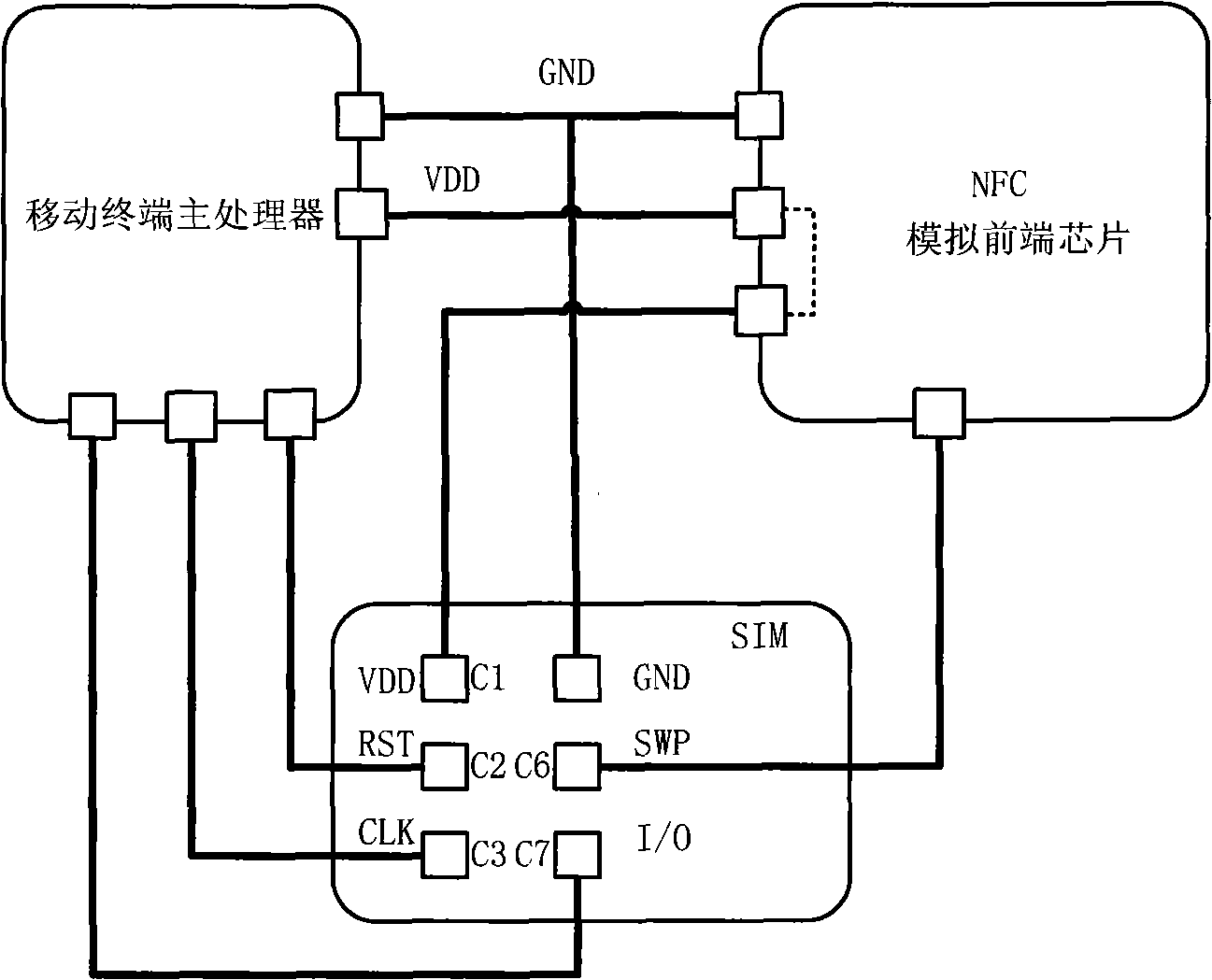
Method realizing binding mobile terminal to user
A mobile terminal, user binding technology, applied in instruments, inductive record carriers, computing, etc., can solve the problem that the user identification card cannot be used
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
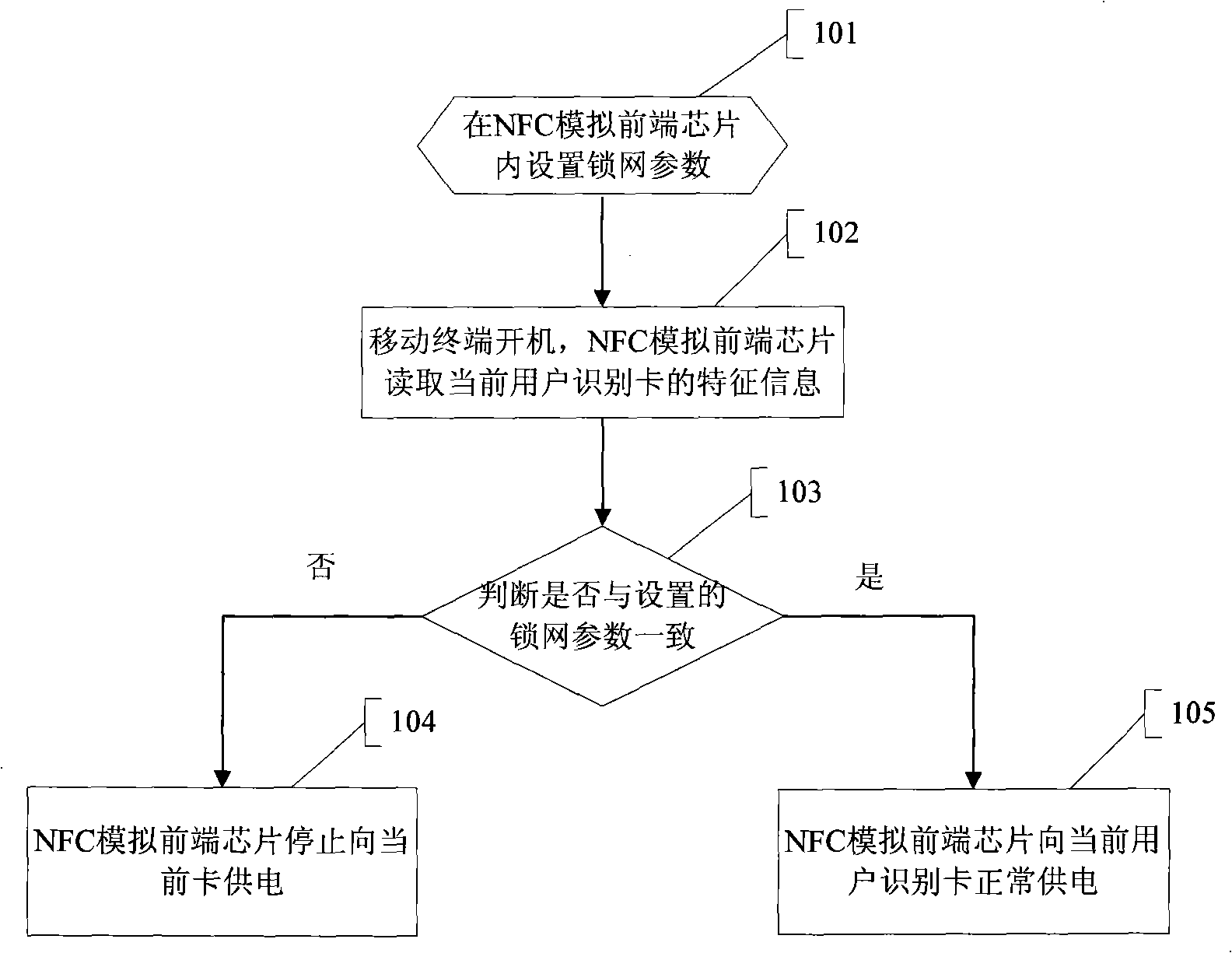
[0032] figure 2 Shown is a schematic flow diagram of applying the method of the present invention to realize the network locking function of the mobile terminal, including the following steps:
[0033] Step 101, setting lock network parameters in the NFC analog front-end chip of the mobile terminal, that is, setting the feature information of the subscriber identification card issued by the operator that is allowed to use;
[0034] The characteristic information of the subscriber identification card set here is information that can be used to distinguish certain types of subscriber identification cards. In this embodiment, the characteristic information that can distinguish the subscriber identification cards issued by a certain operator is set. The setting may be performed by a network operator or a mobile terminal manufacturer before the mobile terminal is provided to users. The network lock parameter (that is, the characteristic information of the subscriber identificatio...
no. 2 example
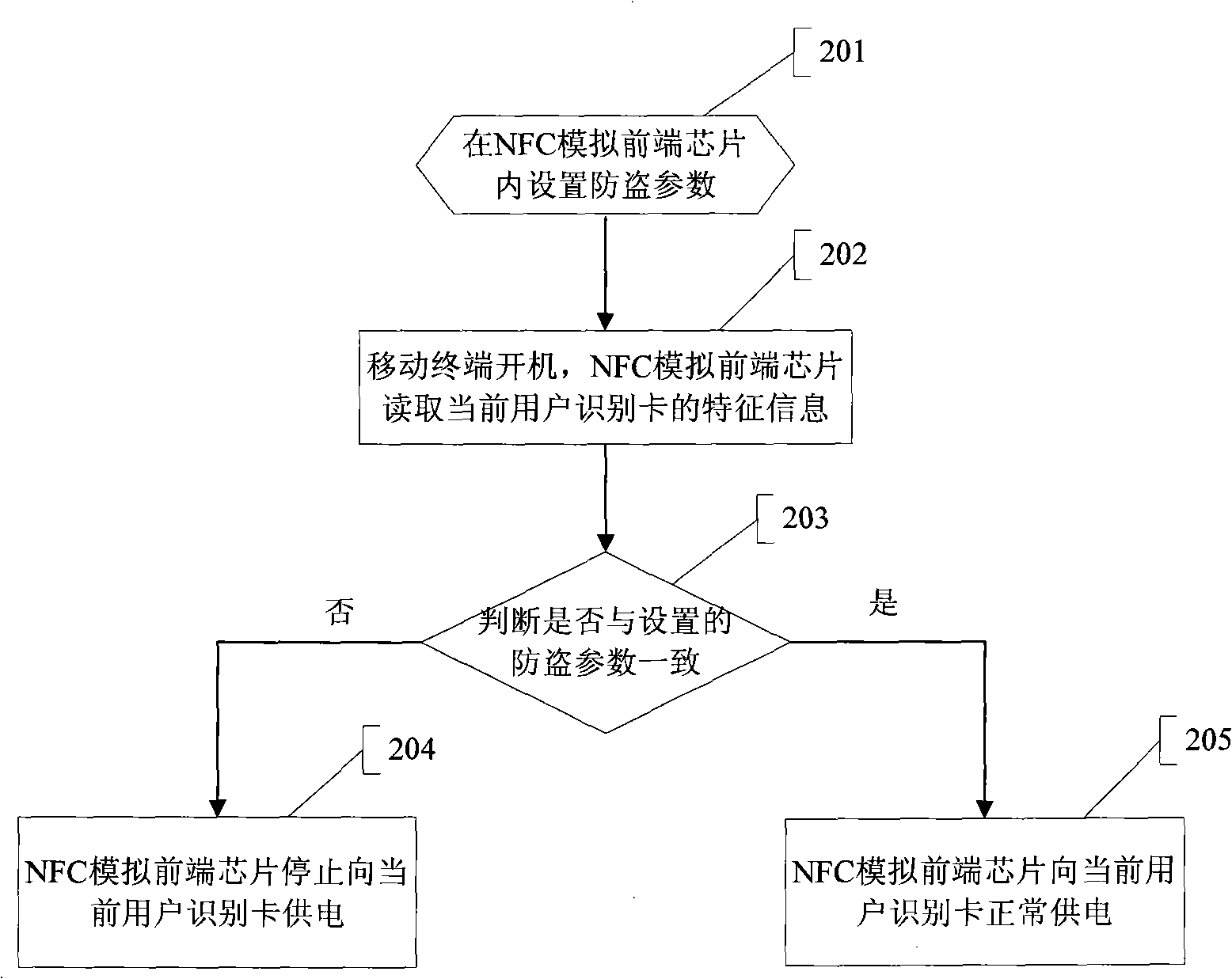
[0044] image 3 Shown is a schematic flow chart of implementing the anti-theft function of the mobile terminal by applying the method of the present invention, including the following steps:
[0045] Step 201, setting anti-theft parameters in the NFC analog front-end chip of the mobile terminal, that is, setting the feature information of the subscriber identification card used by the mobile terminal holder;
[0046] The anti-theft parameter may use the IMSI of the subscriber identity card. IMSI assigns a unique international mobile subscriber identity code to each mobile terminal user. This code is valid in all locations in the network including roaming areas, and can identify a unique subscriber identity card; and the IMSI written into the subscriber identity card cannot modified. IMSI consists of the following 3 pieces of information: the MCC, MNC and MSIN (Mobile Subscriber Identification Number) of the operator to which the card belongs are used to uniquely identify mob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com