Embedded enciphering system
An embedded system, encryption system technology, applied in the direction of user identity/authority verification, etc., can solve the problem that the general encryption system is not suitable for use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0009] specific implementation plan
[0010] An embedded encryption system including server and client.
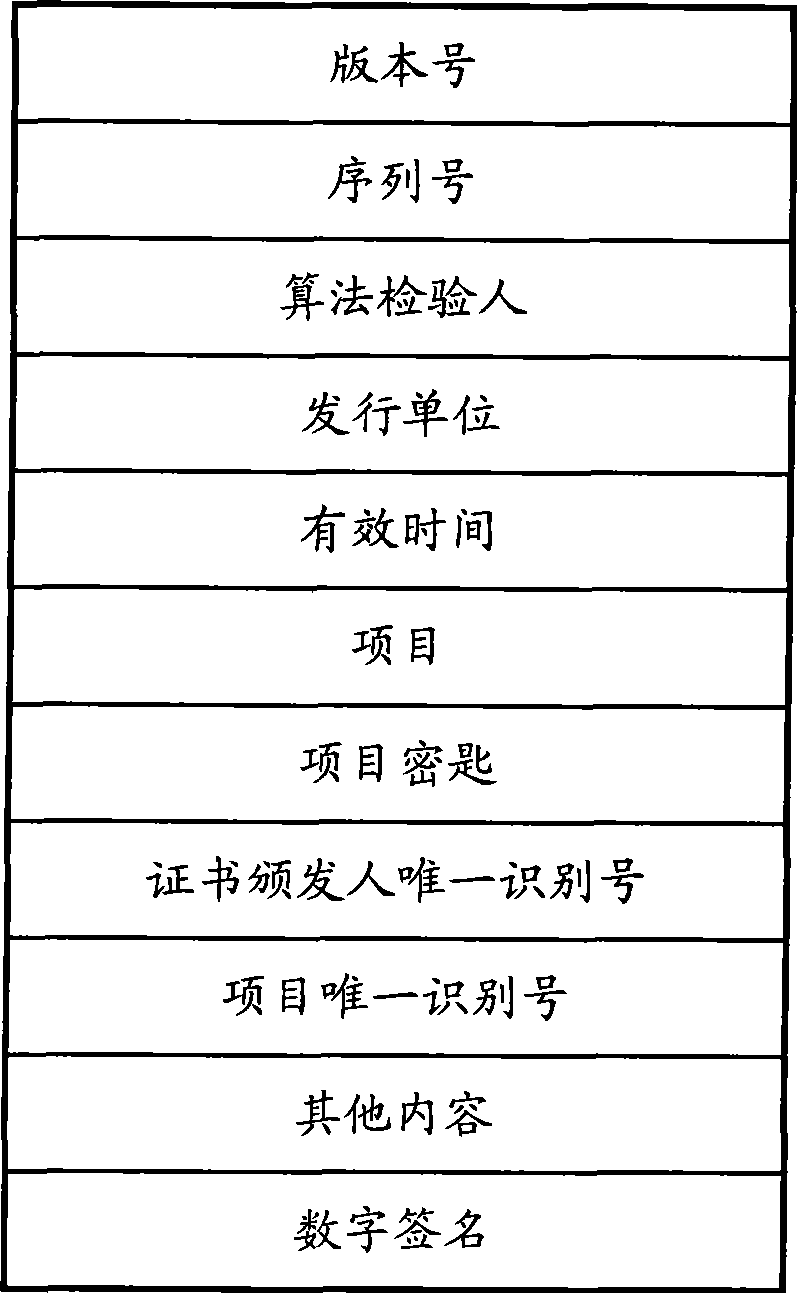
[0011] The most important mechanisms in the embedded encryption system of the present invention are multi-level key mechanism, security certificate, digital signature, etc., which will be introduced in detail below.
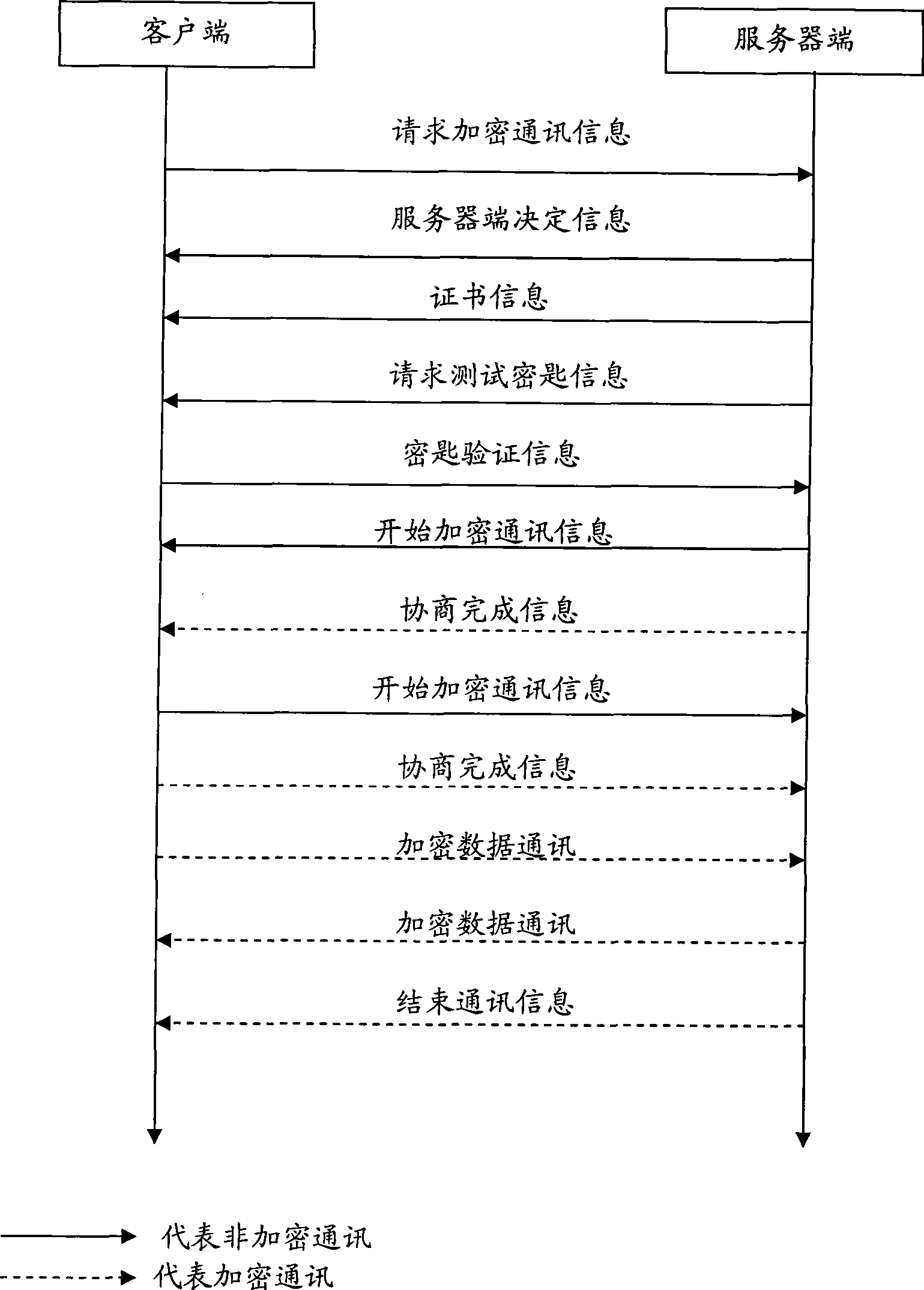
[0012] The main process of the encryption system is: the server side establishes a connection with the client side by generating a security certificate loaded with a specific digital signature, and establishes an encrypted communication connection for communication after a series of information exchanges between the two parties.
[0013] When an encrypted communication connection needs to be established, the client first sends a connection establishment request. The server sends a response after receiving the request. After receiving the response, the client first needs to confirm that it is communicating with the correct server, and then establish an encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com