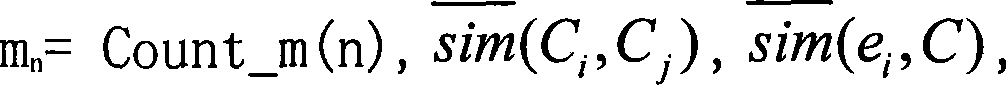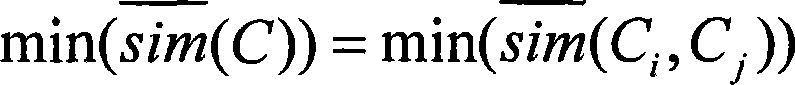Network exception detection method based on quick clustering algorithm
A clustering algorithm and network anomaly technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems that it is difficult to meet the needs of effective extraction of security information, and the intrusion mode cannot be extracted.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be described in detail below with reference to the drawings and embodiments.
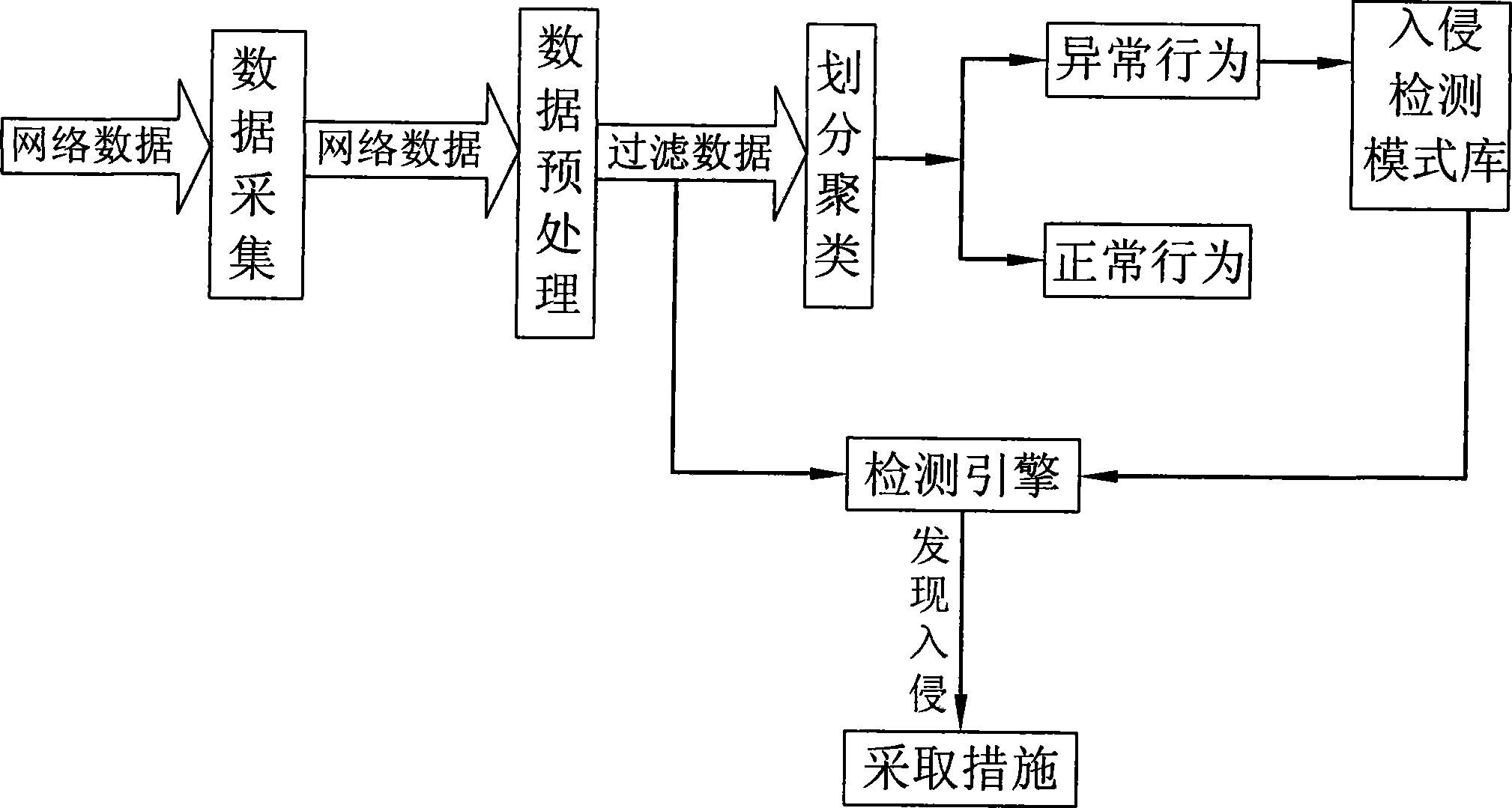
[0053] A method for network anomaly detection based on a fast clustering algorithm, which is implemented through the following steps:
[0054] Step 1: Grab the TCP / IP traffic data packets on the network in a bypass listening mode, and collect the data;
[0055] Step 2: Perform data preprocessing, decompose the attributes of the captured data packets, and send the filtered data to Step 3 and Step 5 at the same time;
[0056] Step 3: Use the fast clustering algorithm to cluster the filtered data, which includes
[0057] Algorithm: fast clustering algorithm for mixed type data;
[0058] Input: data set E, sampling times n;
[0059] output: each cluster;
[0060] Its operation process is:
[0061] (1)Search_m(E,n); / / Get the initial cluster center m1, m2
[0062] (2) Repeat
[0063] (3) Read new record e i ;
[0064] (4) calculation m ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com