Flow monitoring method and flow monitoring equipment
A technology of equipment and traffic, applied in the field of network communication, can solve the problems of idle bandwidth not being used by other users, waste of bandwidth resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
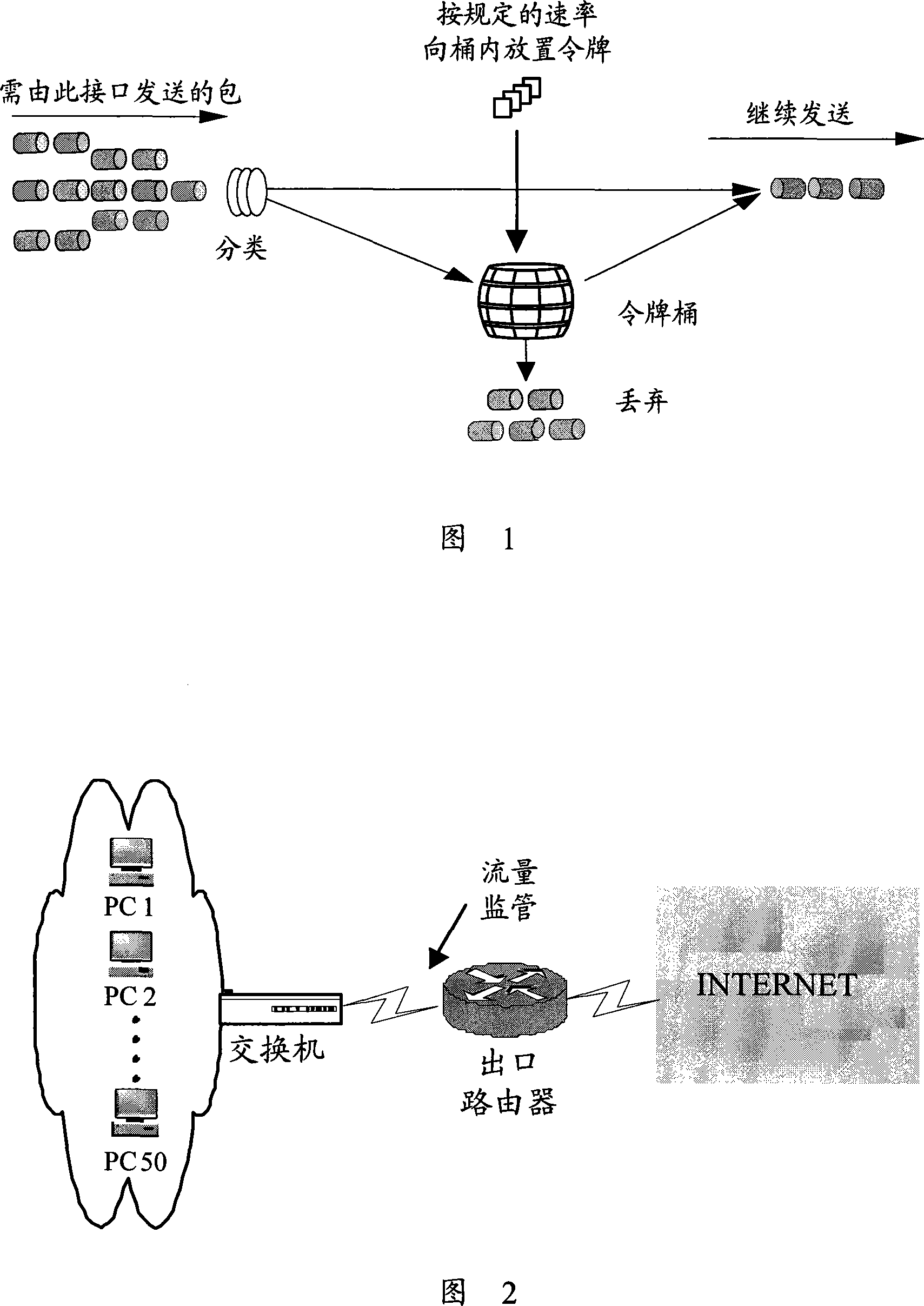
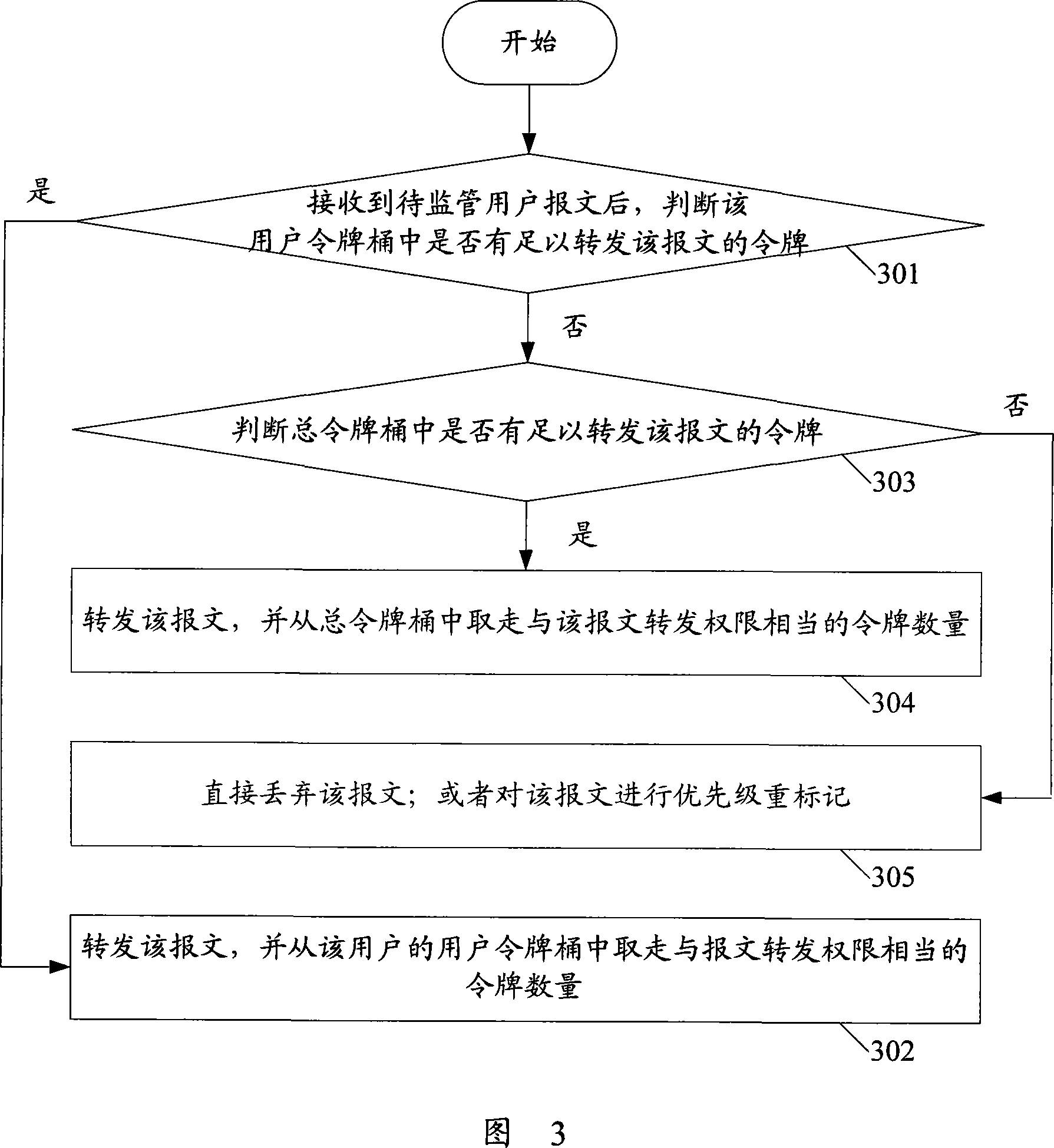
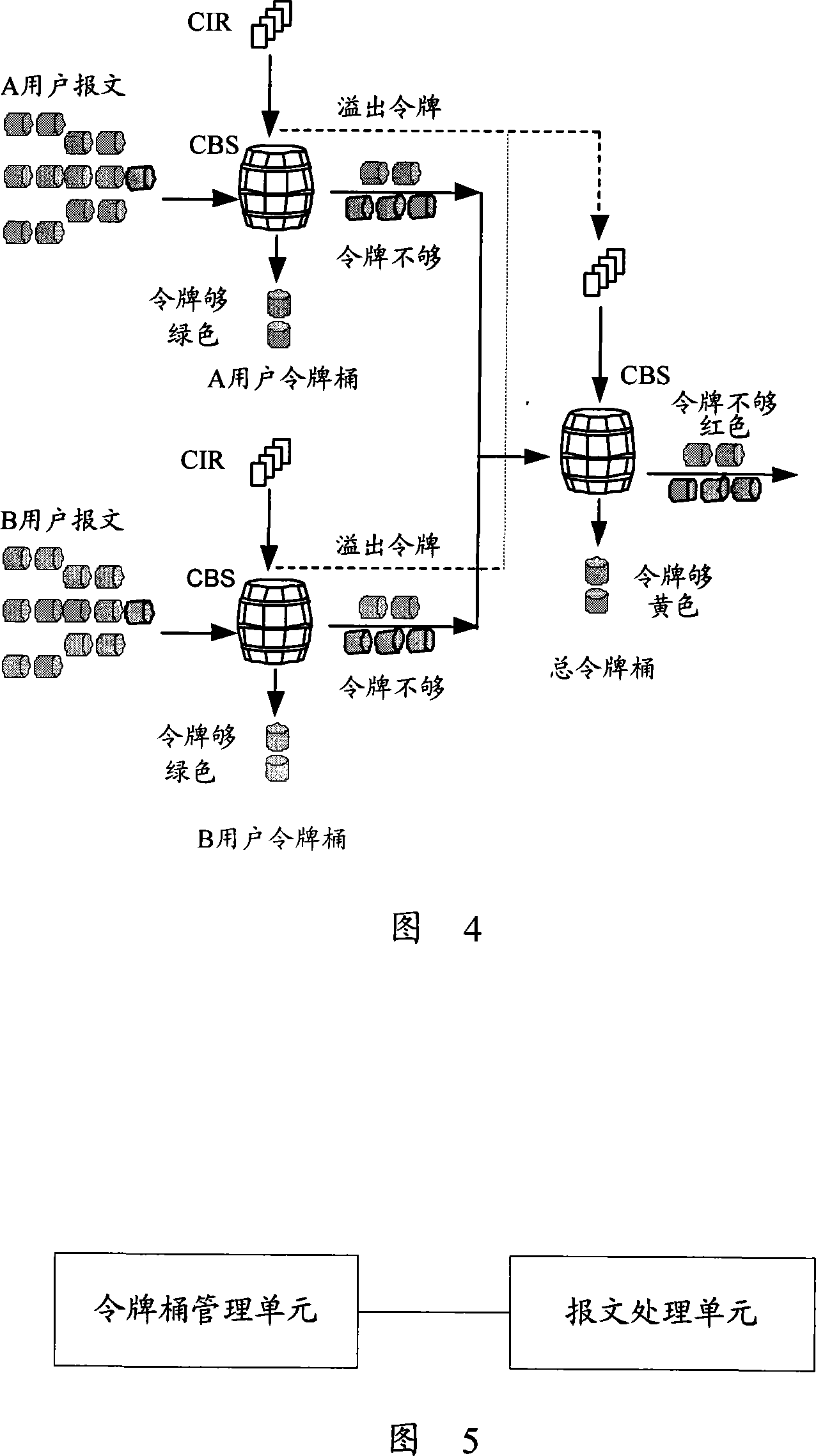
[0037] In order to overcome the problem of low bandwidth resource utilization in the prior art, the present invention proposes a flow monitoring method. In this method, two levels of token buckets need to be set: 1. User token buckets, which correspond to users to be supervised one-to-one, and are used to limit the traffic of each user to be supervised; 2. Total token buckets, used to limit all users of the total flow. Among them, the capacities of the user token bucket and the total token bucket can be set according to actual needs.
[0038] Usually, the configuration parameters of the token bucket include: Committed Information Rate (CIR) and Committed Burst Size (CBS), CIR indicates the rate at which tokens are placed in the bucket, and CBS indicate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com