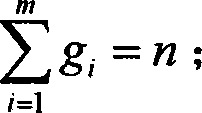Peer network secure routing method based on multi-dimension distributed hash table
A technology of distributed hash table and peer-to-peer network, which is applied in the field of network security to achieve the effect of high routing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
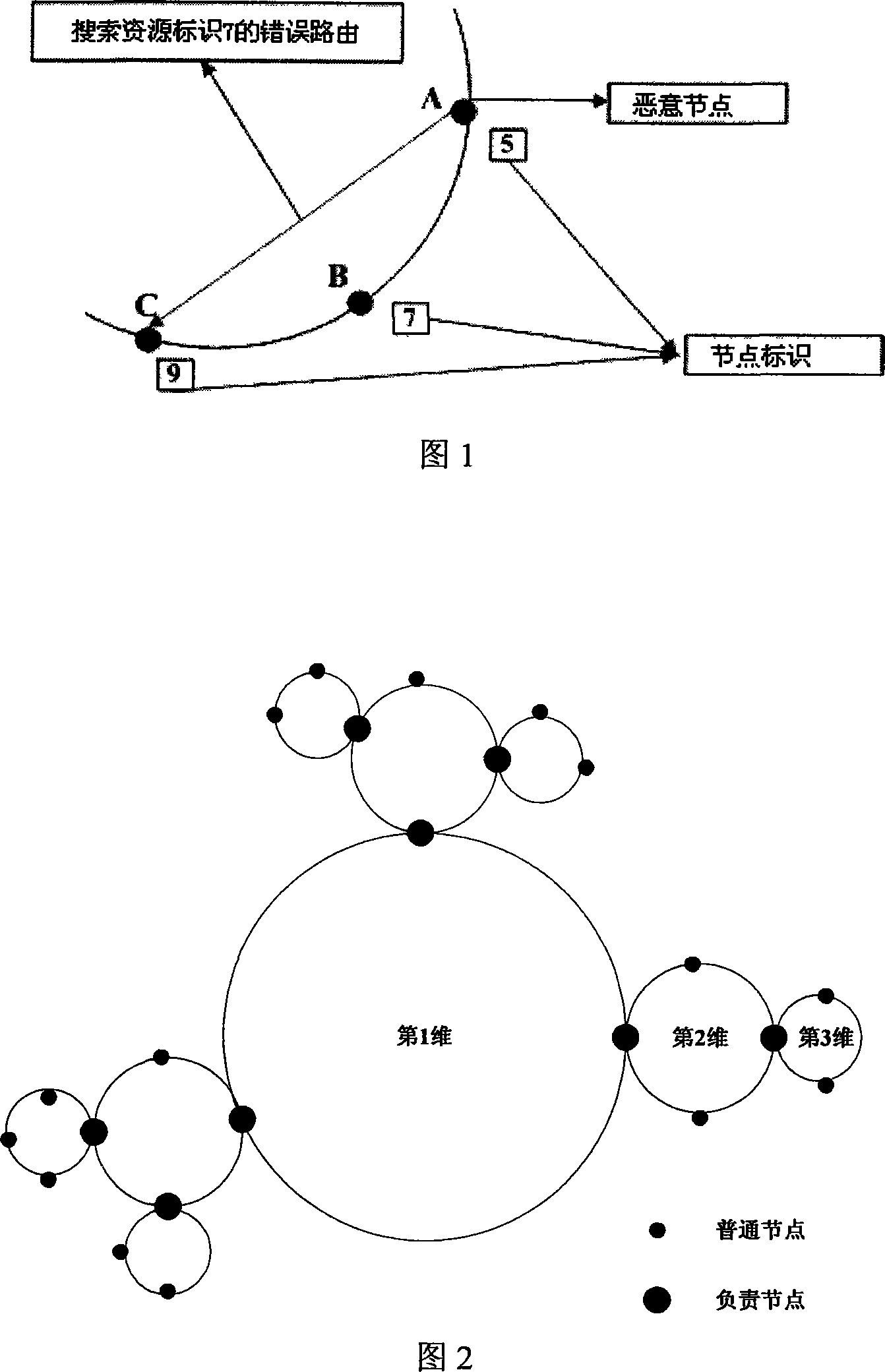
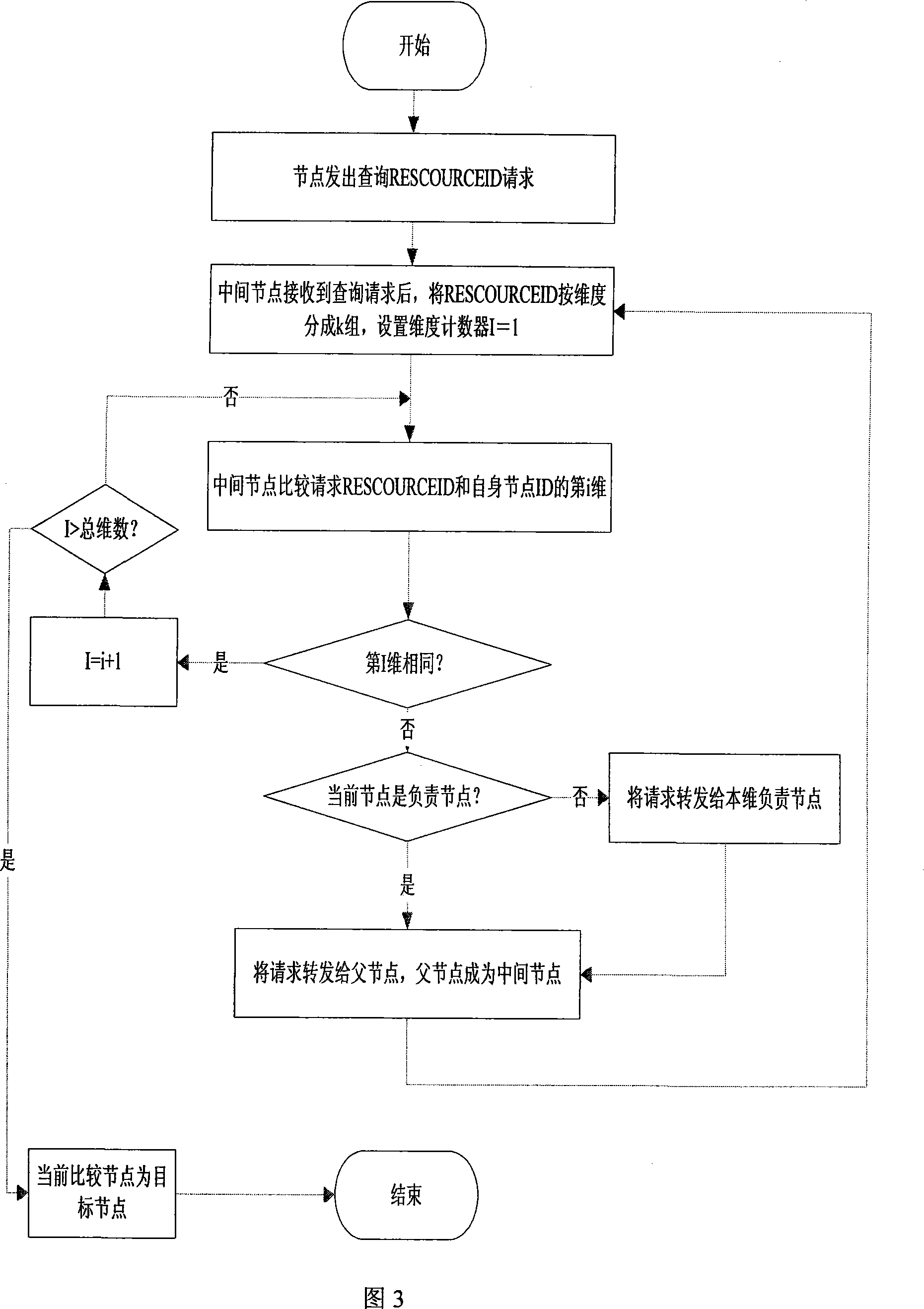
[0056] The method of the present invention is divided into three parts: the design of the multi-dimensional distributed hash table structure, routing forwarding, and malicious node identification method; the multi-dimensional distributed hash table divides the identification of the node into different dimensions and the responsibility of each dimension. The node organizes the nodes of the entire P2P application into a tree-like structure, thus providing the basis for safe routing forwarding and identification of malicious nodes; routing forwarding is based on the multi-dimensional DHT structure, and the routing forwarding process is converted into each target node The process of gradually approaching each dimension can achieve higher routing efficiency; the identification of malicious nodes is based on the distributed hash table structure and routing forwarding, and through the dimension information saved by nodes of the same dimension, various types of malicious nodes can be id...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com