Method, system and device for protecting privacy of customer terminal
A user terminal, privacy technology, applied in the field of communication, can solve the problem of deleting user context, etc., to achieve the effect of protecting privacy and avoiding permanent identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The implementation of the present invention will be further described below in conjunction with the drawings and examples.
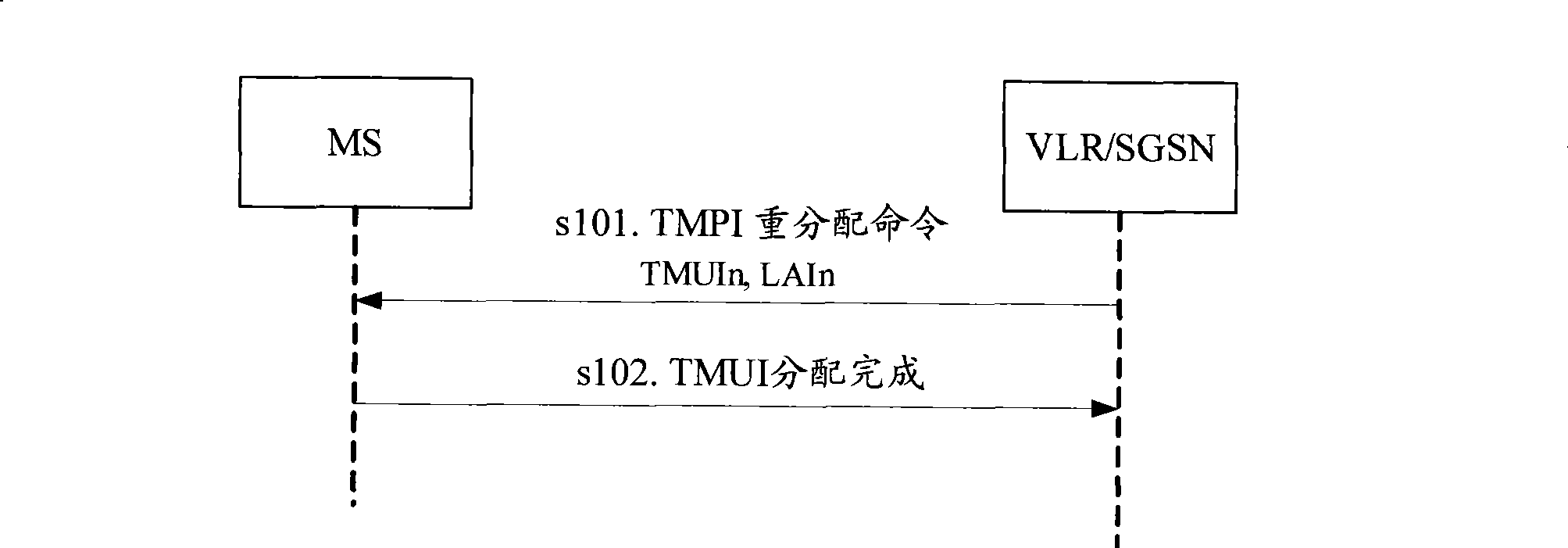
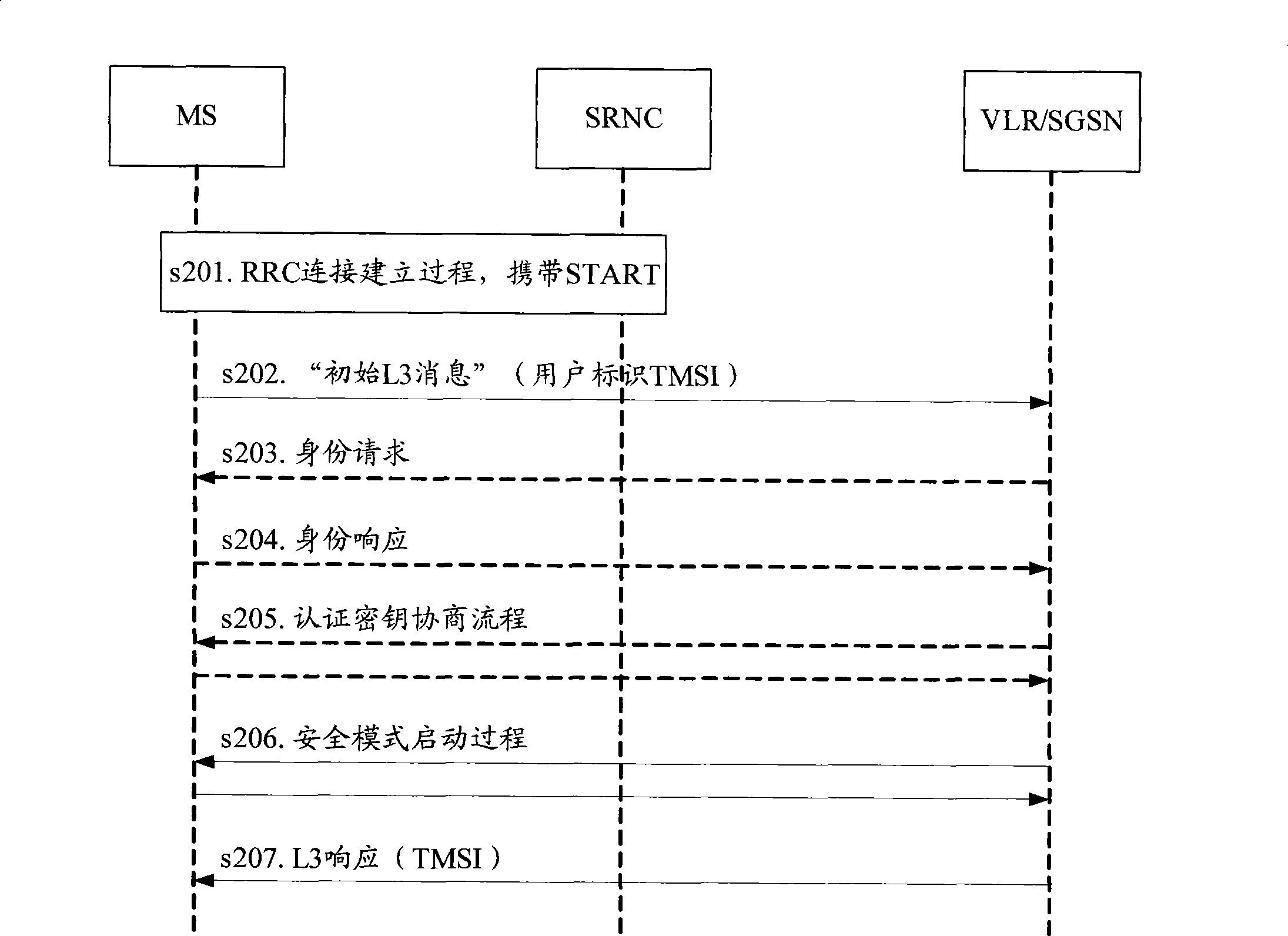
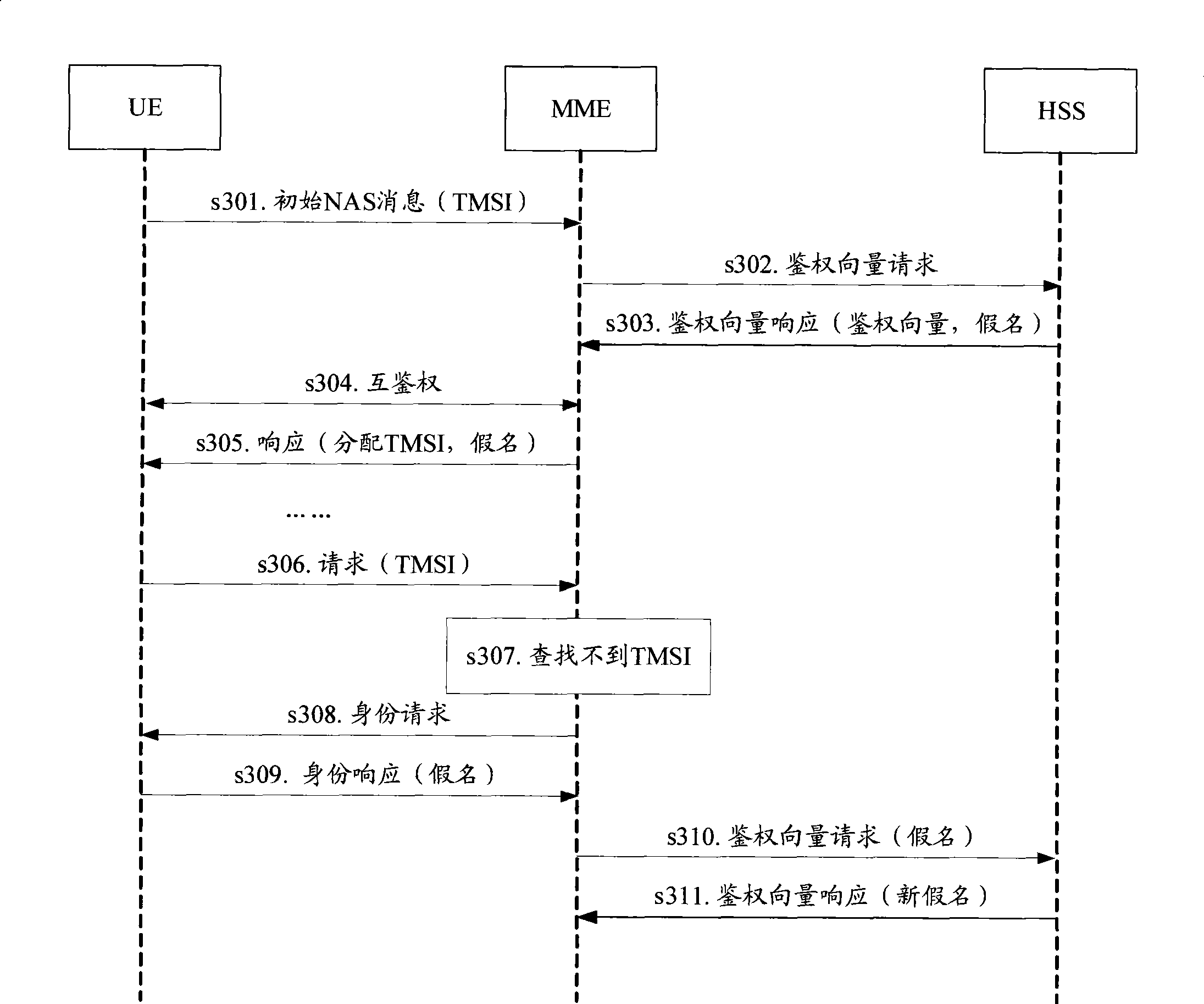
[0042]In Embodiment 1 of the present invention, the privacy of the user terminal is protected by using a pseudonym on the user terminal. Specifically, when the temporary identity of the user terminal cannot be recognized by the network side, the previously assigned pseudonym replaces the permanent identity and is sent to the network side for authentication, preventing illegal terminals from pretending to be the network to send identity request information to obtain the UE's permanent identity. In specific implementation, in order to reduce the impact on the AKA protocol, after the HSS generates a pseudonym and sends it to the MME (Mobile Management Entity, mobile management entity), the MME does not issue the pseudonym during the AKA process, but saves it. When the AKA ends and the temporary identity is assigned to the UE, the pseudonym assigned b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com