Method for generating network authority hoisting route based on data digging technology
A privilege escalation and data mining technology, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
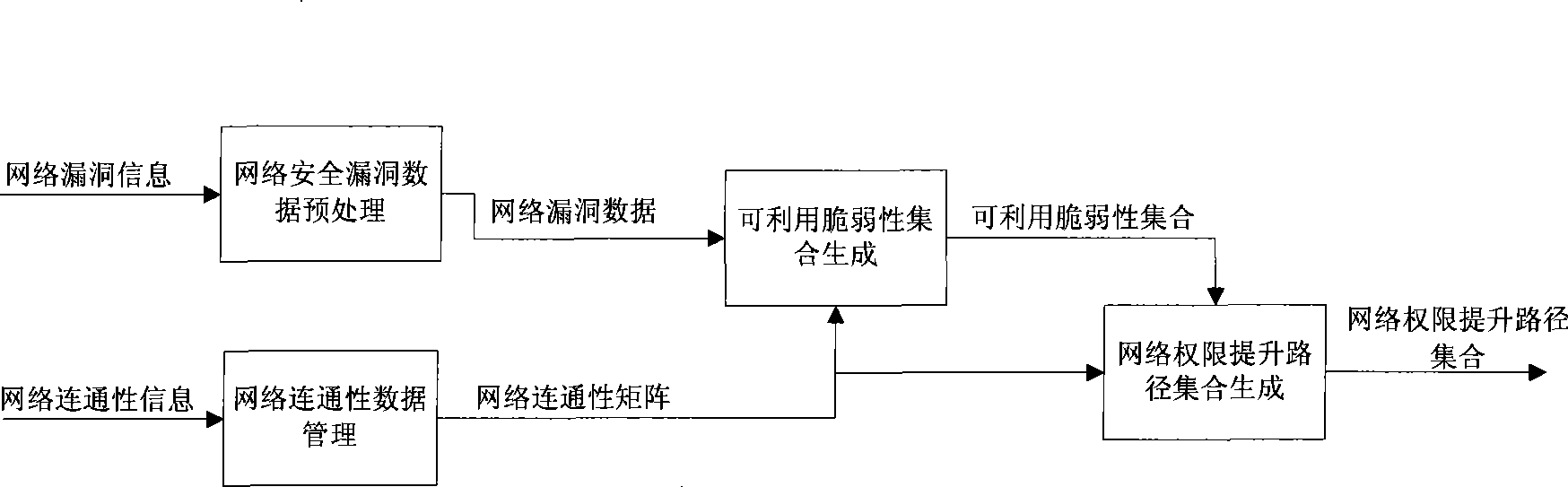
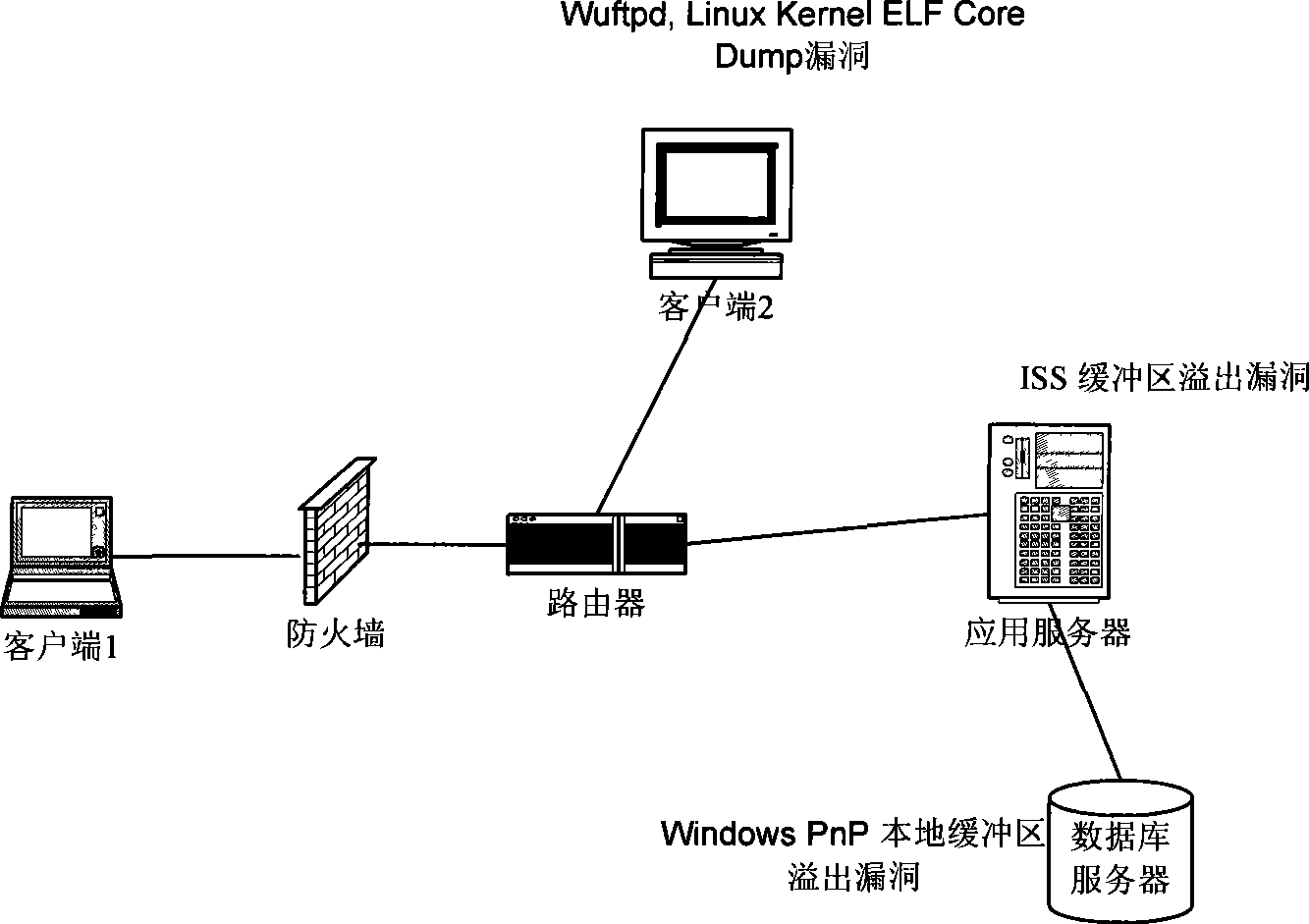
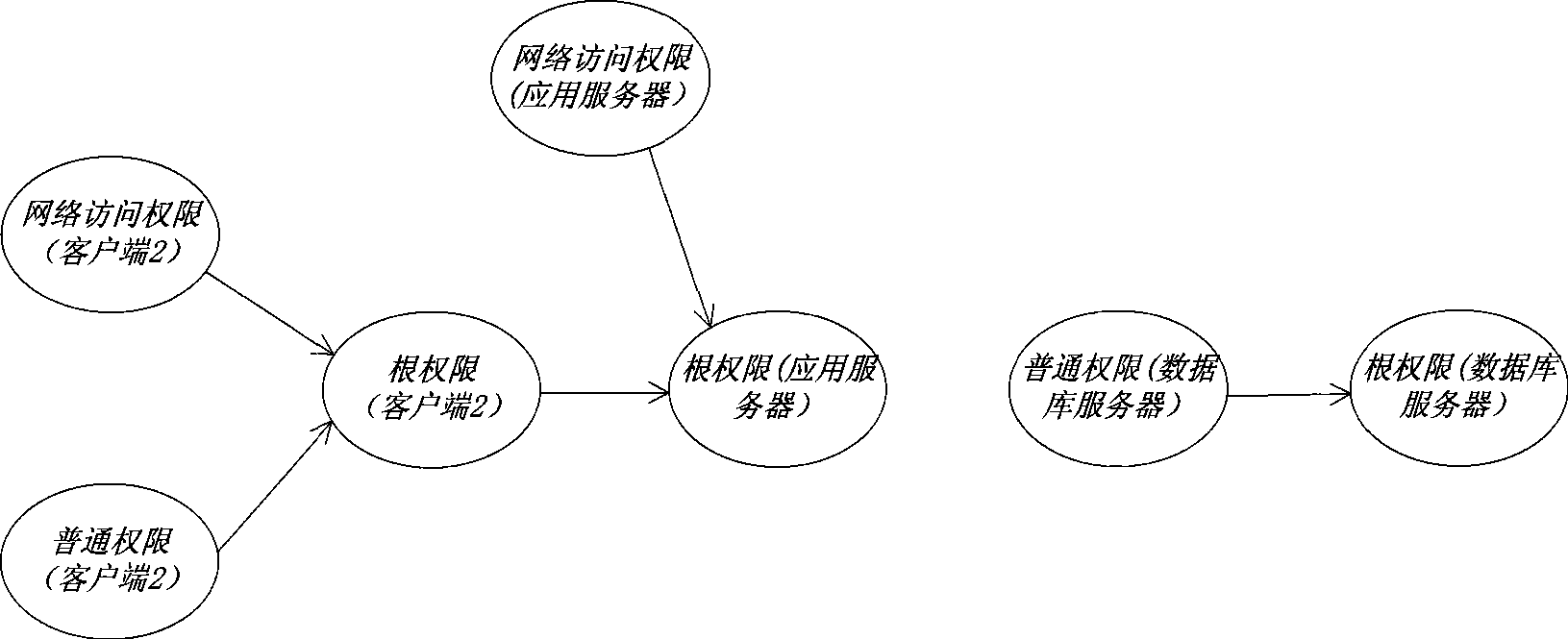
[0027] According to the common network application technology architecture, without loss of generality, adopt figure 2 The network shown in is used as an example. In the example, the application server is responsible for providing enterprise application services. It is directly connected to the database server and connected to client 2 and client 1 via a router; client 1 represents access from external customers, and client 2 represents access from internal The customer's access, the security loopholes in it have been marked in the figure respectively, specifically as figure 2 shown;
[0028] 1. Network vulnerability data preprocessing
[0029] The input of this step is the network security vulnerability information, and the network vulnerability data is output as the network vulnerability data in a given format through preprocessing of the network vulnerability data. Specifically, the network security vulnerabilities in this example have been marked on their respective h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com