Method, unit and system for preventing address resolution protocol flux attack
A traffic attack and processing unit technology, applied in transmission systems, digital transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
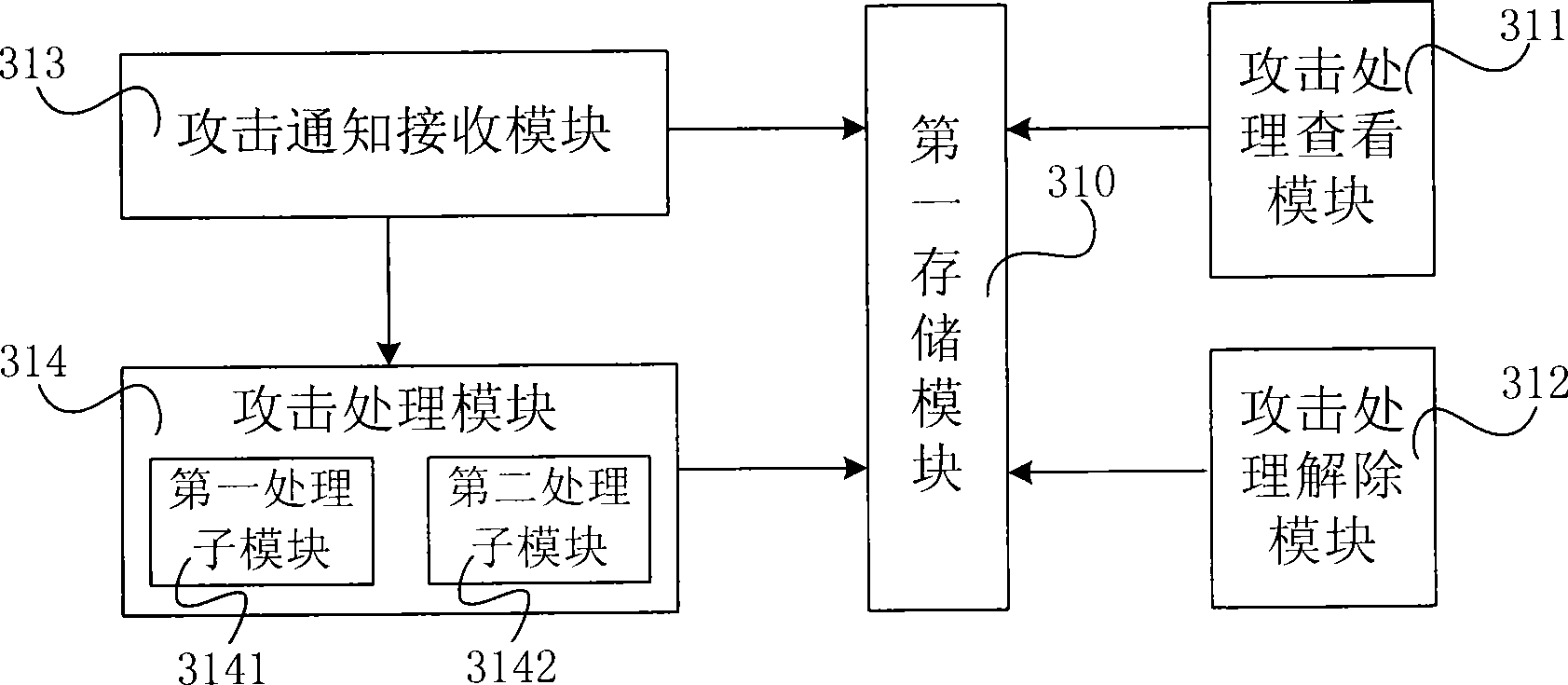
Image
Examples
Embodiment 1
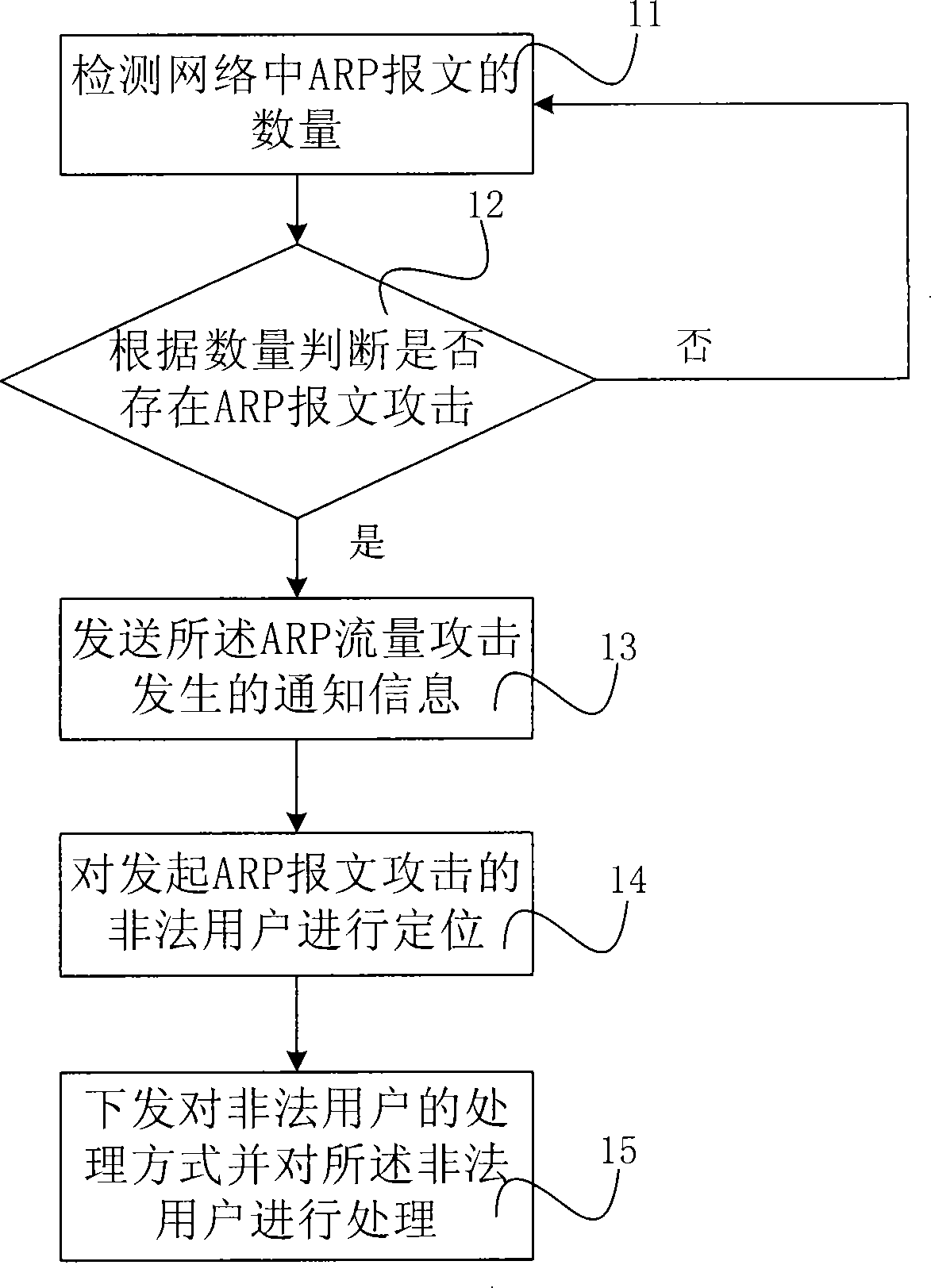
[0031] like figure 1 Shown is the flow chart of embodiment one of the method for preventing ARP flow attack of the present invention, and this method comprises the following steps:
[0032] Step 11, detecting the number of ARP packets with the same characteristics in the network;
[0033] Under normal circumstances, the process of using the ARP protocol to make an ARP request when sending a message is completed by the operating system, so each host usually only needs to send an ARP request message to the gateway device to realize the IP address and MAC address. parsing process. Based on this principle, the gateway device can determine whether an ARP traffic attack has occurred in the current network by detecting the number of ARP packets with the same characteristics in the network within a certain time range.
[0034] Step 12, judging whether the quantity exceeds a preset threshold, if it exceeds the threshold, execute step 13, if not, execute step 11;
[0035] Step 13, s...
Embodiment 2
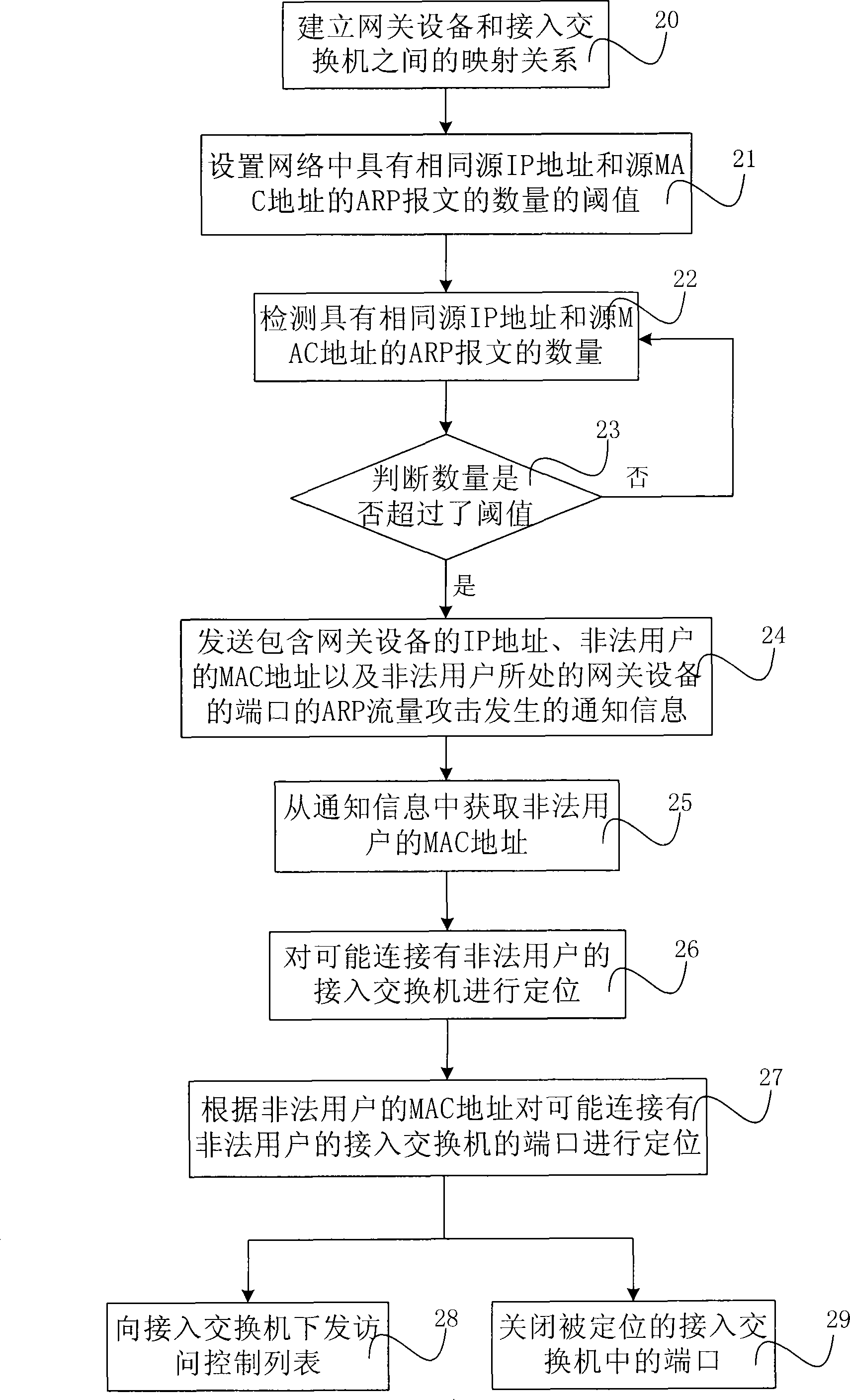
[0044] like figure 2 Shown is the flow chart of Embodiment 2 of the method for preventing ARP traffic attacks of the present invention, including
[0045] Step 20, establishing a mapping relationship between the gateway device and the access switch;
[0046] The mapping relationship represents the corresponding relationship between the port of the gateway device and the access switch existing under the port. The way to establish the mapping relationship between the gateway device and the access switch can be that the access switch uses its own MAC address to poll all gateway devices through the port and MAC address mapping table (802.1d table) stored in the standard gateway device, and from the gateway Obtain on the device which port the access switch itself is under the gateway device; you can also establish a corresponding relationship between the access switch IP-gateway device IP-corresponding gateway device port through the gateway information, switch information and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com