Method and apparatus for discovering malignancy of computer program
A computer program and malicious technology, applied in computer security devices, calculations, instruments, etc., can solve problems such as difficult to identify hidden virus programs, and achieve the effect of accurate and efficient discovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
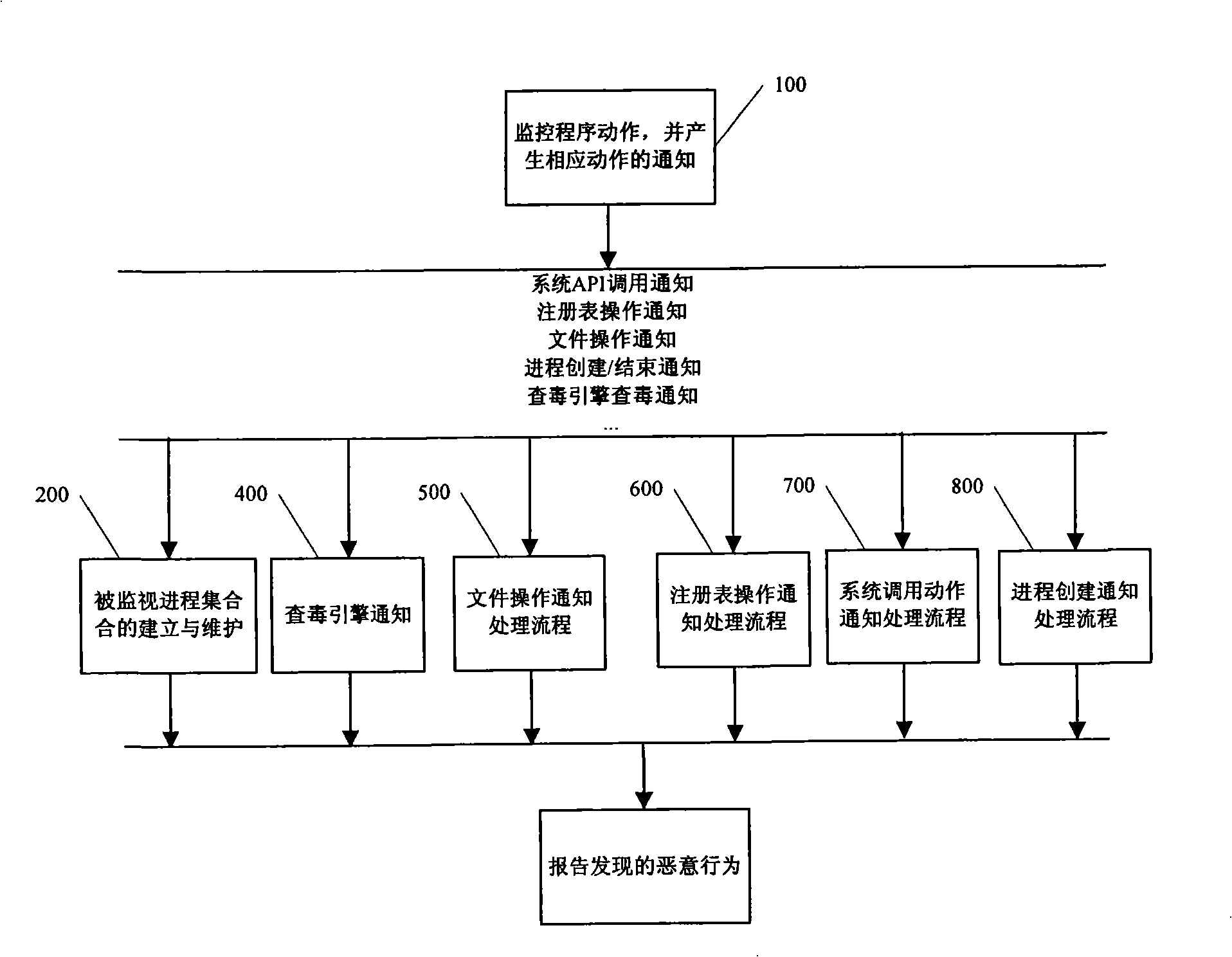
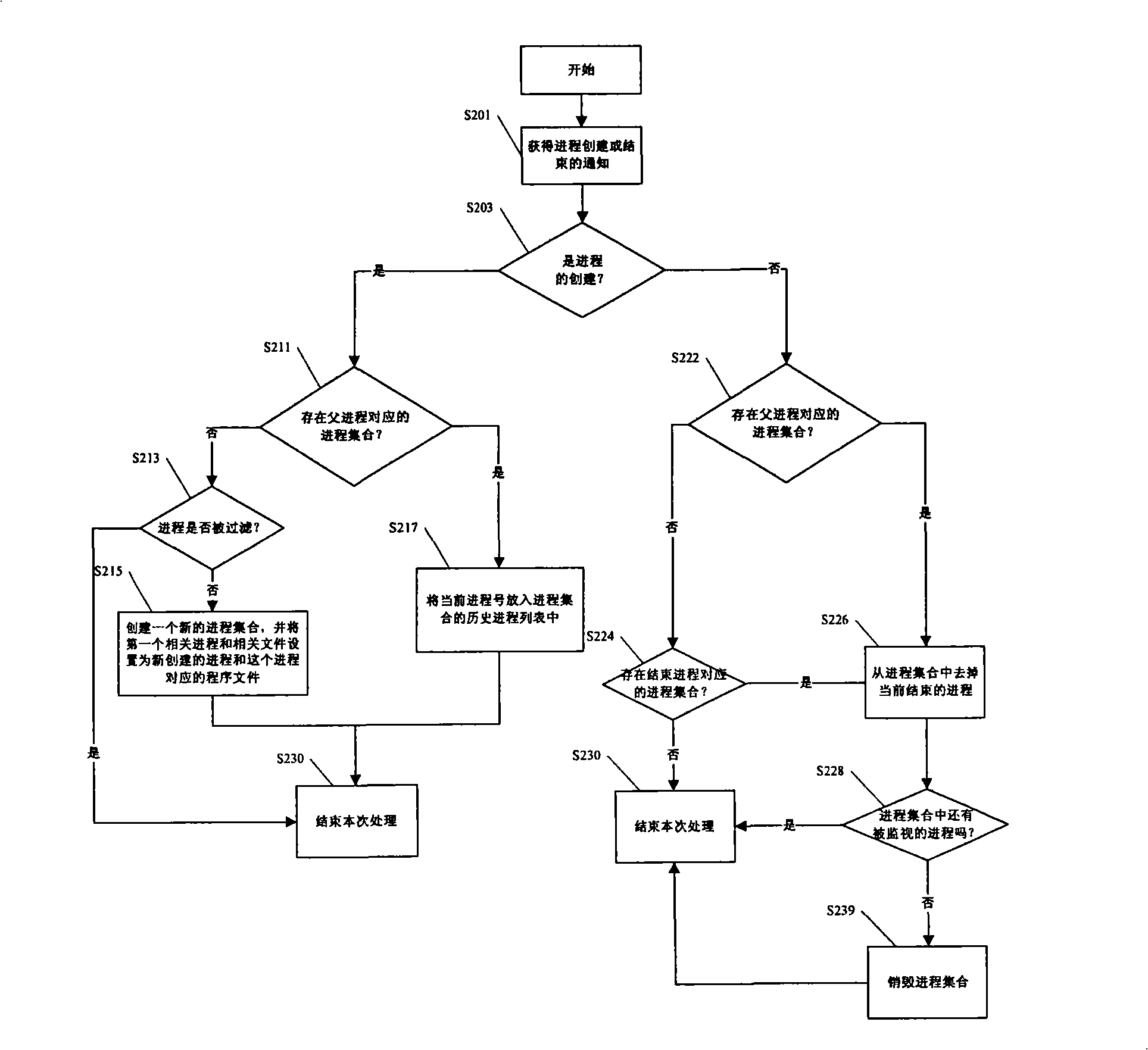
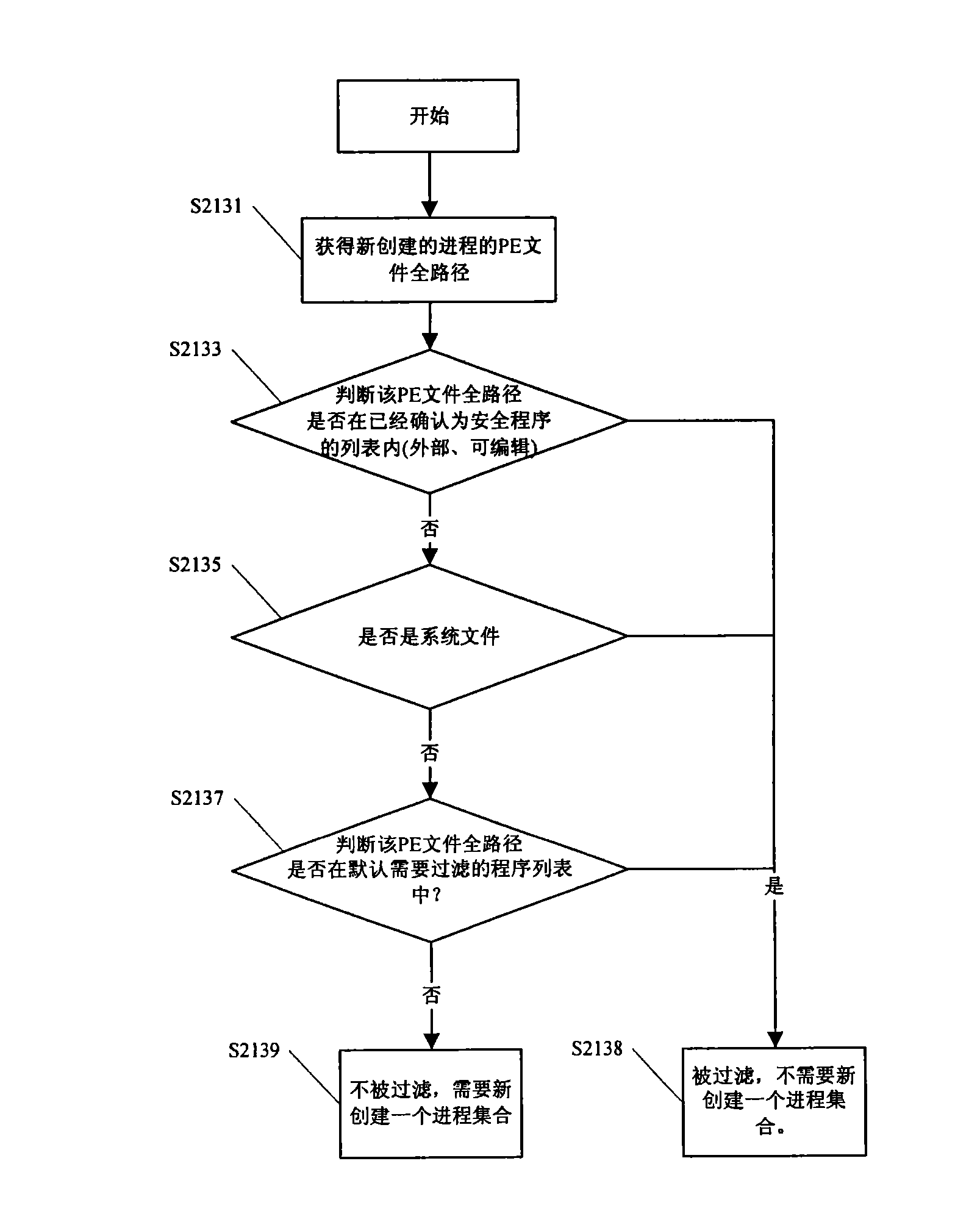
[0025] The method and apparatus for discovering malicious behaviors of computer programs proposed by the present invention will be described in detail below in conjunction with specific embodiments. For ease of understanding, in the following embodiments, only the Windows operating system is used as an example for description. However, those skilled in the art can understand that the idea and spirit of the present invention can also be applied to other computer systems, not limited to the Windows operating system.
[0026] Like the aforementioned "grey pigeon" program, today's viruses or spyware no longer attack computers in a single process, but perform malicious actions in the process of creating and / or ending multiple processes, so that they It is easier to fool the monitoring of anti-virus software.
[0027] In addition, through the analysis of many computer virus programs and spyware today, it can also be found that malicious programs may be composed of some basic malici...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com