Fixed network access into IMS bidirectional authentication and key distribution method
A technology of two-way authentication and fixed network, applied in the field of authentication, can solve the problems of lowering capability requirements and the inability to fully satisfy the capability of fixed network terminals, and achieve the effect of lowering requirements and ensuring confidentiality and integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
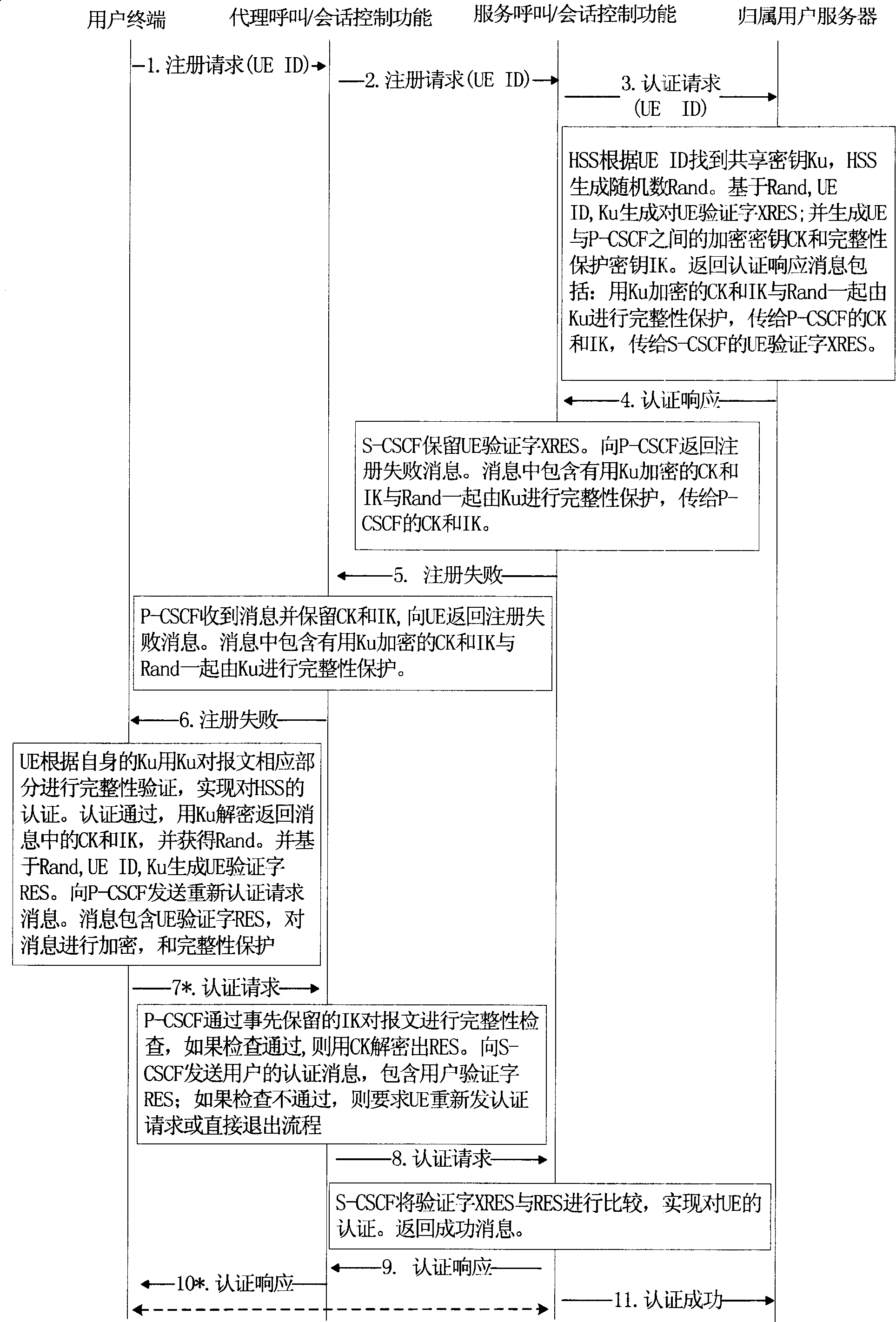
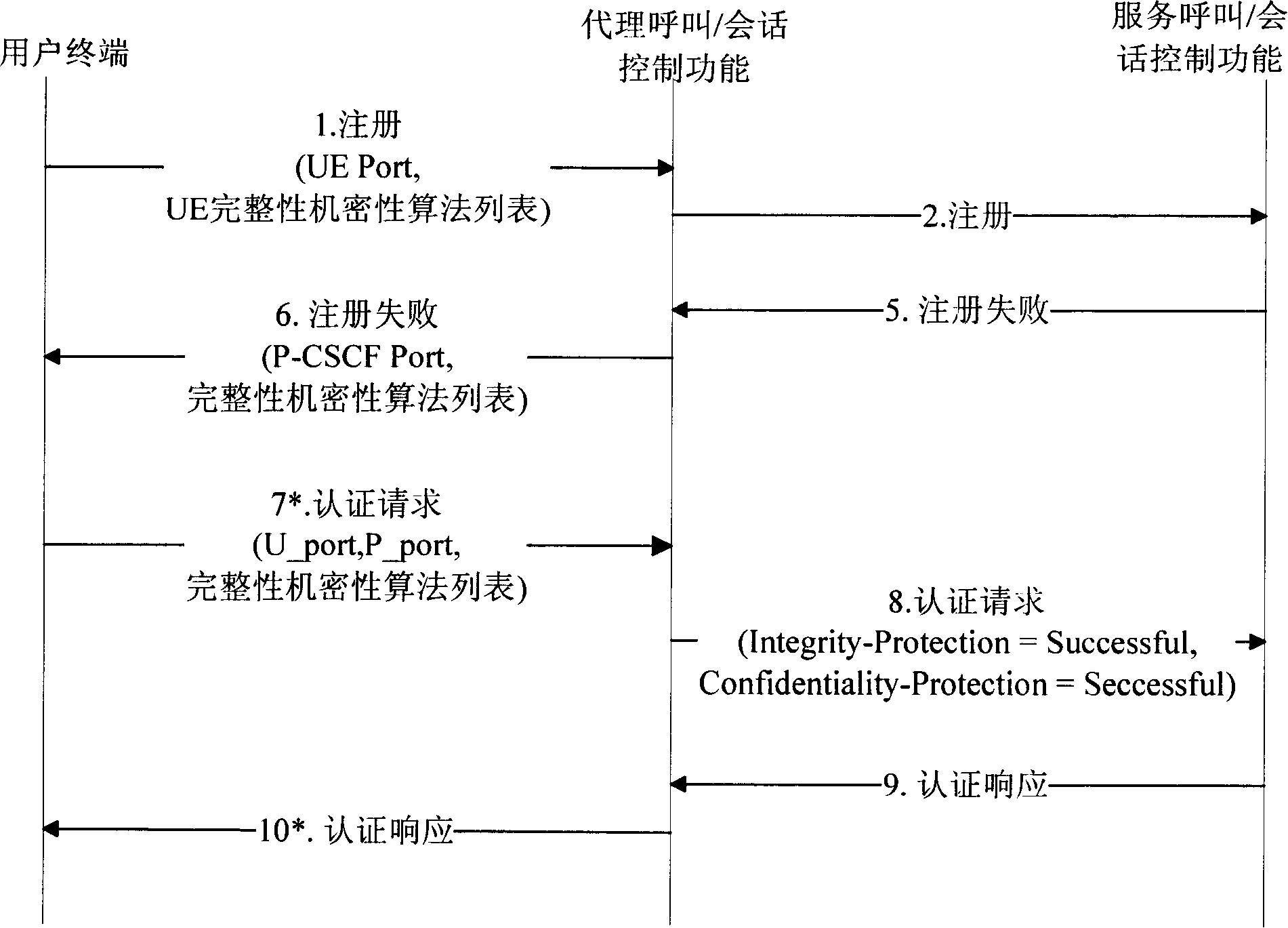
[0043] The fixed network access IMS two-way authentication and key distribution method of the present invention realizes the two-way authentication between the fixed network user terminal and the IMS network side, completes key distribution and security capability negotiation, and ensures communication between broadband fixed users and P-CSCF confidentiality and integrity.
[0044] The entities involved in the present invention include fixed network user terminals, P-CSCF, S-CSCF and HSS in the IMS domain. (where CSCF is a call / session control function defined in 3GPP R5).
[0045] A user terminal (UE) is a terminal that accesses the IMS system and enjoys IMS services, and there is a shared key between the user terminal and the IMS network side.
[0046] P-CSCF is a proxy CSCF, and is the entrance of IMS network and external network.
[0047] The S-CSCF is the serving CSCF, which completes the session control function of the UE.
[0048] HSS is the home user server, which c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com