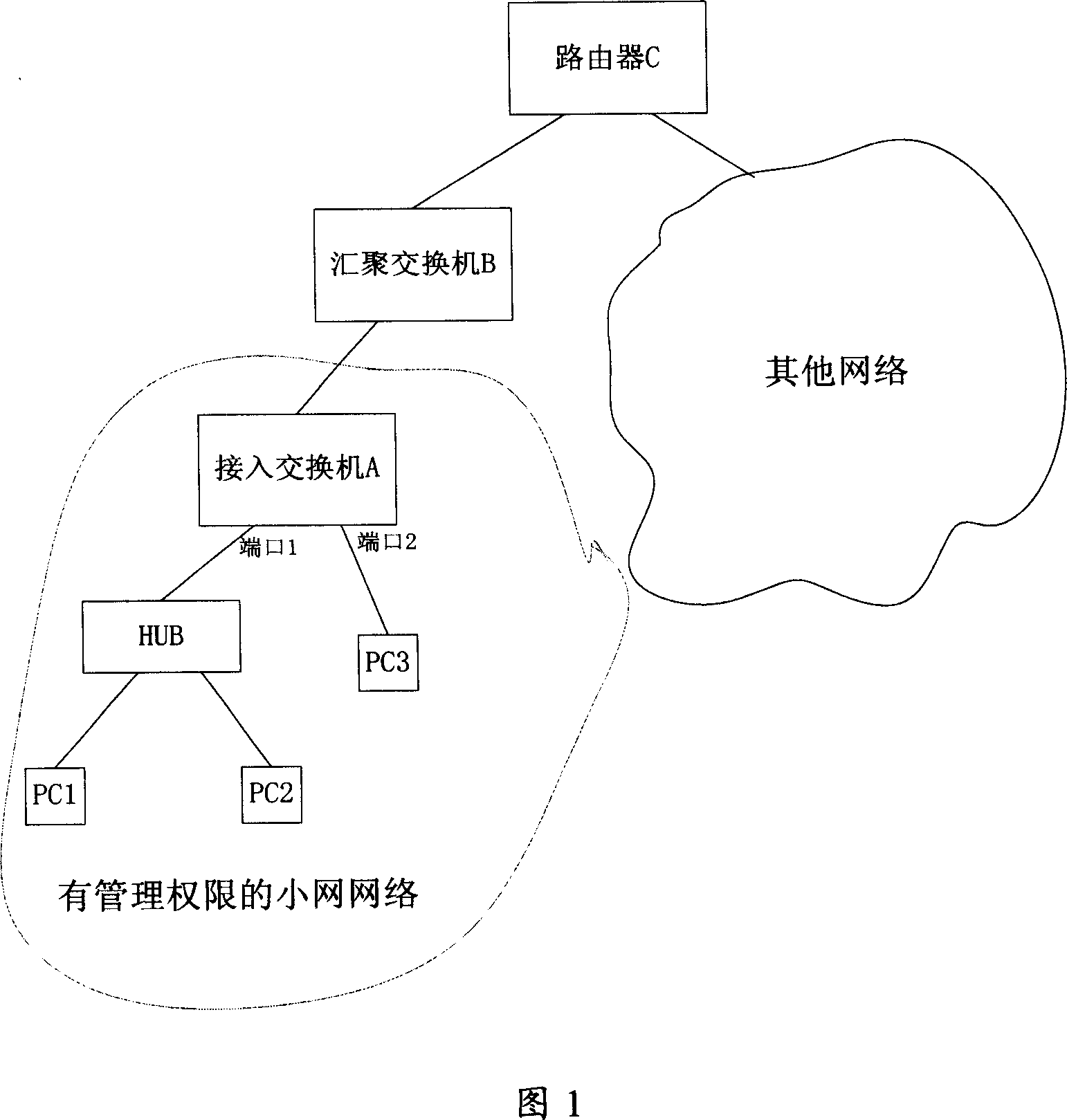
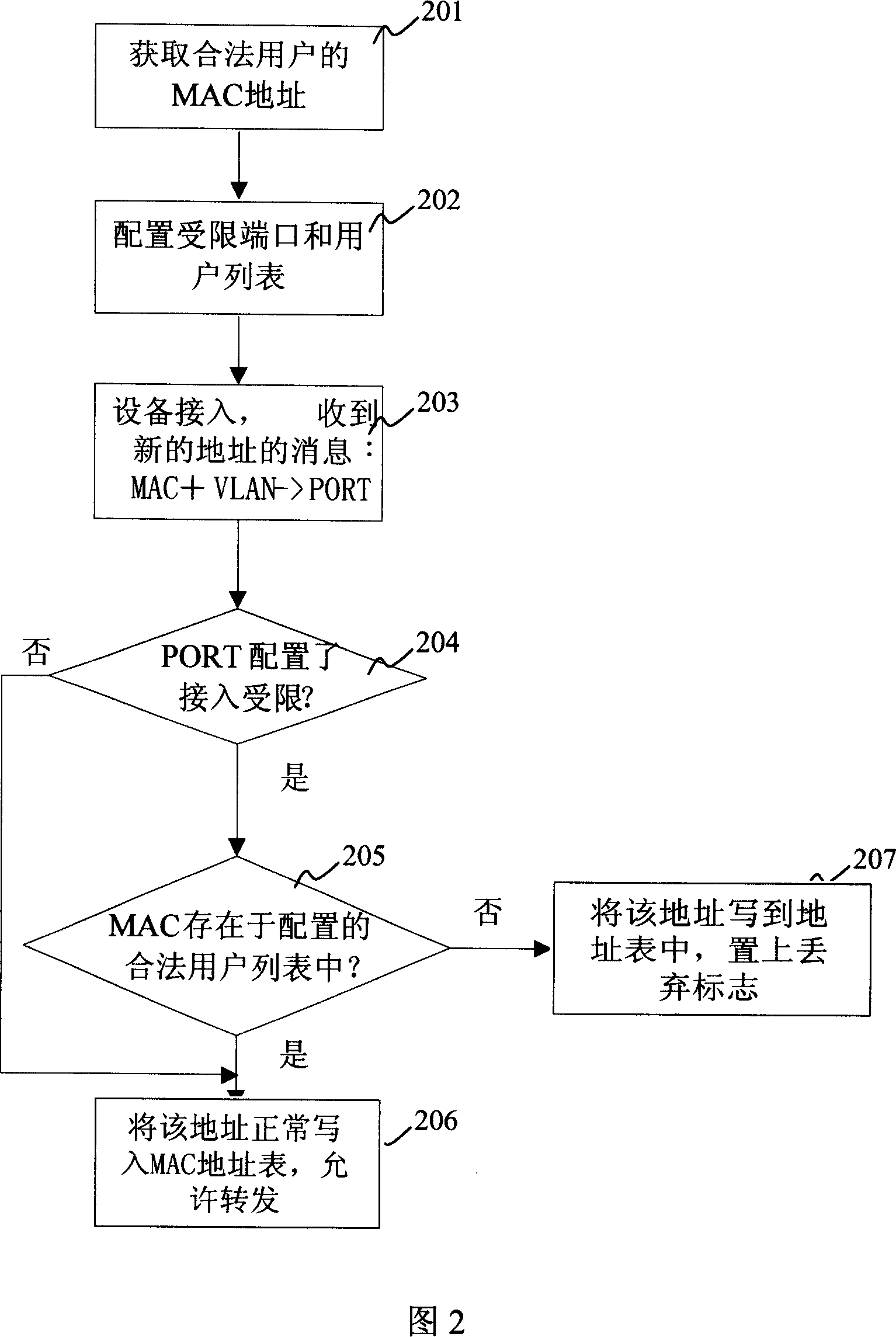
[0018] The invention controls the communication of the fixed legal user under a certain port of the access switch by controlling the formation of the hardware MAC address table.
[0019] After the Ethernet network is established, there may be one or several network devices under a certain port of the user access switch closest to the user, and these network devices are approved by the administrator of this switch.
[0020] The processing method of controlling access through MAC address learning in the present invention will be described below in conjunction with the accompanying drawings.
[0021] As shown in Figure 1, it is a schematic diagram of a simple network. In the figure, it shows a small network with autonomous management rights. The administrator needs to control the legal access of users in this area, but there are no other networks outside the dotted line. administrative privileges. There are two legal users PC1 and PC2 under the hub HUB of port 1 of switch A, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com