Semiconductor device and method for preventing attacks on the semiconductor device
A semiconductor and device technology, applied in the field of semiconductor devices, which can solve the problem of chip exposure to attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
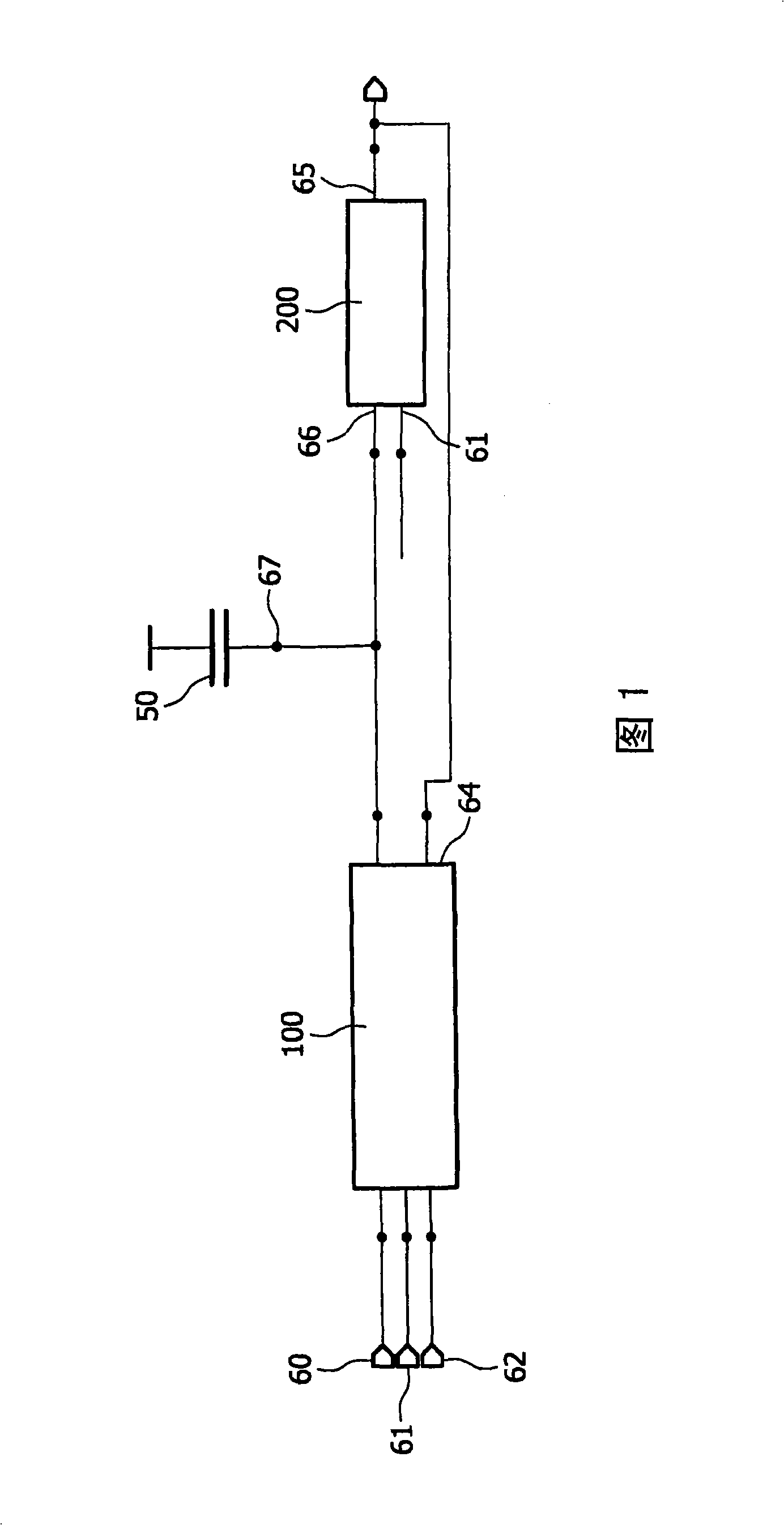
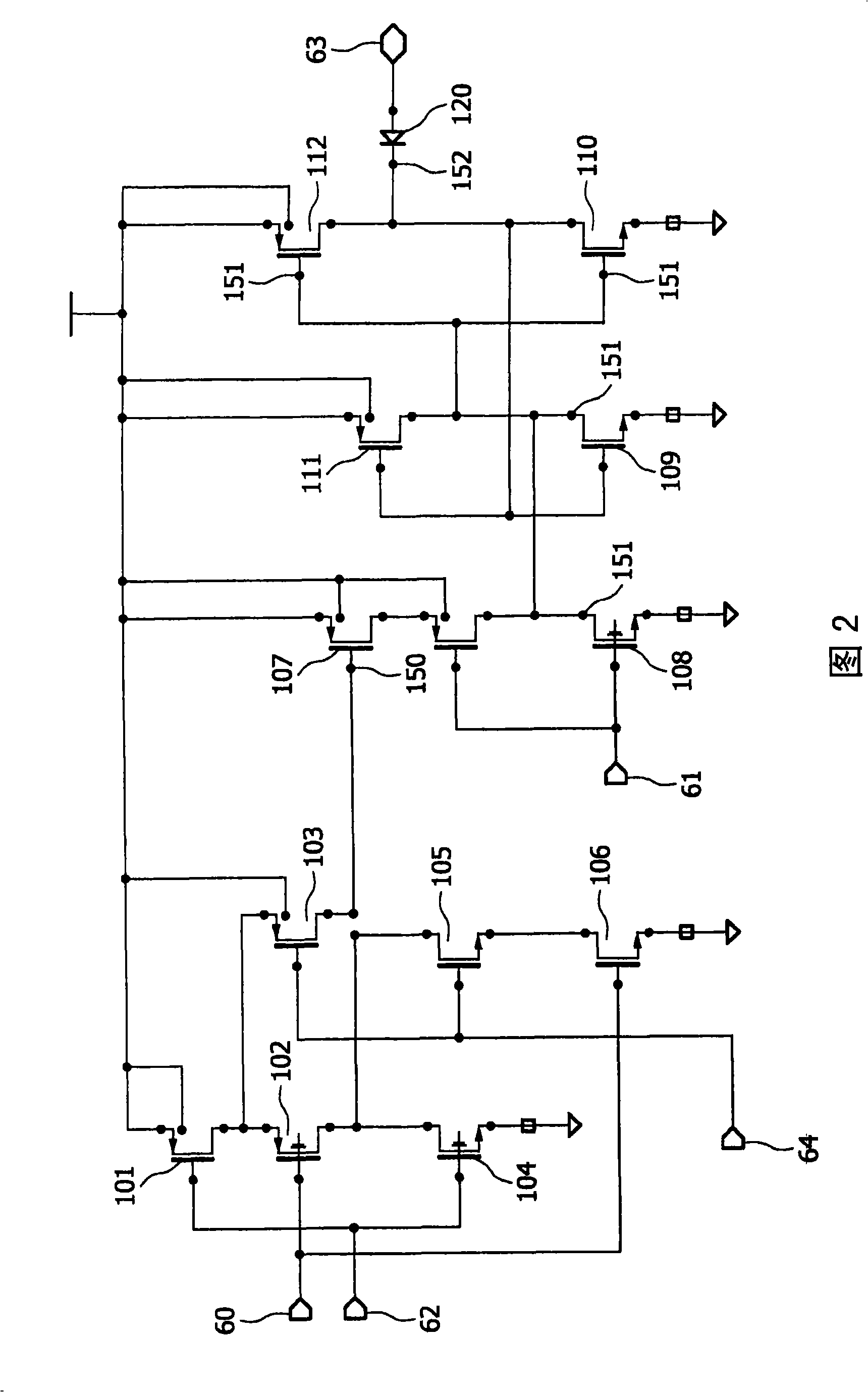
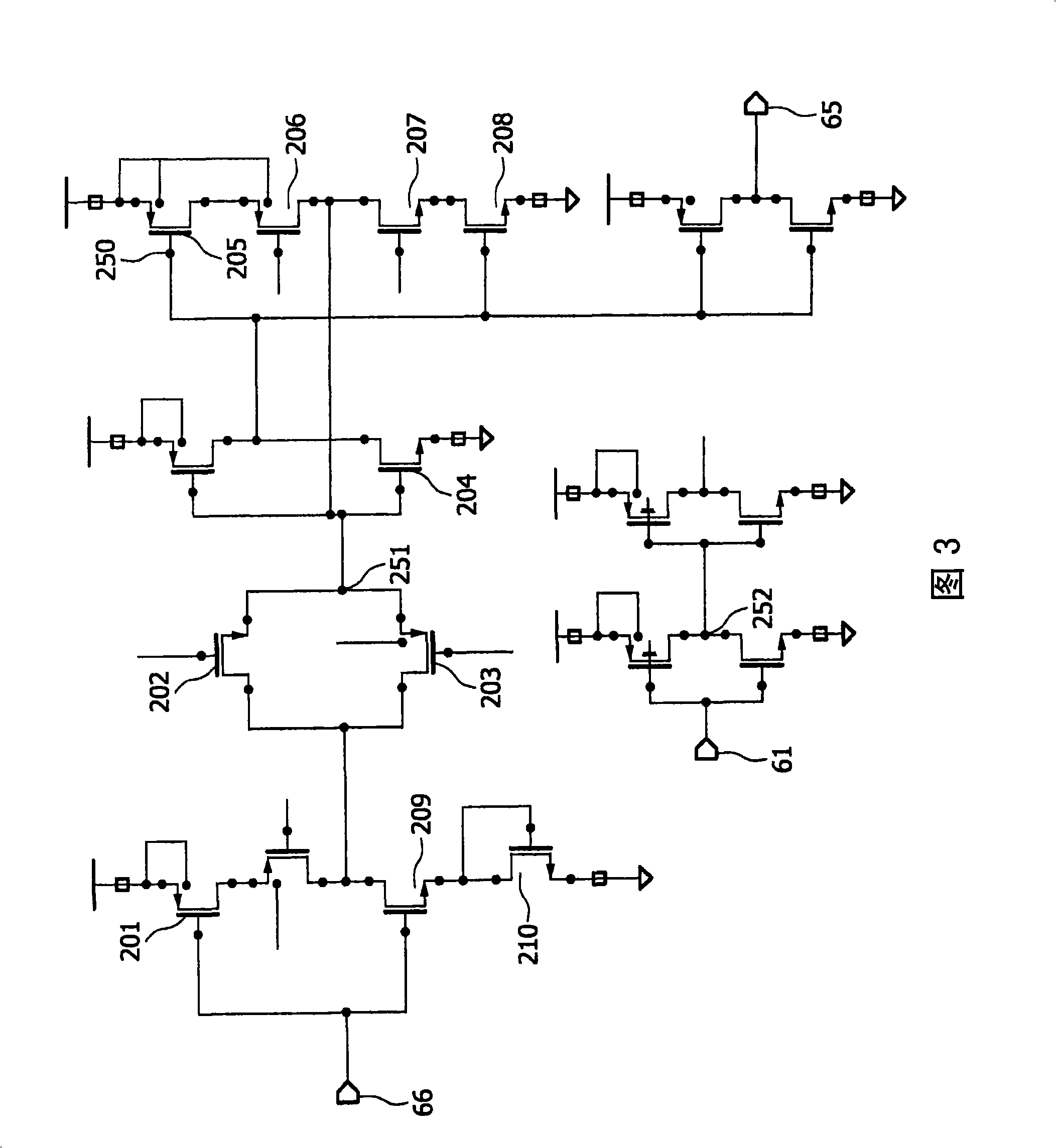
[0063]An example of an embodiment in which the semiconductor device is configured as a smart card chip is described below. The smart card chip includes means for storing items of information relating to the attack. An item of information may eg result from the reaction of one of the aforementioned sensors. The response of this sensor leads to initialization of the smart card chip. According to the invention, the items of information on the chip of the smart card which are relevant to the attack remain valid even after initialization. Once initialized, these items of information are read and used to trigger further initializations. This would cause the risk of an infinite loop of initialization, thereby preventing any update attack on the smart card chip.
[0064] If the smart card chip is disconnected from the supply voltage, the stored information items involved in the attack will remain intact for a predetermined period of time before being lost. Preferably, the time per...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com