An encryption method based on H.264 video stream
An encryption method and video streaming technology, applied in the fields of digital video signal modification, television, analog security/charging system, etc., can solve the problems of great real-time influence, difficult real-time encoding, and changing statistical characteristics.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention utilizes the characteristics of 4*4 DCT transformation in H.264, and provides a new DCLSA algorithm by constructing a layered model of DCT coefficients.
[0046] An encryption method based on H.264 video stream:
[0047] 1. DCT coefficient hierarchical model
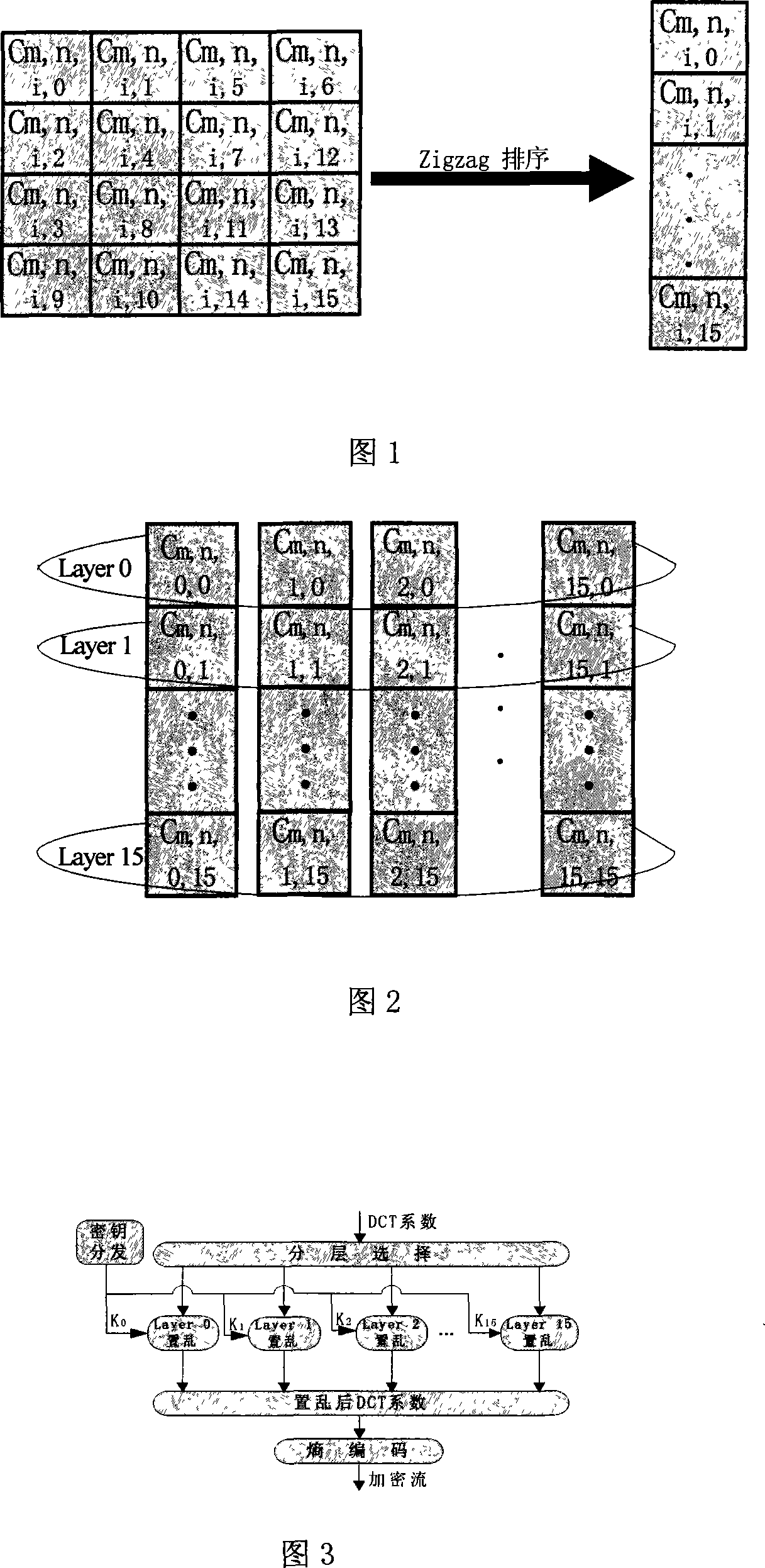
[0048] Before the model is established, during H.264 encoding, a frame of image is first selected to be divided into m (m≥1) slices, and each slice contains n (n≥1) macroblocks. Specifically, each macroblock is divided into 16 sub-blocks with 4×4 as the basic unit: Z m,n,0 ,Z m,n,1 ,…,Z m,n,15 , each sub-block contains 16 DCT coefficients, namely Z m,n,i ={C m,n,i,0 , C m,n,i,1 ,...,C m,n,i,15}(m≥1, n≥1, 0≤i≤15).
[0049] Step 1: Each 4×4 sub-block Z in the same macro block m,n,i The two-dimensional coefficient matrix contained in (m≥1, n≥1, 0≤i≤15) is mapped into a one-dimensional coefficient matrix, and the mapping function is Zigzag sorting, as shown in Figure 1.
[0050] Step 2:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com